| FileWave Central | FileWave Anywhere |
| [](https://kb.filewave.com/uploads/images/gallery/2023-09/oBkPgmcZik7IX2C6-image.png) | [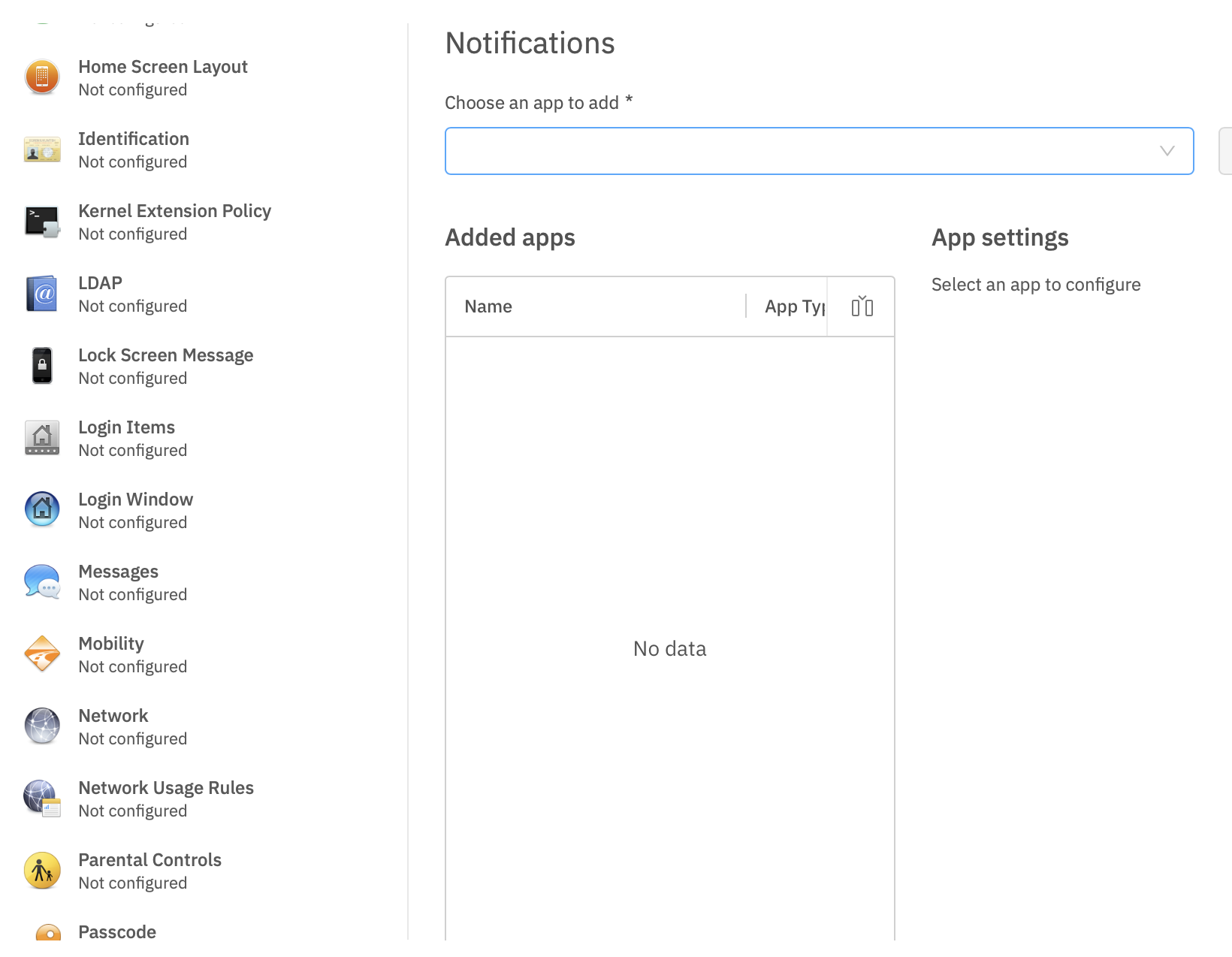](https://kb.filewave.com/uploads/images/gallery/2023-09/dkacmlqpWuWaVWdC-image.png) |
| [](https://kb.filewave.com/uploads/images/gallery/2023-09/XcsrqBqh27AhI4EM-image.png) | [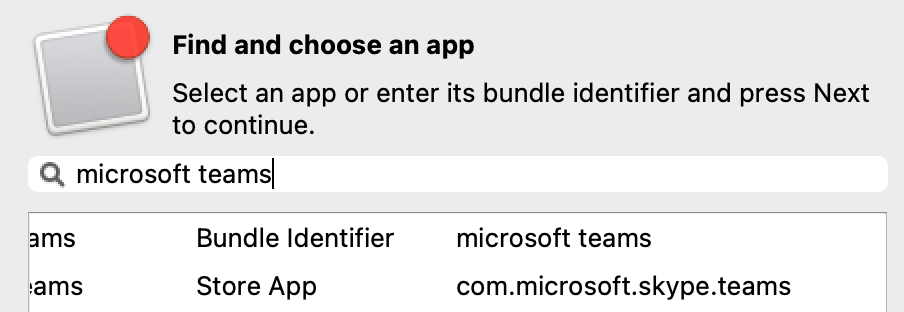](https://kb.filewave.com/uploads/images/gallery/2023-09/L06S9miJZMT1rKxE-image.png) |
| FileWave Central | FileWave Anywhere |
| [](https://kb.filewave.com/uploads/images/gallery/2023-09/KSf7e6rmCZX4AIgK-image.png) | [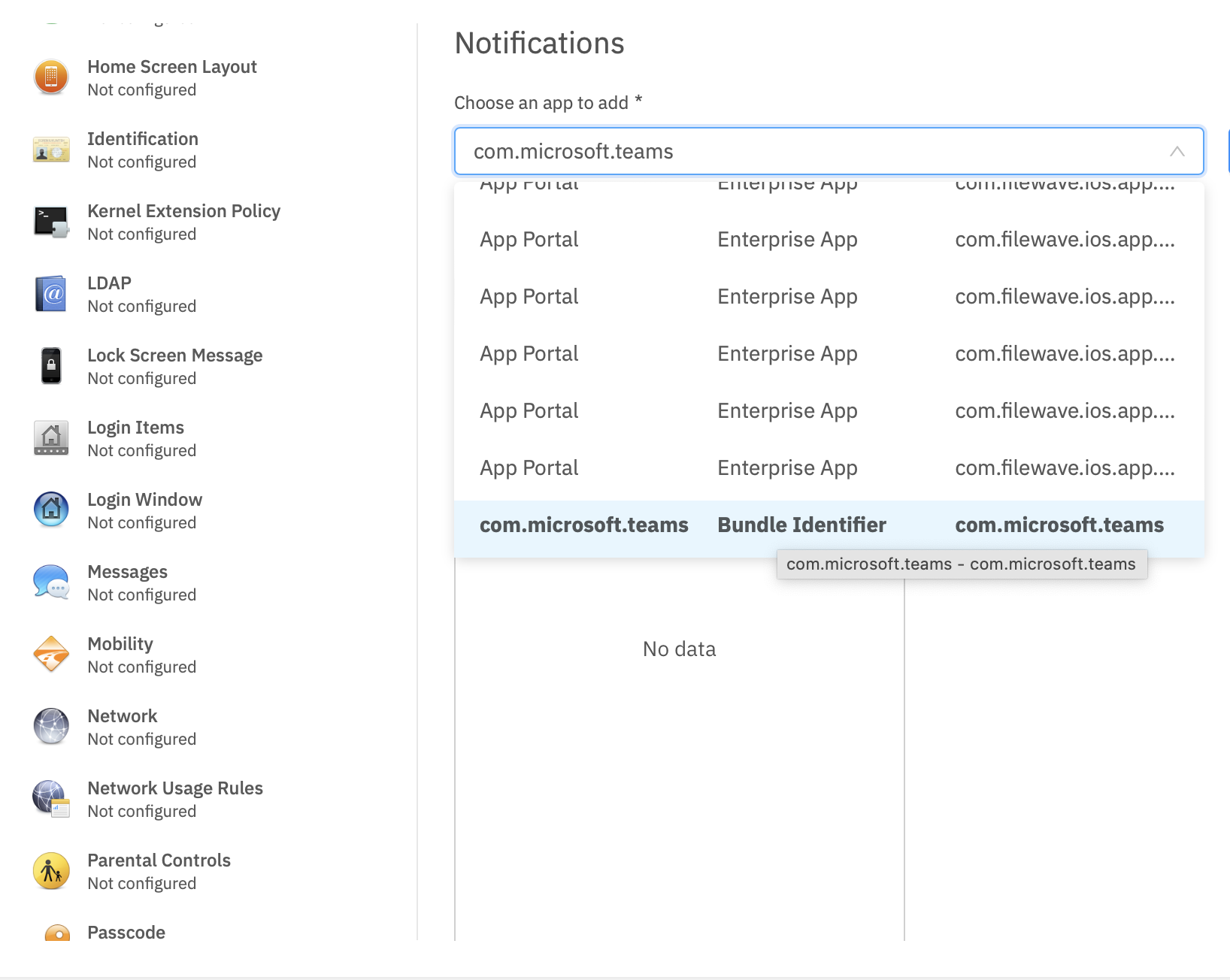](https://kb.filewave.com/uploads/images/gallery/2023-09/afEpt3taM1ESCUJM-image.png) |
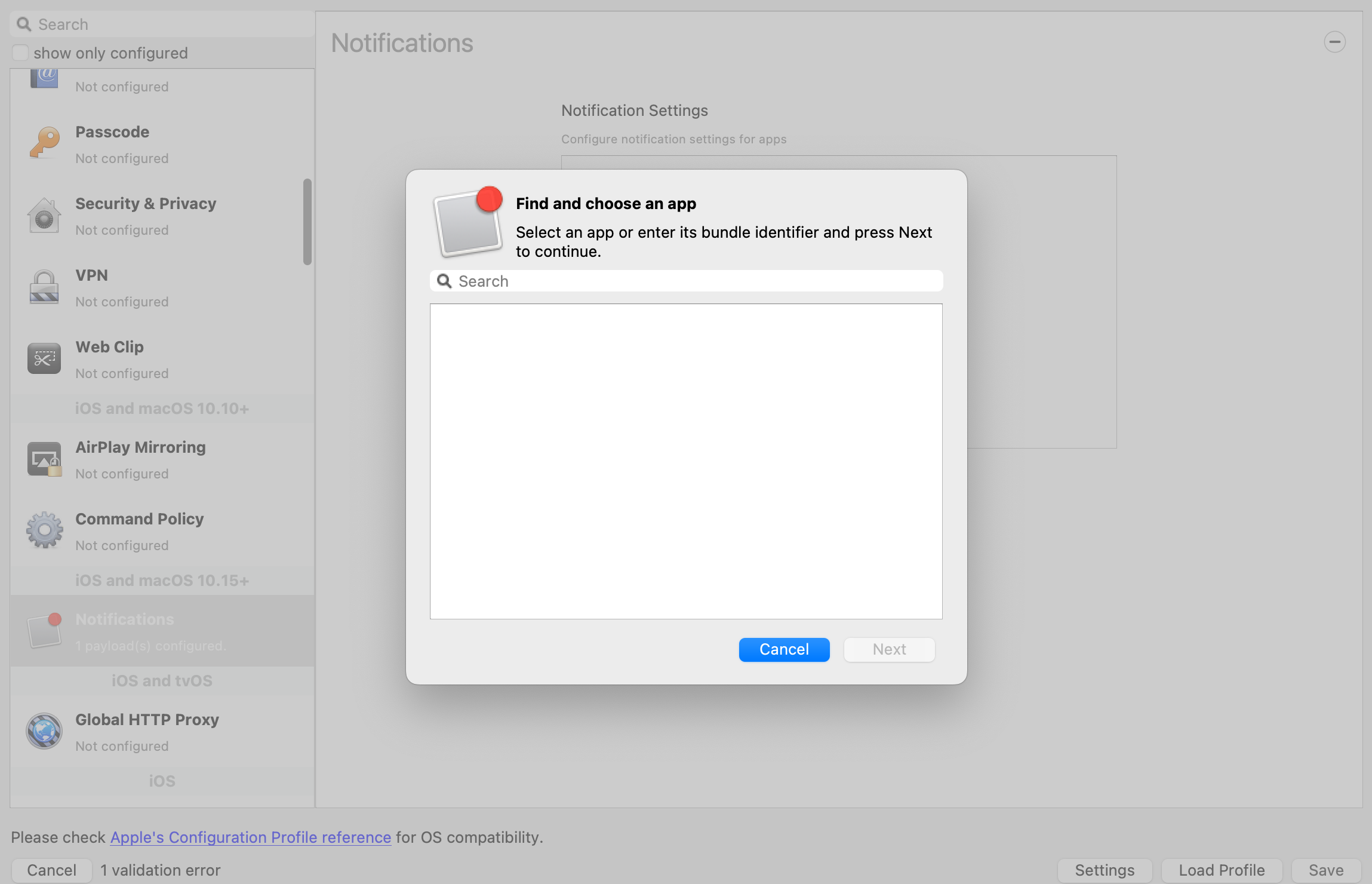
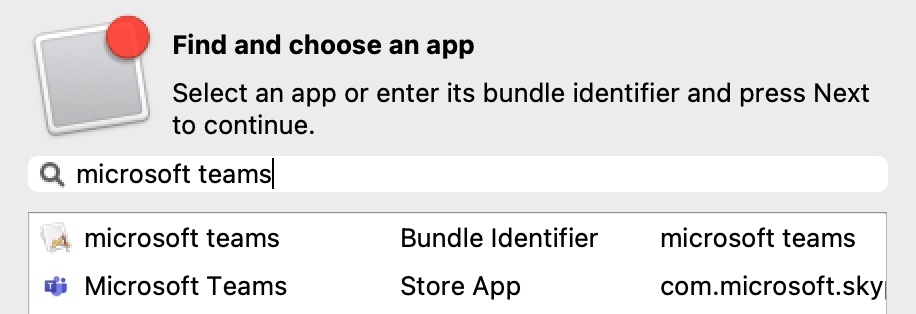
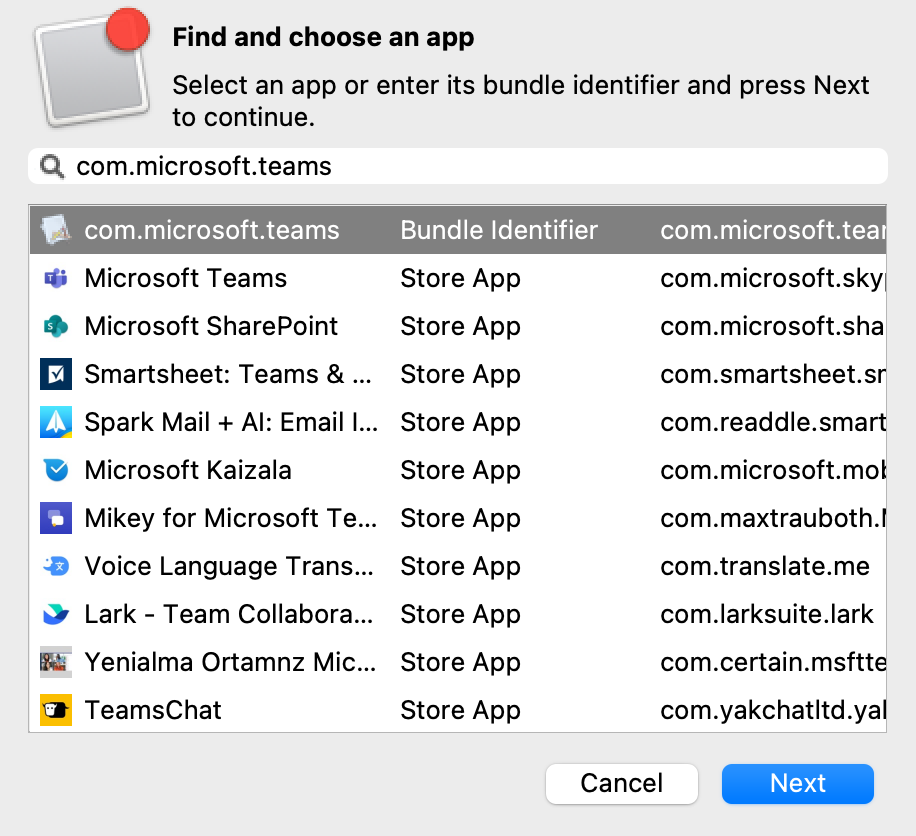
Re-opening the Payload in the future may show the Bundle ID instead of the App name, where App Store items were previously accepted.
[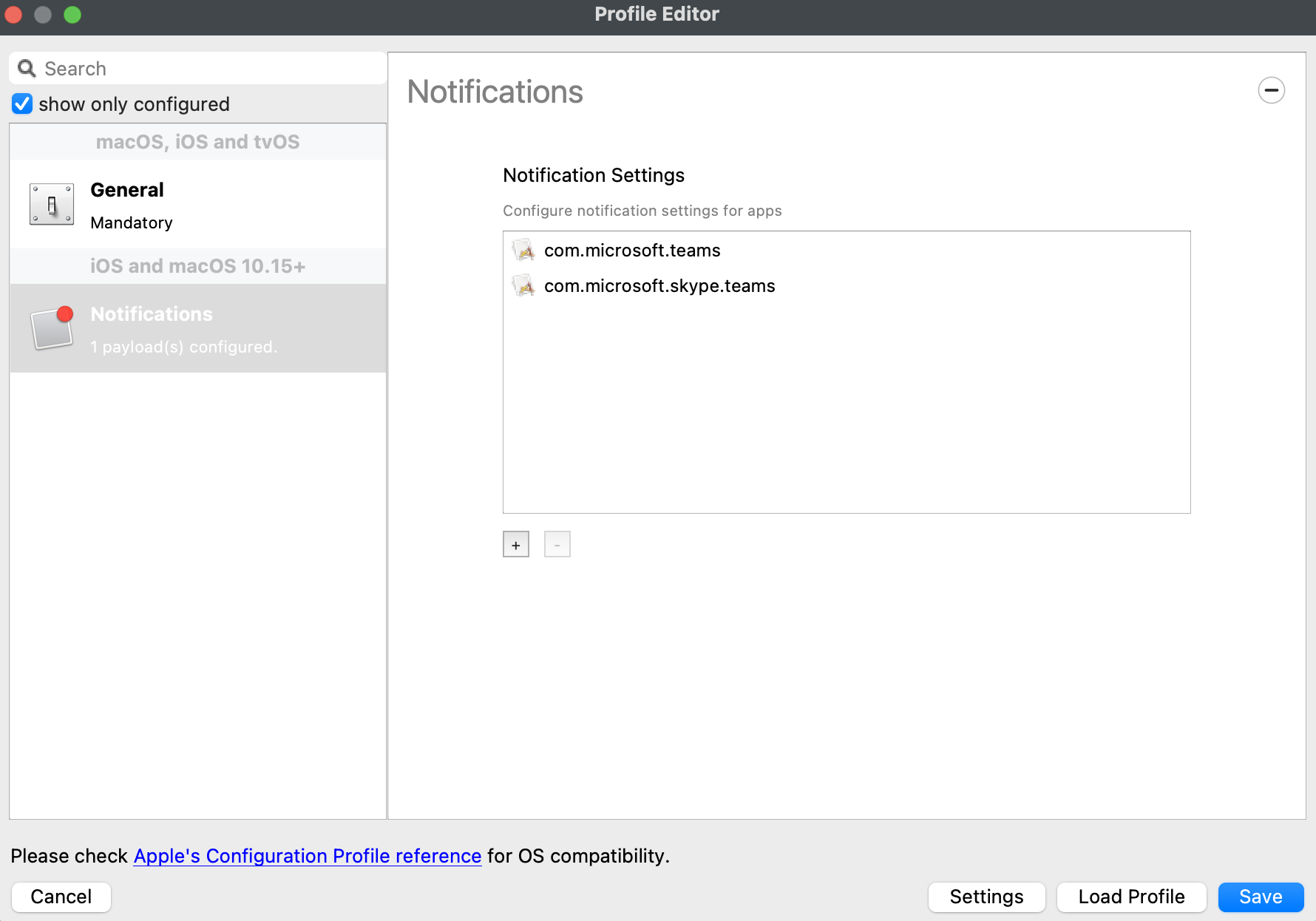](https://kb.filewave.com/uploads/images/gallery/2023-09/MUCM0AYraIrpR9ED-image.png) Home Screen Layout is another Payload example which requires a Bundle ID and the search should behave in the same manner, where if found, the App Store version may be selected, otherwise the Application Bundle ID must be added manually into the search box to be selected:| [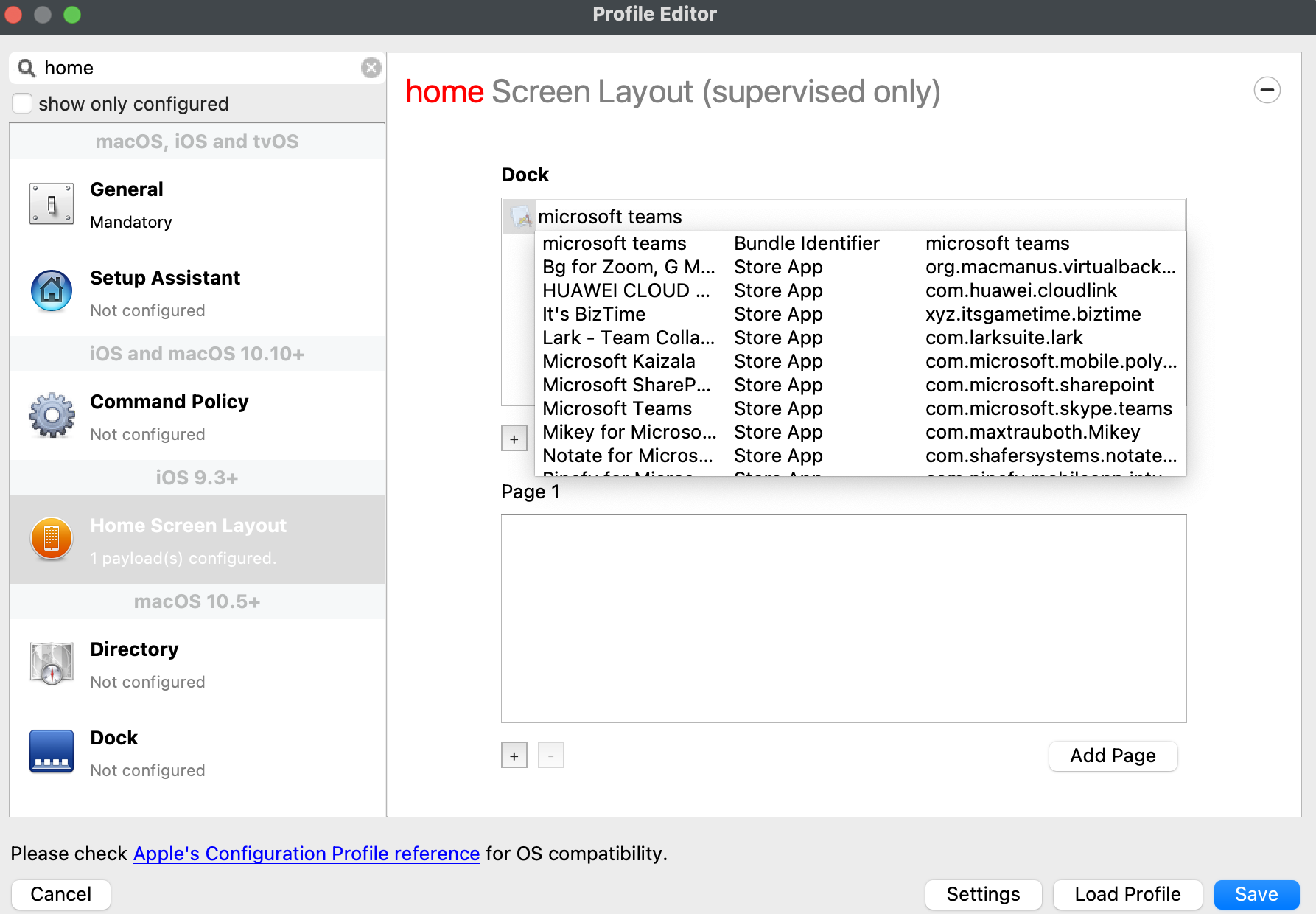](https://kb.filewave.com/uploads/images/gallery/2023-09/aCdnWeZqG1AjwmKE-image.png) | [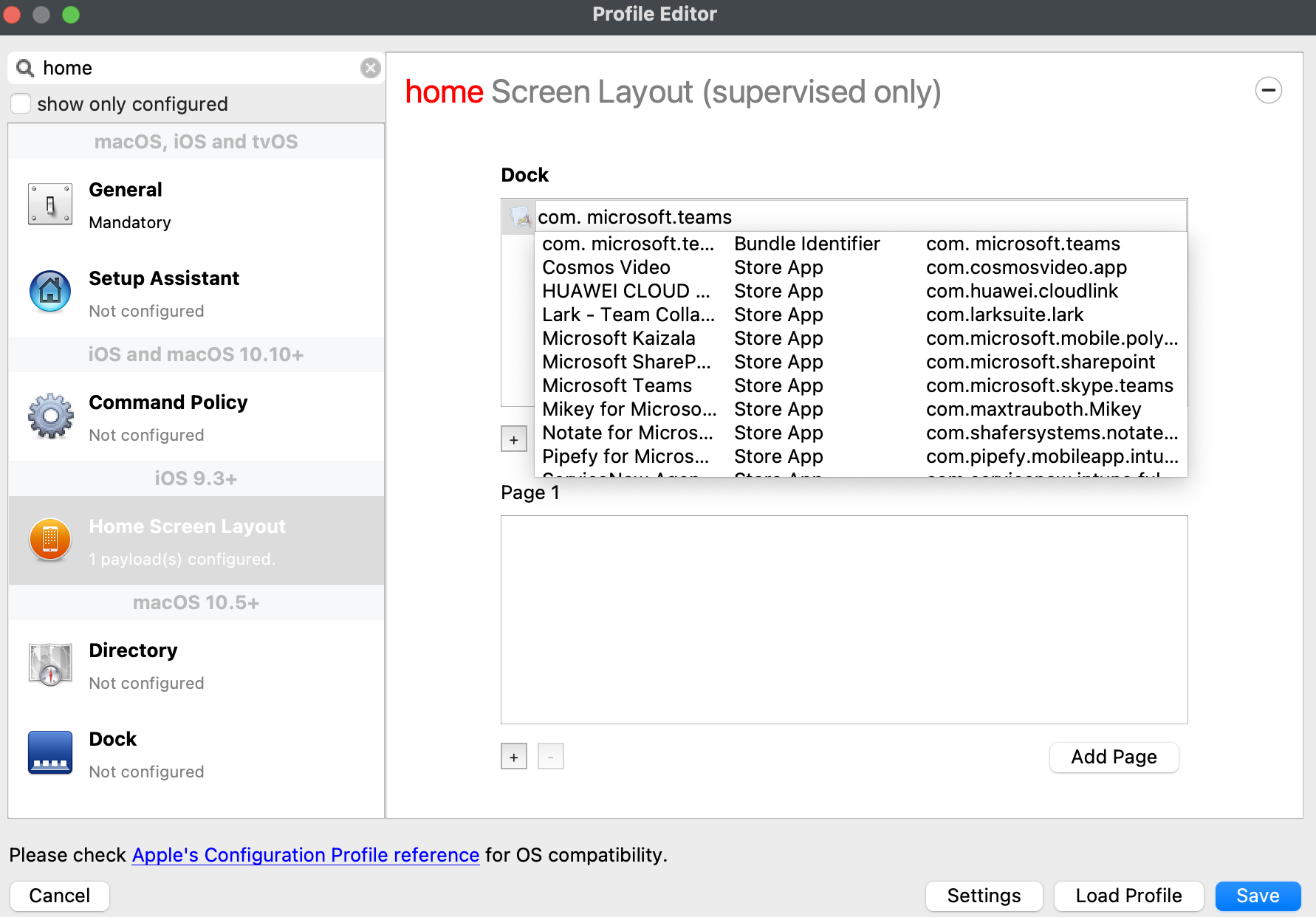](https://kb.filewave.com/uploads/images/gallery/2023-09/lxLSa1IuteRmcwos-image.png) |
| [](https://kb.filewave.com/uploads/images/gallery/2023-09/WQYjOBAevprqoQLI-image.png) | [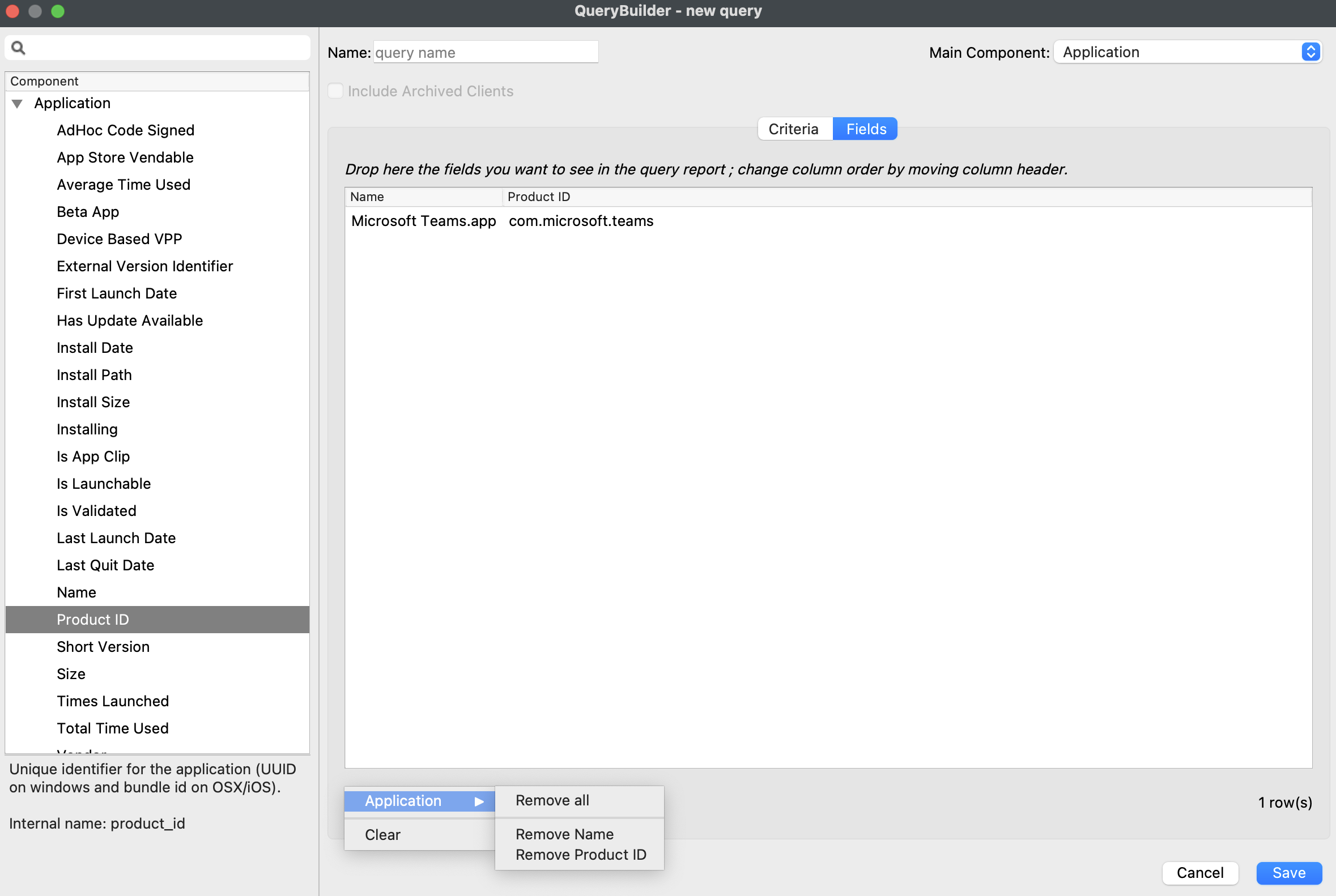](https://kb.filewave.com/uploads/images/gallery/2023-09/kXUYiVvEn5vufzEy-image.png) |
| ↓ macOS |
| [](https://kb.filewave.com/attachments/163) |
| ↓ maOS |
| [](https://kb.filewave.com/attachments/164) |
Where an alternate browser is targeted, that browser must already be installed on the device.
## How ### Web Clip URLPage may need to be a non-secure or secure link, http or https respectively. Be sure to test the URL link before mass deployment.
Configuring a Web Clip Payload to use either http or https, will cause the Web Clip to open in the users chosen default browser. This will be Safari, if not changed. For example, on an non-configured device, meaning Safari is default, either of the following should open using Safari: - `http://ww.filewave.com` - `https://www.filewave.com` Each browser has an identifier which may be set to force the Web Clip to open in that browser, including:| Browser | Browser URL Prefix | Browser URL Secure Prefix |
| Google Chrome | googlechrome:// | googlechromes:// |
| Firefox | firefox://open-url?url=http:// | firefox://open-url?url=https:// |
| Microsoft Edge | microsoft-edge-http:// | microsoft-edge-https:// |
| Browser | Bundle ID |
| Safari | com.apple.mobilesafari |
| Firefox | org.mozilla.ios.Firefox |
| Opera | com.opera.OperaTouch |
| Microsoft Edge | com.microsoft.msedge |
| Google Chrome | com.google.chrome.ios |
| Brave | com.brave.ios.browser |
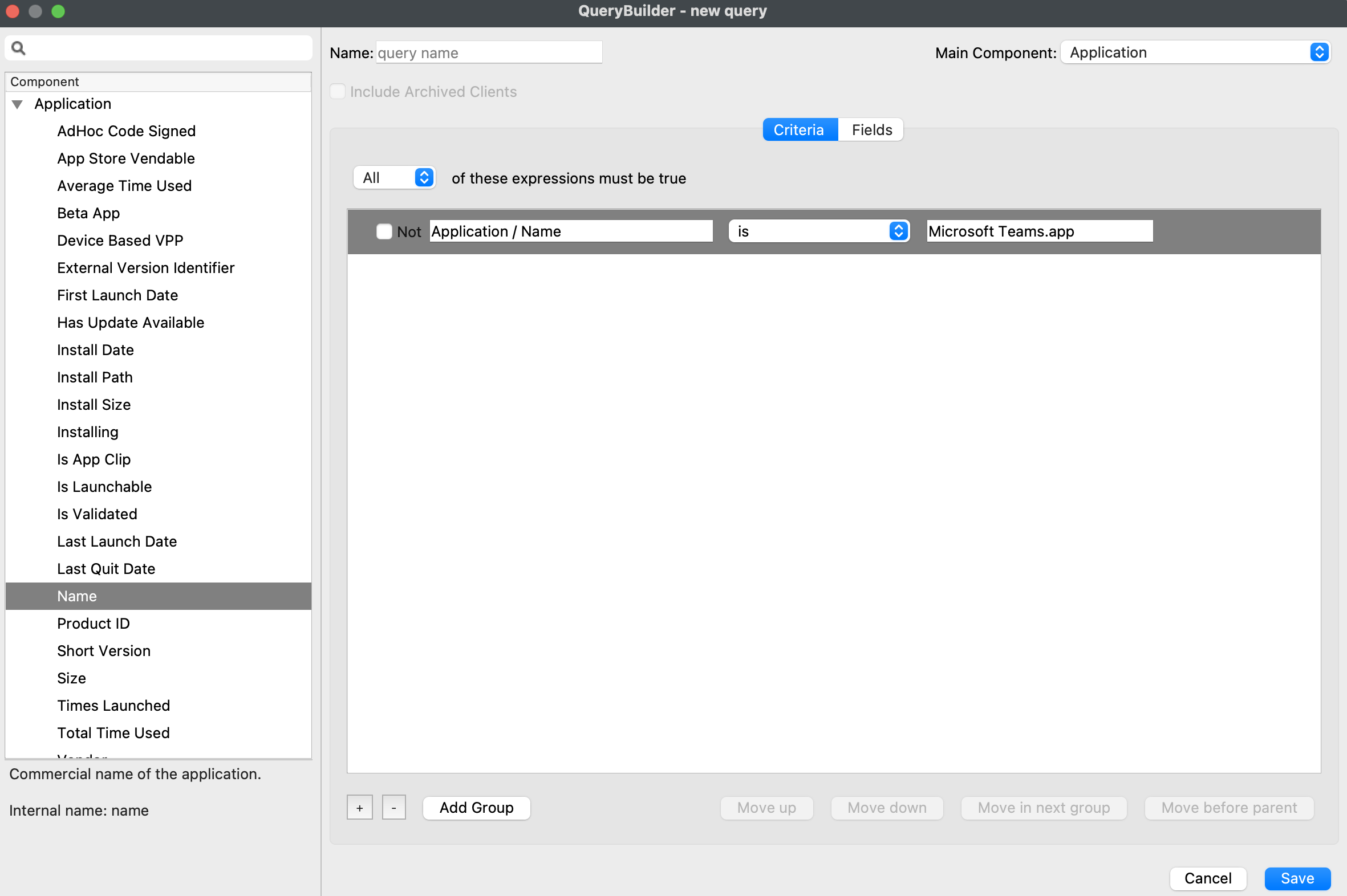
| 1. Create a new profile | |
| 2. Select "Command Policy" in the *iOS and macOS 10.10+* section | [](https://kb.filewave.com/uploads/images/gallery/2023-07/2q1RcxLKC2sturHW-image.png) |
| 3. In the profile definition, enter the url provided by your carrier in the *Refresh Cellular Plan* section | [](https://kb.filewave.com/uploads/images/gallery/2023-07/VUEfciOxIlmMIWC7-image.png) |
| 4. Deploy the profile to the corresponding devices |
Bundle ID Since the Bundle ID is the same for all Web Clips, restrictions will either allow or deny all Web Clips. Associations should be used for granular control.
User Created Web Clips When App Restrictions are in place which deny 'Allow Removing Apps', users may create their own Web Clips, but will not be able to remove them.
# FileWave Apple Profile Editor Explained ## Description Configuration of Apple devices largely relies upon Profiles. Profiles contain Payloads: settings defined to control aspects of the Operating System and user experience. FileWave has a built-in editor allowing the building of Profiles. This editor is designed to ensure Profiles only contain Payload keys that meets Apple's definitions, which in turn provides peace of mind that Profiles will instal on devices when associated. ## Apple Definitions Apple's developer pages list definitions of all payloads and as such, which keys are available within each payload; including, amongst other things, whether keys are required or optional. Below is the link to Apple's definition for the Lock Screen Message Payload and example content:For the keen eyed, the values provided for two of the possible keys contain parameters from inventory. This allows far more flexibility than fixed details.
macOS will react to all missing Payload Keys by applying default values
Below is an example for managing Finder:| **ShowExternalHardDrivesOnDesktop --** boolean If false, the system doesn’t show external hard drives on the Desktop. **Default**: true |
| **ShowRemovableMediaOnDesktop --** boolean If false, the system doesn’t show removable media items on the Desktop. **Default**: true |
| **WarnOnEmptyTrash --** boolean If false, the system doesn’t warn the user before emptying the trash. **Default**: true |
Building Profiles in FileWave should ensure you always have correctly configured Payloads.
## Custom Settings Prior to Profile Payloads, Apple had a mechanism known as Managed Preferences (MCX). These were either controlled using Apple Server or as with Profiles, could be installed locally on devices. In many ways, they are essentially the same thing; an xml structured file containing configuration. Despite Profiles taking over from MCX many years ago, MCX management still exists today in the latest macOS. The FileWave Profile Editor is able to leverage these and they are managed with the Custom Settings Payload. This means that not only can the OS be managed, but also provides a mechanism for controlling 3rd party Applications whose configuration is defined by this same implementation.Custom Settings have a slightly different format than Profiles. It is not possibly to directly import a Profile into a Custom Settings Payload
## Importing Profiles It is possible to find keys that are not defined by Apple, yet may still seem to function. As such, it would seem on face value, reasonable to add such keys to the Payload. Yet, FileWave only includes those that are defined by Apple, so how could this be possible? One method would be the use of Custom Settings, however it is possible to use FileWave to Import any Profile, either from another FileWave Server, built using an Editor or from another tool. There are though some important considerations when importing from other tools. ### FileWave Definitions As noted above, FileWave definitions are built from Apple's definitions. Additionally, FileWave will always configure **ALL** key/value pairs to default if not already defined. However, the flip side of this is that FileWave will also **REMOVE** any keys that are not part of the definition. ### Importing Undefined Keys If the Profile being imported contains keys that are not part of the definition, the Profile should never be altered or saved within FileWave.To avoid the need to save the Profile to be imported, drag and drop the Profile into FileWave Central Filesets view or use FileWave Anywhere to upload the Profile. Avoid duplication, as noted below.
The Profile, if opened, will not display unknown keys and if the payload only contains unknown definitions, it will appear as if it doesn't even exist within the Profile.This action will, as with all save actions with Profiles, causes all missing, but defined keys, to be added with default values, **whilst all undefined keys will be removed.**
## macOS GUI The macOS GUI does not always necessarily display the setting that is defined. In some instances, it may even look like it allows the user to alter the value, however, to the user it will appear not to work, since in reality it is managed. ## Undefined Keys Looking into plist files or binaries of applications, additional, undefined keys can sometimes be found. What's more, it may be possible to use these keys, either within an imported Payload or Custom Settings, with the desired effect. However, since they are undefined, it cannot be guaranteed that these settings will work on all versions of macOS.| **allowAirDrop --** boolean If false, the system disables AirDrop. Requires a supervised device. Available in iOS 7 and later, and macOS 10.13 and later. **Default**: true |
Remember, this is an undefined key and may not function as desired with all macOS versions.
FileWave no longer deploys a Web Clip version of the FileWave App Portal. The new version 2 Kiosk App's Bundle ID is: **com.filewave.ios.app.kiosk2**
[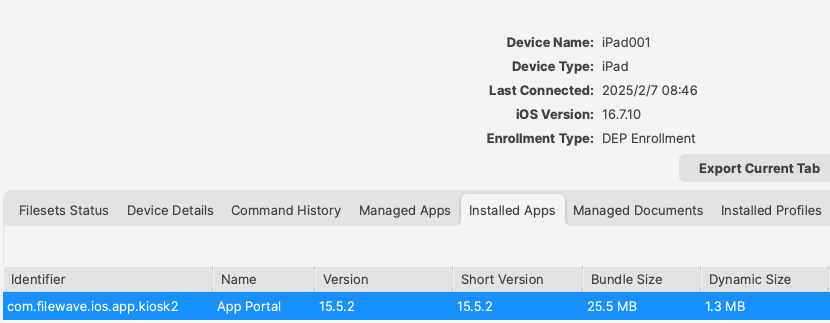](https://kb.filewave.com/uploads/images/gallery/2025-02/NmhtJGOVN2fg8eFe-image.png) For the new App, it may be referenced in a Home Screen Layout Payload by this Bundle ID: [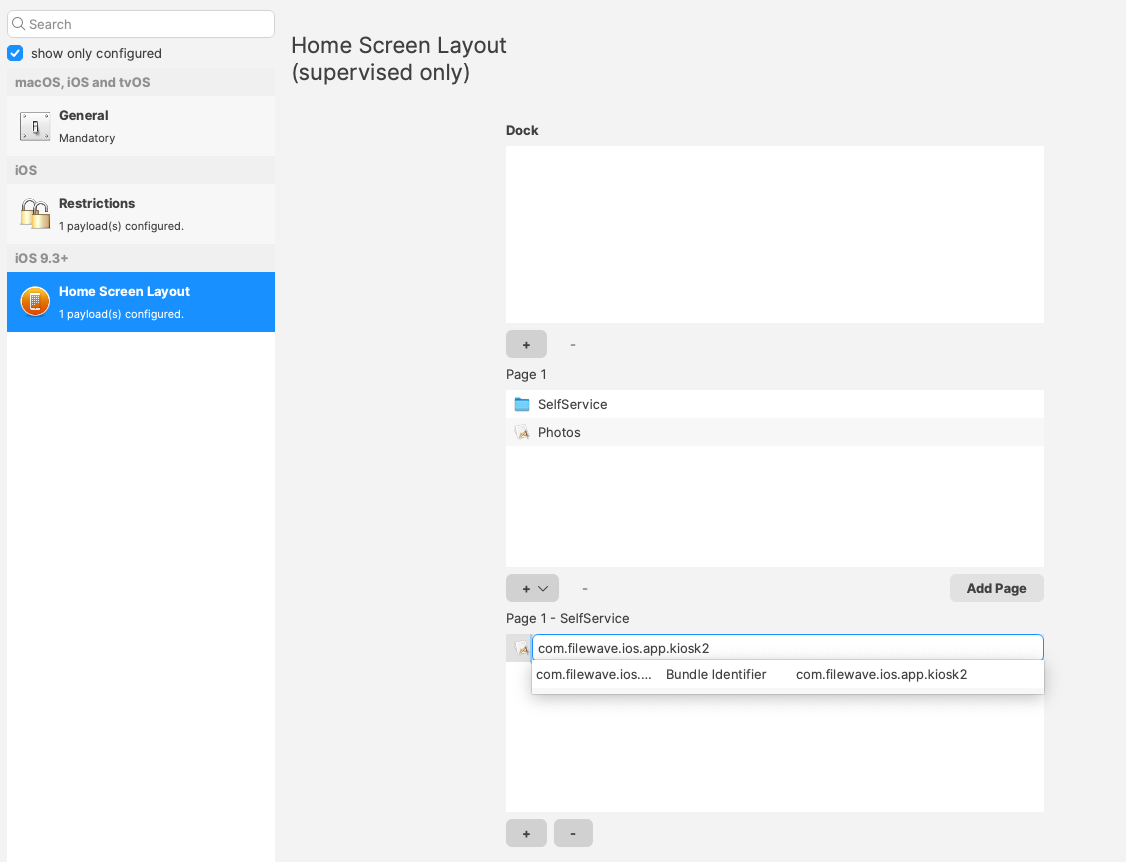](https://kb.filewave.com/uploads/images/gallery/2025-02/Oe9eYTAl96mzGc80-image.png)The below method for the Web Clip App Portal is legacy and will be removed from our KB at a later date.
To move the App Portal Web Clip using the Home Screen Layout Payload, locate the URL of the web clip from any iOS device settings: - Settings App > General > Device Management > FileWave MDM > More Details "Web Clip" as seen below: [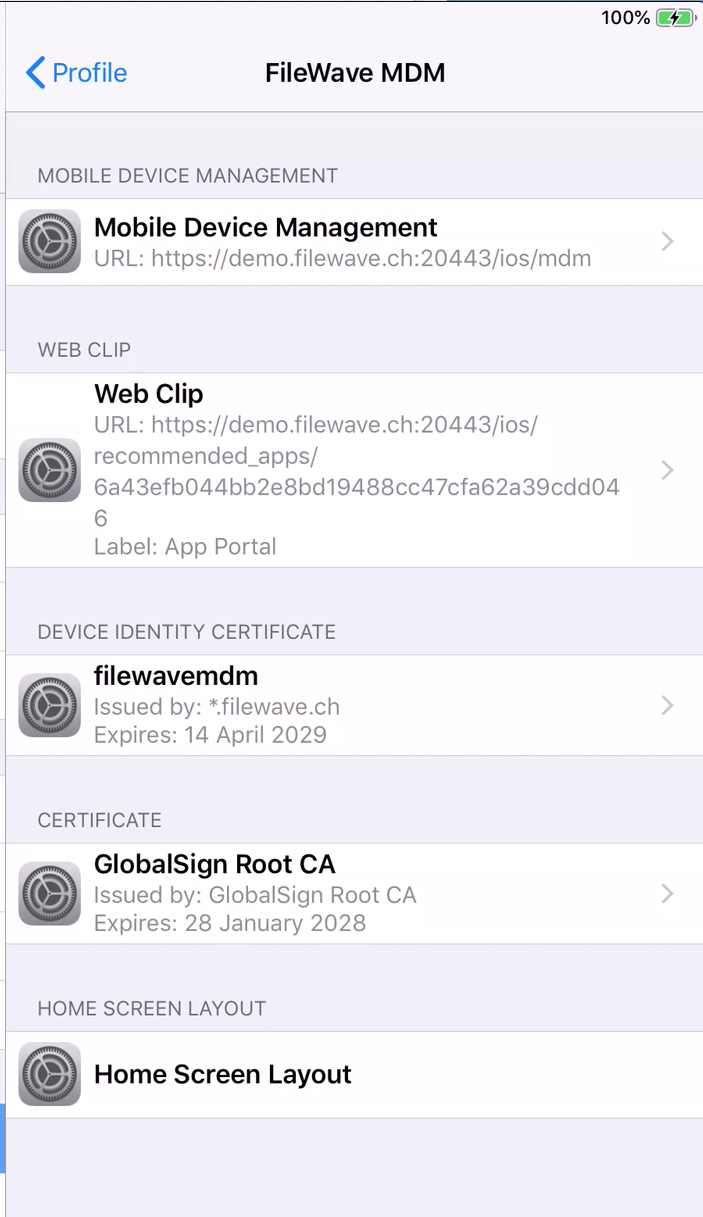](https://kb.filewave.com/uploads/images/gallery/2023-07/MaC6Lwm07yy15nJM-image.png) The Web Clip address shown should be injected into the Home Screen Layout Payload, replacing the long string of characters and numbers at the end with %device\_id% . In this example: ```bash https://demo.filewave.ch:20445/ios/recommended_apps/6a43efb044bb2e8bd19488cc47cfa62a39cdd04 ``` becomes: ```bash https://demo.filewave.ch:20445/ios/recommended_apps/%device_id% ``` Inject this into the home screen layout payload you are deploying, instead of an app name, and the App portal will be moved into that folder. [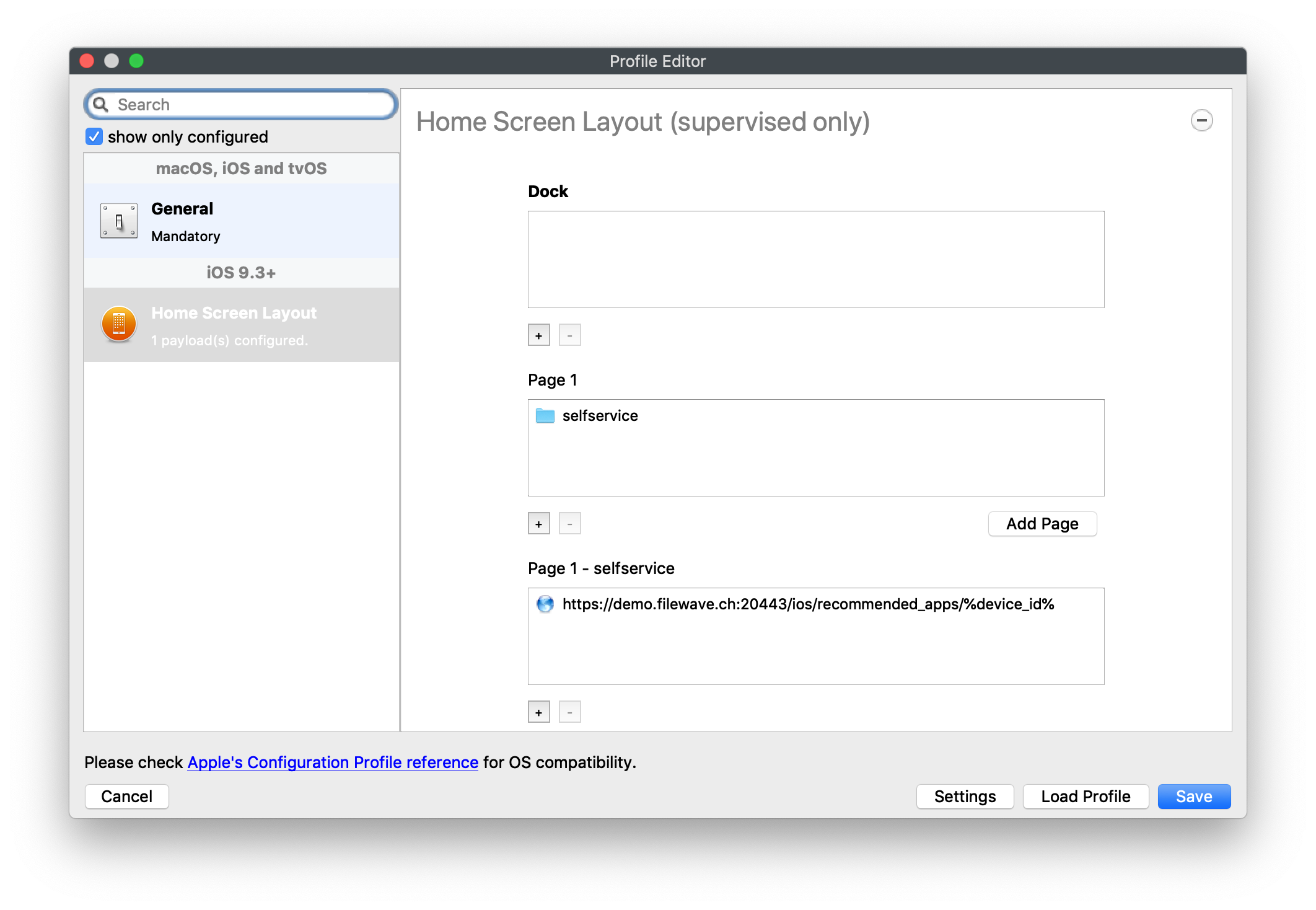](https://kb.filewave.com/uploads/images/gallery/2023-07/FLuMssbcS2BLJg9i-image.png) # Privacy Preferences Policy Control (TCC) ### Description Apple's TCC payload was introduced in FileWave 13 and controls the Privacy section of the Security & Privacy Preference. Since it was controlling the Security & Privacy tab, it was included in one single Security & Privacy Payload, when creating the Fileset. This, however, reduces flexibility of Privacy Payload distribution. FileWave 13.1 has addressed this. ### Information FileWave 13.1 separates the Privacy TCC payload from the Security & Privacy Preference in our Profile Editor, providing two Security & Privacy Payloads ##### Security & Privacy - iOS and macOS (10.7+) Including the tabs: General (macOS only), FileVault (macOS only), Firewall and Privacy [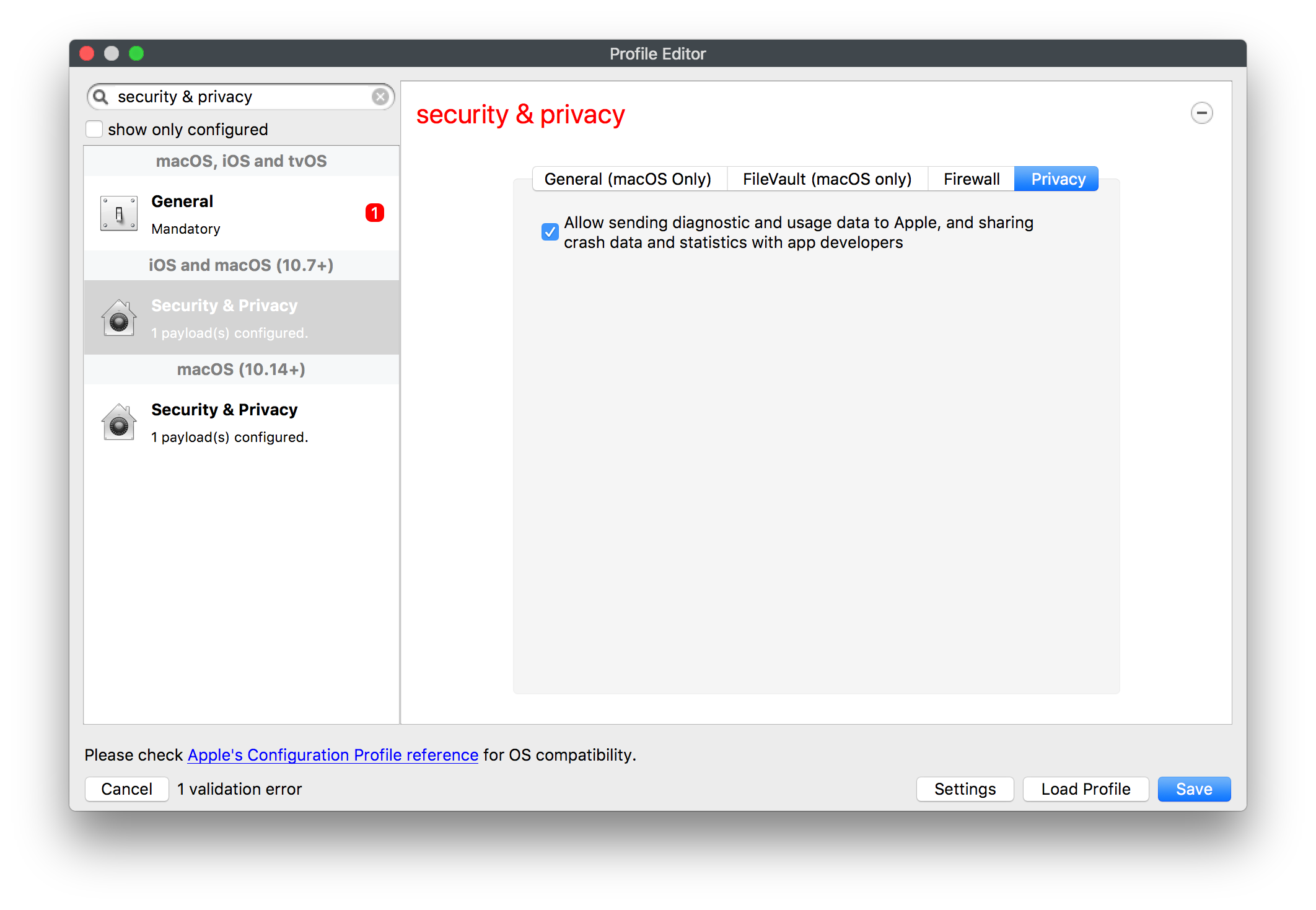](https://kb.filewave.com/uploads/images/gallery/2023-07/rQxKc9CNimap9GXo-image.png) ##### Security & Privacy - macOS (10.14+) Only includes the additional TCC Payload from within Privacy [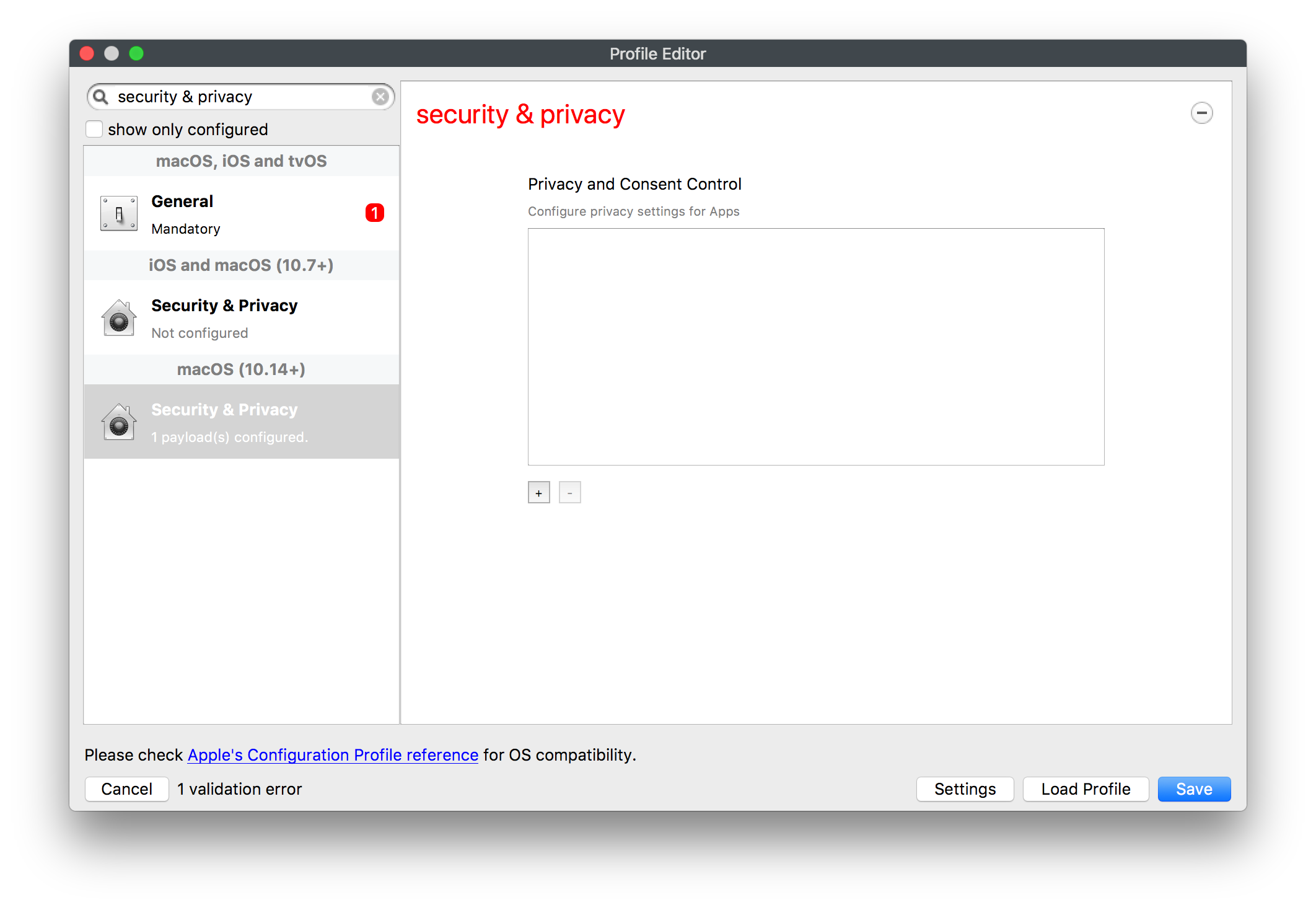](https://kb.filewave.com/uploads/images/gallery/2023-07/O6uvgizyCc0WxUXM-image.png) ### Upgrading to FileWave 13.1 For any existing payloads, created in 13.0.x, that included TCC Privacy Payloads, during migration to FileWave 13.1+ the Profile will be converted and will now show both Security & Privacy Payloads. It is highly recommended that two separate Profiles are created instead; one containing the General, FileVault and Firewall and the other containing the Privacy TCC Payload. With a separate TCC Privacy Payload, it is then possible to deliver multiple Privacy Payloads, providing greater granular control. # Apple Profile: ACME Certificate ## What The **ACME Certificate** profile is a new Apple Profile component introduced in **FileWave 15.5.0** and above. This feature allows administrators to configure and manage ACME (Automatic Certificate Management Environment) certificates on Apple devices directly through FileWave. With this profile, devices can automatically obtain and renew digital certificates from an ACME server, streamlining certificate management and enhancing security across your organization’s Apple devices. ## When/Why Use the ACME Certificate profile when you want to automate the deployment and renewal of digital certificates on managed Apple devices using **FileWave 15.5.0** or later. This is particularly useful for securing communications for services like HTTPS, Wi-Fi authentication, VPN connections, and email encryption. By leveraging ACME certificates through FileWave, you reduce administrative overhead, minimize the risk of service disruptions due to expired certificates, and ensure consistent security practices across all devices. ## How To configure the ACME Certificate profile in **FileWave 15.5.0** and above: 1. **Access the Profile Editor**: - Open the Profile Editor within the FileWave Central or Anywhere interface. 2. **Create a New Profile**: - Select the option to add a new profile. - Choose the **ACME Certificate** payload from the list of available Apple Profile components. 3. **Configure ACME Settings**: - **Directory URL**: Enter the URL of your ACME server (e.g., Let’s Encrypt). - **Client Identifier:** A unique string identifying a specific device (e.g., %udid%). - **Subject**: Specify the desired subject name for the certificate. (e.g., O=Company Name/CN=Foo). - **Additional Options**: Configure settings like key usage, extended key usage, and subject alternative names as required. [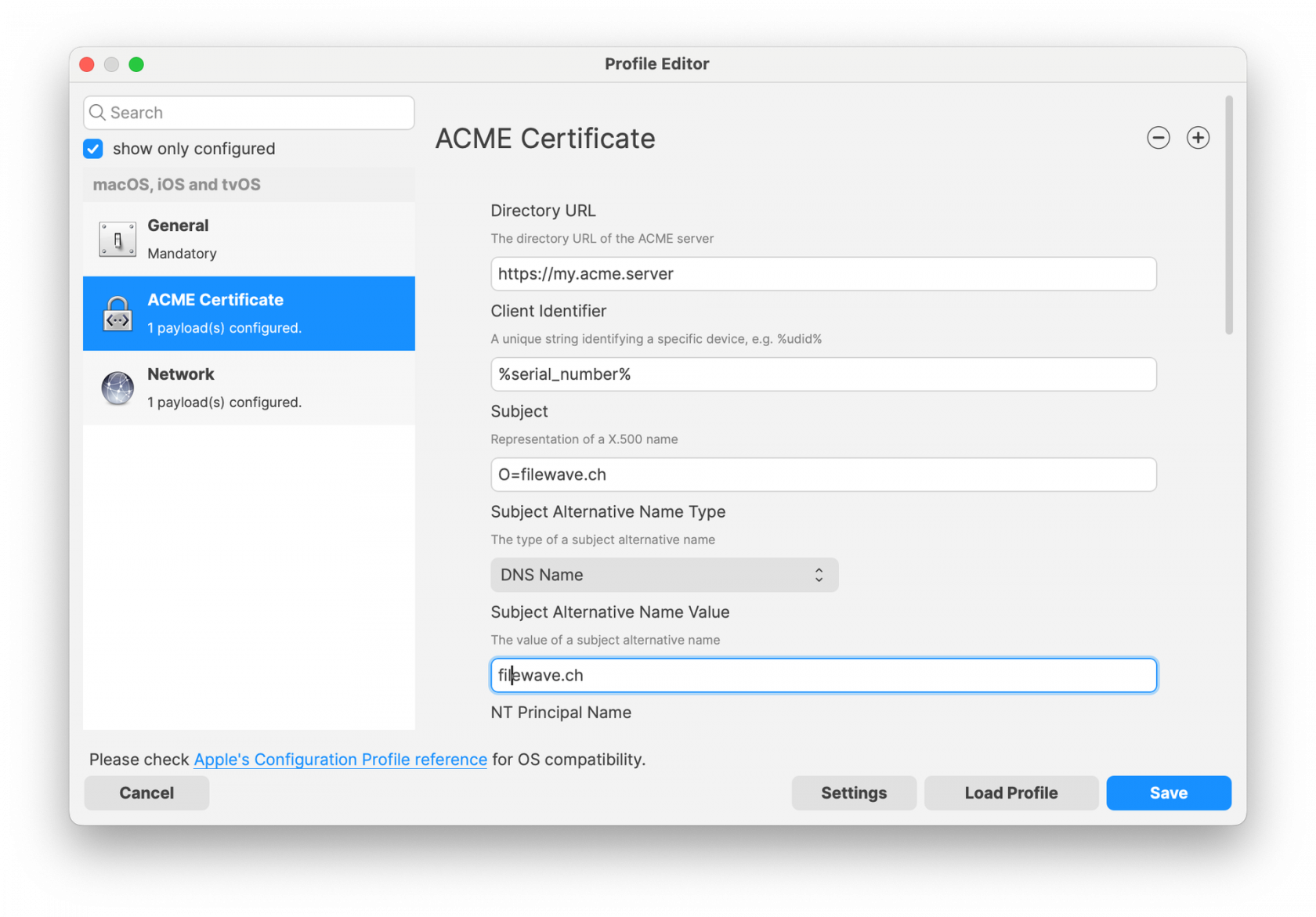](https://kb.filewave.com/uploads/images/gallery/2024-10/HzEdZvtfcjq3savt-image.png) 4. **Reference ACME Payload in Other Profiles**: - Other payloads, such as the **Network** payload, can reference the ACME Certificate payload, similar to how they would reference SCEP payloads. - This allows services like Wi-Fi configurations within the Network payload to utilize the ACME-issued certificates seamlessly for authentication. [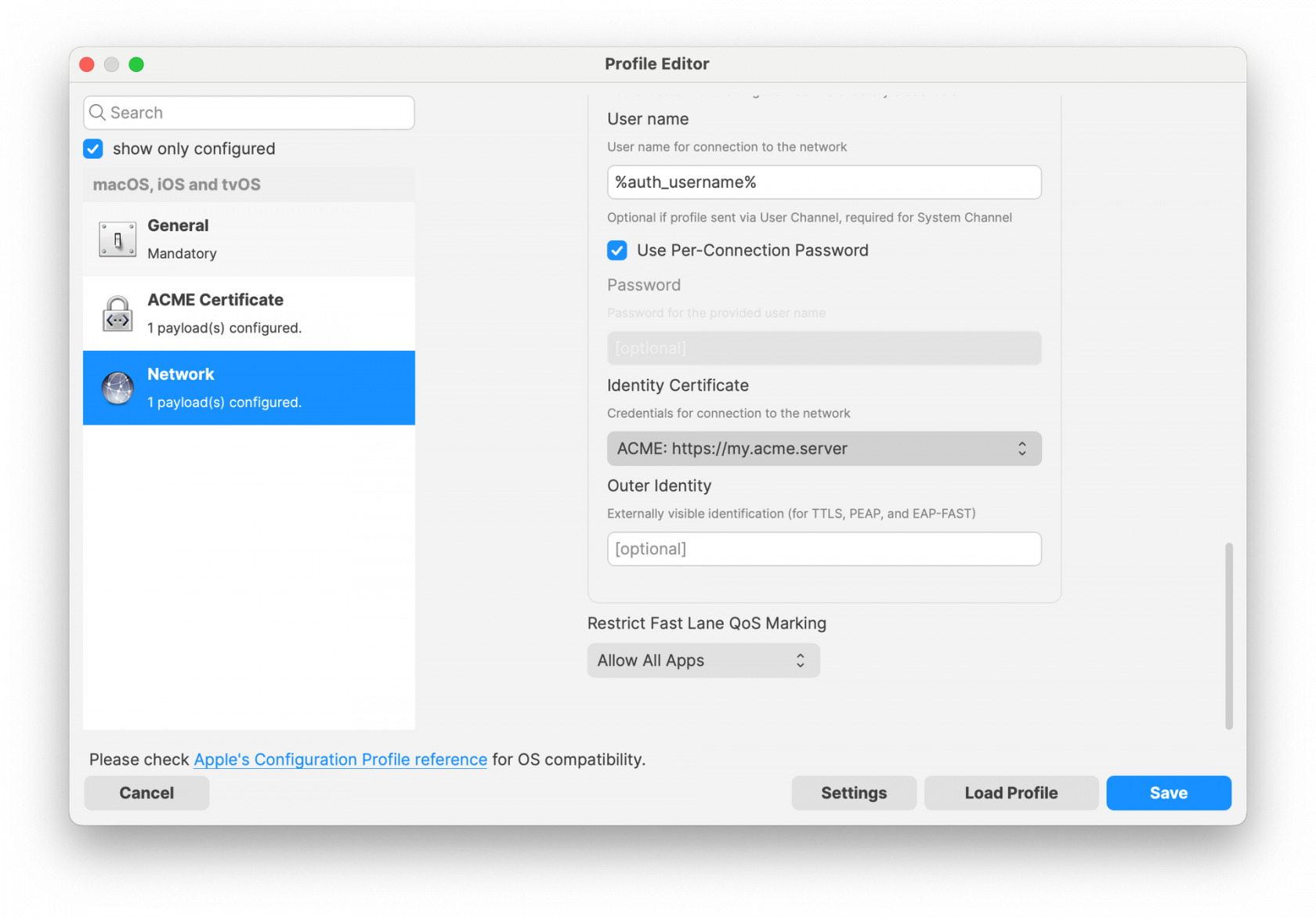](https://kb.filewave.com/uploads/images/gallery/2024-10/06EWmVBdfz8Wsc2y-image.png) 5. **Save and Deploy**: - Ensure all required fields are completed correctly. - Save the profile and deploy it to the target Apple devices managed by **FileWave 15.5.0** or later. **Note**: The ACME Certificate profile is supported on devices running macOS 10.15 and later, iOS 14 and later, and iPadOS 14 and later. All profiles are signed according to the latest Apple requirements to ensure integrity and authenticity. ## Related Content - [ACME Certificate Profile Documentation](https://support.apple.com/guide/deployment/automated-certificate-management-environment-depb95c66a07/1/web/1.0) ## Digging Deeper With the introduction of the ACME Certificate profile in **FileWave 15.5.0** and above, administrators can now integrate automated certificate management into their Apple device management workflows more efficiently. The ACME protocol automates interactions with certificate authorities (CAs), such as Let’s Encrypt, to provision certificates without manual intervention. A significant advantage of the ACME Certificate profile is its ability to be used alongside the **Network** payload within an Apple Profile. This means you can configure Wi-Fi or Ethernet settings in the Network payload and reference the ACME Certificate for authentication purposes. By doing so, devices can automatically obtain the necessary certificates for secure network access, streamlining the onboarding process for network services. By allowing other configuration profiles to reference ACME payloads similarly to SCEP payloads within FileWave, you create a cohesive and efficient system for managing certificates across various services. This approach ensures that all network services relying on digital certificates have access to valid, up-to-date certificates, enhancing both security and user experience. Implementing ACME certificates through FileWave 15.5.0 also contributes to cost savings by utilizing free certificate services like Let’s Encrypt, eliminating the need for purchasing certificates from traditional CAs. Additionally, the automatic renewal feature reduces the administrative burden on IT staff and mitigates the risk of service outages due to expired certificates. As security threats continue to evolve, automating certificate management with ACME profiles in **FileWave 15.5.0** is a proactive step toward safeguarding your organization’s data and communications. Regularly reviewing and updating your certificate policies in line with industry standards will further strengthen your security posture. # Profile Editor Command Policy ## What The Command Policy in the Profile Editor is unique; the contents of a Command Policy is not a profile payload, but instead MDM commands. ## When/Why Some commands are available from the right click context menu, e.g. Wipe Device…. However, some commands would be unwieldy in this manner e.g. iOS Wallpaper. Imagine having hundreds or thousands of devices or if you wanted different Wallpaper based upon location, department, etc. To provide this flexible working, some commands have been placed inside the Profile Editor and all these commands exist within the Command Policy view. This method allows the association of such commands based upon Smart Groups, for example, and allows easy association across many devices.Since these are commands and not Profile Payloads, there will be: \* No request type of ‘InstallProfile’ listed in the Command History \* These will not be listed in the ‘Installed Profiles’ view. \* There will be no Fileset Report for these Command Policies \* The Fileset Status will remain grey and only ever report Associated However, any commands sent should be seen in the Command History view with a request type of ‘Settings’
#### Additional Consideration Some command options allow for enabling or disabling a setting, for example Remote Desktop. In this instance, if a currently associated Command Policy included a setting to enable this feature, a disassociation event should automatically send a command to disable the setting.Some commands are re-sent periodically, e.g. Wallpaper. This command will be re-sent in case the user has changed the Wallpaper, but only re-sent every 24 hours by default, to alleviate undue load on the server. Other commands may be re-sent with a manual Verify.
## How - Open the Profile Editor - Select Command Policy - Edit as desired - Associate to test device(s) first before deploying across many devices Example Command History view for a setting to alter the Wallpaper: [](https://kb.filewave.com/uploads/images/gallery/2023-07/78Ddjnw8Yd3TZ9hs-image.png) # Apple Profile: System Logging ## What The System Logging Profile is a new feature added to the Profile Editor in the web interface, mirroring the functionality available in Central Admin. This profile empowers administrators to configure system logging settings on macOS devices, including enabling private data logging and managing subsystem logging configurations. It provides granular control over what system events are logged, facilitating better monitoring and troubleshooting. ## When/Why Utilize the System Logging Profile when you need detailed insights into system behaviors for diagnostics, security audits, or compliance purposes. It's especially beneficial for troubleshooting complex issues, monitoring system performance, and ensuring that logging practices meet organizational policies or regulatory requirements. ## How Some details about the new macOS Profile for System Logging; **Key Features:** - **Enable Private Data Logging**: A checkbox to enable or disable private data logging for the entire system. Default is unchecked. - **Subsystem Logging Configuration**: A table for configuring logging behavior for subsystems. You can add new configurations with unique identifiers and set logging categories, enabling, and persisting options. - **Modal Configuration**: When adding or editing subsystem logging configurations, you can specify: - **Subsystem Identifier**: A required, unique identifier. - **Logging Categories**: Add and configure categories with enable and persist options. - **Additional Settings**: Configure key-value pairs for each item. - **Validation**: The Save button is enabled only when all required fields are correctly filled. An empty profile cannot be saved. - **Editing**: Post-creation, you can edit the entire profile or individual subsystem logging configurations. The new System Logging Profile supports macOS 10.12 and later versions. All Apple profiles are signed as per the latest updates. [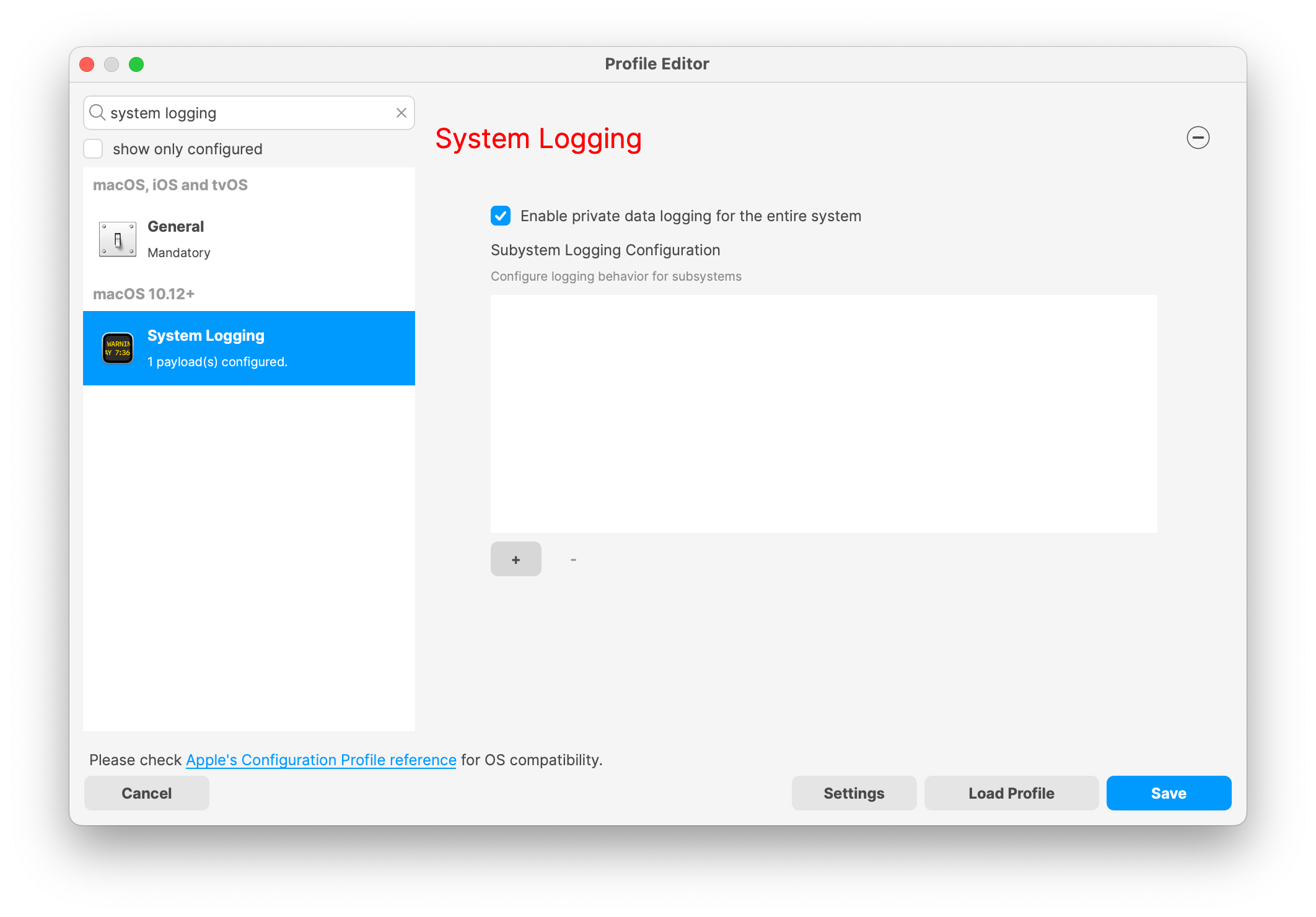](https://kb.filewave.com/uploads/images/gallery/2024-10/MmggpY5eC5s7F1Jd-image.png) ## Related Content - For more details, refer to the Apple documentation on [System Logging](https://developer.apple.com/documentation/devicemanagement/systemlogging "https://developer.apple.com/documentation/devicemanagement/systemlogging") ## Digging Deeper The System Logging Profile provides a powerful tool for administrators to fine-tune logging practices on macOS devices. By customizing subsystem identifiers and logging categories, you can focus on capturing relevant data while minimizing unnecessary log noise. This is crucial for effective system monitoring and can significantly aid in proactive issue resolution. # Profile Editor details for Apple The primary management tool for client management / MDM on iOS and macOS X is the Profile Editor. It can be accessed through either the Desktop Fileset or Mobile Fileset tool. [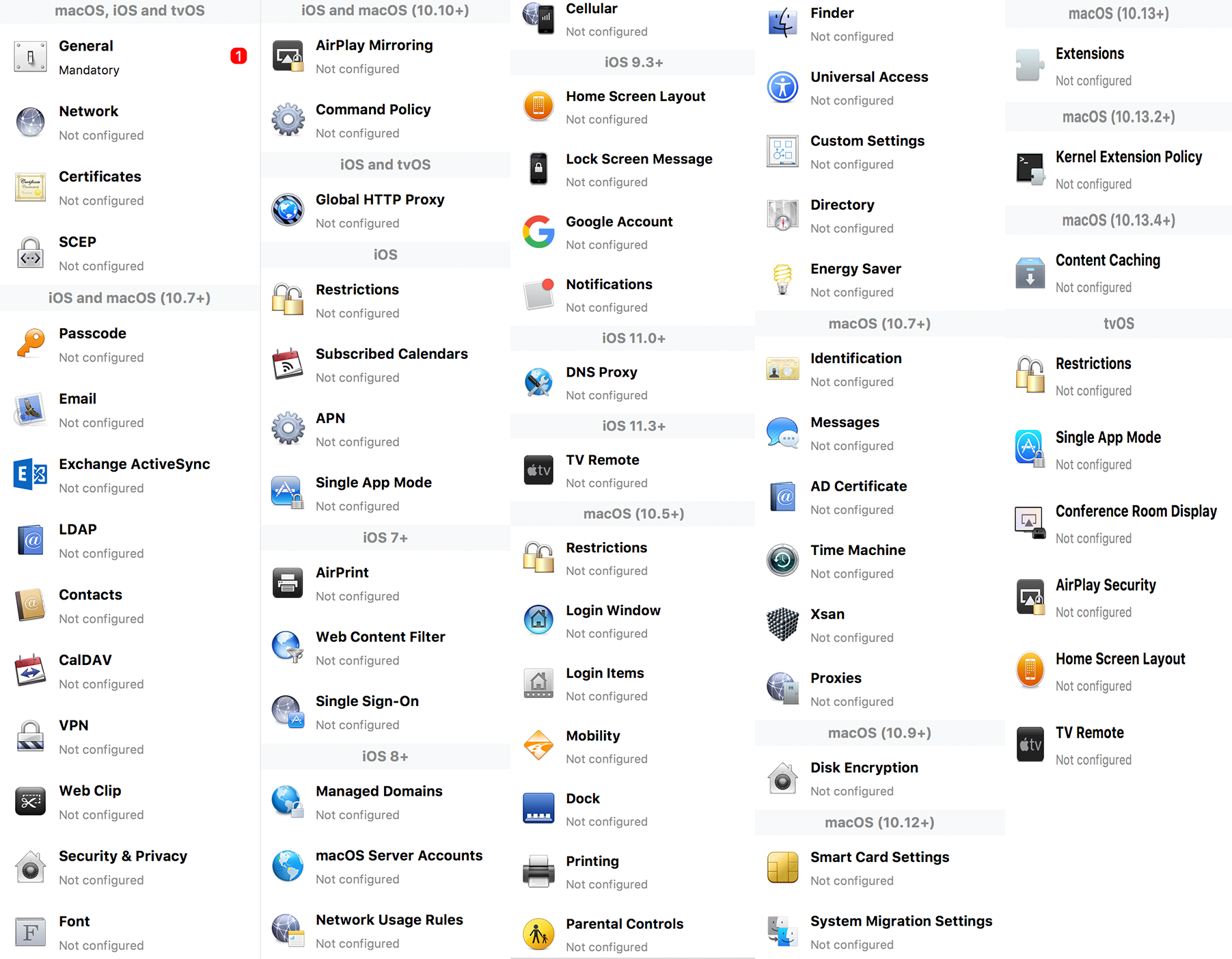](https://kb.filewave.com/uploads/images/gallery/2023-07/aI8S2C366Y4LEgN5-image.png) ## Search and Show only configured (FW 10+) Two features introduced in FileWave 10 are a search field to locate specific settings and the ability to display only the configured payloads in a profile. ## macOS, iOS and tvOS ### General The first item encountered in Profile Editor is the **General** settings. This is not a profile nor payload type; it's a header for any profile to be created. Best practice for profiles is to create a single payload setting within each profile, giving it an descriptive name in the General settings. The key settings to note are the **Name, Security** and **Automatically Remove Profile**. All other General settings are optional. You must give the Profile a name for tracking purposes. The **Security** setting lets you decide if the profile can be removed by the end user or not. Users on unsupervised iOS devices can remove profiles regardless of the settings here. [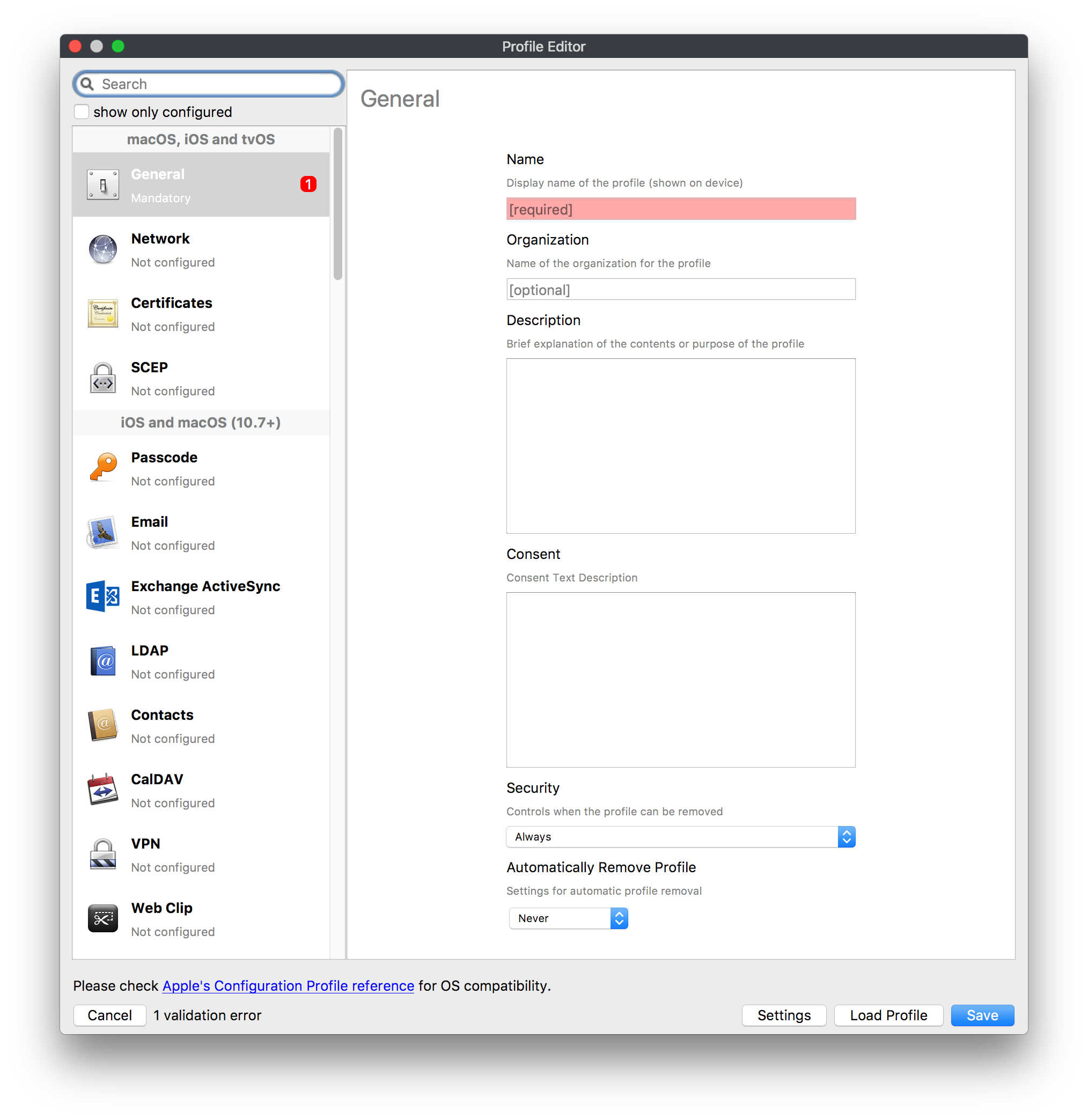](https://kb.filewave.com/uploads/images/gallery/2023-07/AOzOSpJfqibKTSa0-image.png) **Note:** Due to changes in how profiles are installed on OS X 10.10+, if you install a profile with Security set to *Never,* FileWave will not be able to remove the profile and will ask for admin credentials on the client machines. The workaround is to use a password protected removal using the *With Authorization* option. **Automatically Remove Profile** settings will disable the profile after a specific time interval or on a specific date. The recommendation is to leave this set to *Never* and use FileWave to remove the profile when necessary. The **Description** and **Consent** fields are used to provide more detail for troubleshooting purposes, and to display a text block asking the user to agree to the content of the Consent text when installing this profile manually. If the profile is installed as part of a FileWave Fileset, the end user will not see this, however. ### Network [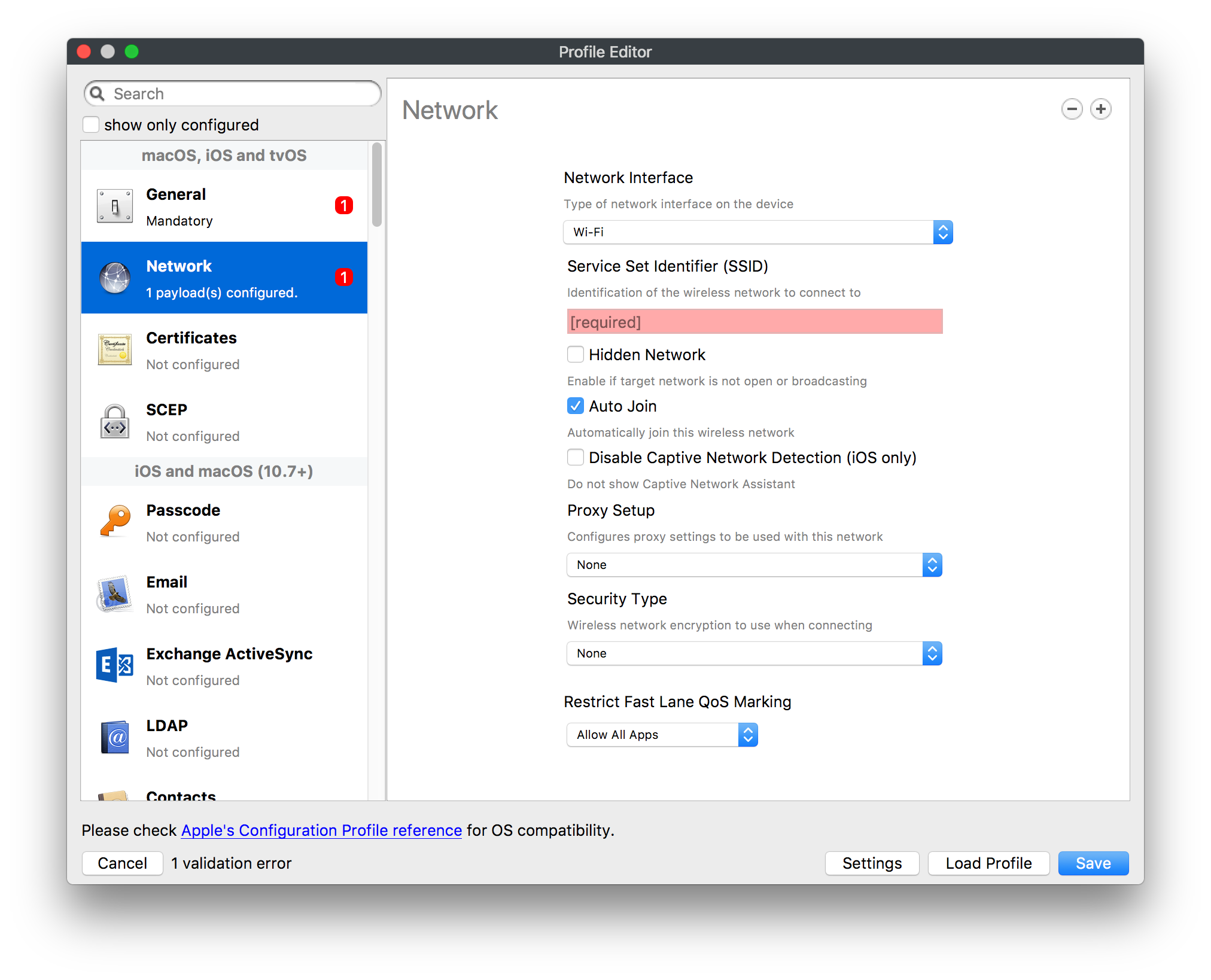](https://kb.filewave.com/uploads/images/gallery/2023-07/Fo0jqIxOLF7717ui-image.png) [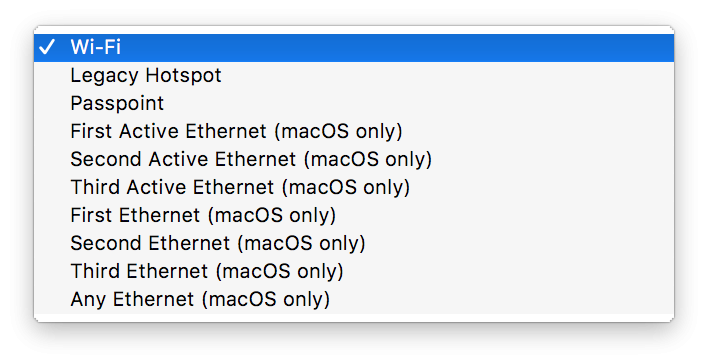](https://kb.filewave.com/uploads/images/gallery/2023-07/GMOdLRPDcoqtqpZJ-image.png) This payload allows you to preconfigure network settings for your devices. You can define Wi-Fi, Legacy Hotspot, Passpoint, or Ethernet (macOS only) settings, including Auto Join, Proxy, Wi-Fi Security, and 802.1x. ### Certificates [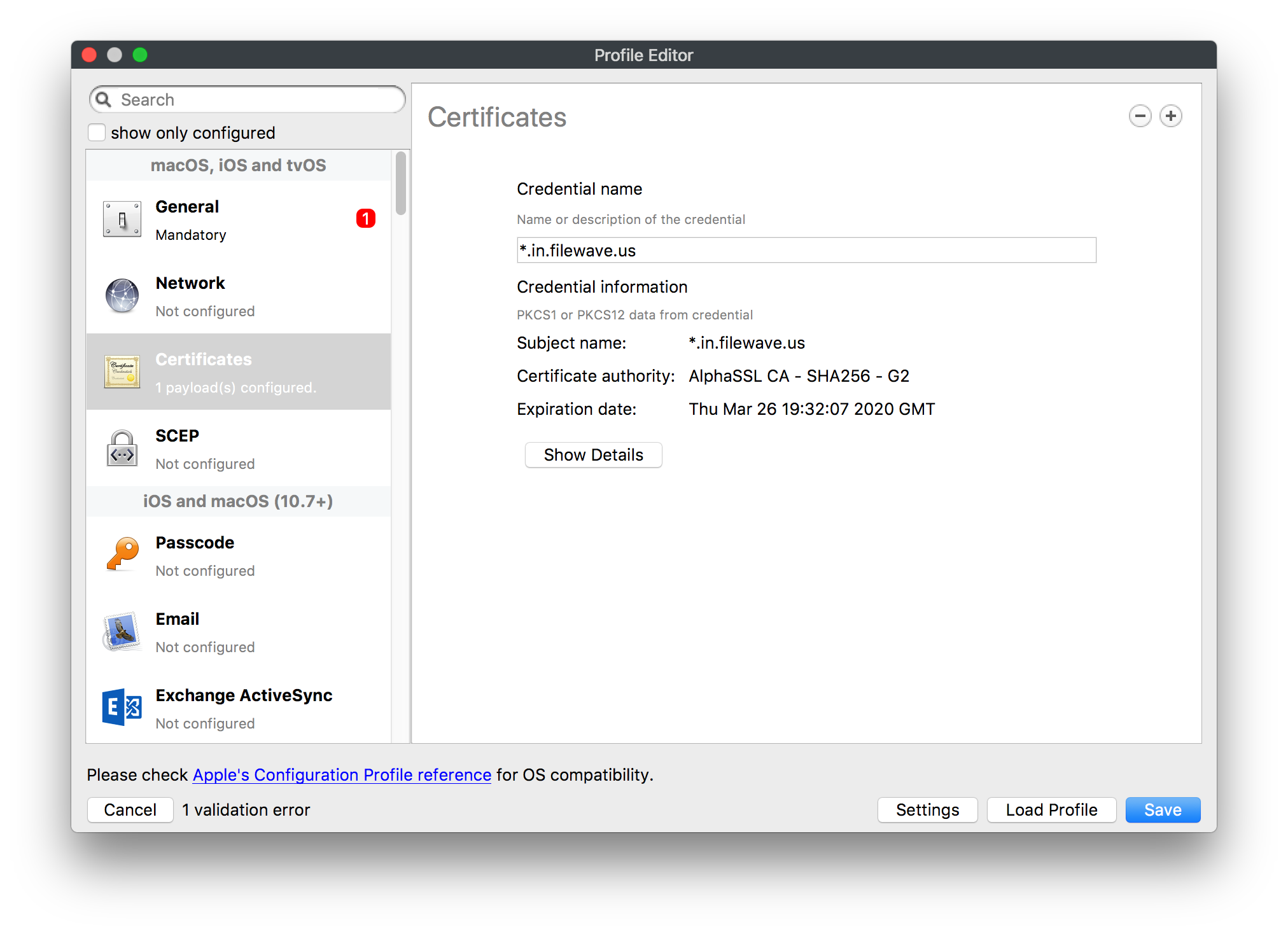](https://kb.filewave.com/uploads/images/gallery/2023-07/6q9R1fNoLKYjqnaG-image.png) The Certificates payload lets you designate PKCS1 or PKCS12 certificate data to be stored on managed devices. You can specify institutional certificates or any other certificates required for access to your network services. ### SCEP [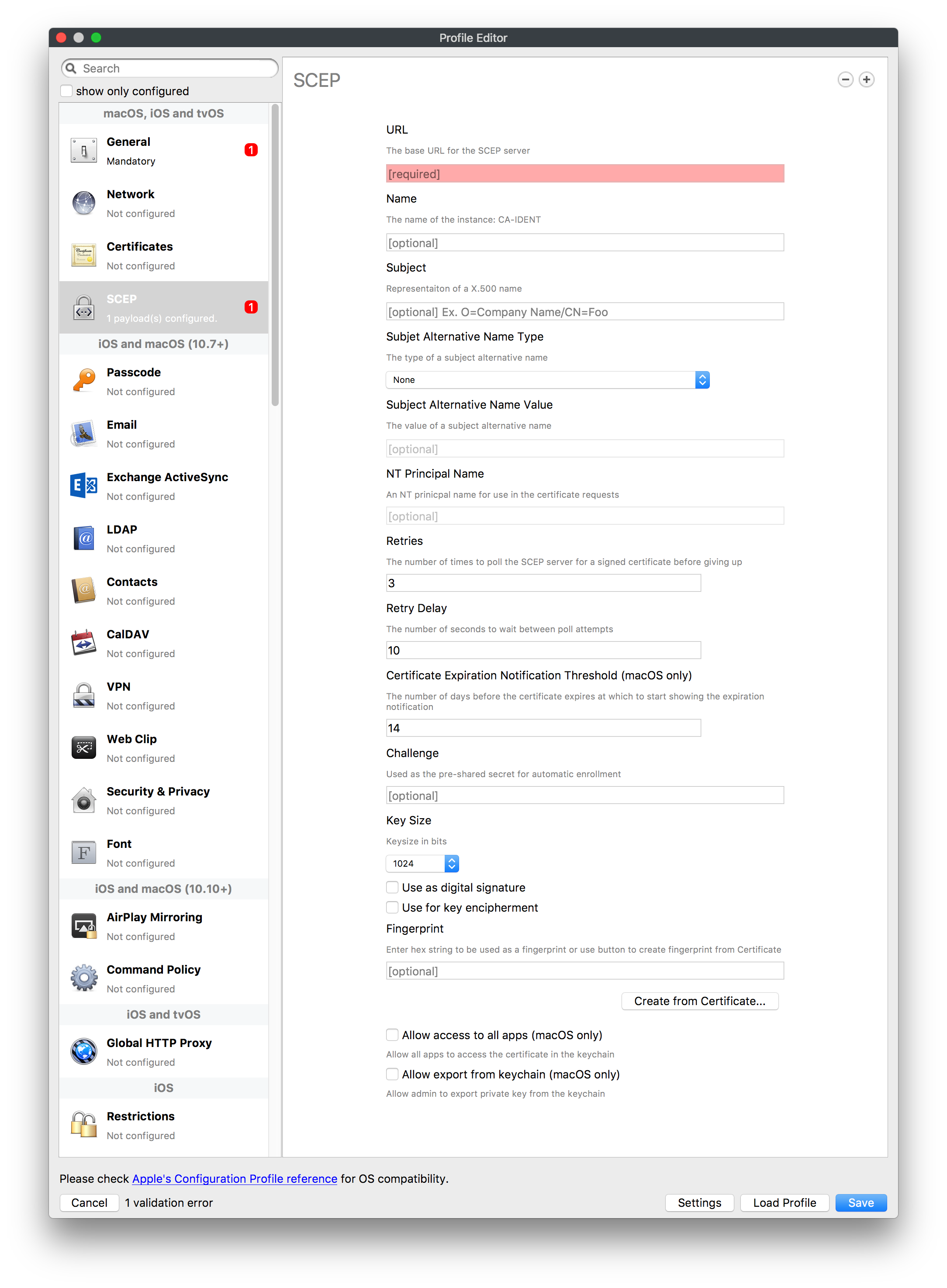](https://kb.filewave.com/uploads/images/gallery/2023-07/qPCxoO3duHdWx2Zj-image.png) The SCEP, or Simple Certificate Enrollment Protocol, payload is used to define the X.500 information needed by an institution for a connected device. You may also import a certificate to provide all the needed settings. ## iOS and macOS (10.7+) These settings are unified and can apply to any supported iOS device as well as any OS X device running 10.7 Lion or higher. ### Passcode [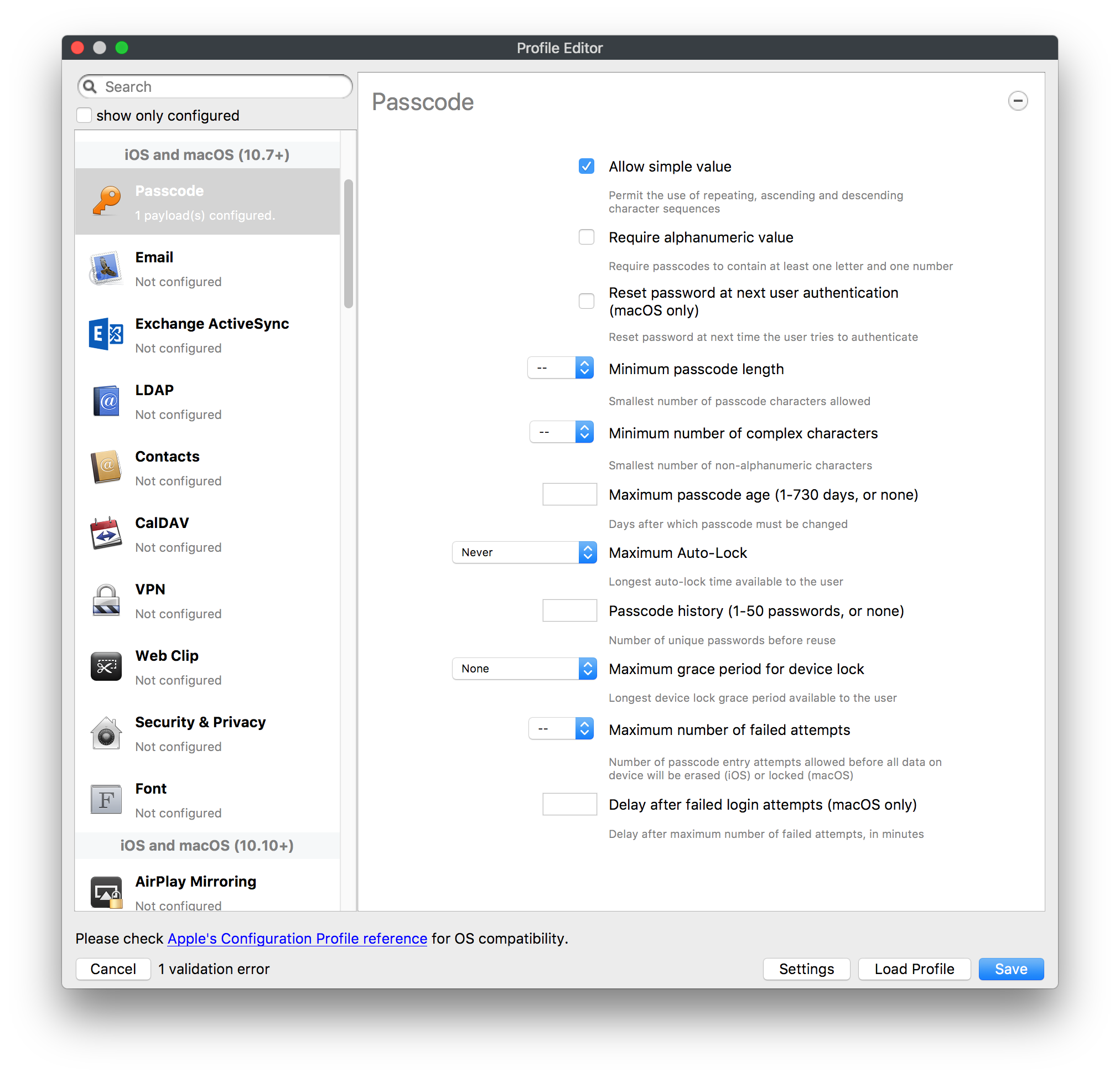](https://kb.filewave.com/uploads/images/gallery/2023-07/xRJTJIM233MZHlsR-image.png) Passcode allows you to establish a more complex passcode rule for end users, including requiring a minimum length, alphanumerics, and time limits. A few of the key settings are: - Maximum passcode age: requires user to change passcode within defined timeframe - Auto-Lock: defines the amount of time the device can be idle before it locks - Grace period for device lock: defines the amount of time after the device locks before a passcode is required ### Email [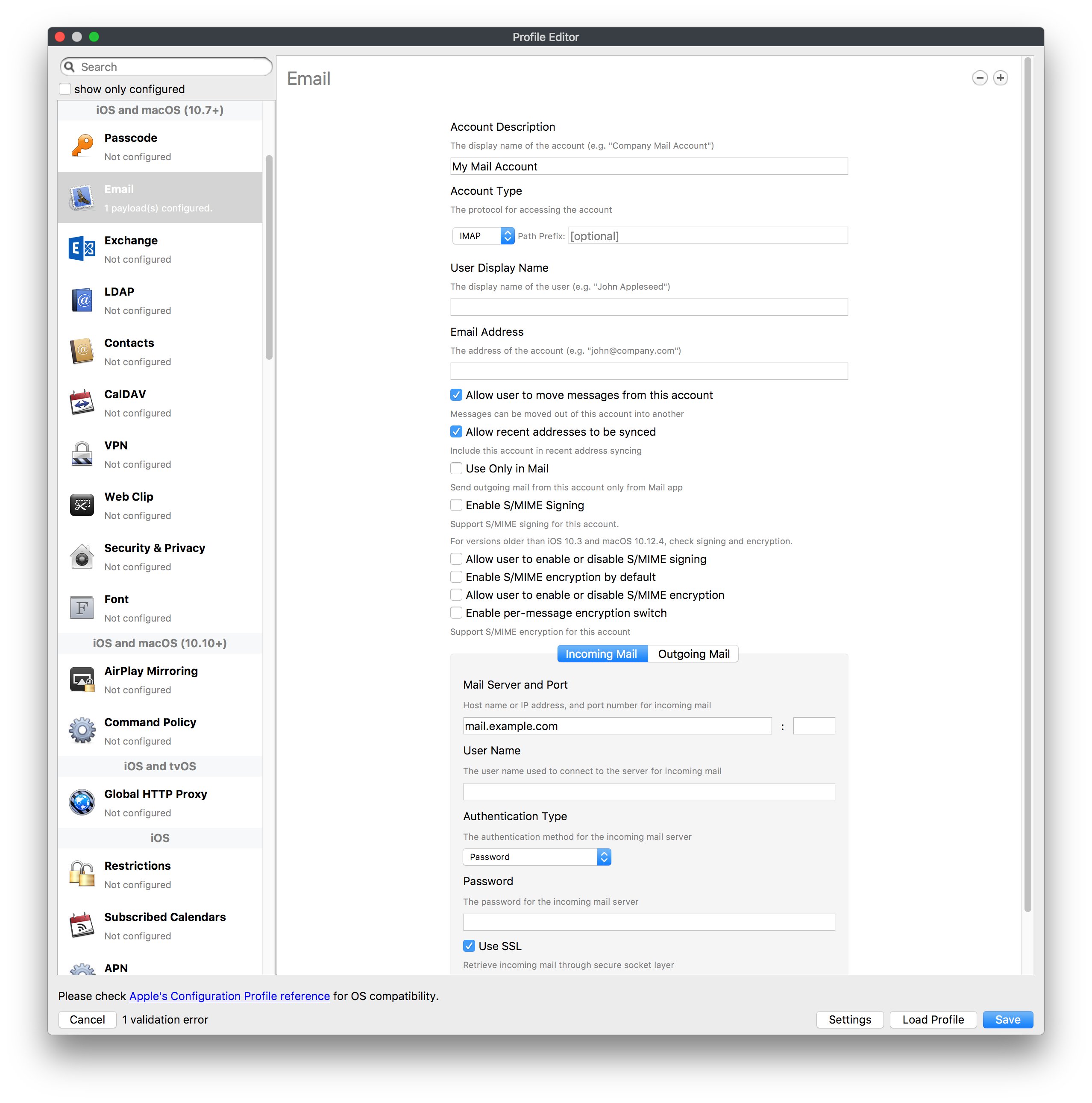](https://kb.filewave.com/uploads/images/gallery/2023-07/Hvnjz8JsFoLle57G-image.png) Email settings allow the systems administrator to predefine key SMTP or IMAP settings for users, such as host server, requirement to use only a defined server for sending mail, use of S/MIME, and SSL. This is one of the profiles that can be configured for parameterized profile settings if the client device is associated with an LDAP directory. ### Exchange ActiveSync [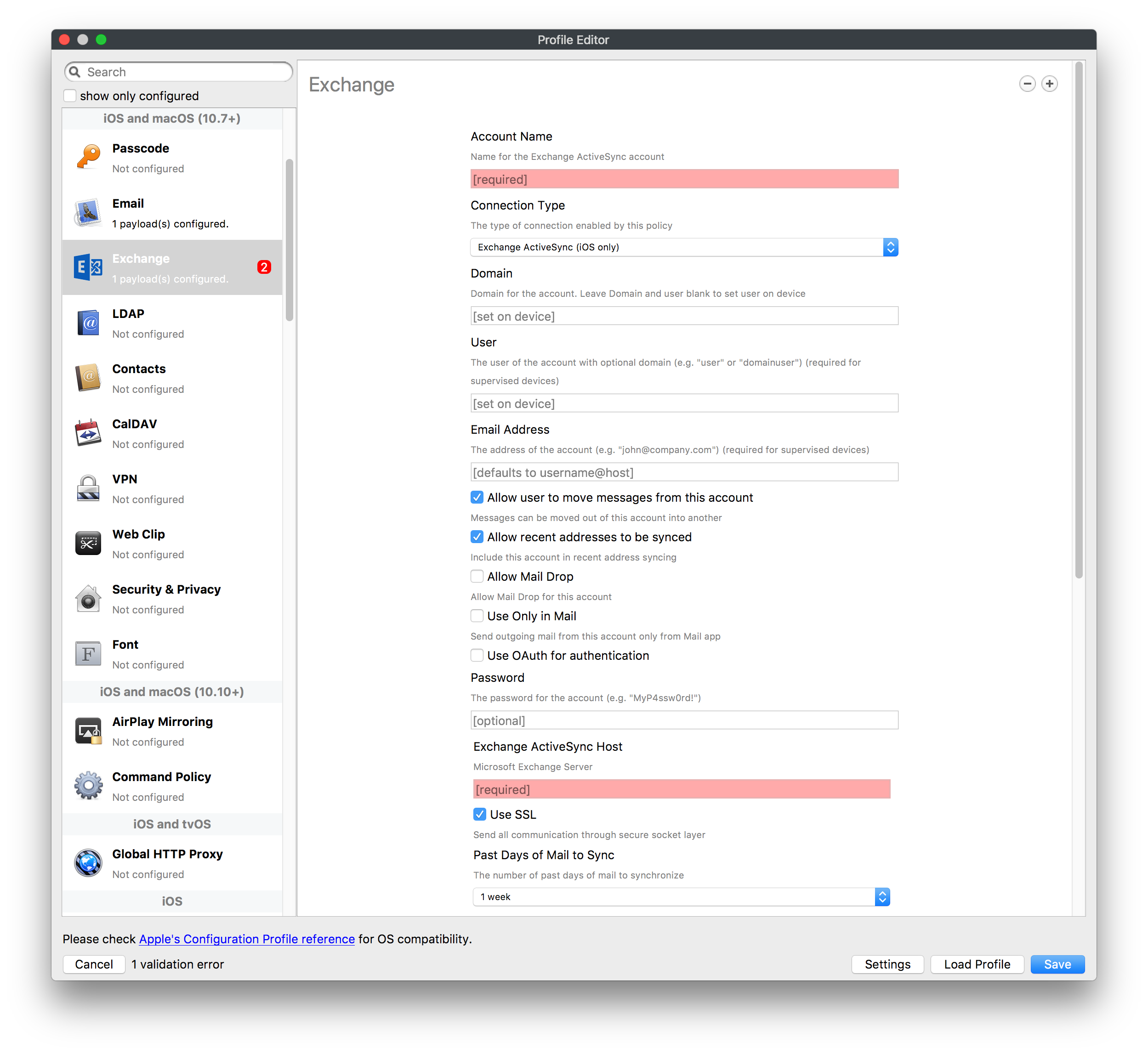](https://kb.filewave.com/uploads/images/gallery/2023-07/aXHmHqD0n05Oud5C-image.png) [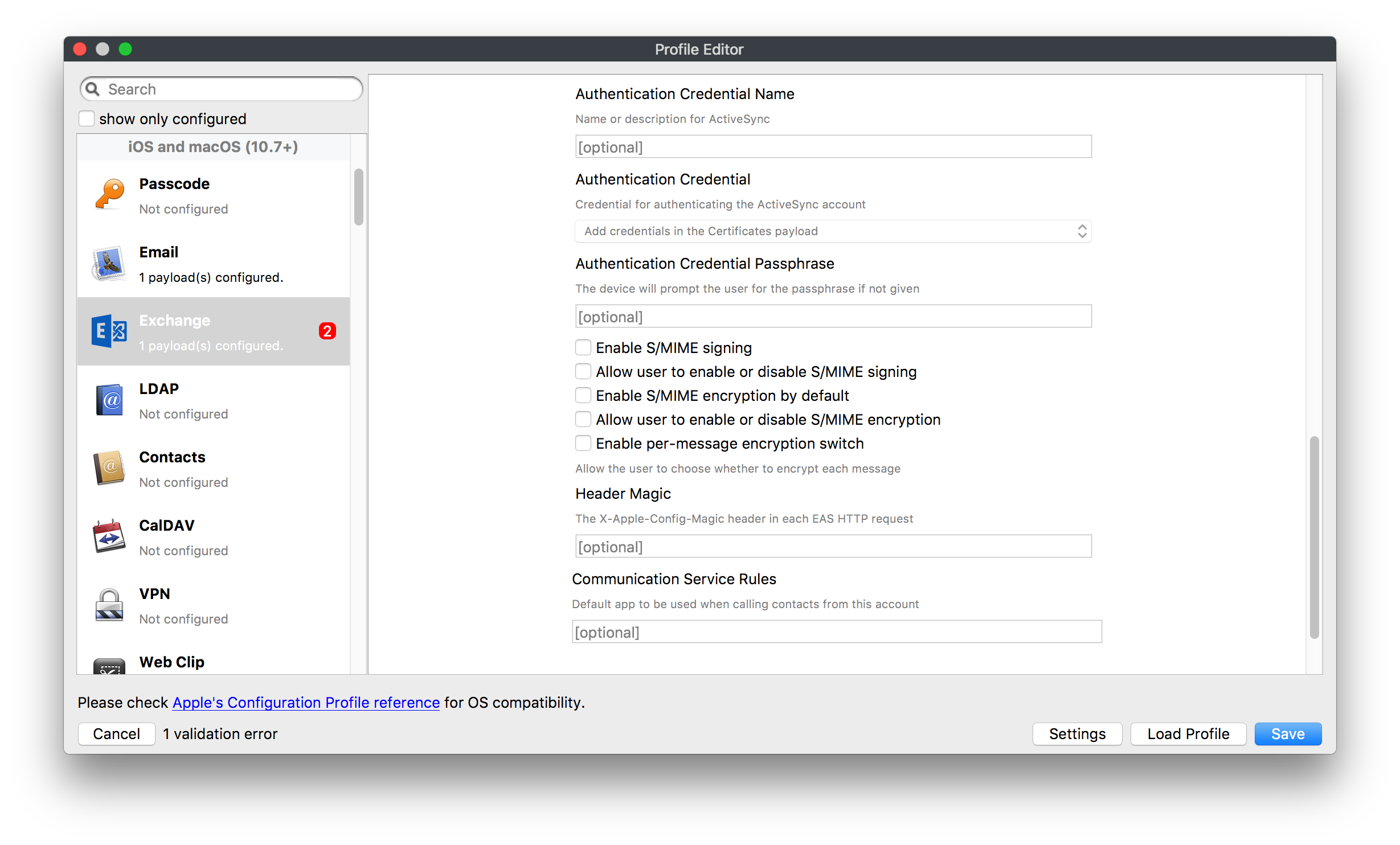](https://kb.filewave.com/uploads/images/gallery/2023-07/ep23l4IpHKN5mDLv-image.png) Exchange ActiveSync is a payload that lets you predefine settings for users' access to Microsoft Exchange services. New with FileWave 11's support for iOS 9.3 is an "Allow Mail Drop" option for the Exchange payload (Mail Drop lets you send large files like videos, presentations, and images through iCloud. For more info, see: [https://support.apple.com/en-us/HT203093](https://support.apple.com/en-us/HT203093). ### LDAP [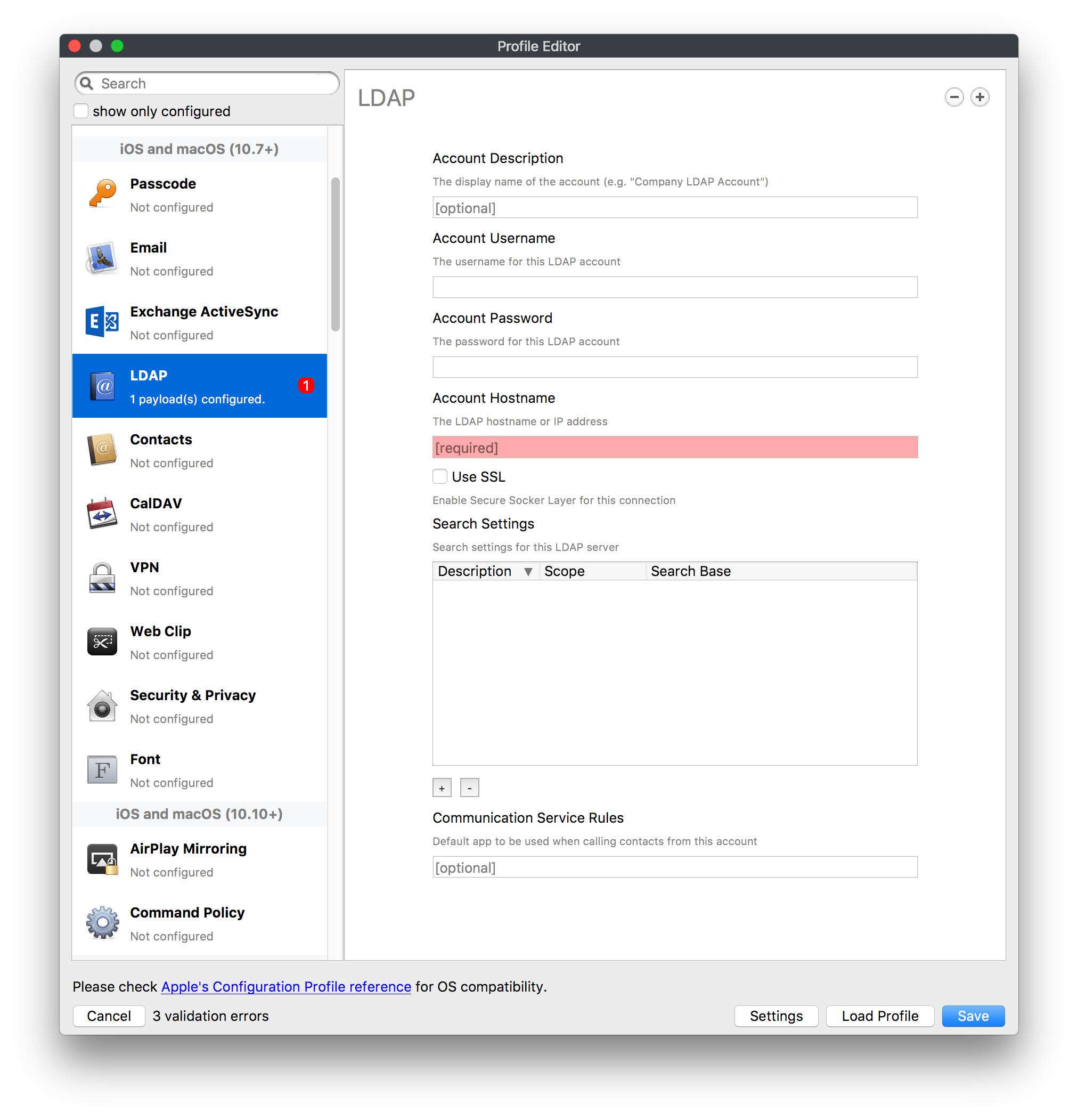](https://kb.filewave.com/uploads/images/gallery/2023-07/x7eNWt1v9JvRq2jd-image.png) The LDAP payload provides the ability to link the device to an LDAP server for lookup and configuration access. You can provide authentication for secure server access, or use just the hostname to gain anonymous access to the network directory. Some of the settings include SSL usage and search criteria. This is not a binding profile since iOS devices cannot be bound to a network directory. For macOS computers, use the Directory payload for binding. ### Contacts [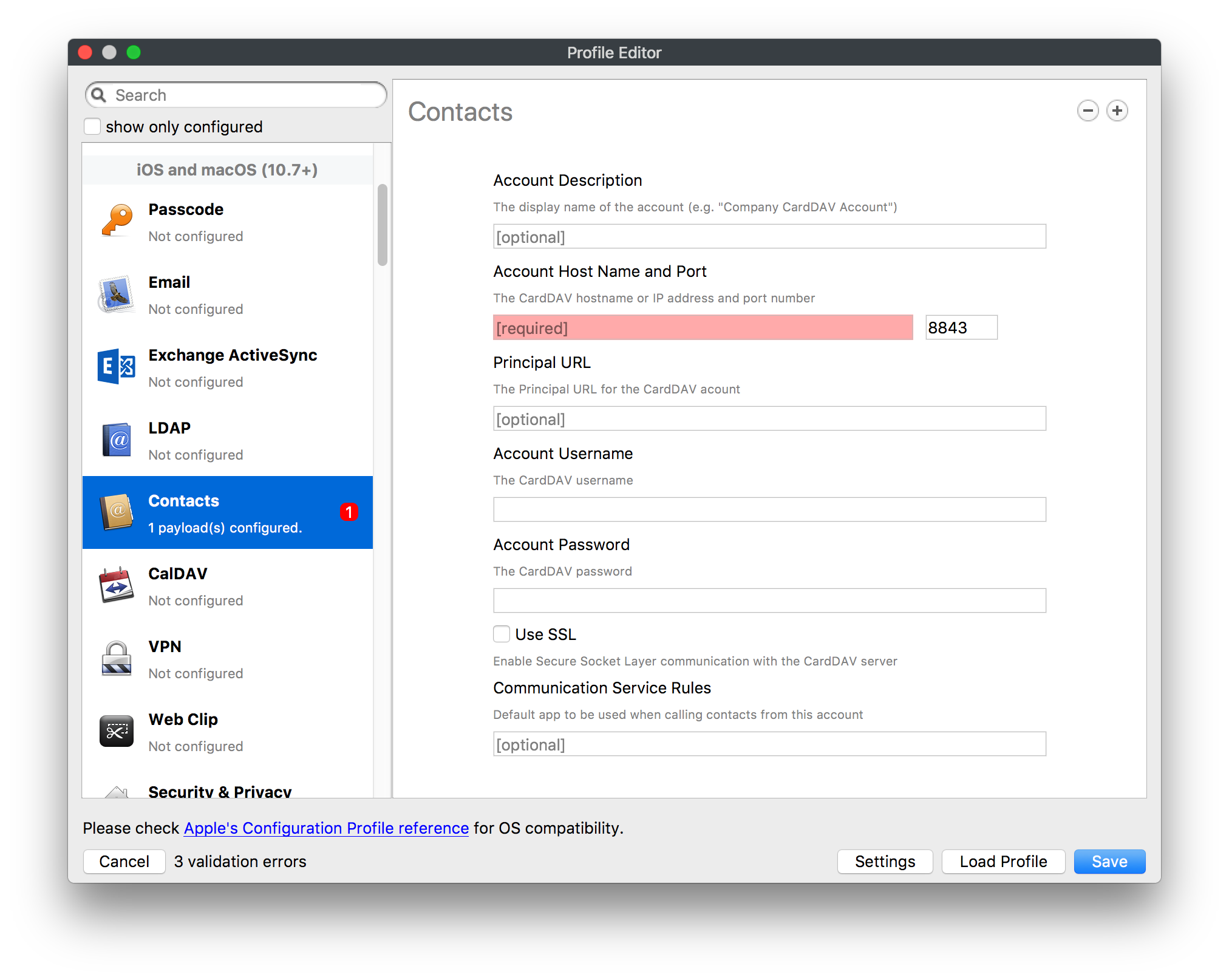](https://kb.filewave.com/uploads/images/gallery/2023-07/2W2jKvTKUGIZ8DjR-image.png) The Contacts payload provides settings to allow access to CardDAV servers. This payload supports parameterized profiles. ### CalDAV [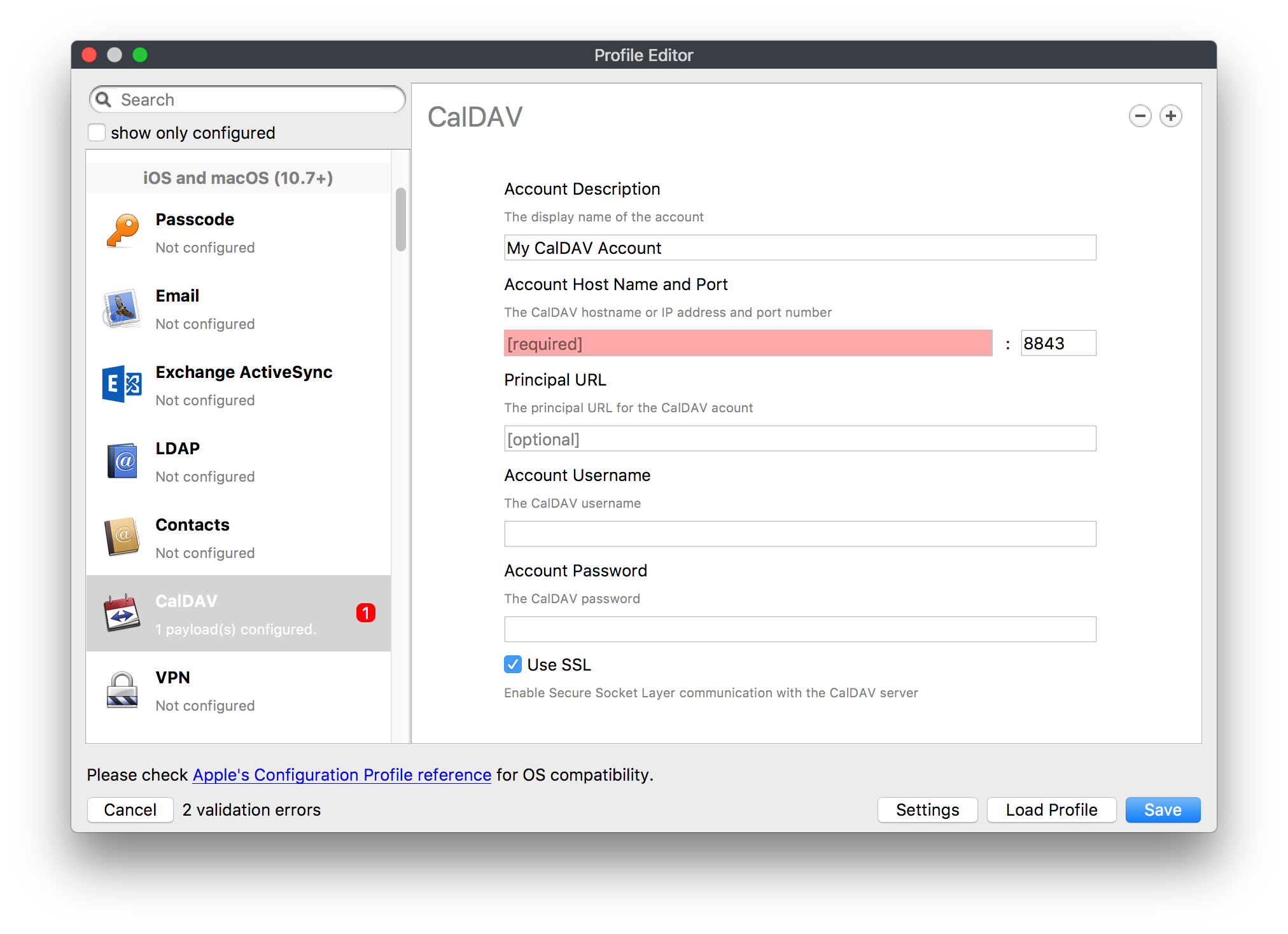](https://kb.filewave.com/uploads/images/gallery/2023-07/Cv4fTegIUJimUXWM-image.png) The CalDAV payload provides settings for access to CalDAV (Calendar) servers. This payload supports parameterized profiles. ### VPN [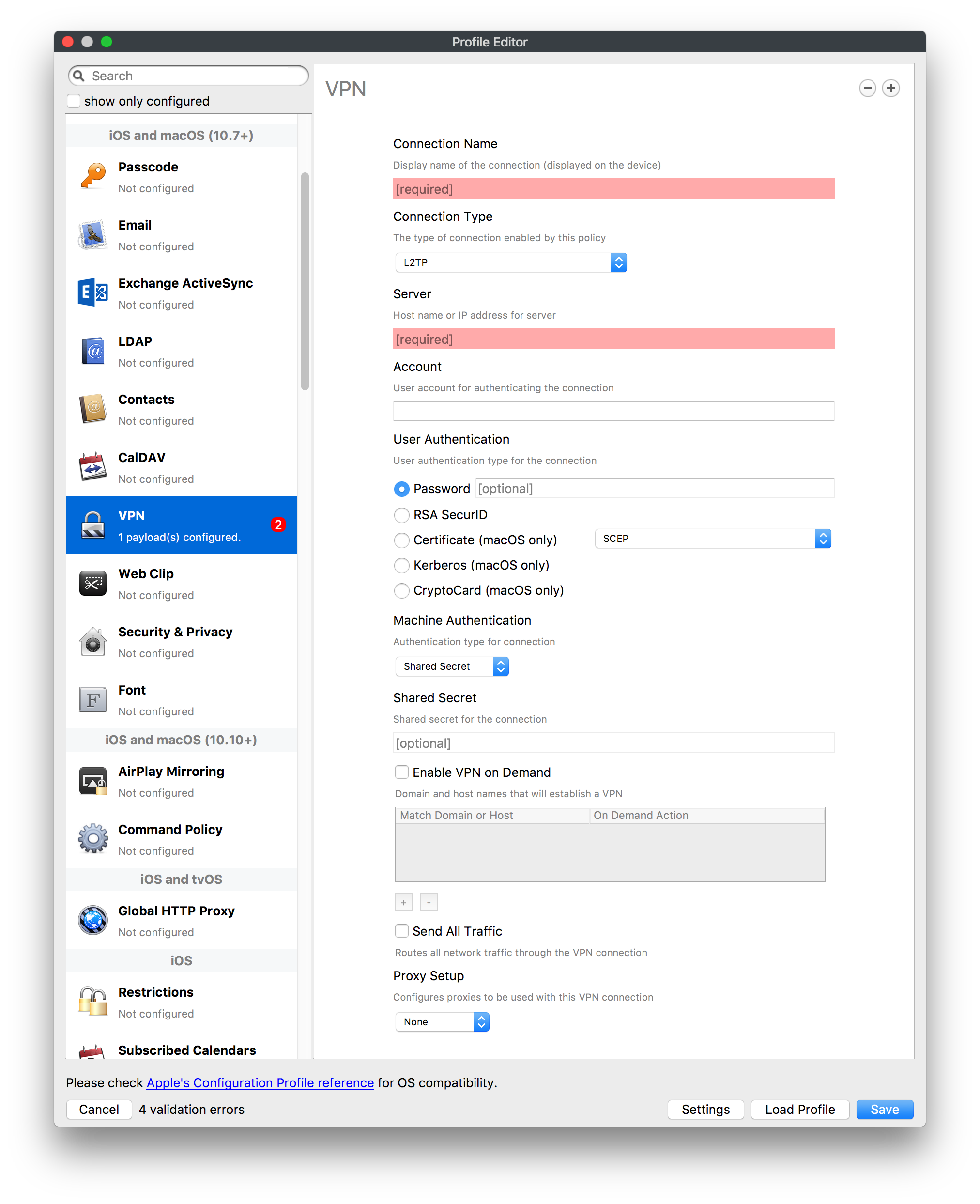](https://kb.filewave.com/uploads/images/gallery/2023-07/kMmXMv0JqxWACJns-image.png) Use the VPN payload to establish settings for a device to connect to a virtual private network. Settings include the user and machine authentication methods (including shared secret or certificate), proxy settings, and ability to force all network traffic through VPN. ### Web Clip [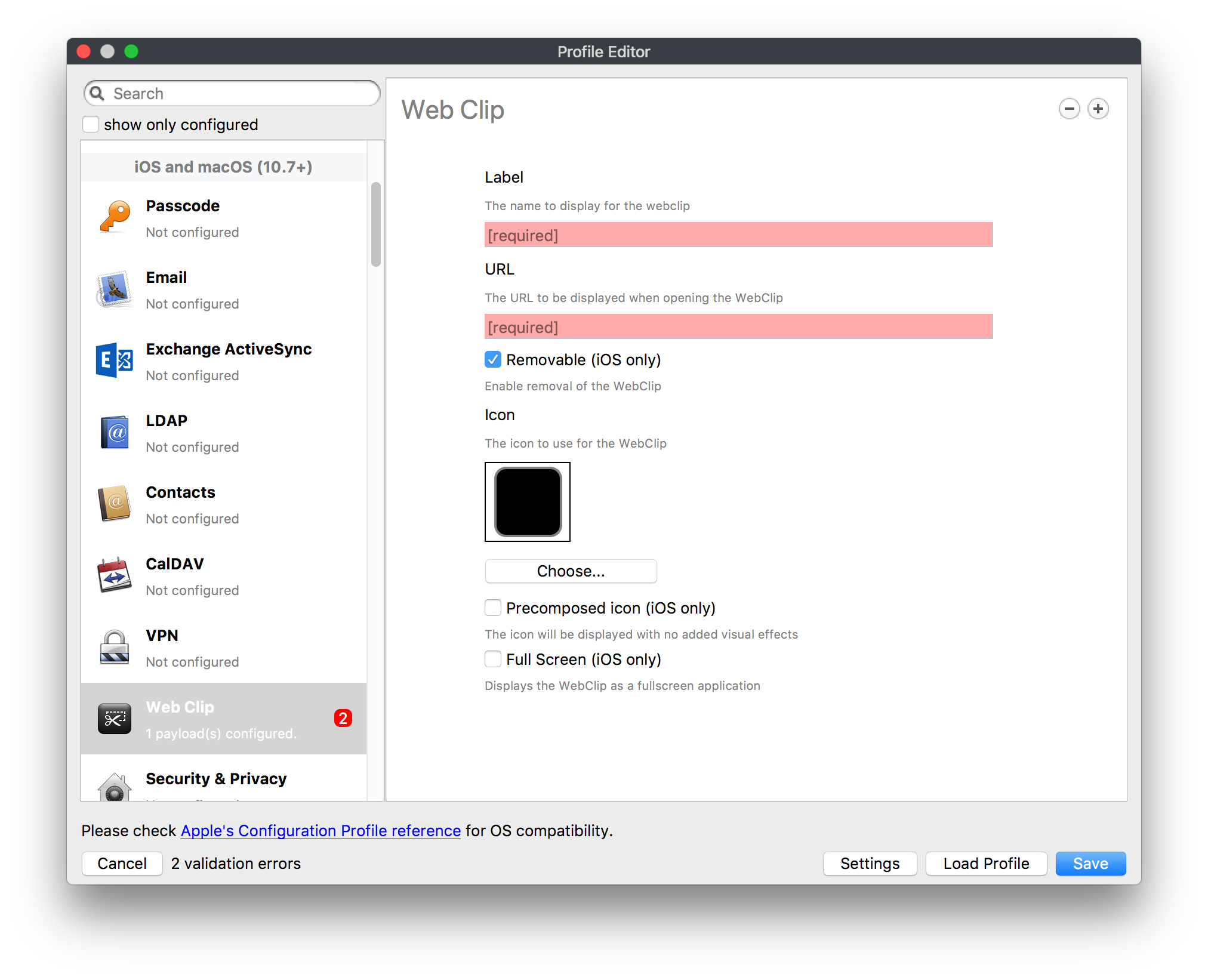](https://kb.filewave.com/uploads/images/gallery/2023-07/XD9fC9MlSWtyhaqK-image.png) The Web Clip payload lets you assign URL's as 'miniApps' to a managed device. Settings include the URL for the clip, an icon for the item, and the ability to force the clip to open as a full screen application. The Web Clip is deployed as a regular application on iOS and as a Dock item on macOS. ### Security & Privacy [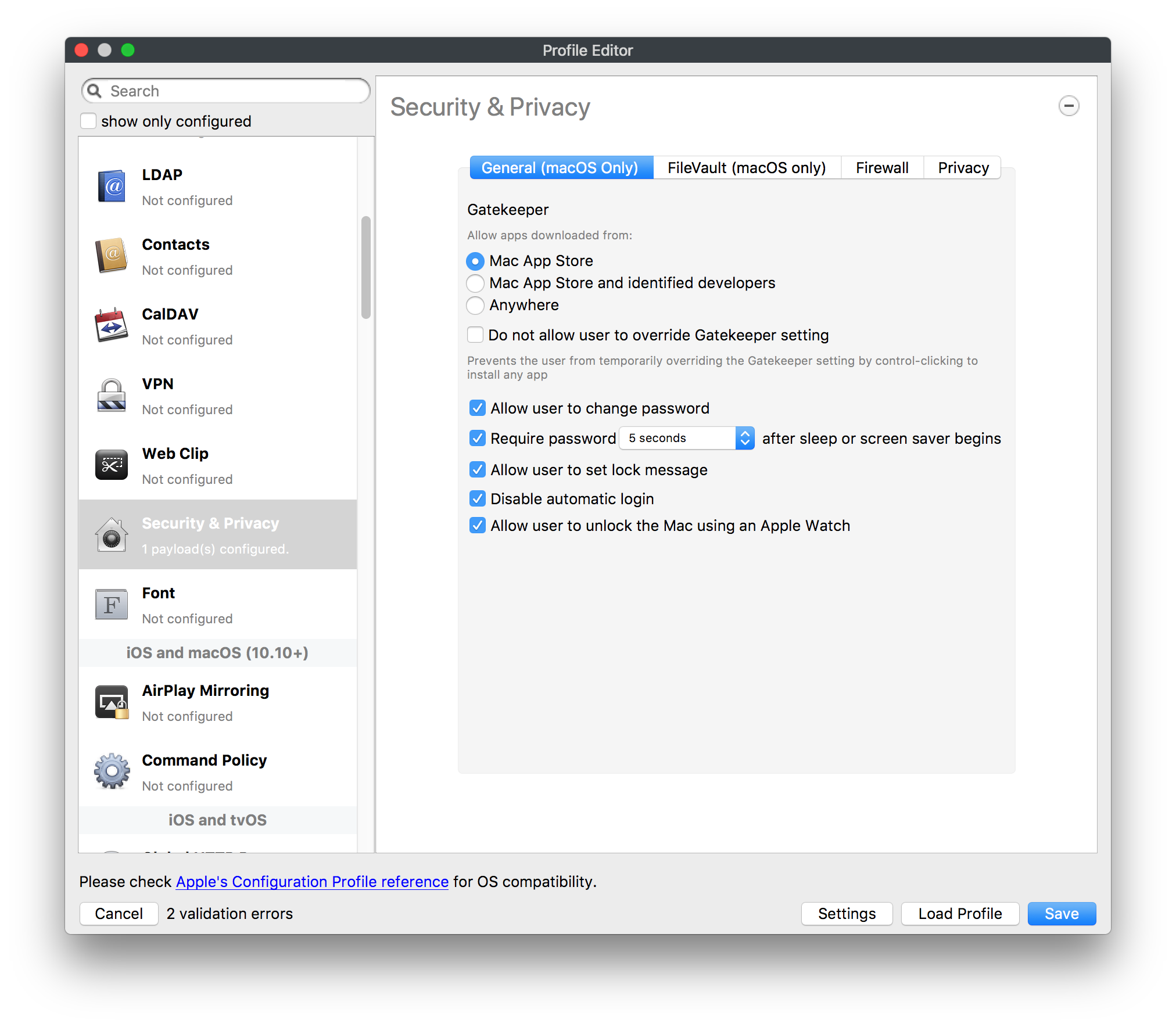](https://kb.filewave.com/uploads/images/gallery/2023-07/x1iens7vIum6CgAx-image.png) [](https://kb.filewave.com/uploads/images/gallery/2023-07/462BNRhareFLCsHy-image.png) [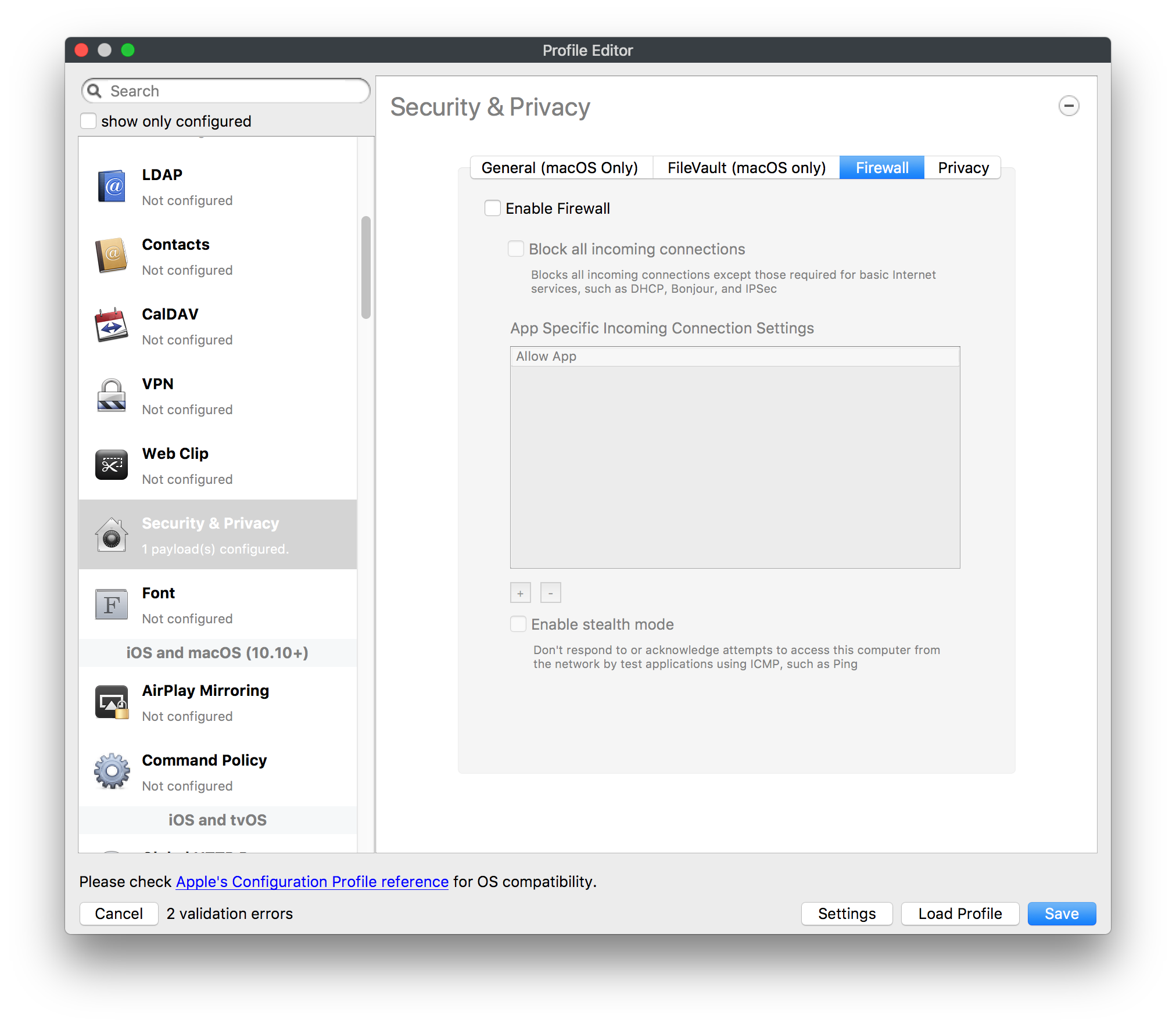](https://kb.filewave.com/uploads/images/gallery/2023-07/15BEG8PUpbRVpzbn-image.png) [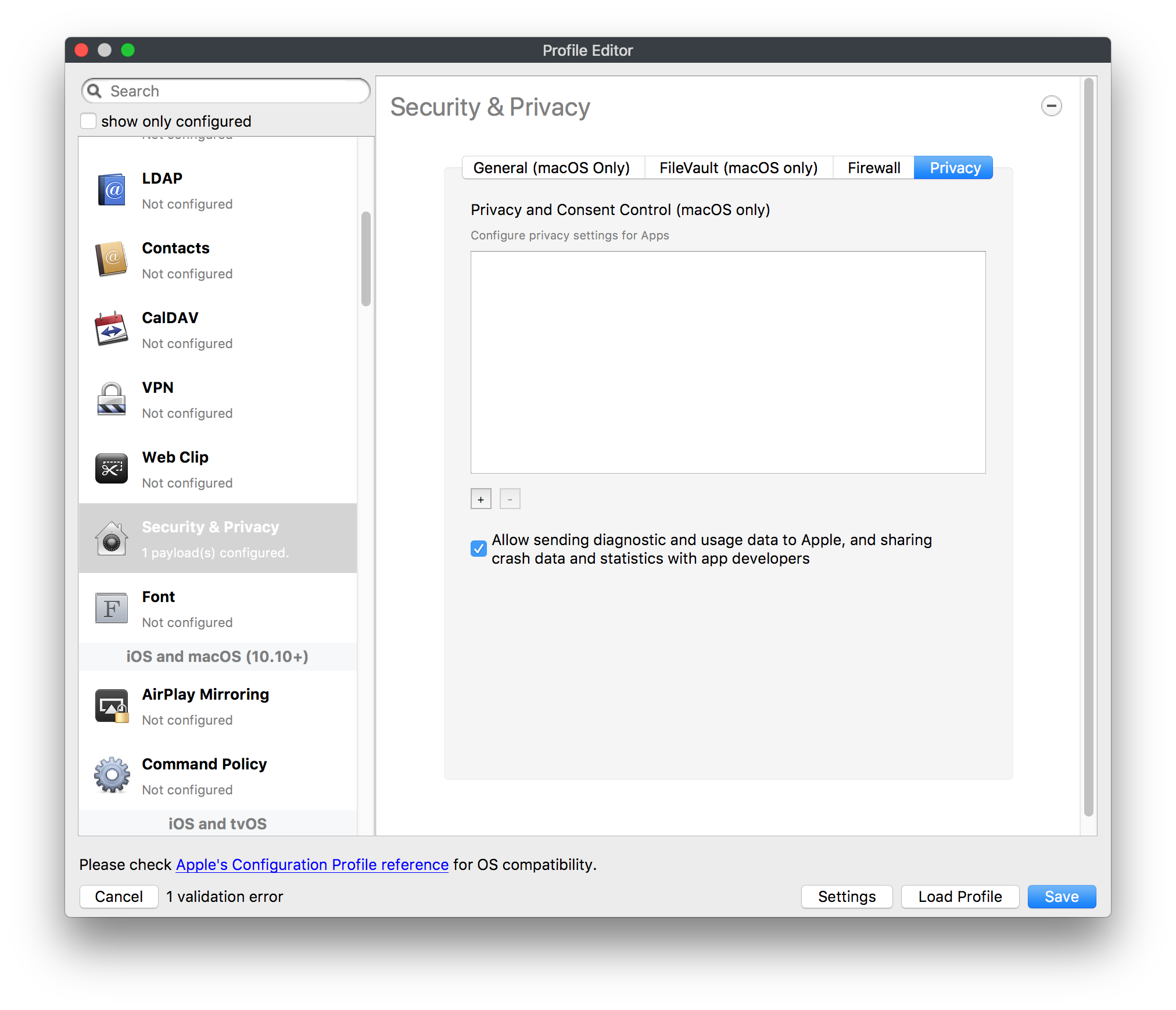](https://kb.filewave.com/uploads/images/gallery/2023-07/HgQaSr3gmc3pjOLB-image.png) [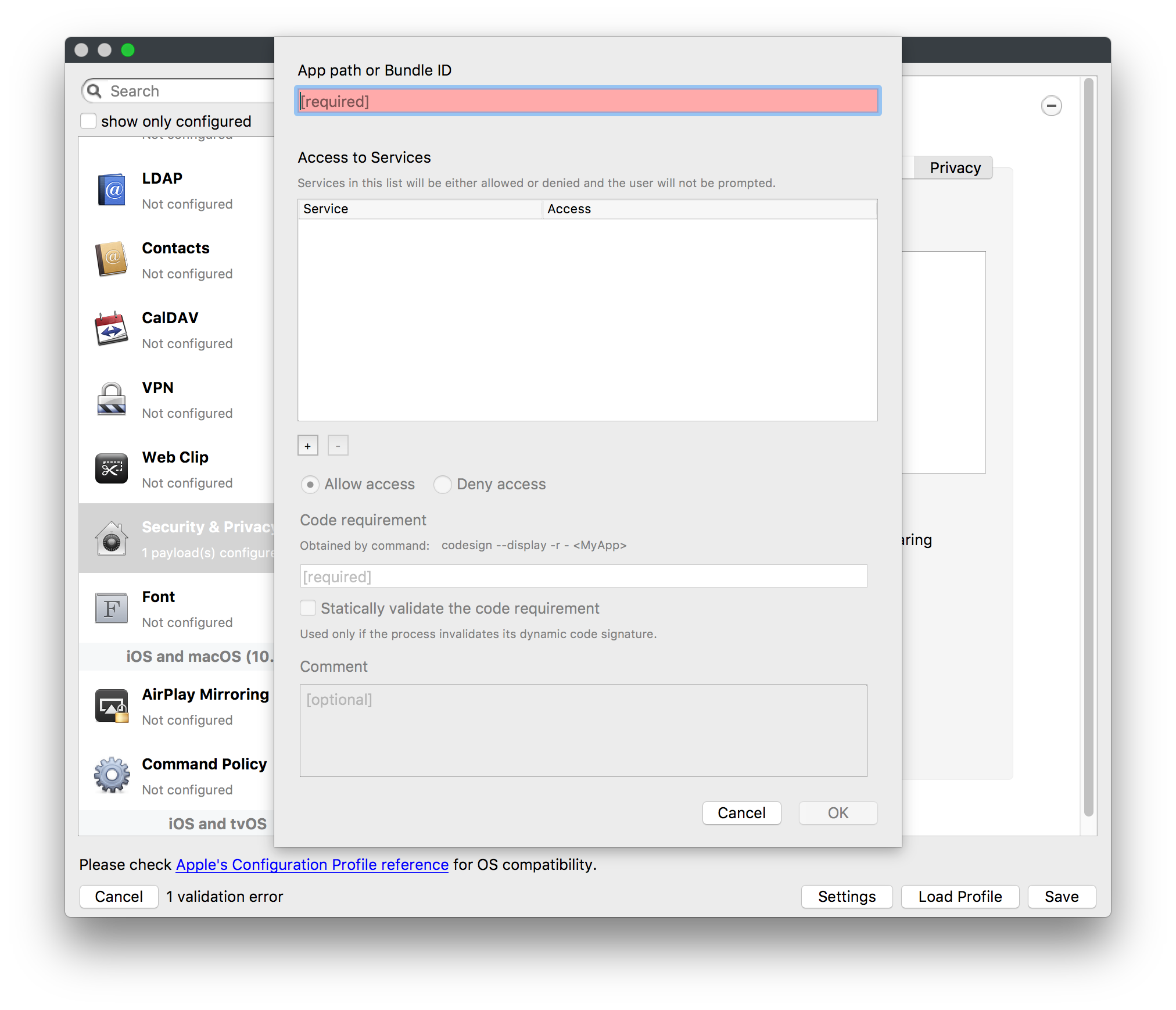](https://kb.filewave.com/uploads/images/gallery/2023-07/RE2l9qJ3ZngxBen5-image.png) The Security & Privacy payload allows managed devices to be configured with access to specific sources for application downloads (macOS only Gatekeeper), Firewall settings, and specify if diagnostic information will be sent to Apple or not. FileVault 2 settings are can be configured using the **Disk Encryption** payload. ### Font [](https://kb.filewave.com/uploads/images/gallery/2023-07/wATxUgJiJxjJA74W-image.png) The Font payload allows you send a specific font set to a device. This capability is very handy for insuring an iOS device has the same font installed for a document that is also being worked on with macOS computes. ## iOS and macOS (10.10+) This payload is for iOS and macOS ### AirPlay Mirroring [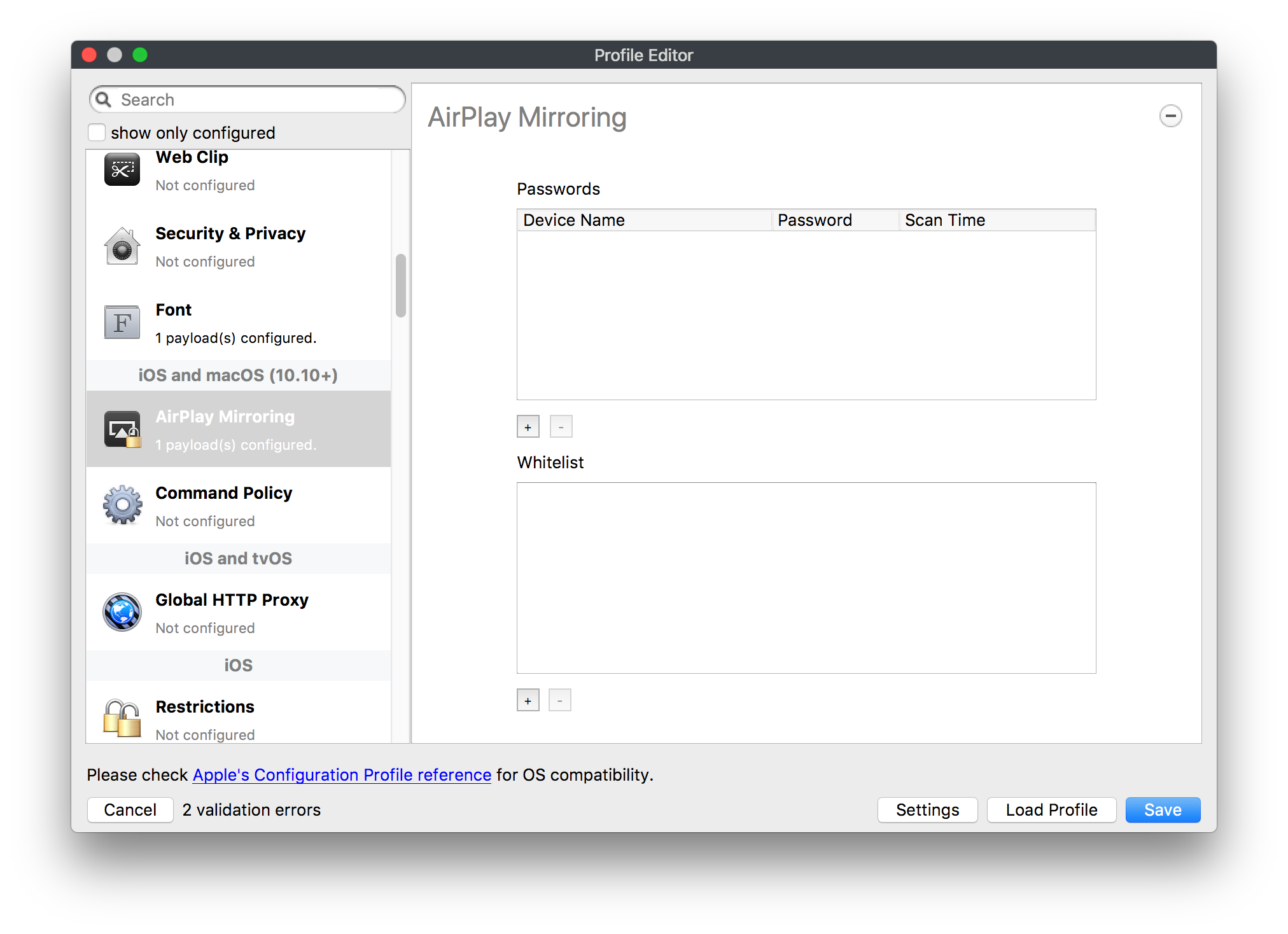](https://kb.filewave.com/uploads/images/gallery/2023-07/nEYK0p8AQ1SL21bA-image.png) AirPlay Mirroring payloads are for assignment of specific AirPlay devices to designated Apple TVs. A Group of iOS devices can be assigned to a certain Apple TV with the password imbedded in the profile. Other devices would not be able to connect to that Apple TV. You can also provide a set of whitelisted Apple TVs that the managed device can use for AirPlay. ### Command Policy [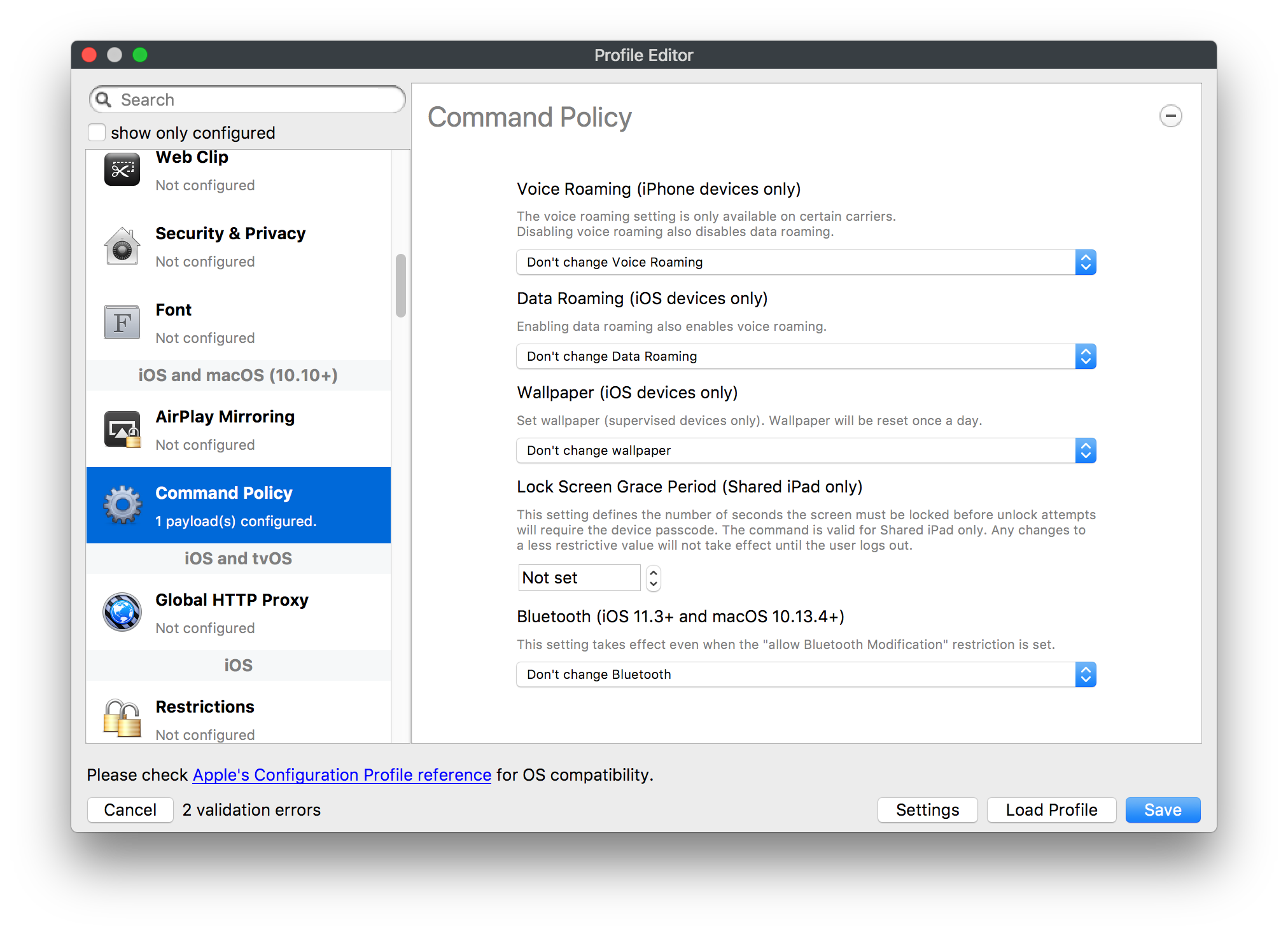](https://kb.filewave.com/uploads/images/gallery/2023-07/0ytGNm1hbIiI9D0c-image.png) These settings determine the voice and data roaming, Wallpaper, Lock Screen Grace Period, or Bluetooth. The commands are sent at each *Verify* from FileWave. ## iOS and tvOS ### Global HTTP Proxy [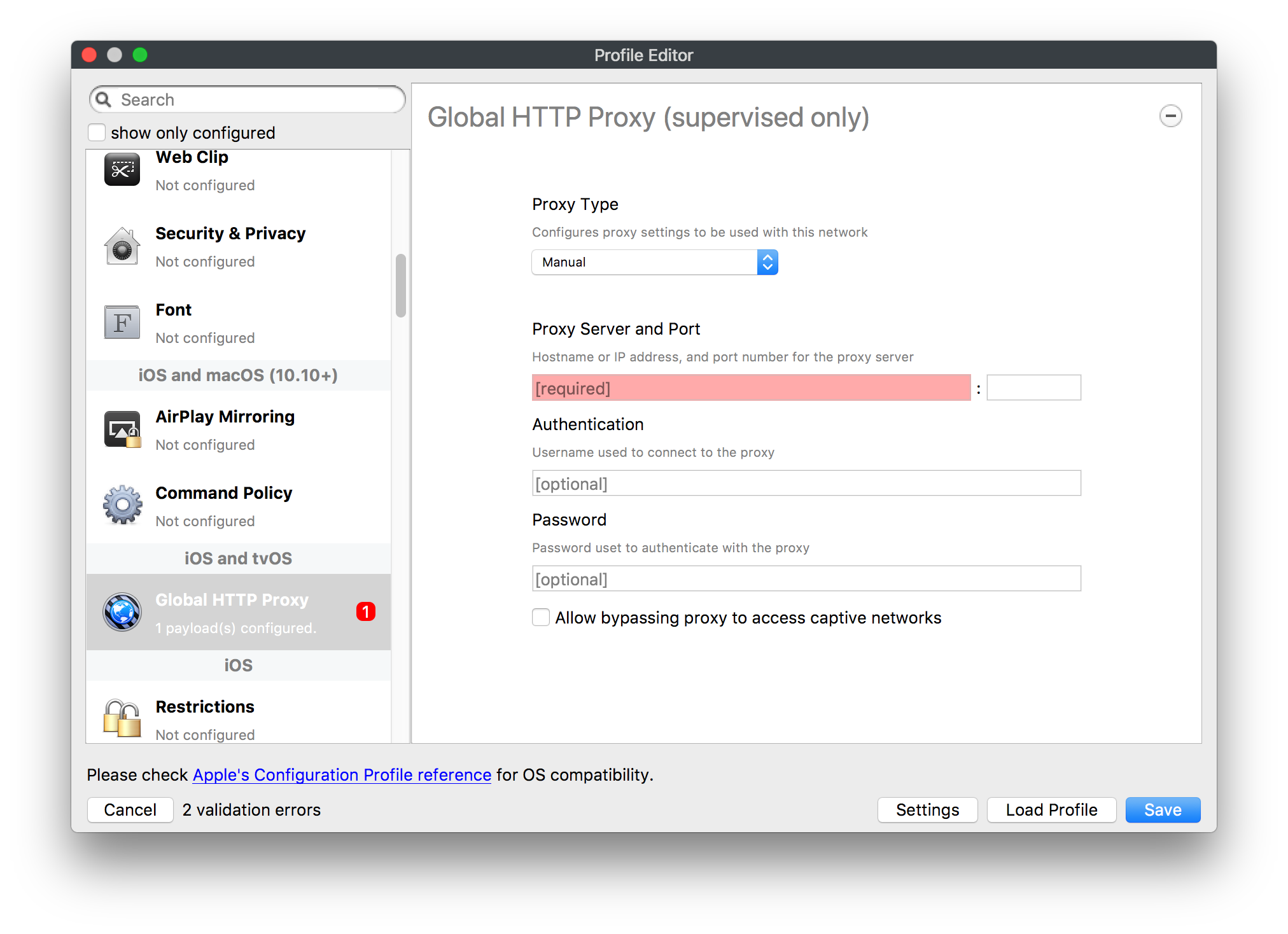](https://kb.filewave.com/uploads/images/gallery/2023-07/9D6SmBOQBHYXzQ4R-image.png) Global HTTP Proxy payload settings allow supervised iOS devices to be linked to a master network proxy for web content. ## iOS These payloads apply to all supported iOS devices. ### Restrictions Restrictions allow for the establishment of tight controls over institutional iOS devices, and can be used for managing BYOD/1:1 devices. These settings include controlling access to the camera, Siri, iTunes, and iCloud. This payload also contains 'Manage open in' and GameCenter controls, as well as content management by age appropriate settings. Note that many of the settings require the device to be supervised. That means the device must be institutionally purchased and configured with either DEP, or with Apple Configurator. [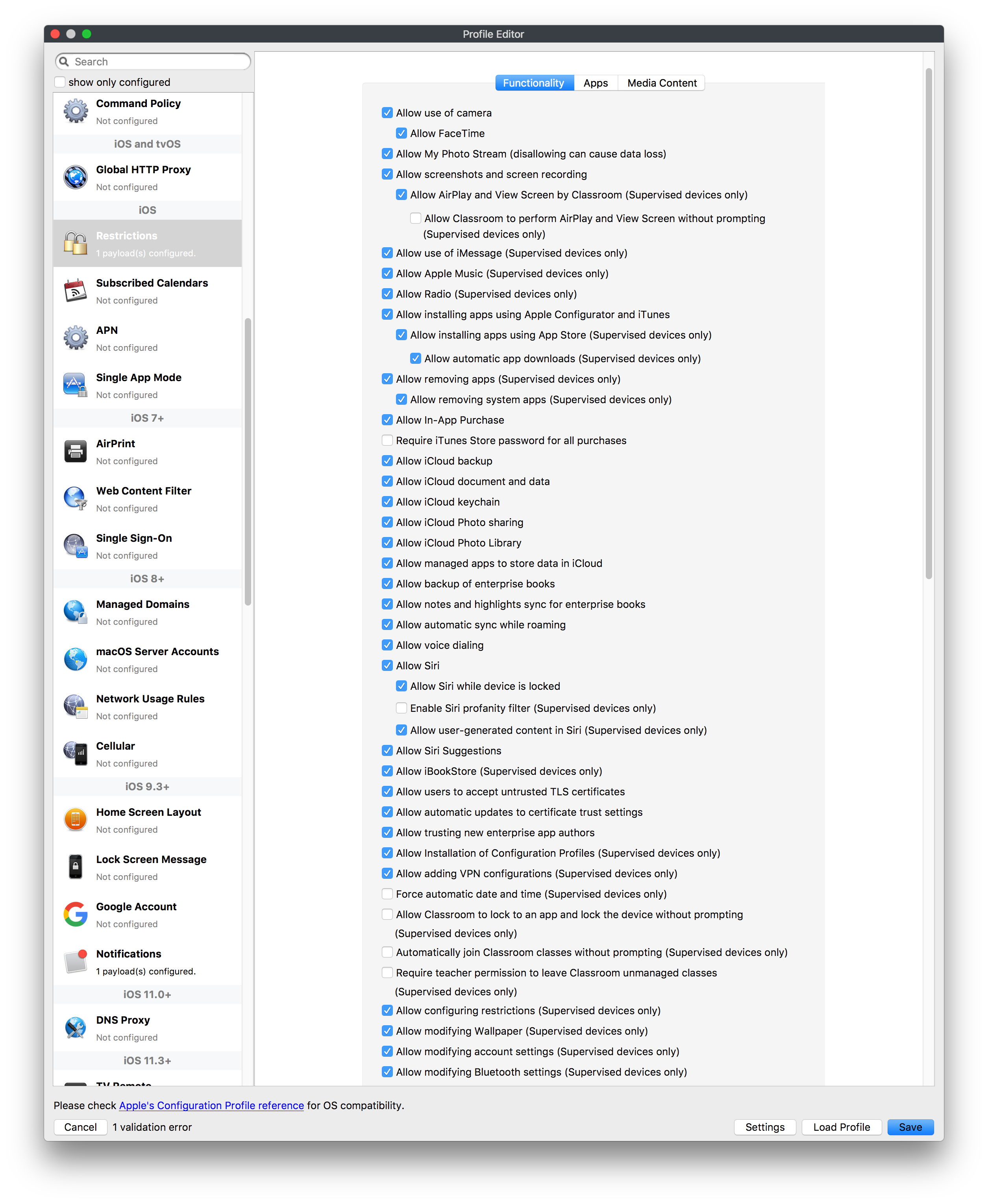](https://kb.filewave.com/uploads/images/gallery/2023-07/jJAmR765XyBt1Qcc-image.png) [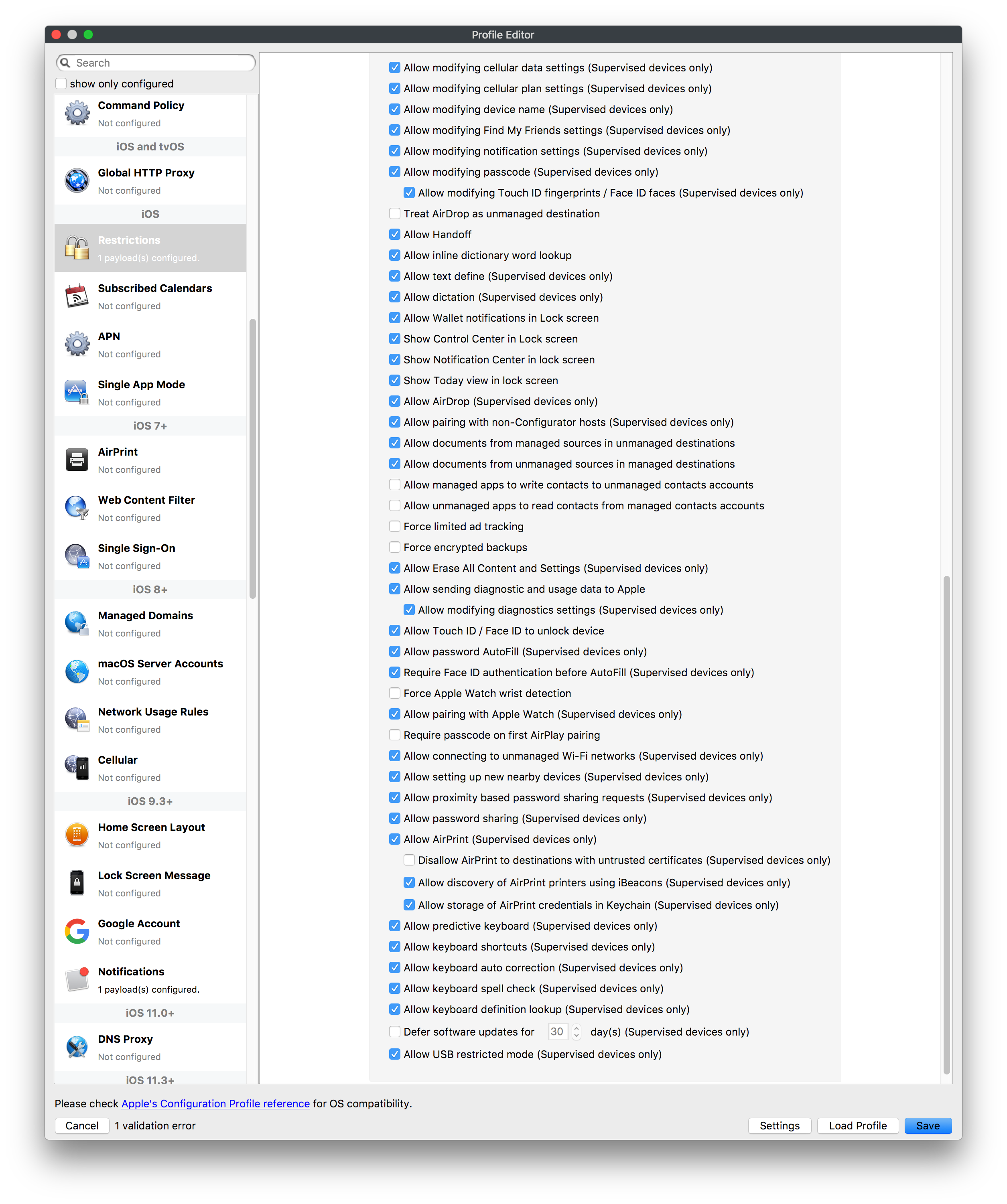](https://kb.filewave.com/uploads/images/gallery/2023-07/YgKkf2ettnPweRnt-image.png) [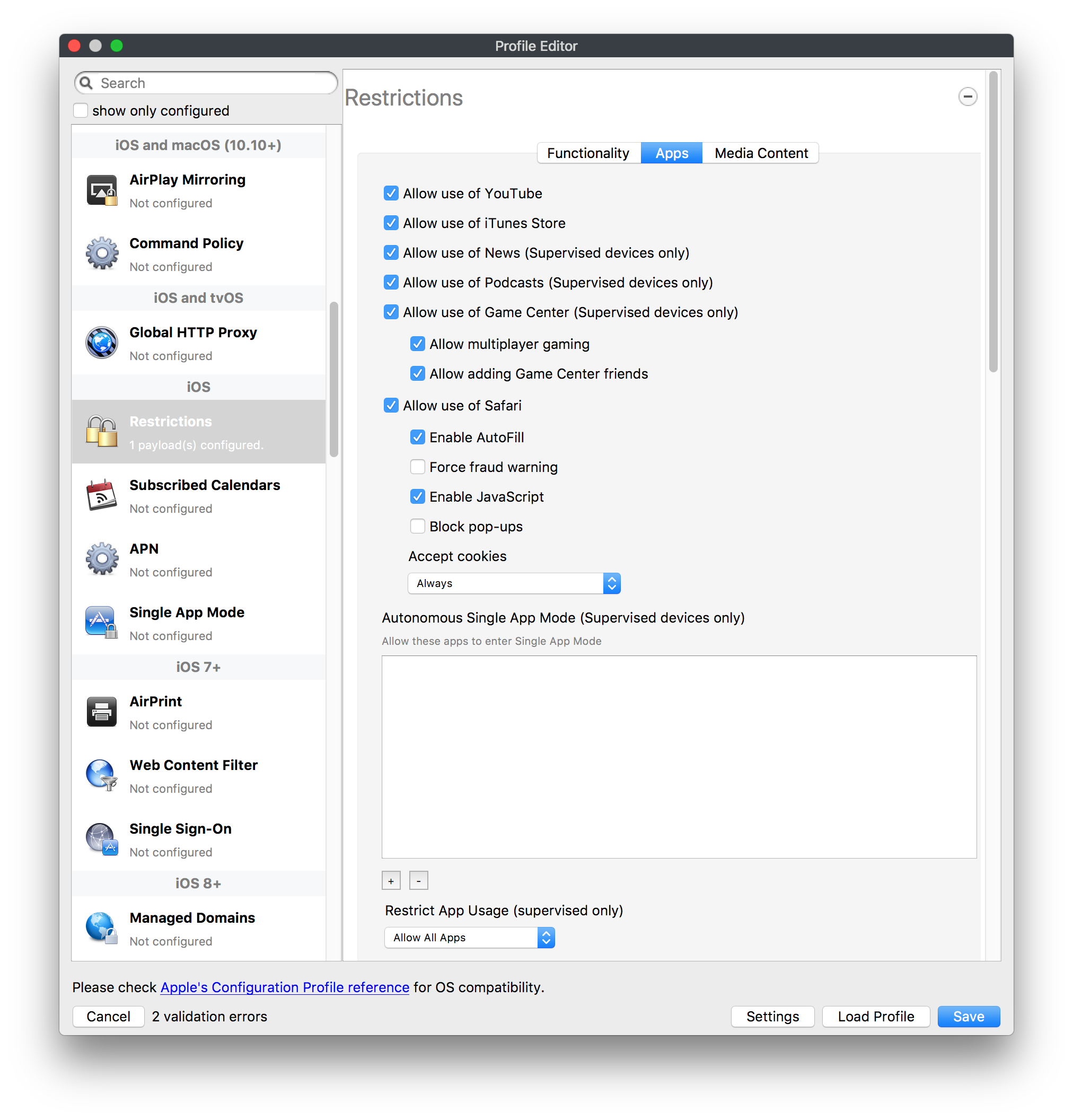](https://kb.filewave.com/uploads/images/gallery/2023-07/rbyNNjsb8HnBjZ7p-image.png) [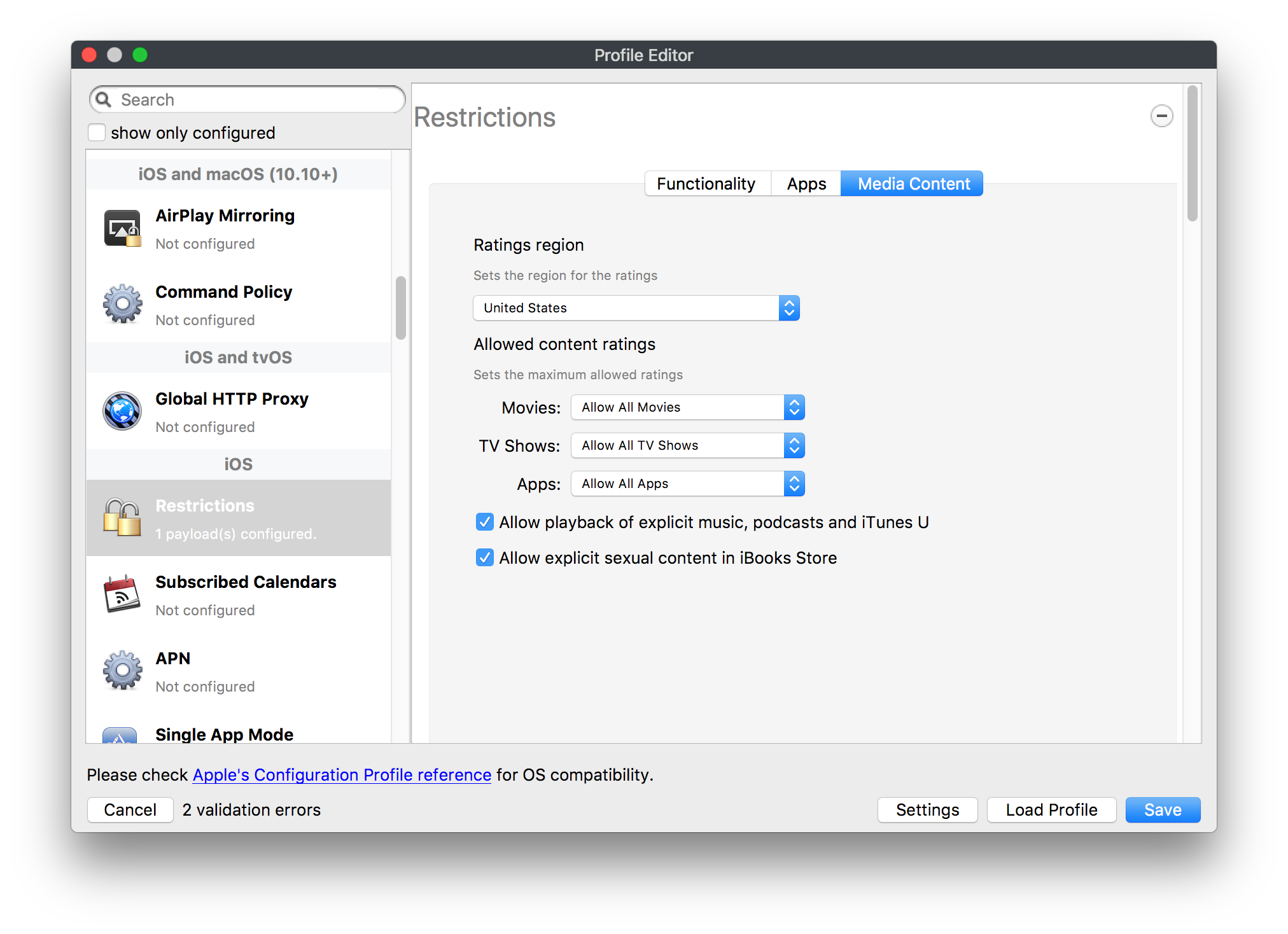](https://kb.filewave.com/uploads/images/gallery/2023-07/QsTjOzLCfZrtzfvp-image.png) New with FileWave 11's support for iOS 9.3 are the following restrictions, which apply to supervised devices: - *Allow Apple Music* — If set to false, Music service is disabled and Music app reverts to classic mode. Defaults to true. - *A\_l\_low Radio* — If set to false, iTunes Radio is disabled. Defaults to true. - *Restrict App Usage*: - Allow All Apps - Allow Some Apps Only, where you can specify what apps are allowed - Don't Allow Some Apps, where you can specify what apps are not allowed ### Subscribed Calendars [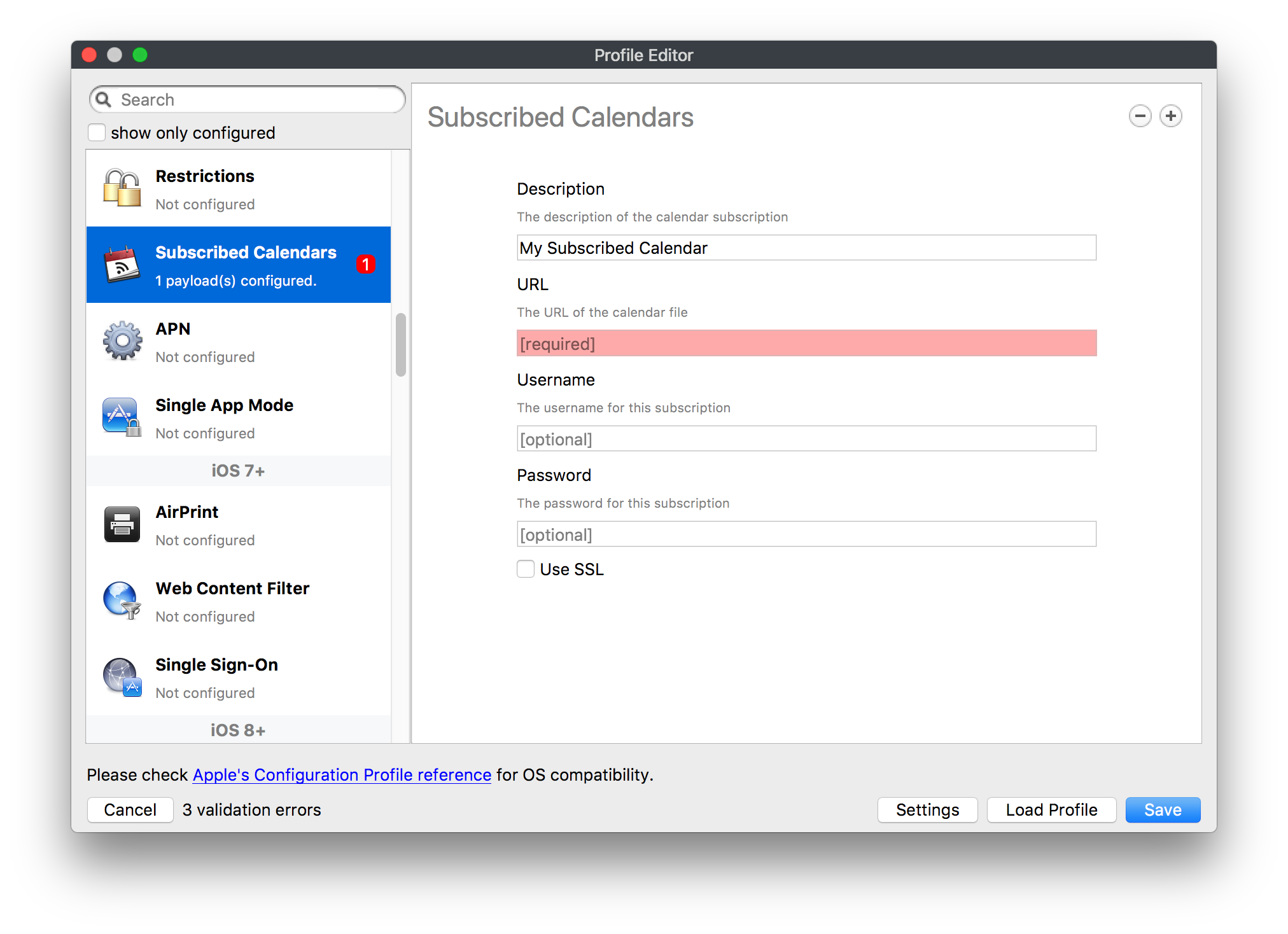](https://kb.filewave.com/uploads/images/gallery/2023-07/ecQ0sro2OX8a1IeH-image.png) The Subscribed Calendars payload lets you provide predefined shared calendar information for your end users on managed devices. The settings work with parameterized profiles. ### APN [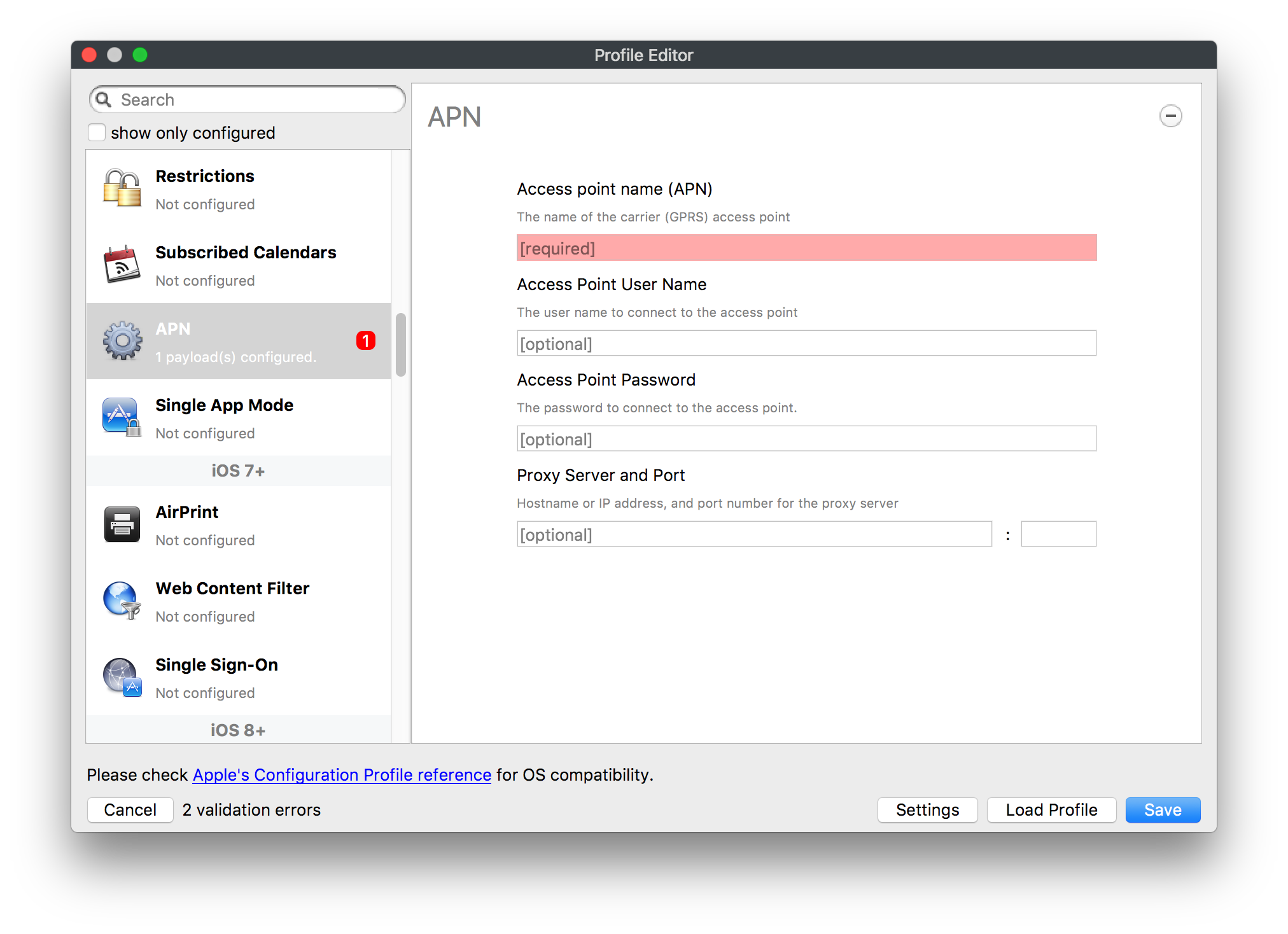](https://kb.filewave.com/uploads/images/gallery/2023-07/MLU5OtFRXVAzX1ZL-image.png) The APN payload allows systems administrators the ability to manage Carrier Access Point Name configuration for iOS devices with cellular services enabled. ### Single App Mode [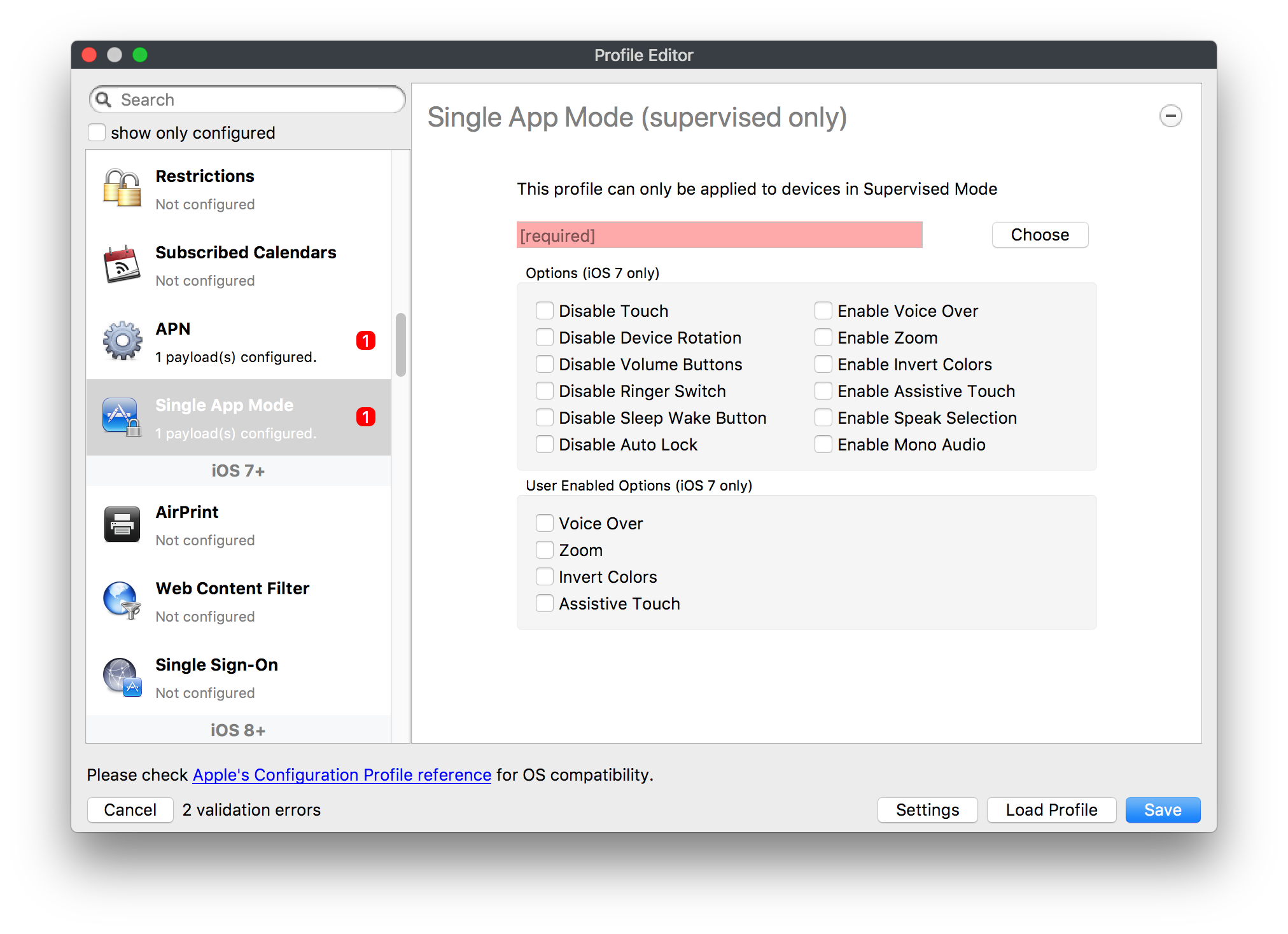](https://kb.filewave.com/uploads/images/gallery/2023-07/PWJzEIibyefXsm3F-image.png) The Single App Mode payload is designed to allow you to configure supervised iOS devices so that they open into a single application. If a user turns the device off, when restarted, it will reopen into the designated app as long as the profile is active on the device. This payload is best used in testing or kiosk environments. Setup requires the use of Apple Configurator to force the device into supervised mode. The payload also allows you to deactivate several other options, such as Auto Lock, Device Rotation, and Volume buttons. You select the app from the list of iOS apps added to Filesets. The iOS app Fileset must also be associated with the device in order for this process to work. ## iOS 7+ settings Payloads for iOS devices running iOS 7 and higher. ### AirPrint [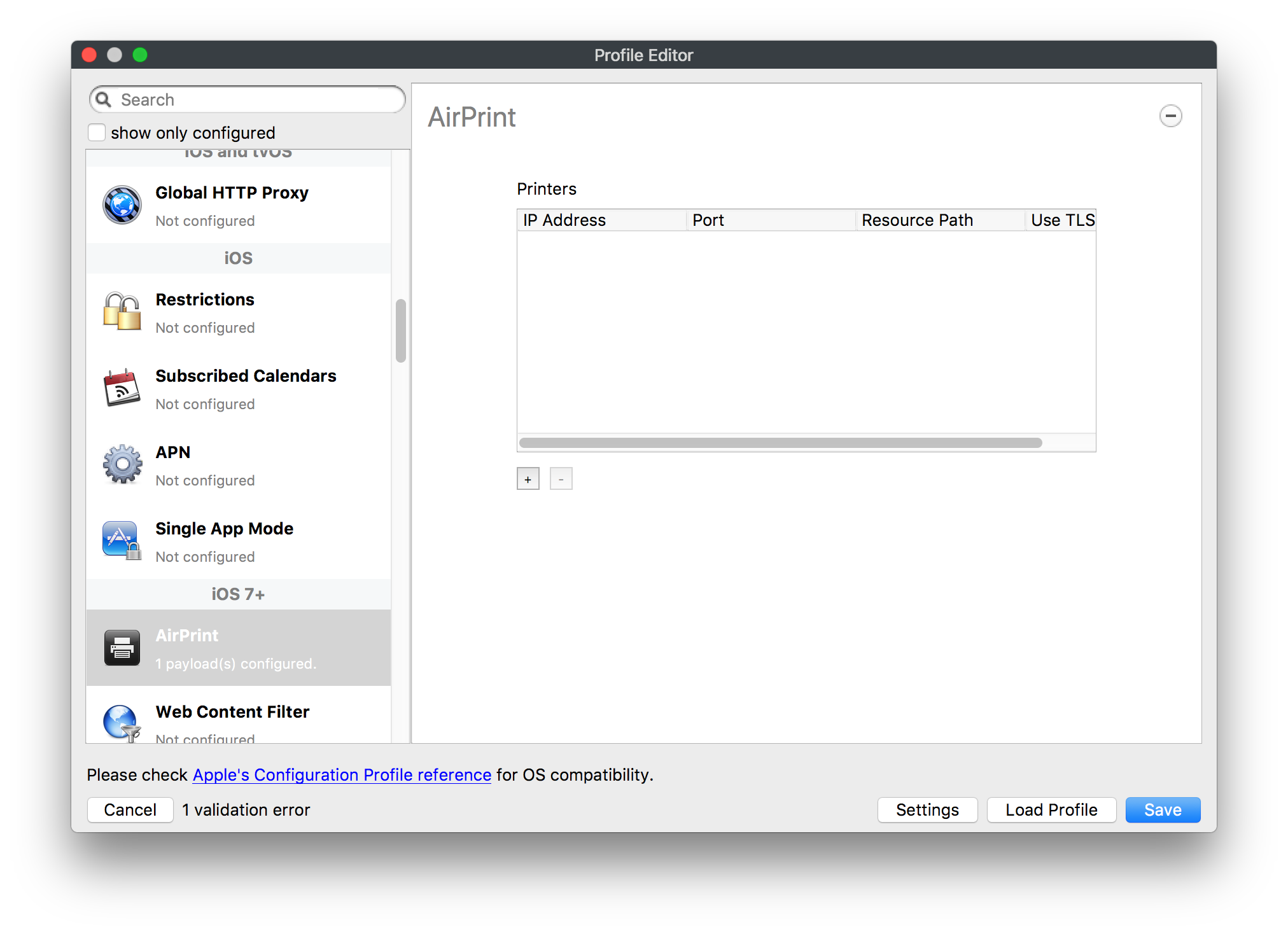](https://kb.filewave.com/uploads/images/gallery/2023-07/5MSmR1F9oVQ6fegC-image.png) Use the AirPrint payload to designate AirPrint capable printers for managed iOS devices. The settings can be manually entered IP addresses or discoverable (Bonjour) devices. ### Web Content Filter (supervised only) [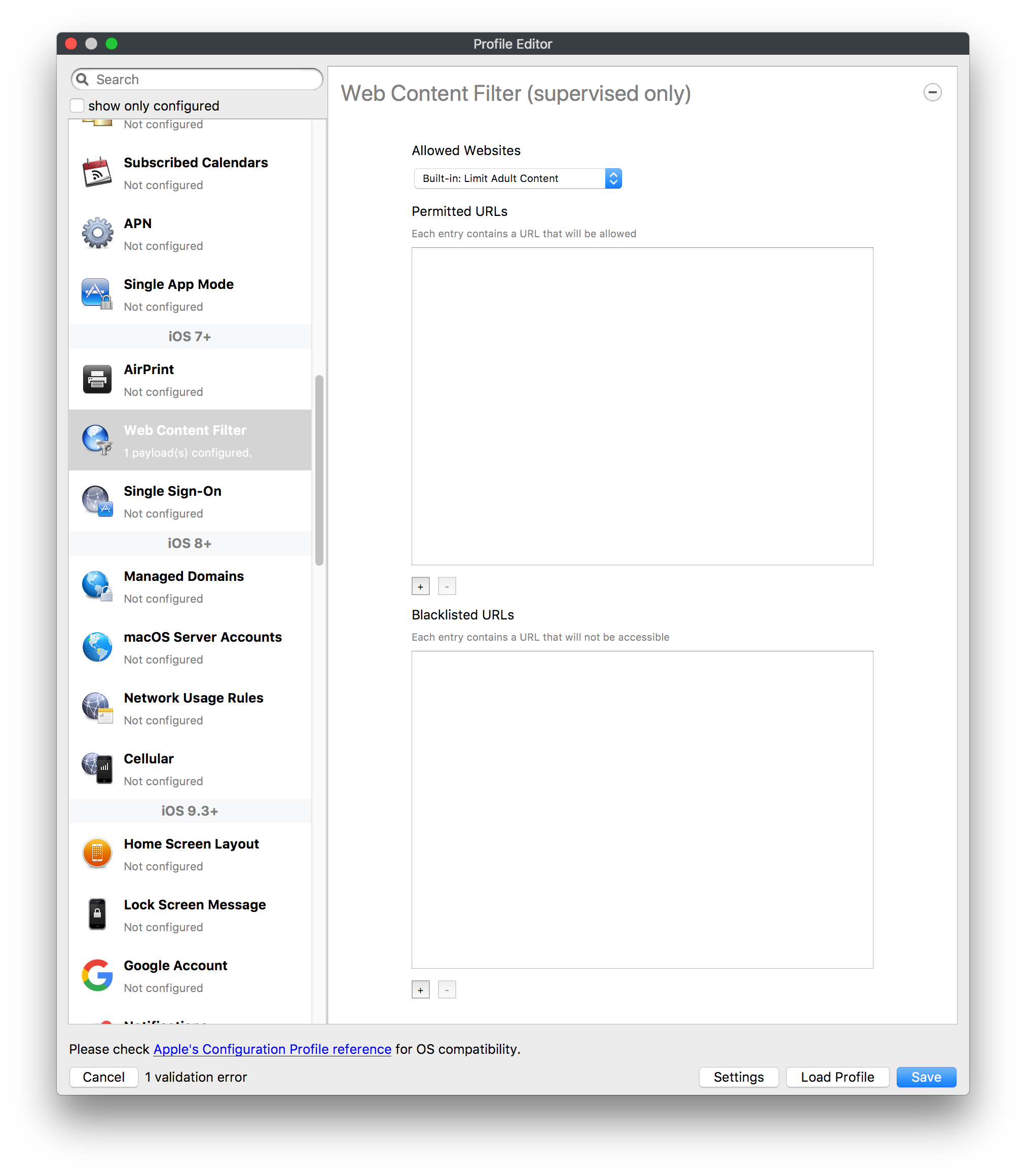](https://kb.filewave.com/uploads/images/gallery/2023-07/DHBNh0BQXSrnF1qT-image.png) The Web Content Filter payload supports whitelists and blacklists for web access, as well as setting a basic content filter to control access to adult content. ### Single Sign-On [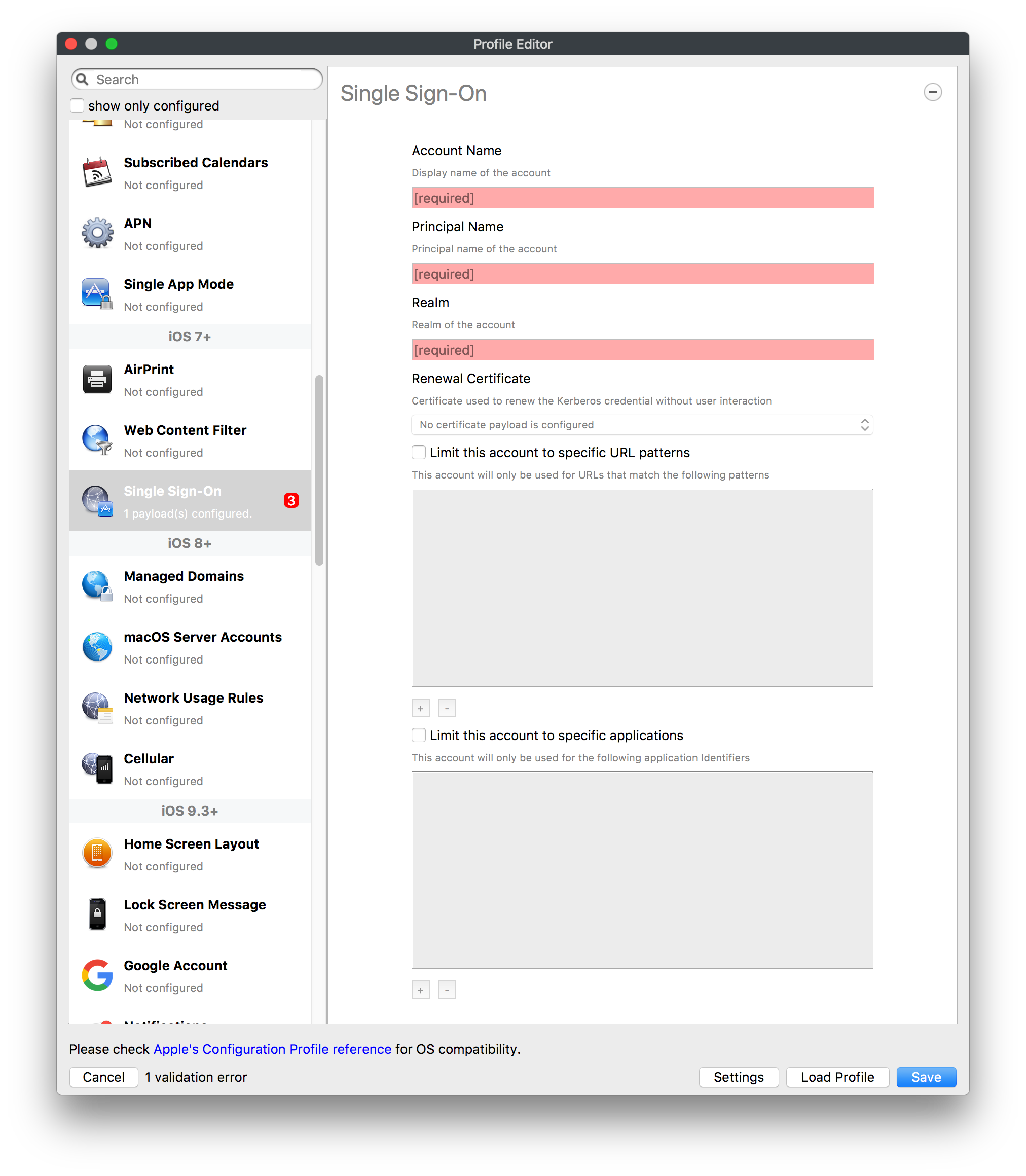](https://kb.filewave.com/uploads/images/gallery/2023-07/JAu7bauBj5PhEcLg-image.png) The Single Sign-On (SSO) payload allows you to configure Kerberos access for your managed device to specific services and applications. ## iOS 8+ These settings are for iOS 8 or higher only. ### Managed Domains [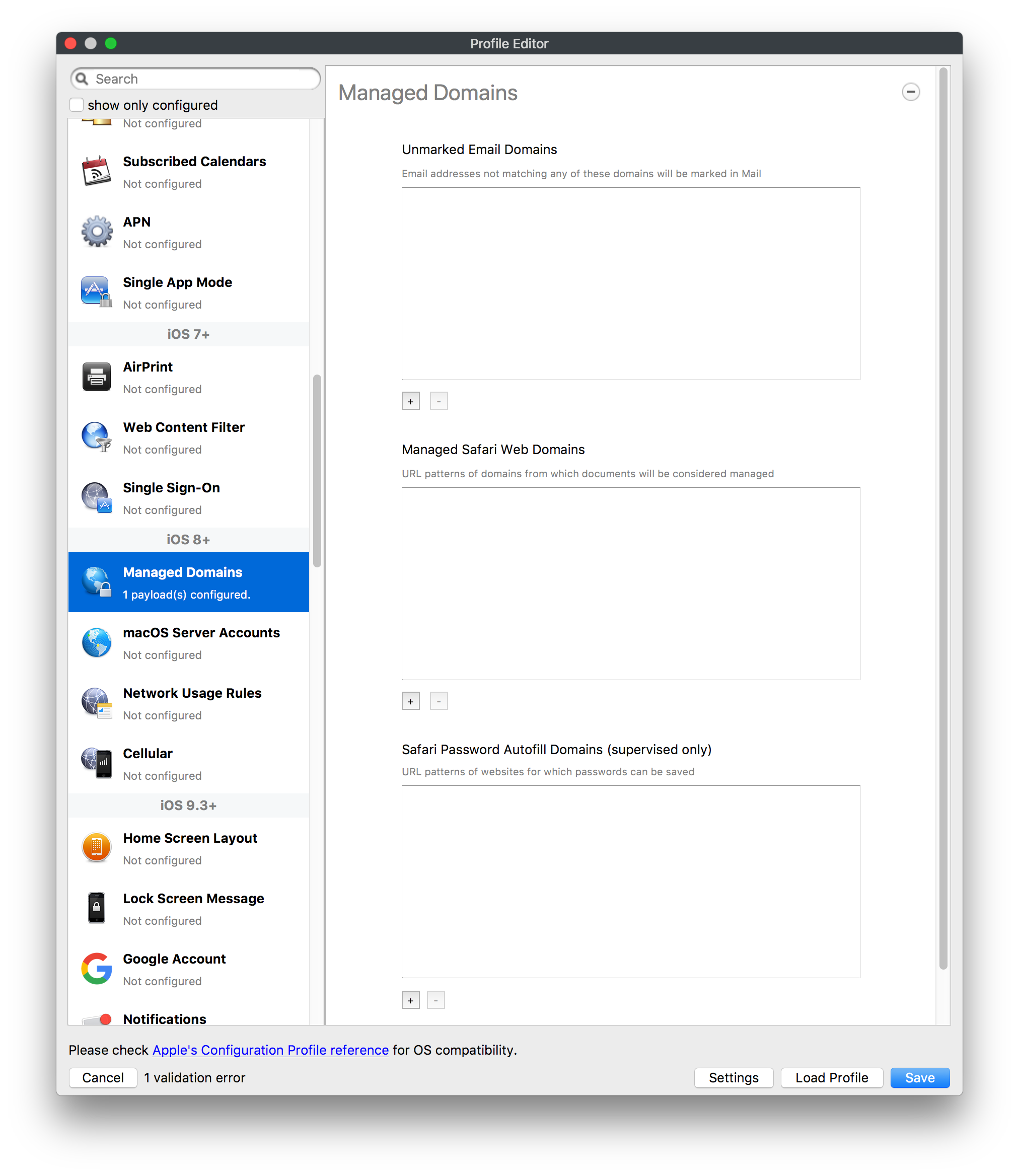](https://kb.filewave.com/uploads/images/gallery/2023-07/PE9chjJBNP6yCwqf-image.png) Managed domains can be set for mail and web sites. For mail, you specify "safe" email domains; e.g. [filewave.com](http://filewave.com/) and any mail coming from, or being sent to another domain will be highlighted. On the web side, documents from approved domains will be considered as managed. This will allow a Web Clip from an approved domain to function while a PDF from an unapproved domain won't be allowed to open in any managed application. New with FileWave 11 and iOS 9.3 is the ability to specify the URL patterns fro which passwords can be saved for supervised devices. ### macOS Server Accounts [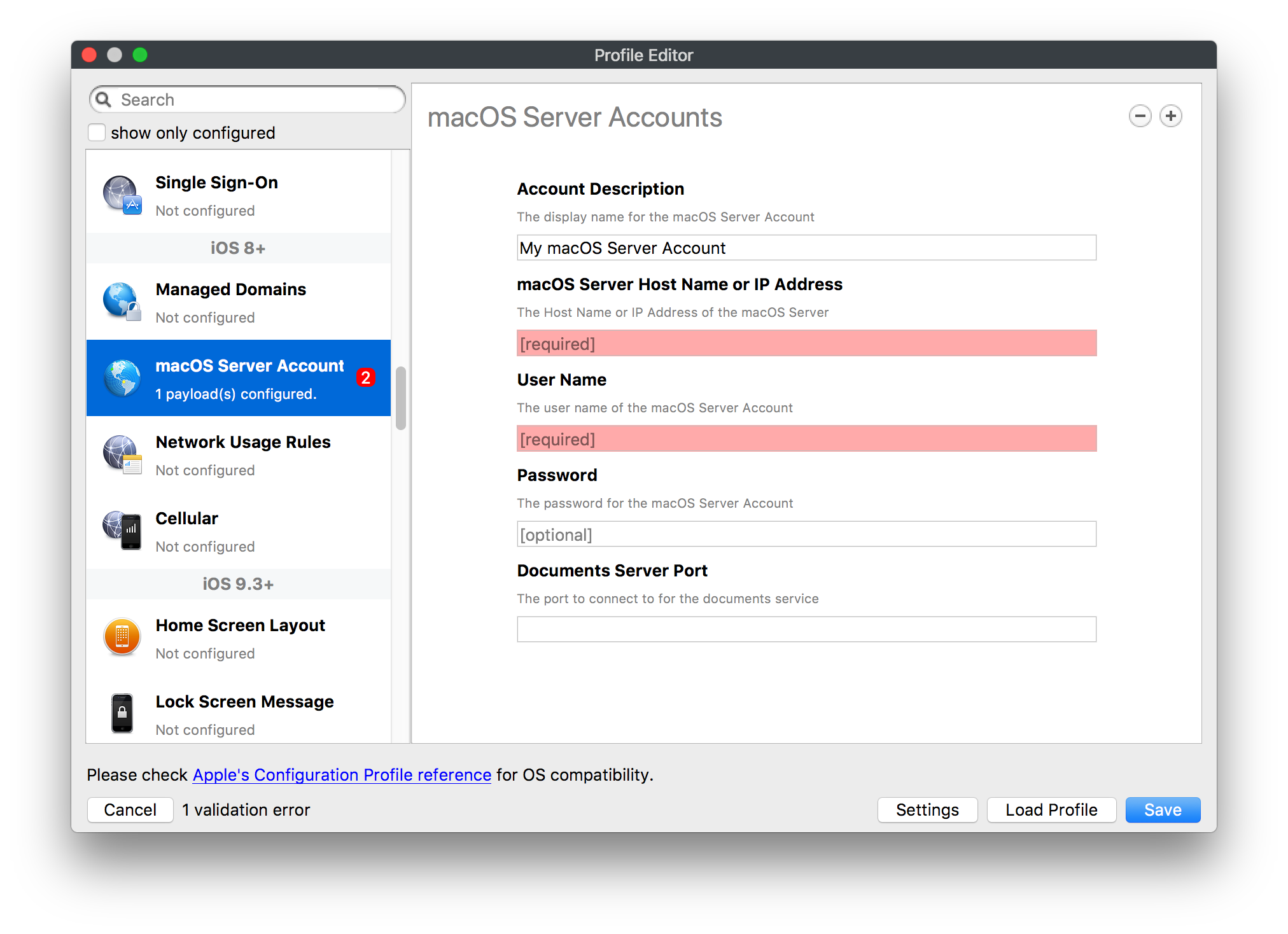](https://kb.filewave.com/uploads/images/gallery/2023-07/ixKcdpV0idKIzG0A-image.png) These settings allow you to pre-configure macOS file servers for access by managed users. ### Network Usage Rules [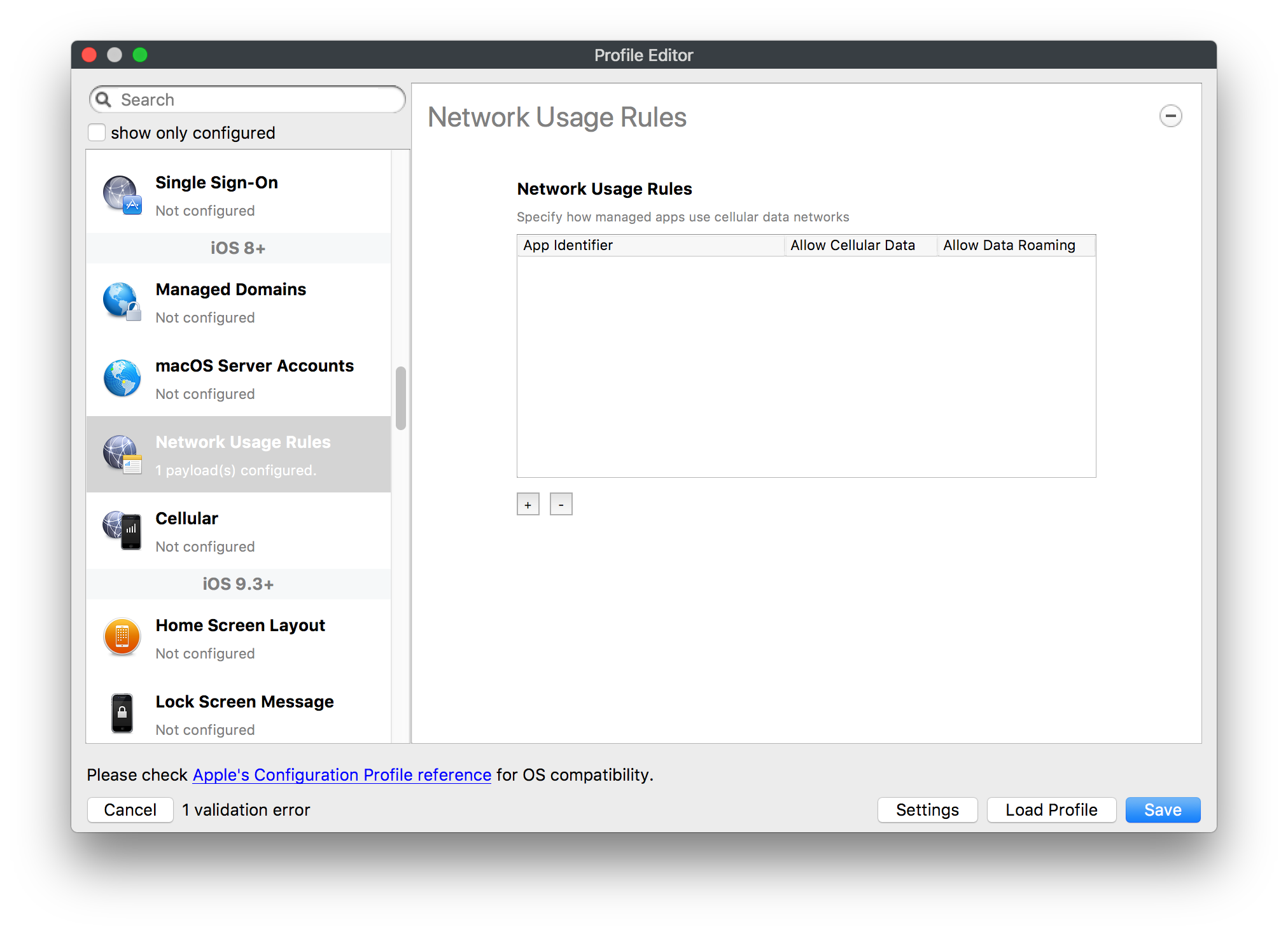](https://kb.filewave.com/uploads/images/gallery/2023-07/dCuxoS577iT2s7S7-image.png) These setting specify how managed apps use cellular data networks. ### Cellular [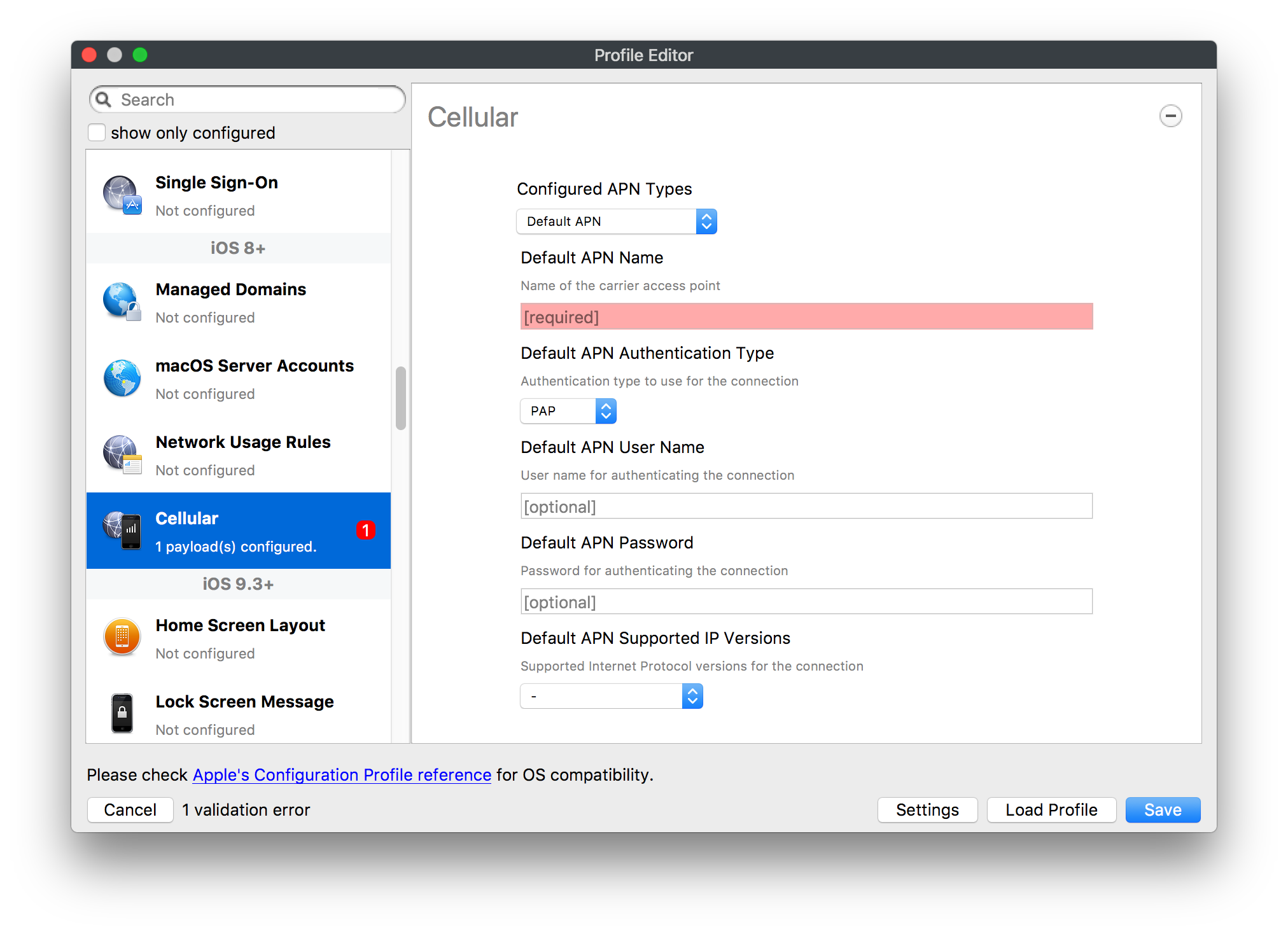](https://kb.filewave.com/uploads/images/gallery/2023-07/fC1u5WoYb1rJ0eRR-image.png) Use this payload for cellular settings. In iOS 7 or later, the APN payload is deprecated in favor of the Cellular payload. ## iOS 9.3+ These settings apply to iOS devices running iOS 9.3 or higher. ### Home Screen Layout (supervised only) [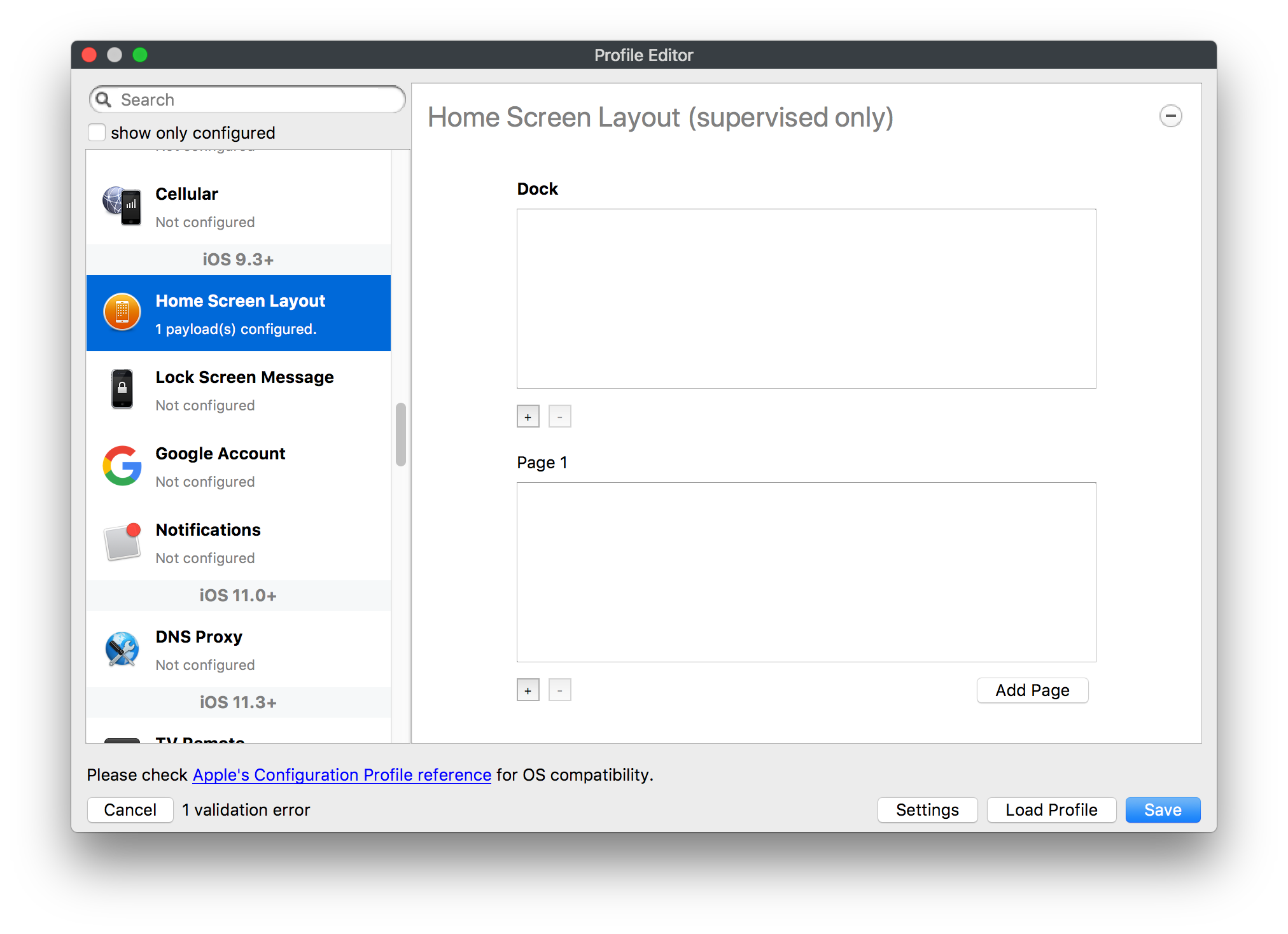](https://kb.filewave.com/uploads/images/gallery/2023-07/wZ7pHd8igNqggvoi-image.png) With supervised devices, you can specify the home screen layout including which apps are in the Dock and which apps appear where on different pages of the home screen. ### Lock Screen Message [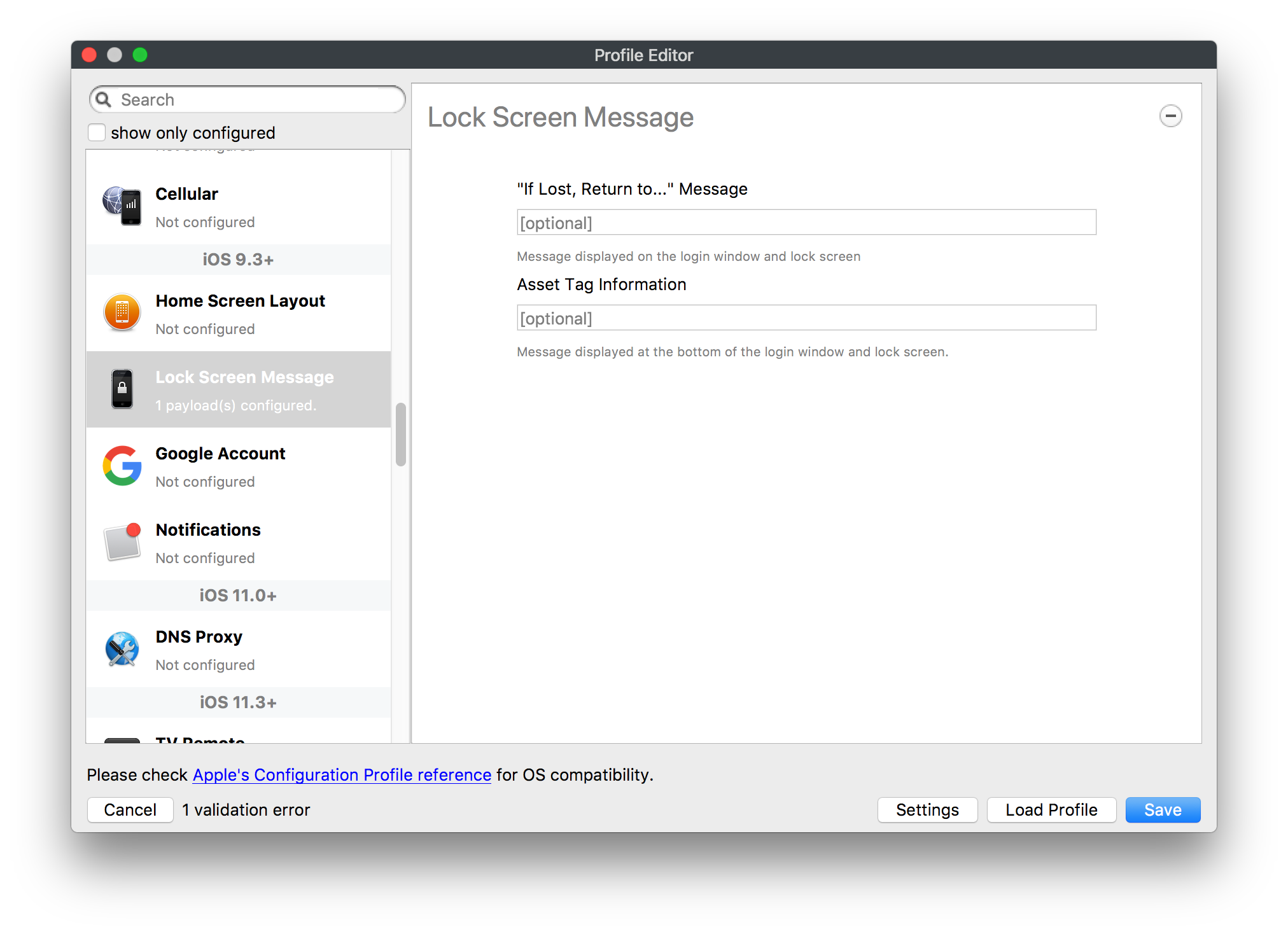](https://kb.filewave.com/uploads/images/gallery/2023-07/SfeHRXZiQnuIilof-image.png) This allows you to specify the text to be displayed in the login window and on the lock screen. Devices do not have to be supervised to use this payload type. ### Google Account [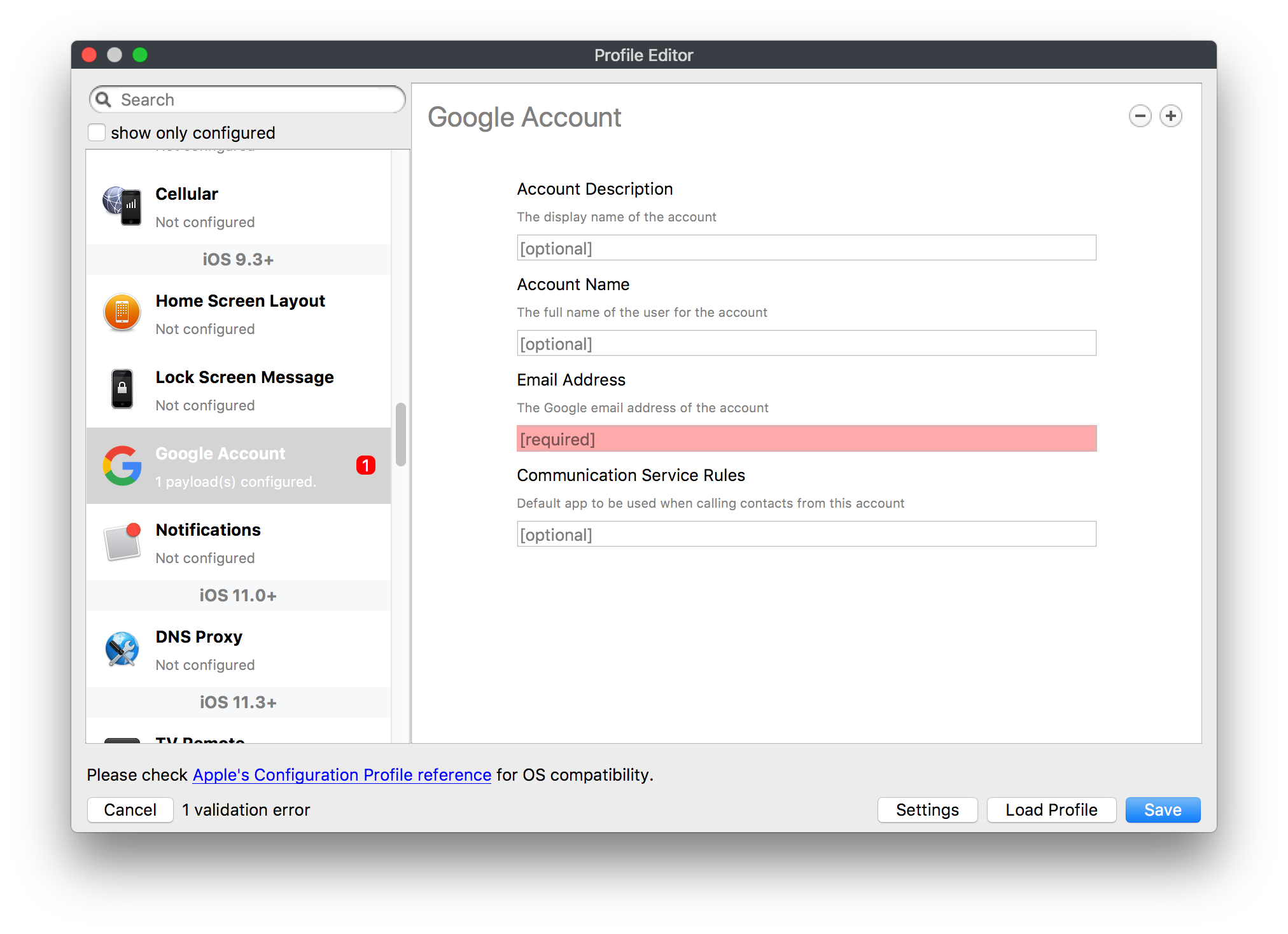](https://kb.filewave.com/uploads/images/gallery/2023-07/gInXBchtGnxEL7mZ-image.png) This payload type is used to configure Google accounts. The user will be prompted to sign in to the configured account(s). ### Notifications [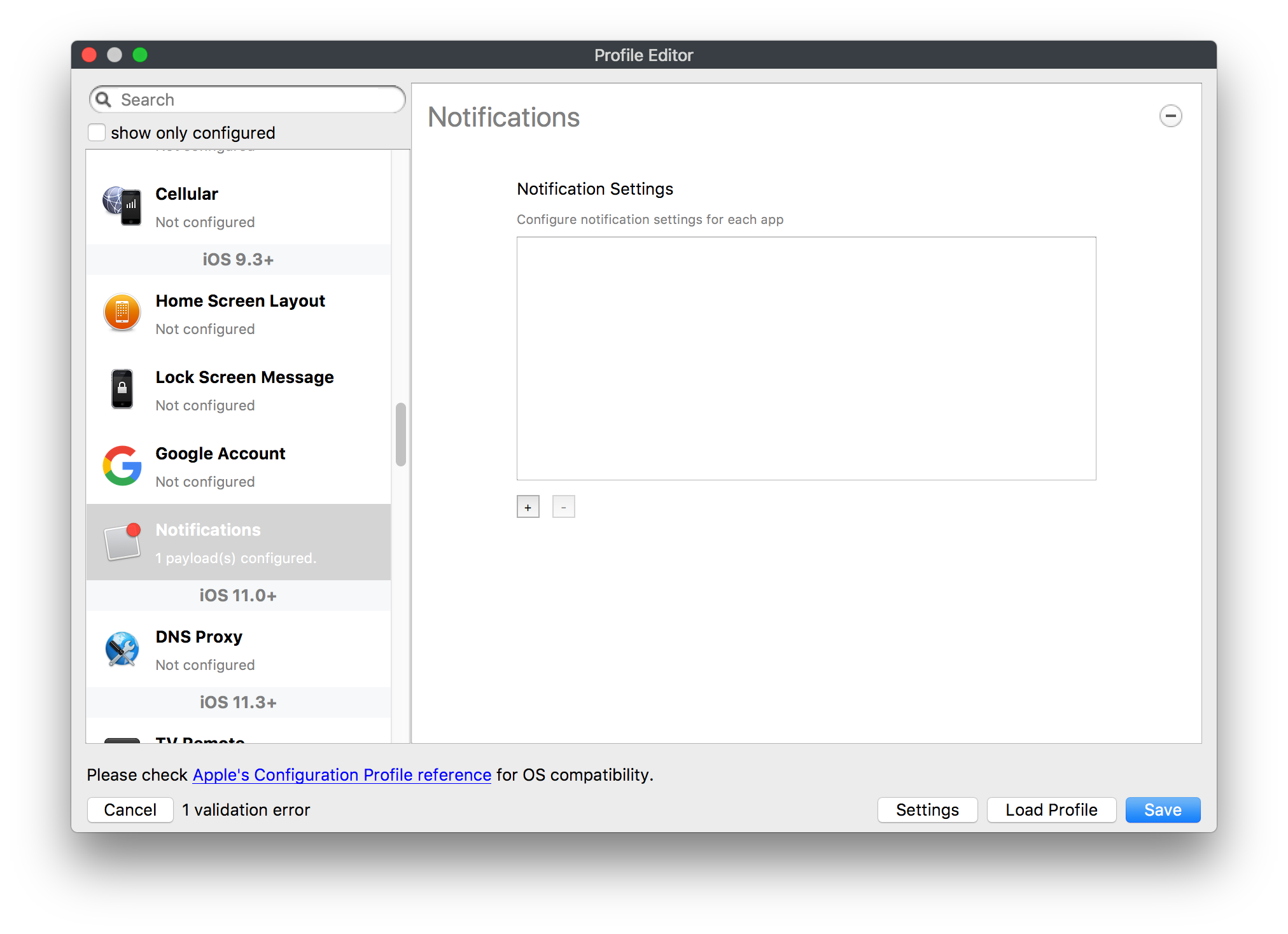](https://kb.filewave.com/uploads/images/gallery/2023-07/YPqr3FCHNgp3BpSm-image.png) [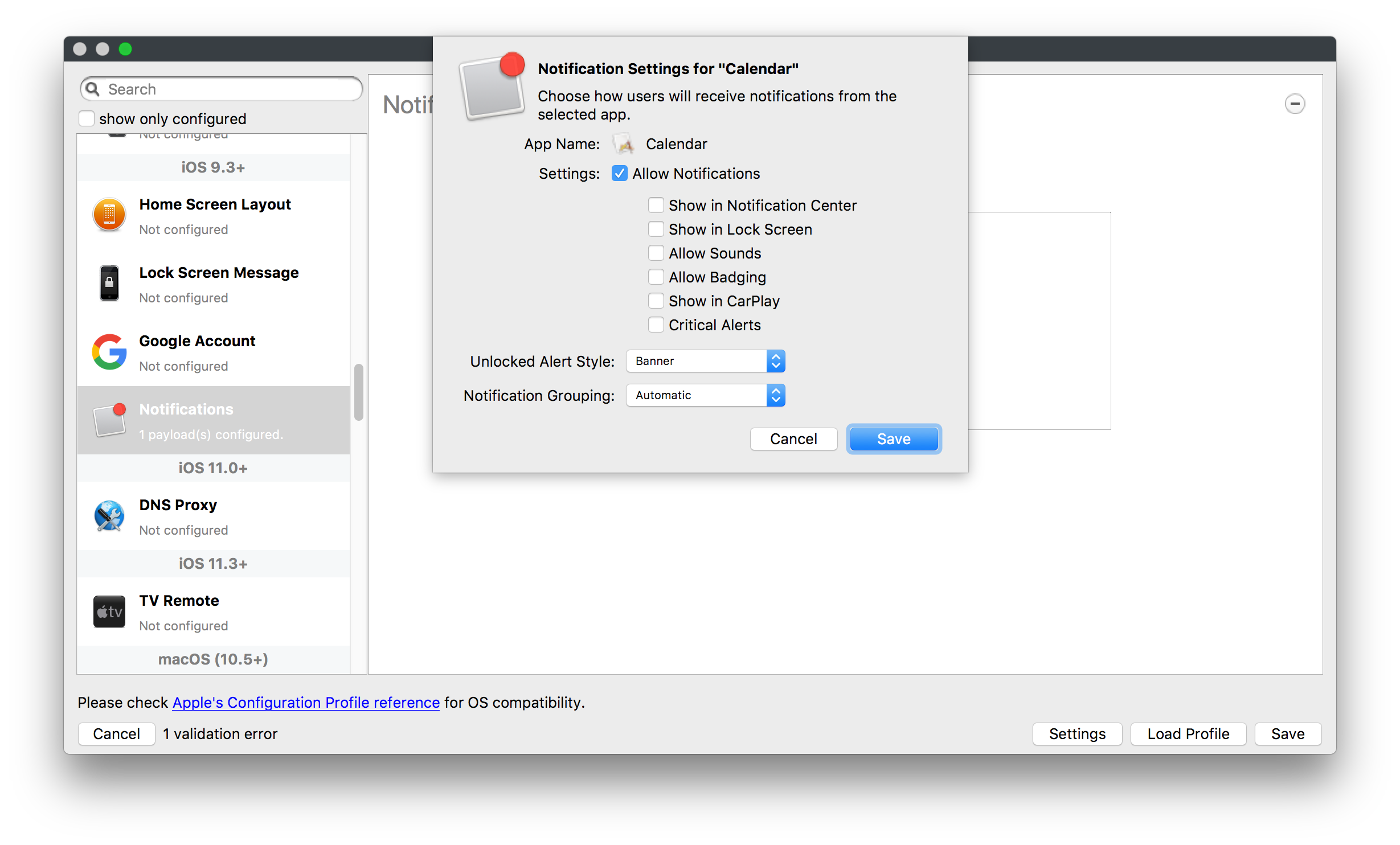](https://kb.filewave.com/uploads/images/gallery/2023-07/lw7JdM7KARMvZd06-image.png) This payload type is used to enforce notification settings for each app. These settings only affect supervised devices. ## iOS 11.0+ ### DNS Proxy (supervised only) [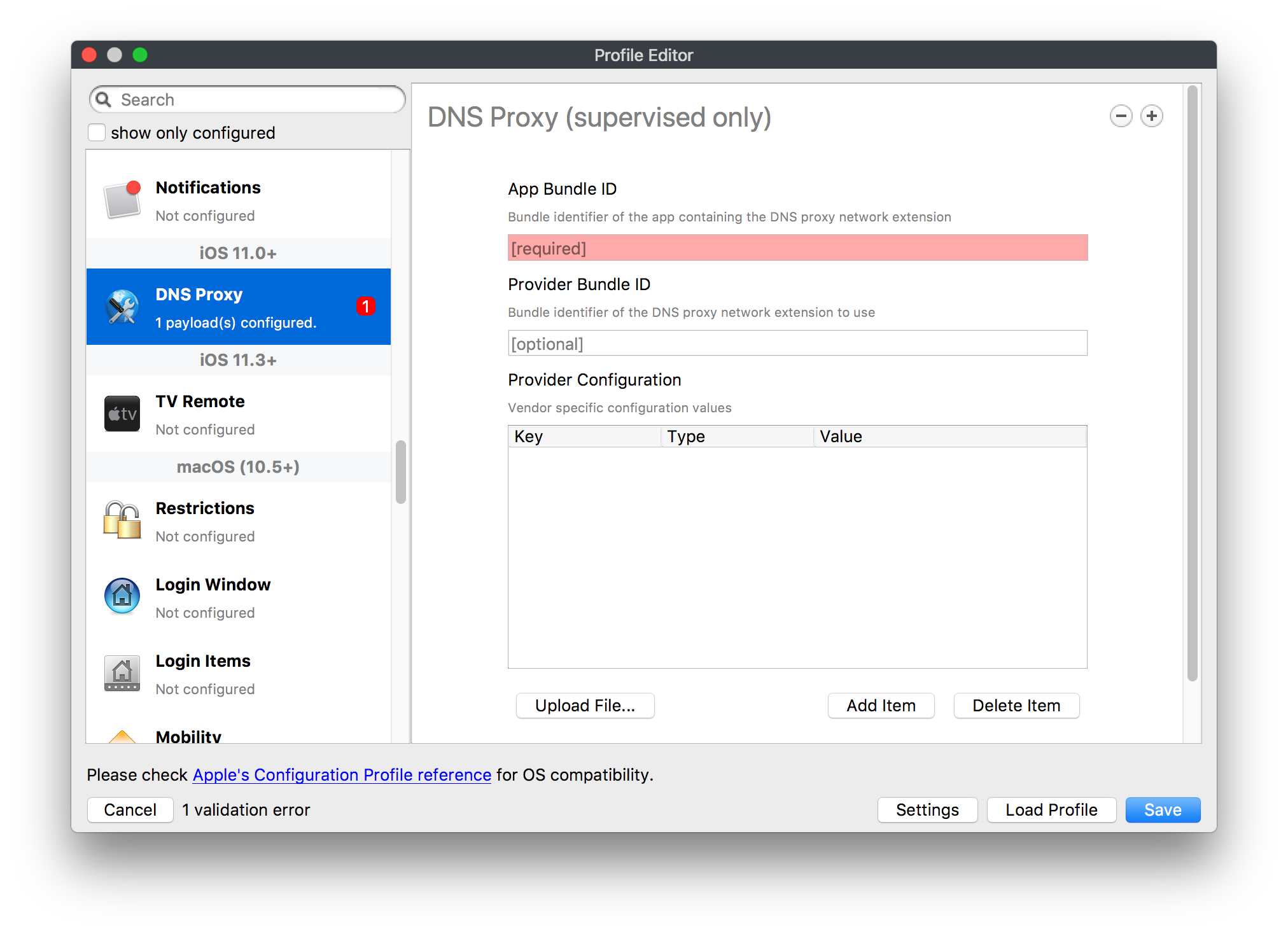](https://kb.filewave.com/uploads/images/gallery/2023-07/XKo9A7fuAcpD1DVr-image.png) Use this section to configure DNS procy settings. These settings will only affect supervised devices. ## iOS 11.3+ ### TV Remote (supervised only) [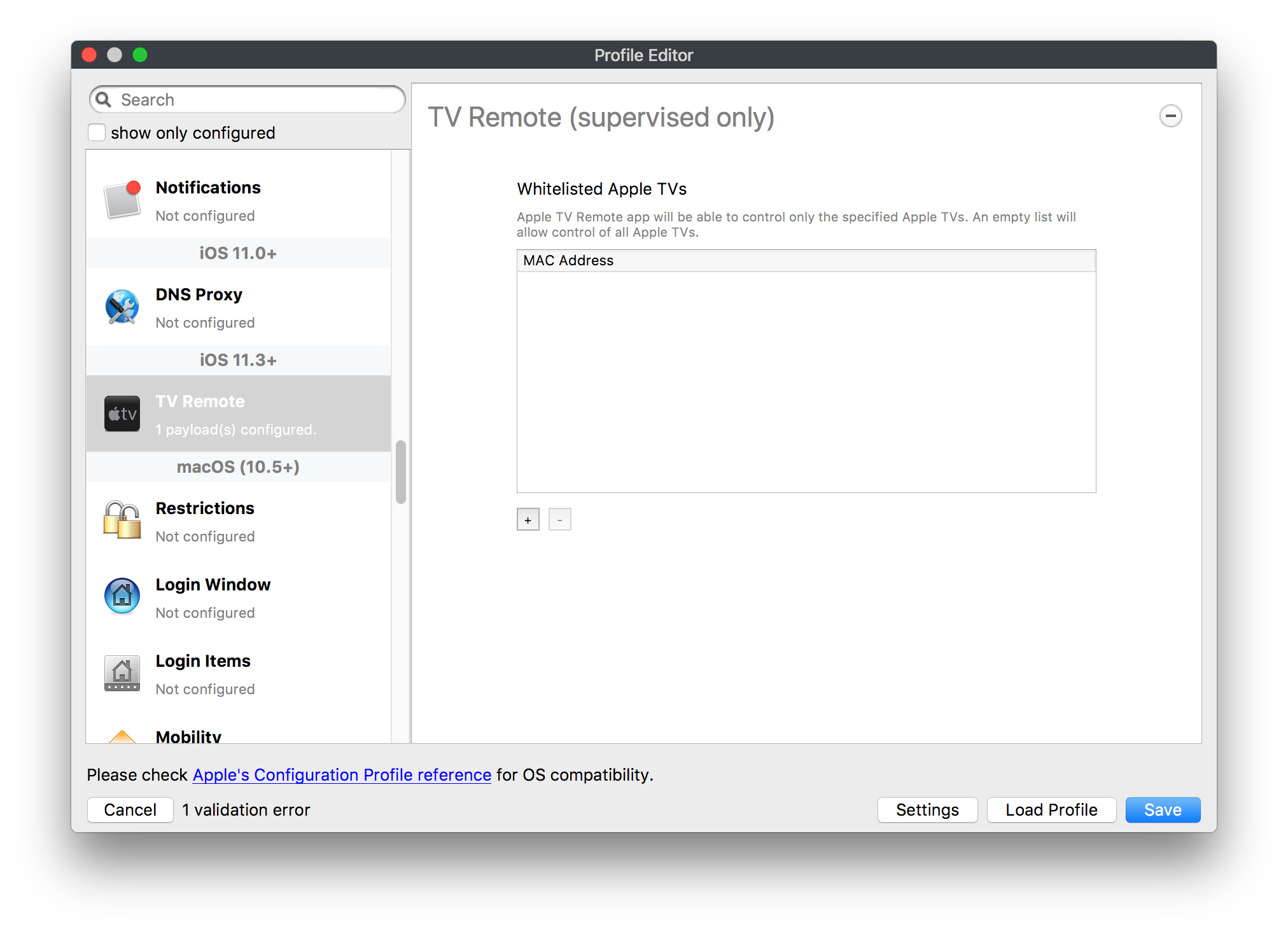](https://kb.filewave.com/uploads/images/gallery/2023-07/51kn1d4rrjGFHRr3-image.png) Use this section to configure the list of Apple TVs that can be controlled using the Remote app. these settings will only affect supervised devices. ## macOS (10.5+) These settings are for macOS only. Settings applied to systems running OS X pre-Lion will be sent as Managed Client property lists (mcx.plists); settings sent to OS X 10.7 – 10.11 and macOS Sierra (10.12) will be sent as managed profiles. **Note: In order to keep using mcx.plists, you must be using the 8.1.5 version of the FileWave client. Newer versions of the client do not convert profiles to mcx.plists.** ### Restrictions [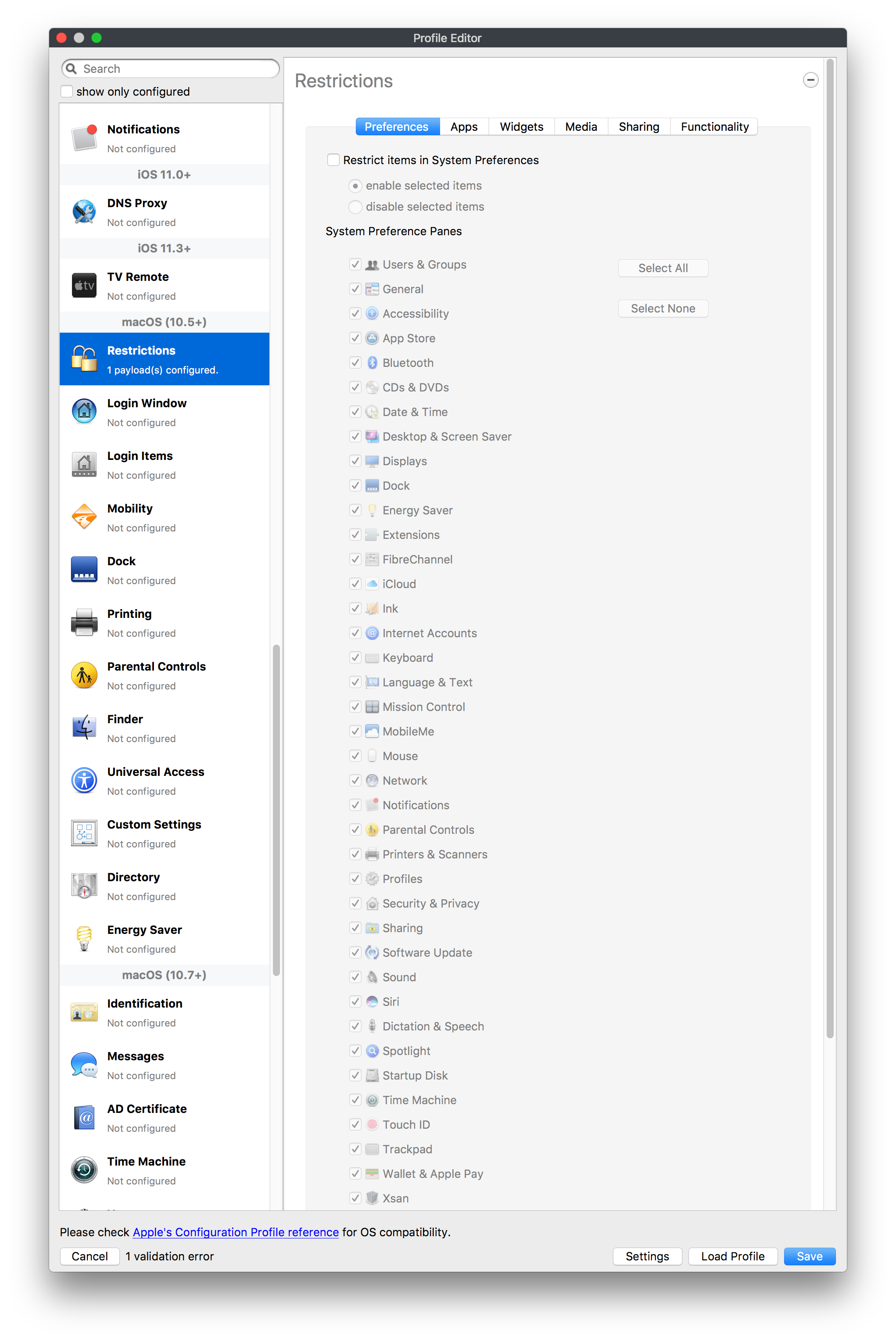](https://kb.filewave.com/uploads/images/gallery/2023-07/o5ZbwGaZfRiqIjFD-image.png) [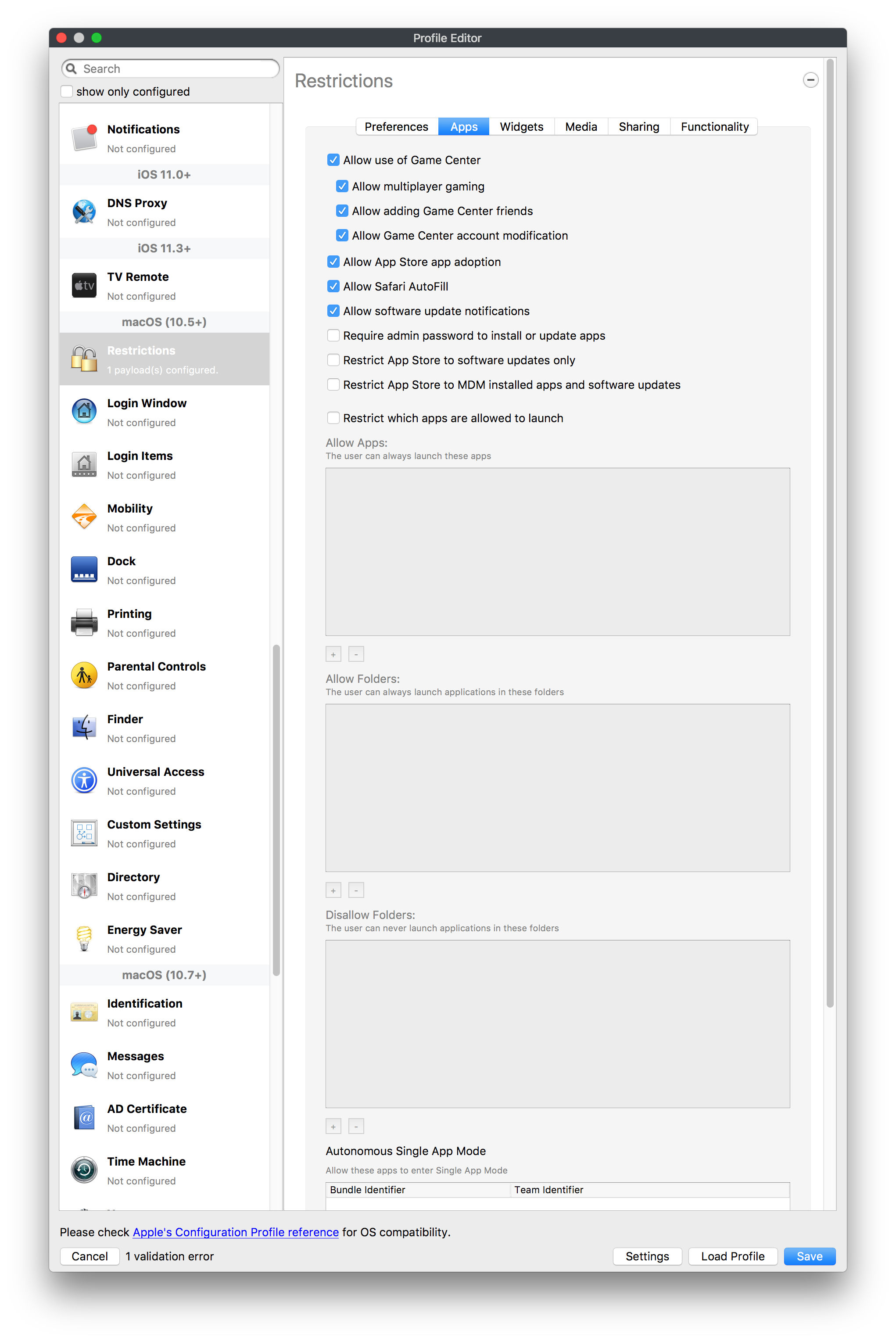](https://kb.filewave.com/uploads/images/gallery/2023-07/nckFUyqW2YIgNjNv-image.png) [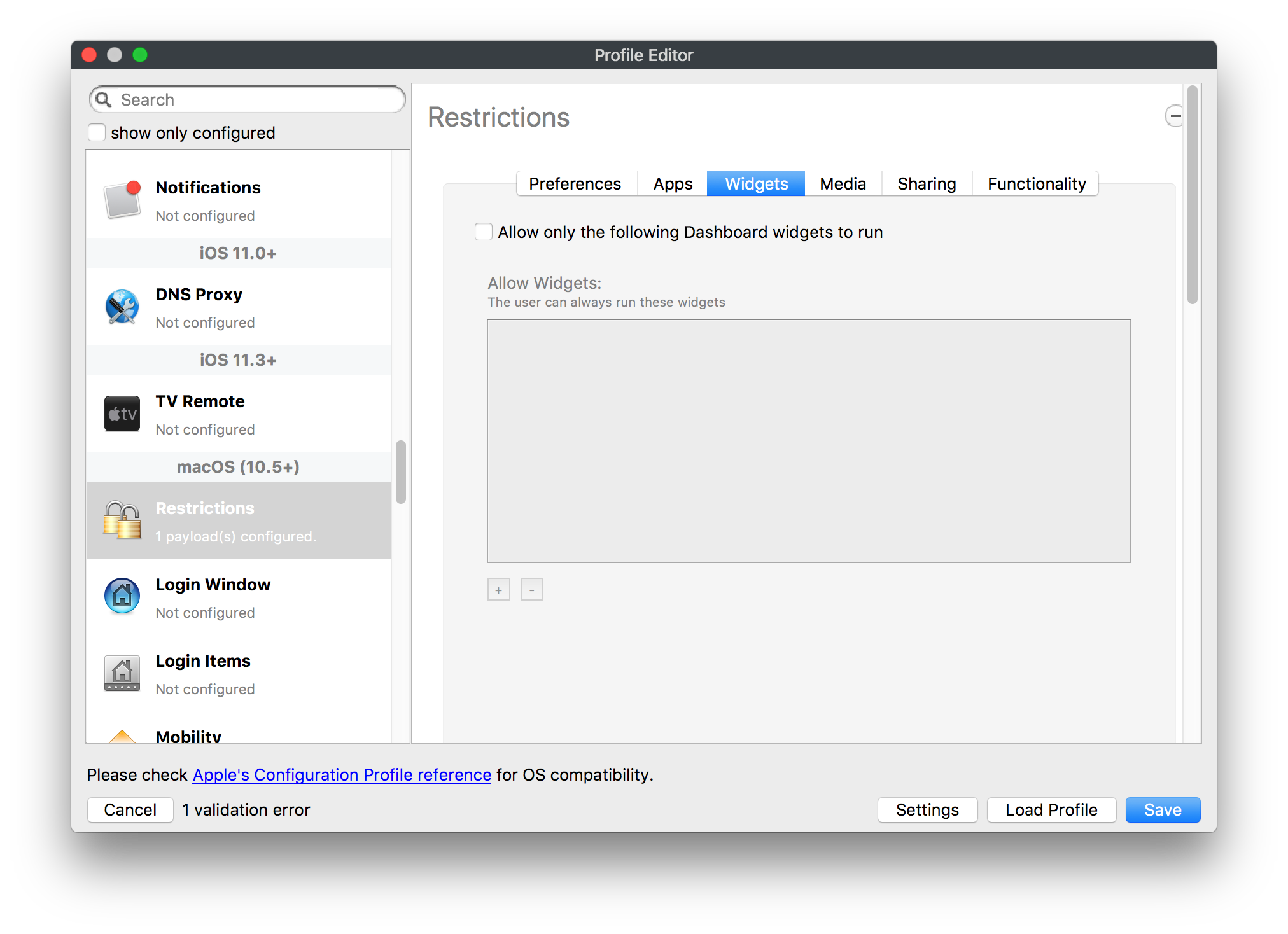](https://kb.filewave.com/uploads/images/gallery/2023-07/F90QWIetgkaMnqDq-image.png) [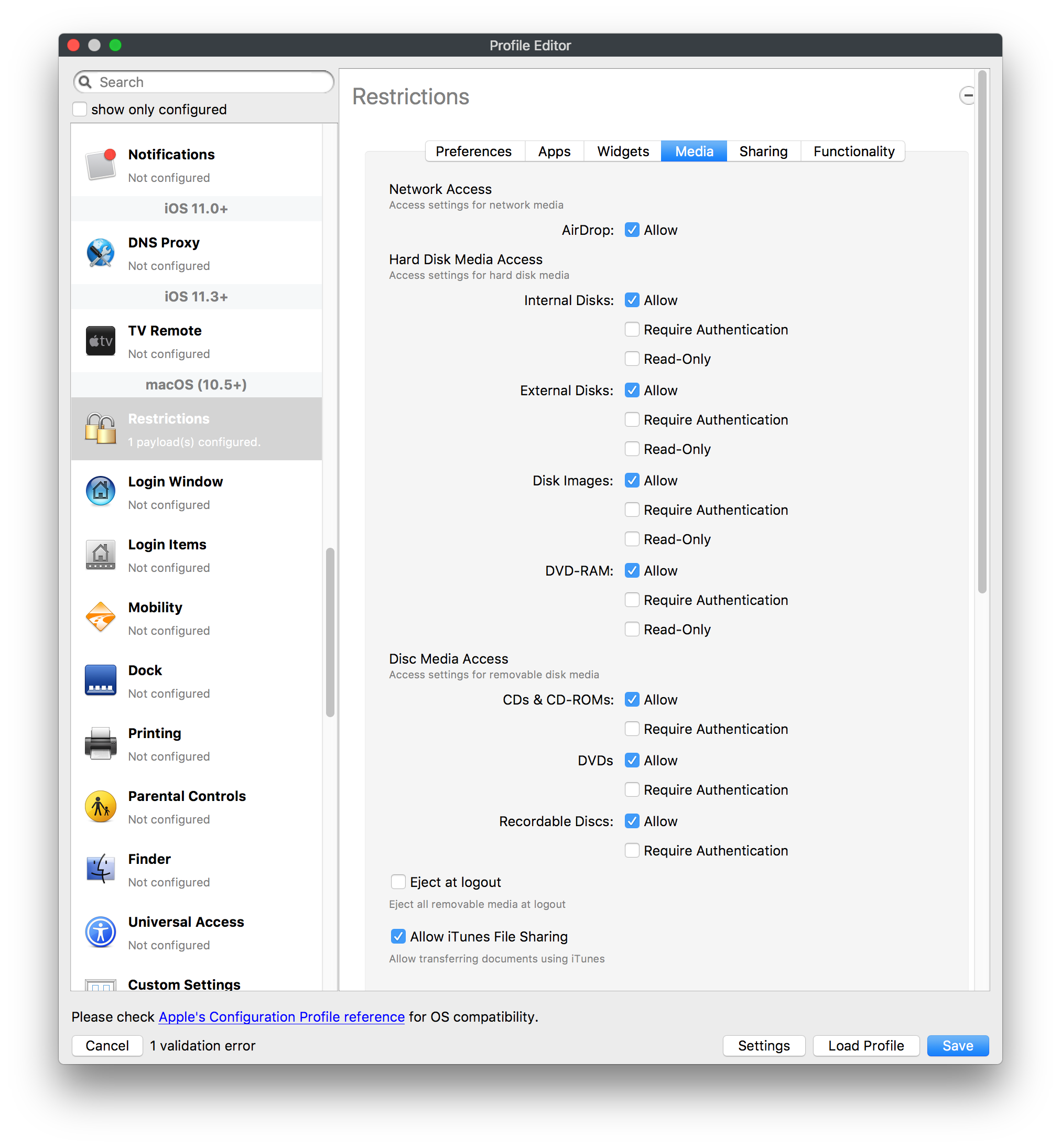](https://kb.filewave.com/uploads/images/gallery/2023-07/TiLGQUZi92PWm3xf-image.png) [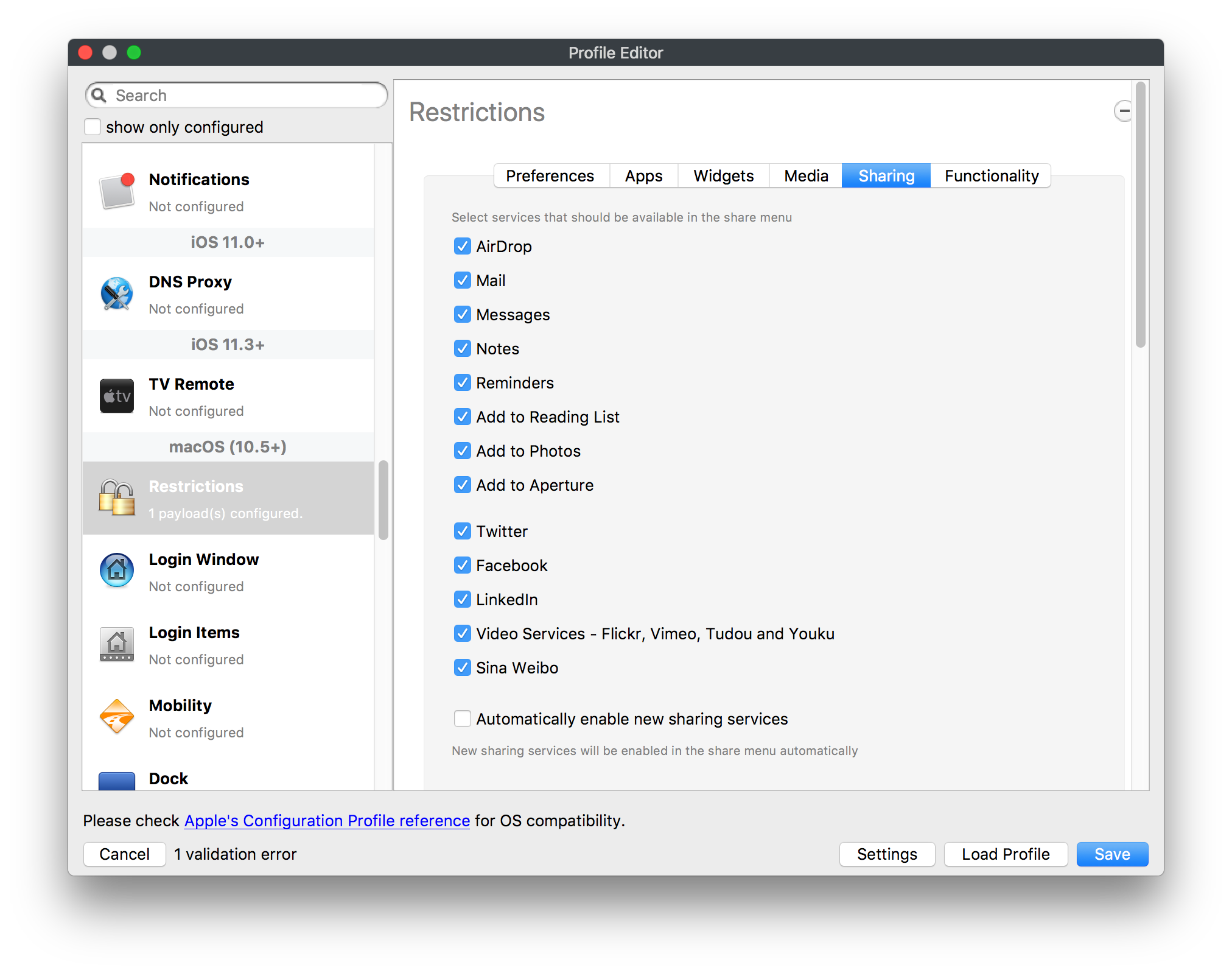](https://kb.filewave.com/uploads/images/gallery/2023-07/gzPwlibZbYNvP1RV-image.png) [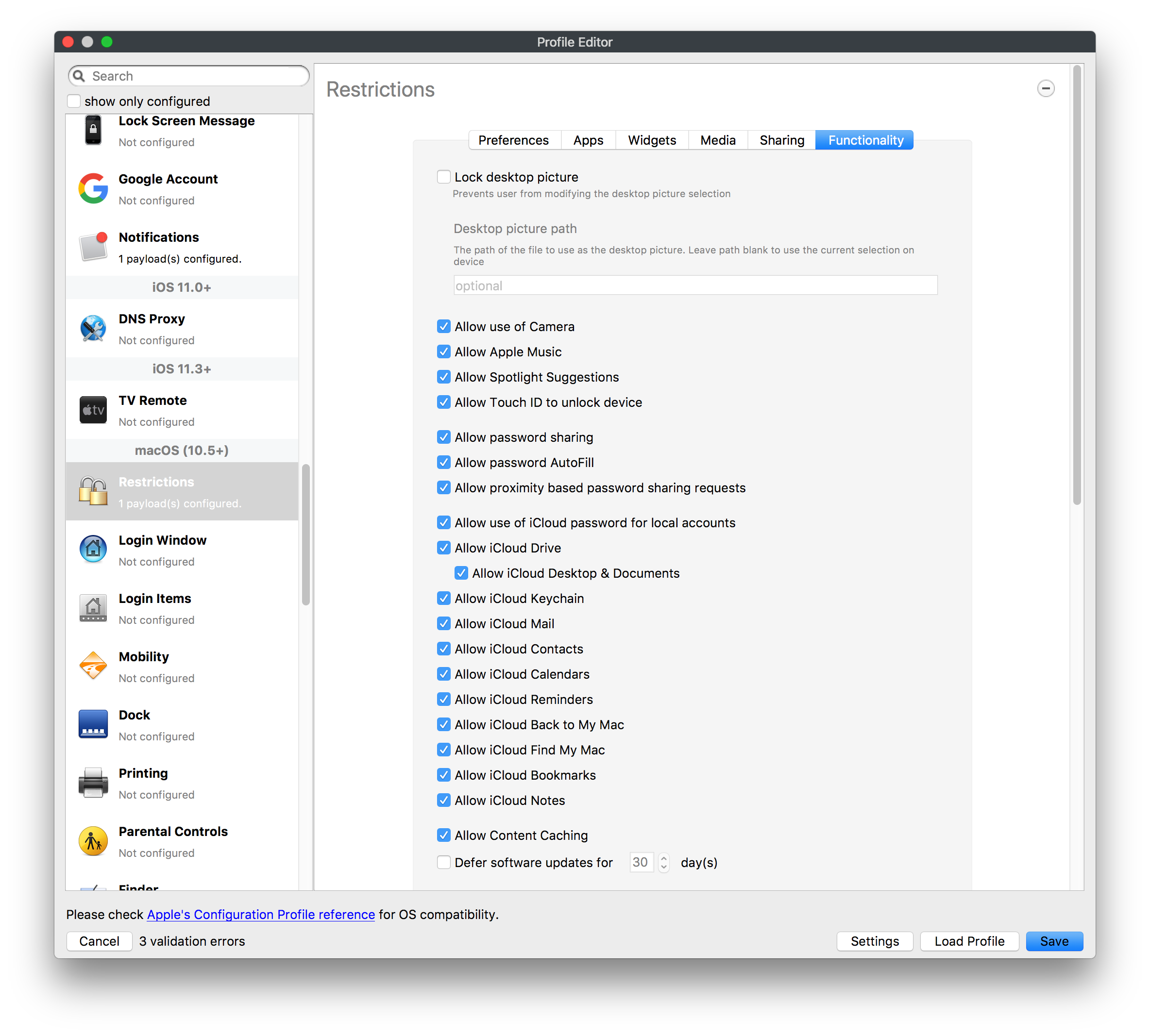](https://kb.filewave.com/uploads/images/gallery/2023-07/AwpHIIqBVYkH3OGq-image.png) The restrictions payload contains settings to limit access to system preferences, applications, Widgets, media, and sharing services. Preferences now includes all Systems Preferences plus the 3rd party Preference panes that are installed on the FileWave Admin machine. If you want to control 3rd party Preference panes on client devices, you must have that same item installed on your administration machine in order to have it show up in the list for management. For application control, the best practice is to designate the 'safe' paths for applications, such as /Applications; then designate restricted paths to 'unsafe' areas. Do not try to specify all 'allowed' applications because you will also have to locate all helper and sub-launched apps. Some of the settings include control over AirDrop and App Store app adoption, Other settings include the ability to manage access to media, such as external drives, USB flash drives, and Game Center, plus the ability to manage access to shared services such as Twitter and Facebook. Desktop settings allow control of the Desktop picture, Camera use, iCloud documents, data and passwords, and Spotlight suggestions. ### Login Window [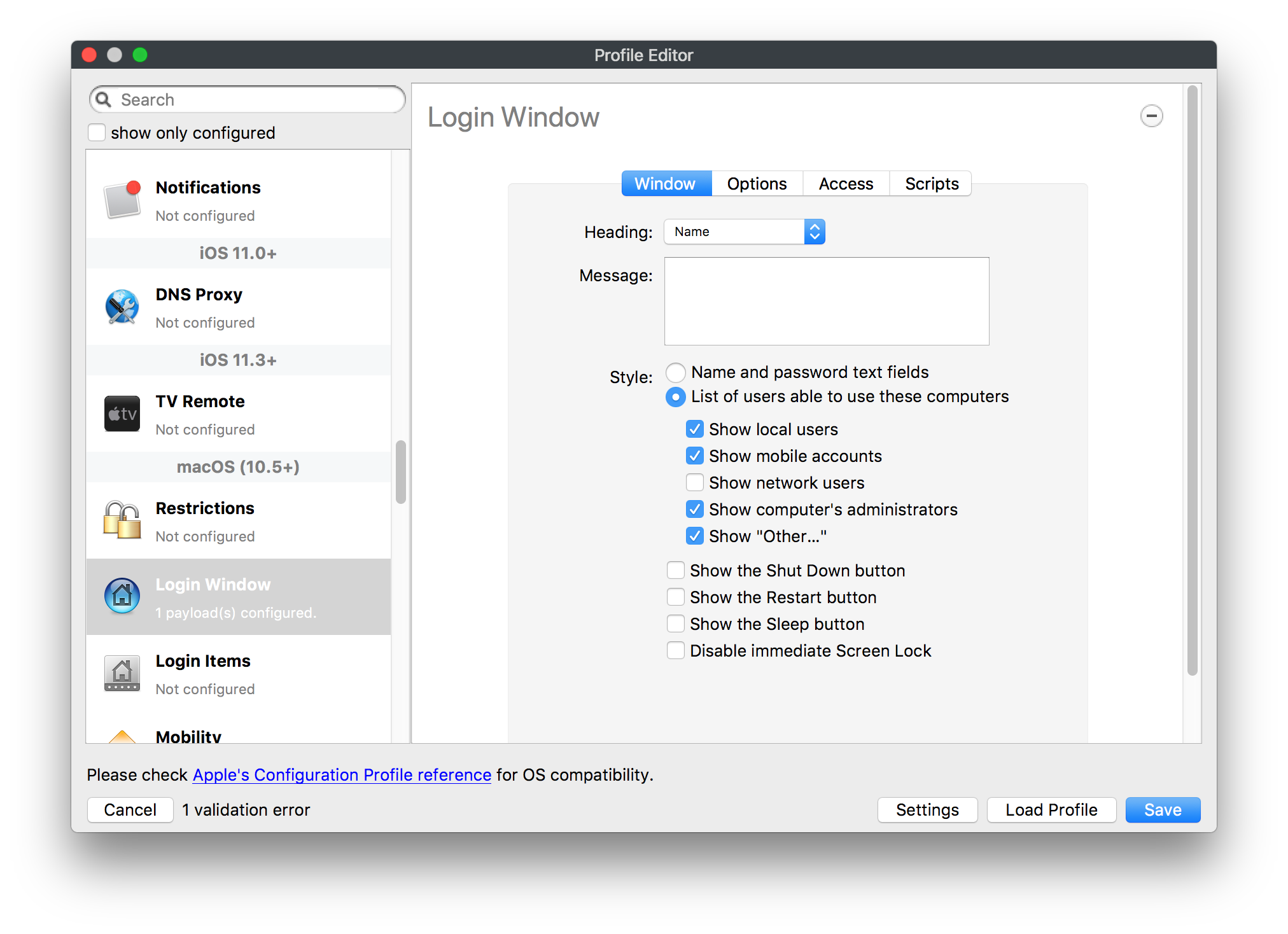](https://kb.filewave.com/uploads/images/gallery/2023-07/ah3wwy0K1H6EWj69-image.png) [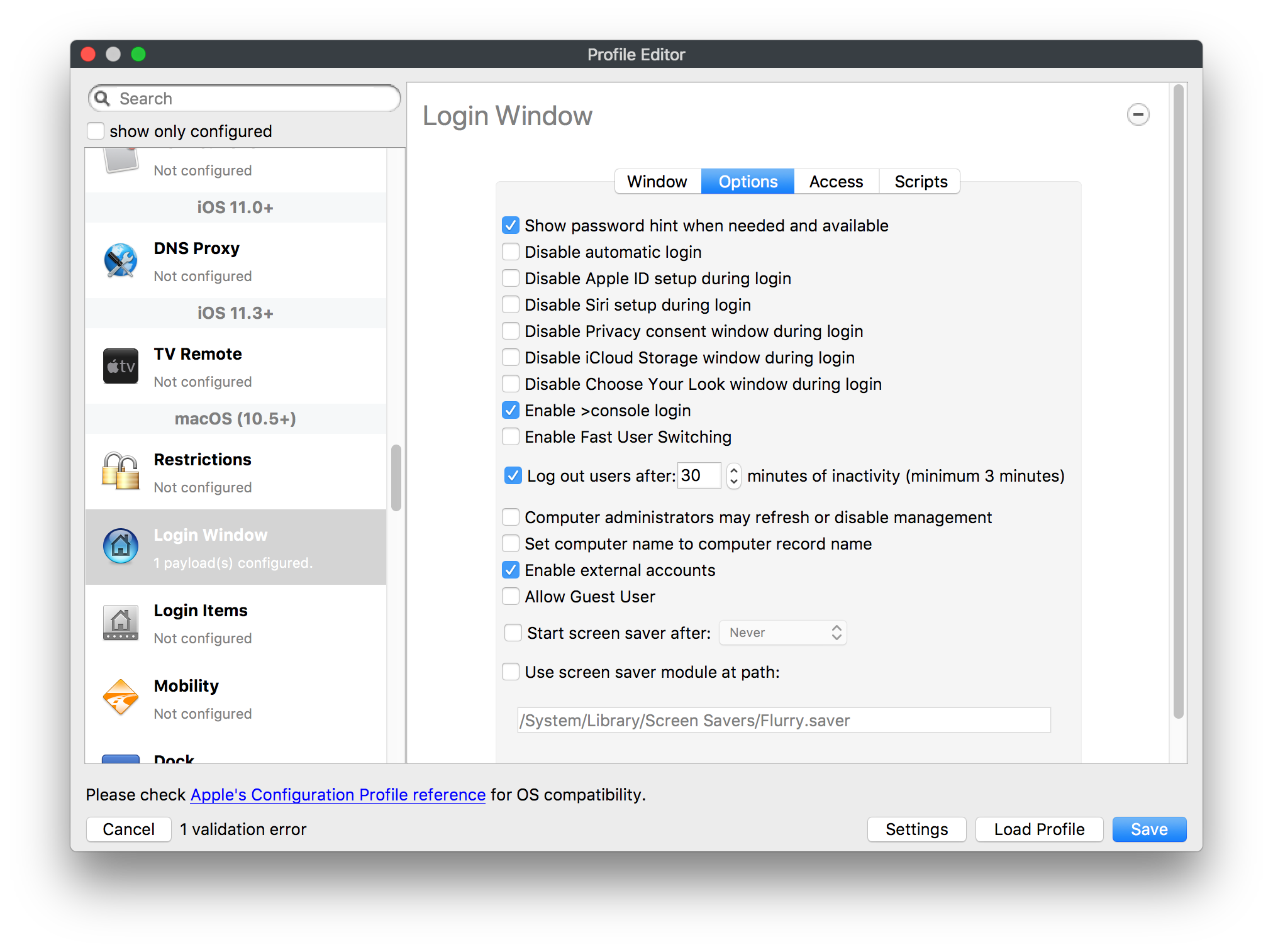](https://kb.filewave.com/uploads/images/gallery/2023-07/9hsr83OKz6refUAT-image.png) [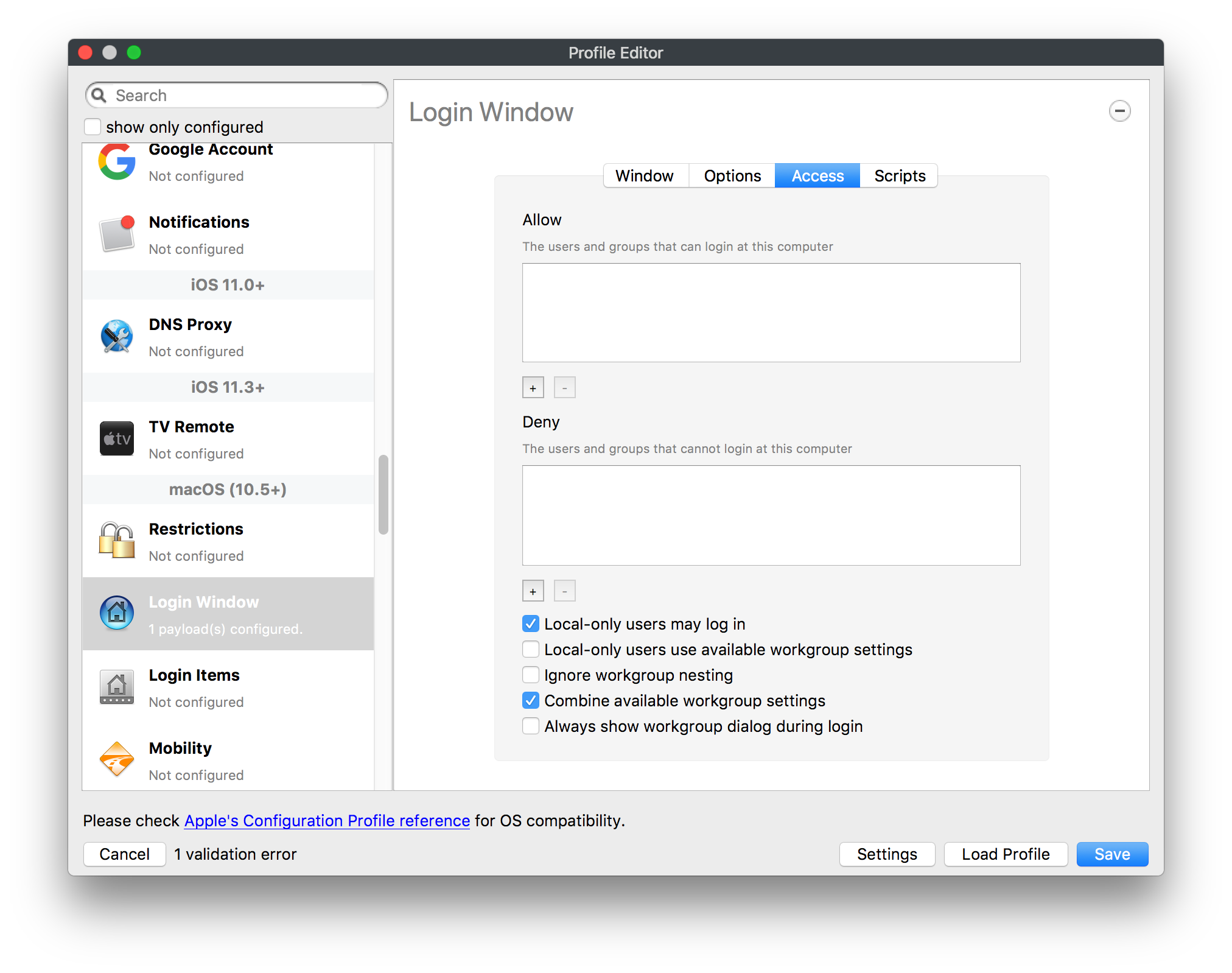](https://kb.filewave.com/uploads/images/gallery/2023-07/p06okRWxJ3b51V9M-image.png) [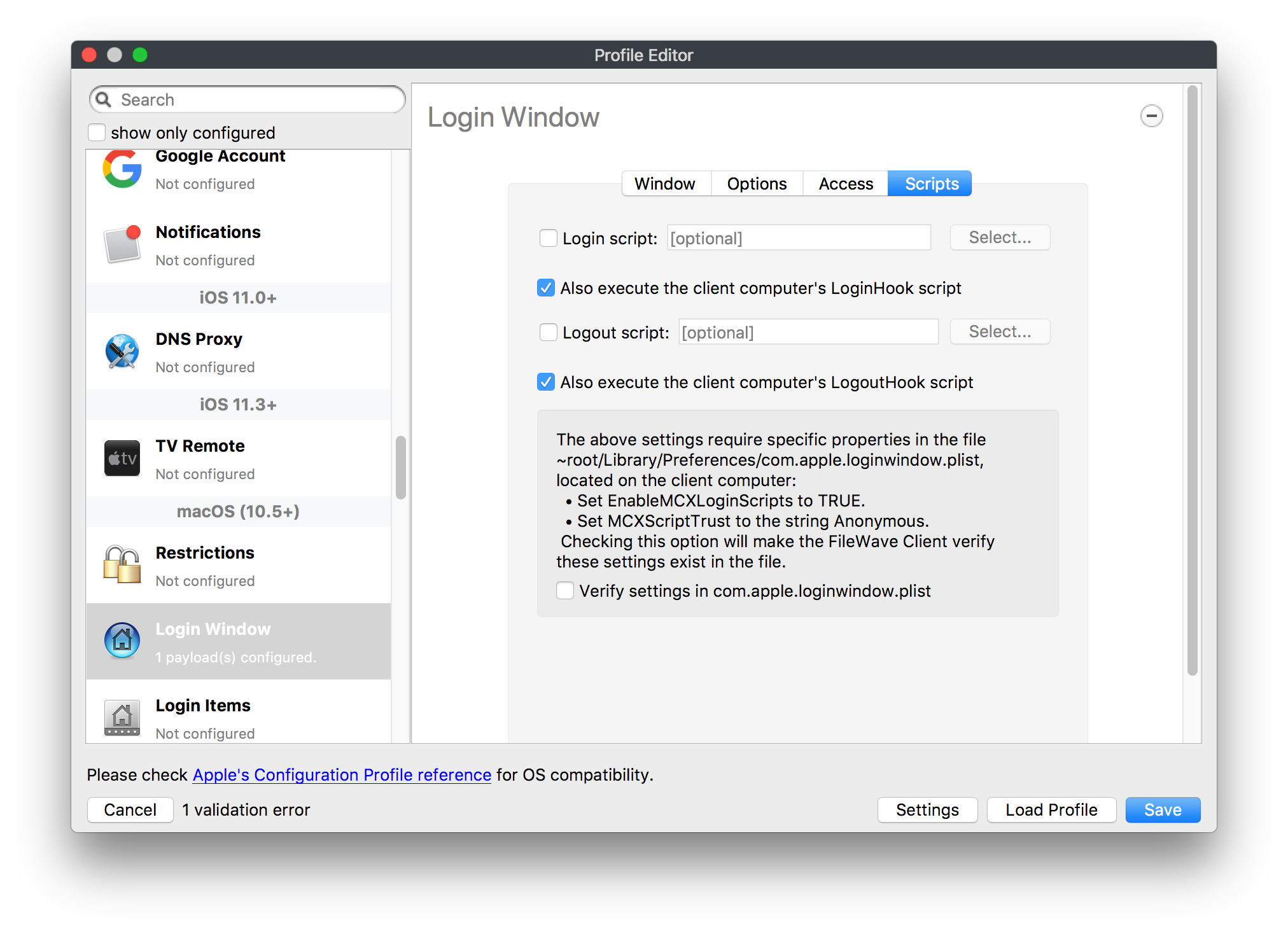](https://kb.filewave.com/uploads/images/gallery/2023-07/1sAwx2LLEvFWYvgS-image.png) The Login Window payload lets you configure the login window with a message, designate the type of login display (name/pwd or list), allow local administrators to bypass management, allow the Guest account, configure a login window screen saver, limit device access to certain Groups, and imbed login/logout scripts. ### Login Items [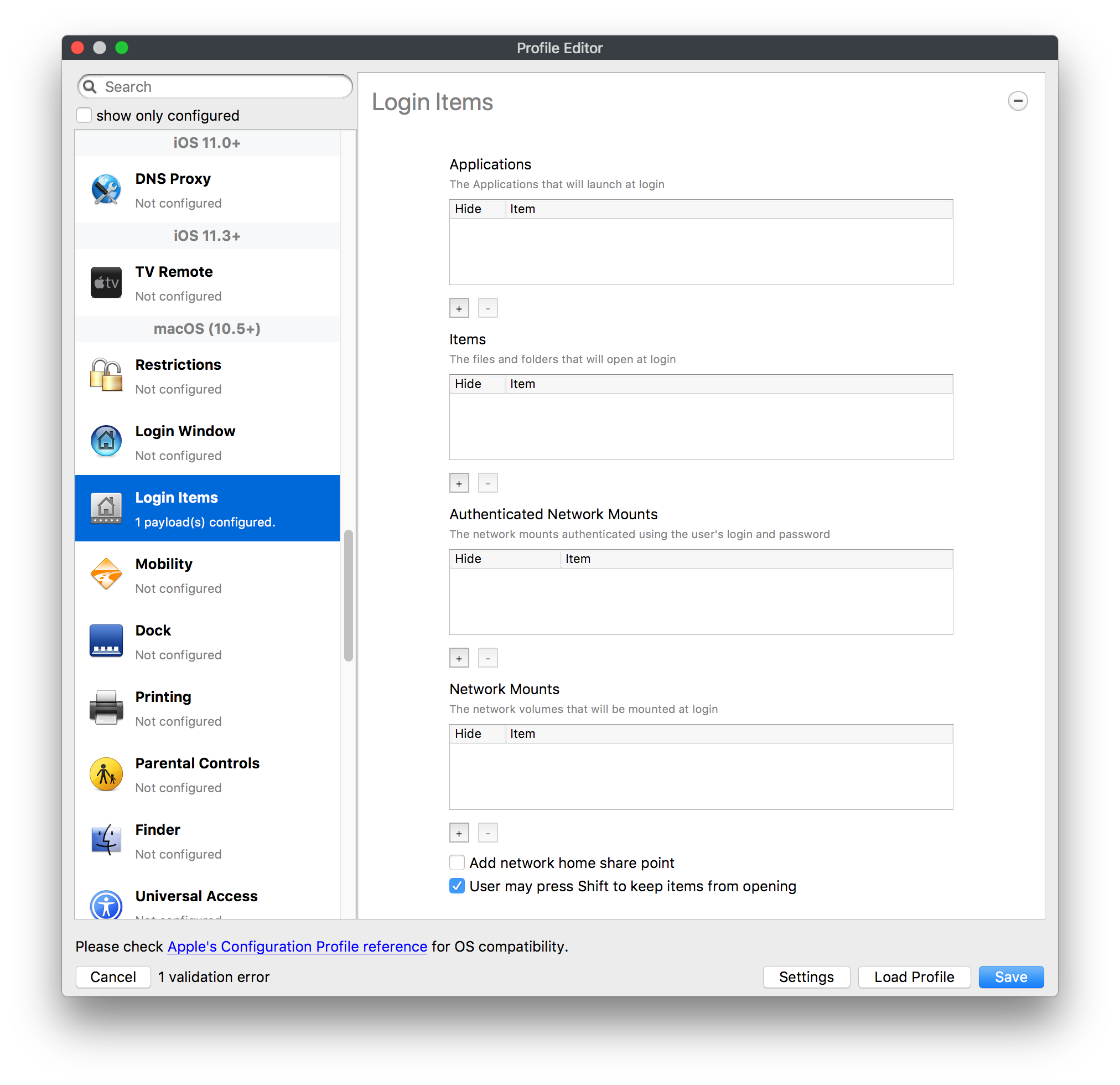](https://kb.filewave.com/uploads/images/gallery/2023-07/4f5ThW6MtkLhzPD4-image.png) Login Items is a payload that can contain specified applications and network sharepoints to be activated at user login. The designated items will launch or mount after the user logs in and the Finder launches. ### Mobility [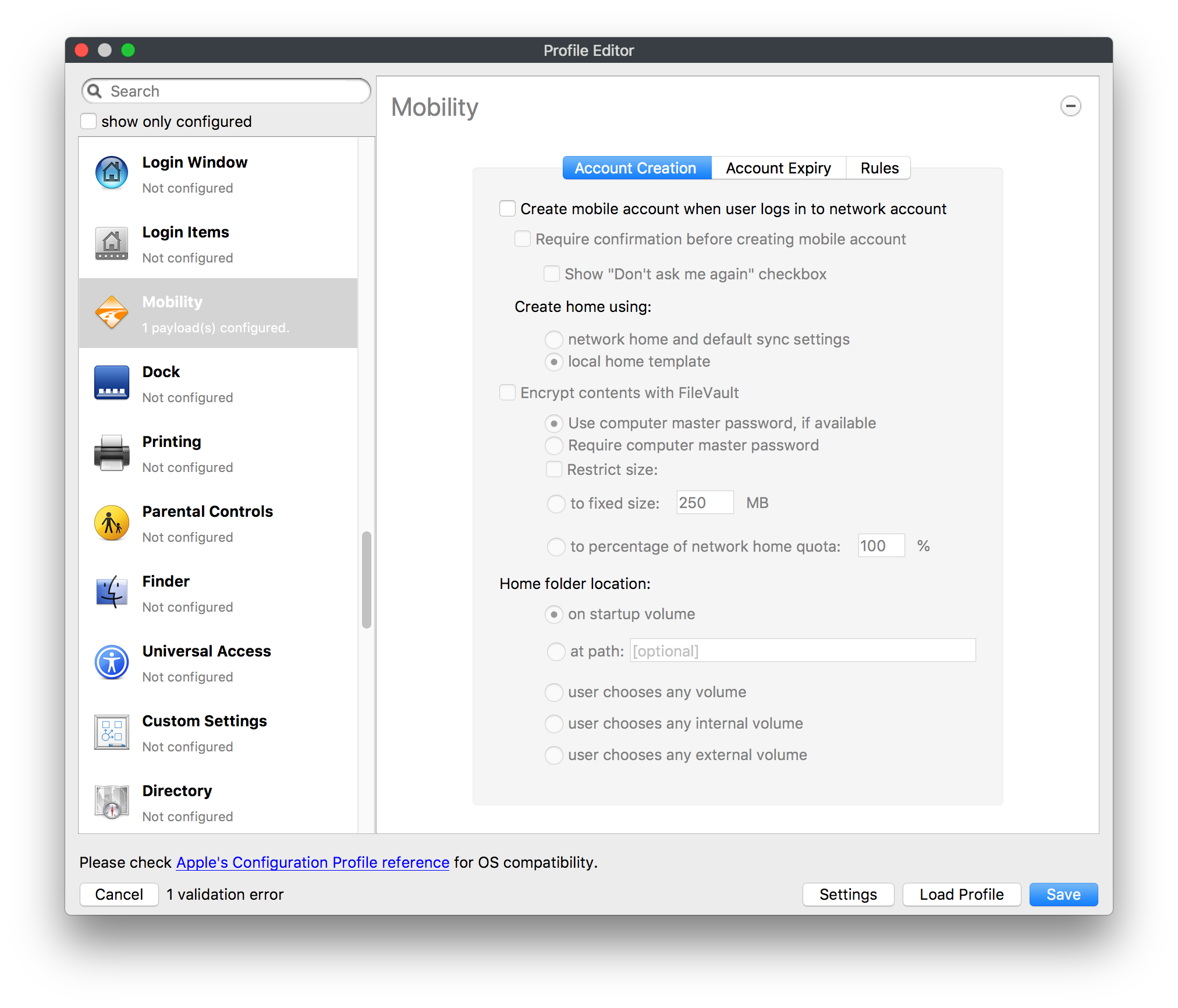](https://kb.filewave.com/uploads/images/gallery/2023-07/cVYYzrMztQknQFoi-image.png) [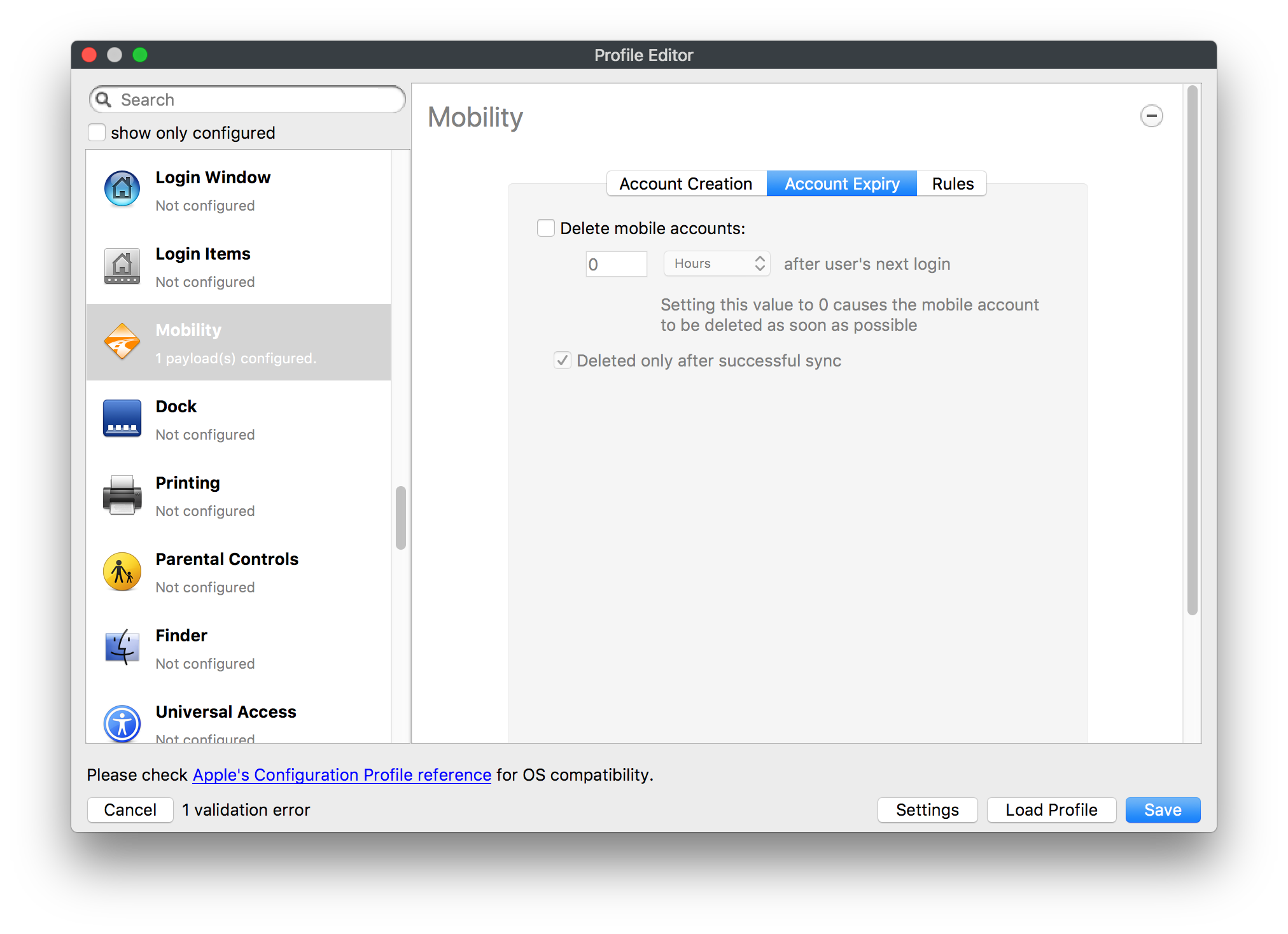](https://kb.filewave.com/uploads/images/gallery/2023-07/DddJOFSBwvohbBYL-image.png) [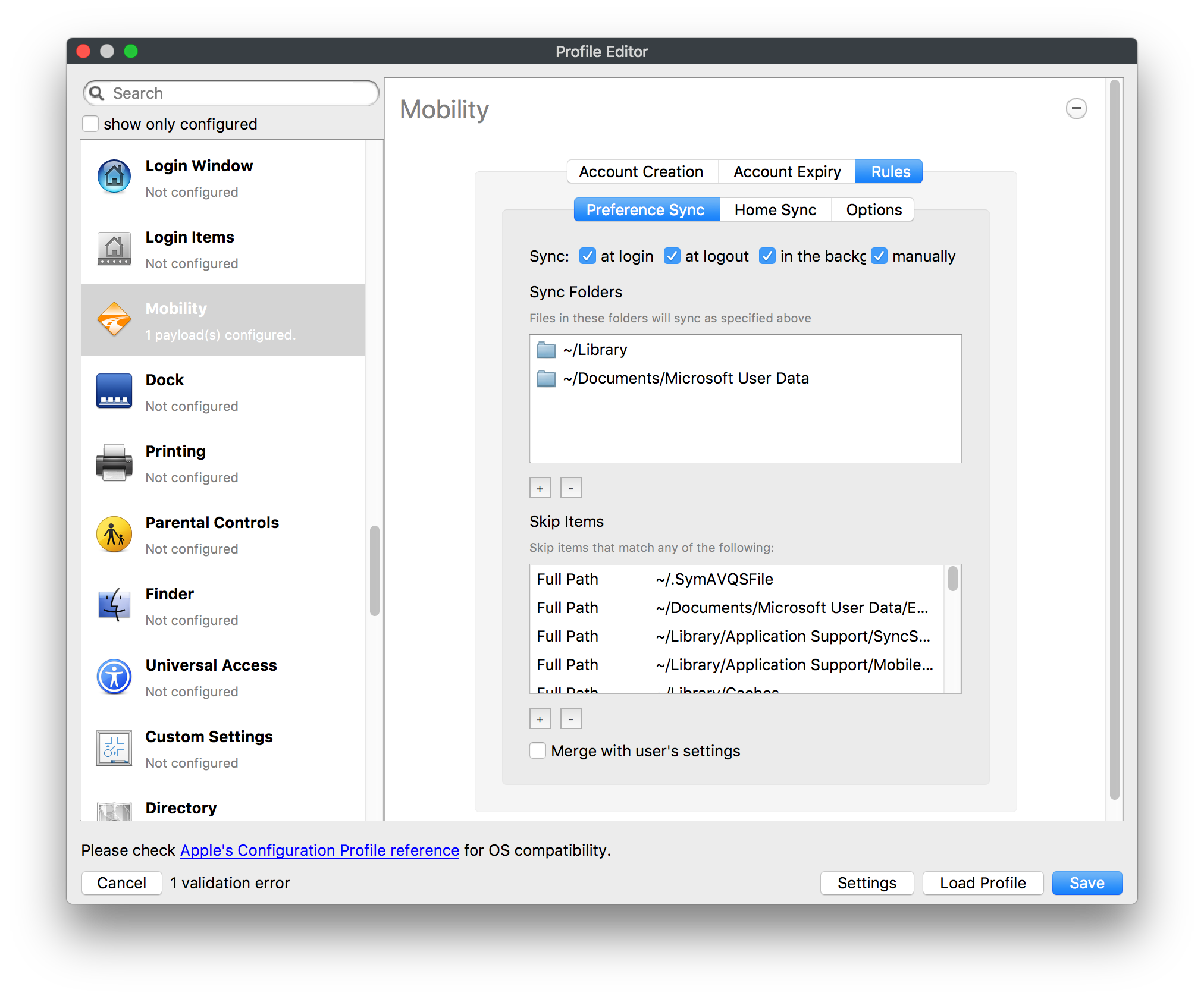](https://kb.filewave.com/uploads/images/gallery/2023-07/nqyH8ebAzr3Lh5xd-image.png) [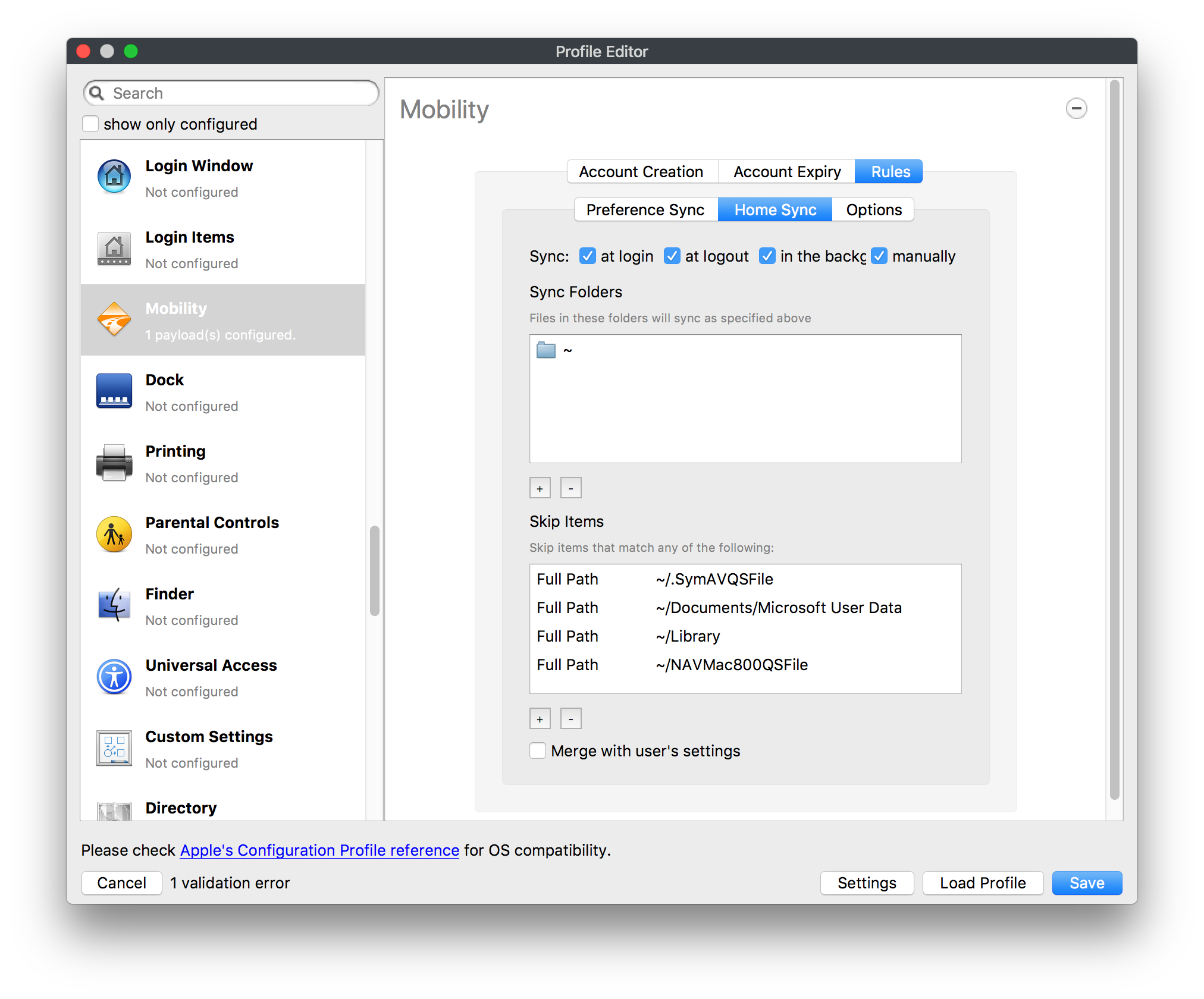](https://kb.filewave.com/uploads/images/gallery/2023-07/KKhFJwTiQ2AWdZ5h-image.png) [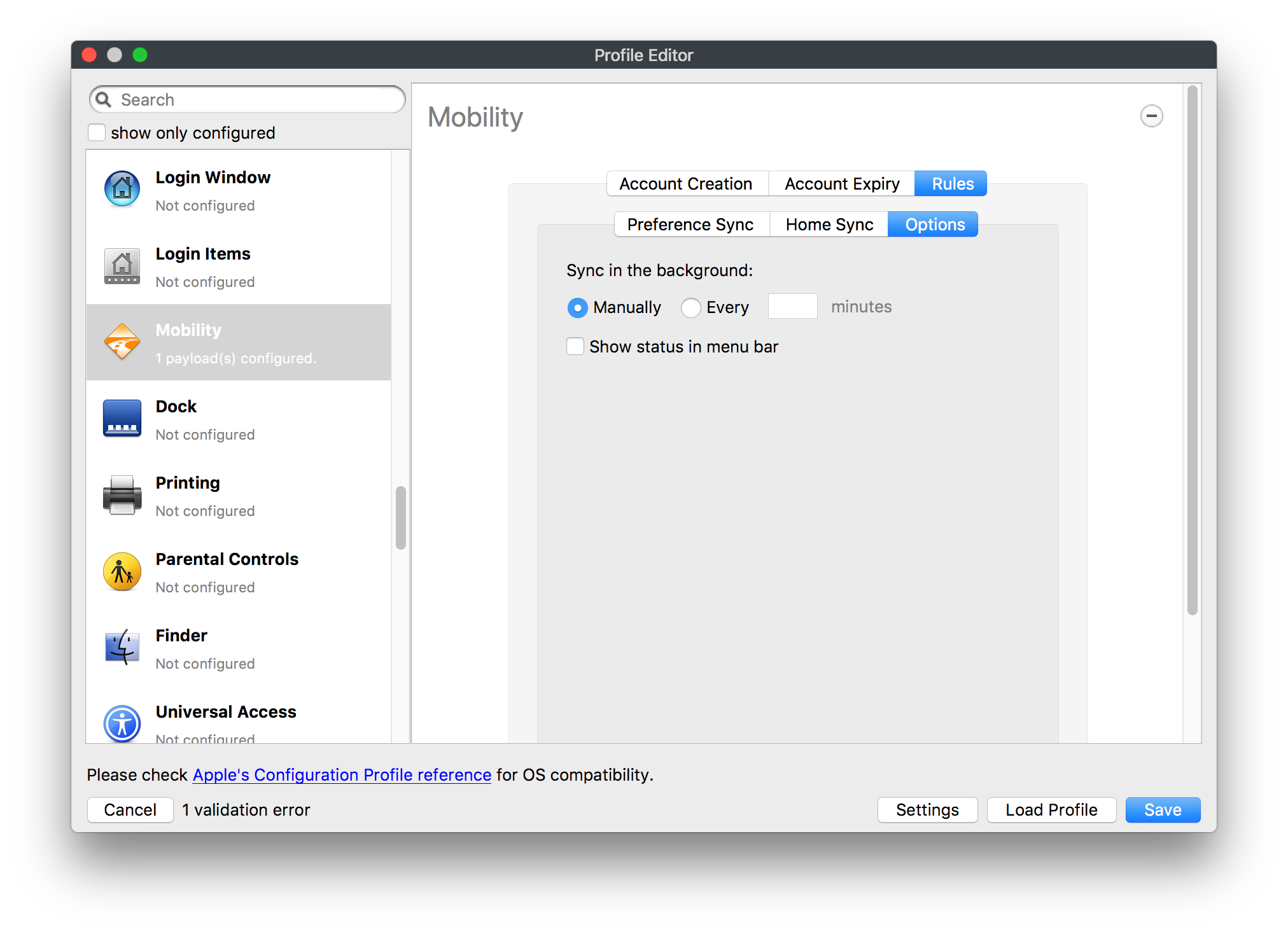](https://kb.filewave.com/uploads/images/gallery/2023-07/PANjviv0YHmNMe4p-image.png) Mobility allows you to create mobile accounts - network user accounts with portable home directories. Used in conjunction with the Login Window payload, you can specify support for the External account, which is a mobile account with an externally attached home directory. The idea is to have managed systems, bound to a network directory, where the user carries their home directory (USB/Thunderbolt drive) from device to device; but still logs in as a network directory account. ### Dock [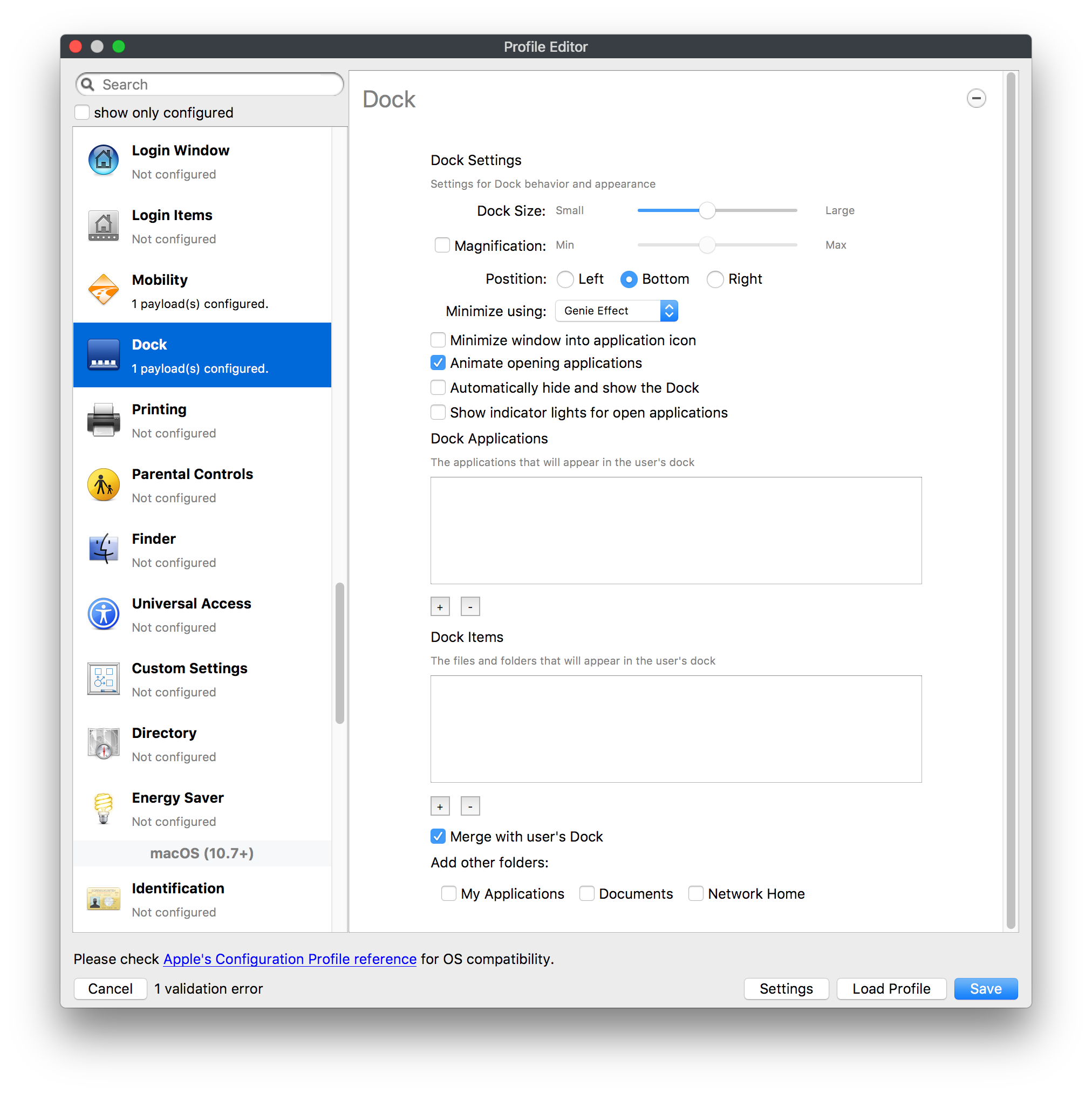](https://kb.filewave.com/uploads/images/gallery/2023-07/ungKApSIcvl9mxLP-image.png) The Dock payload can be configured for shared computers that need to have a consistent look and feel regardless of user. ### Printing [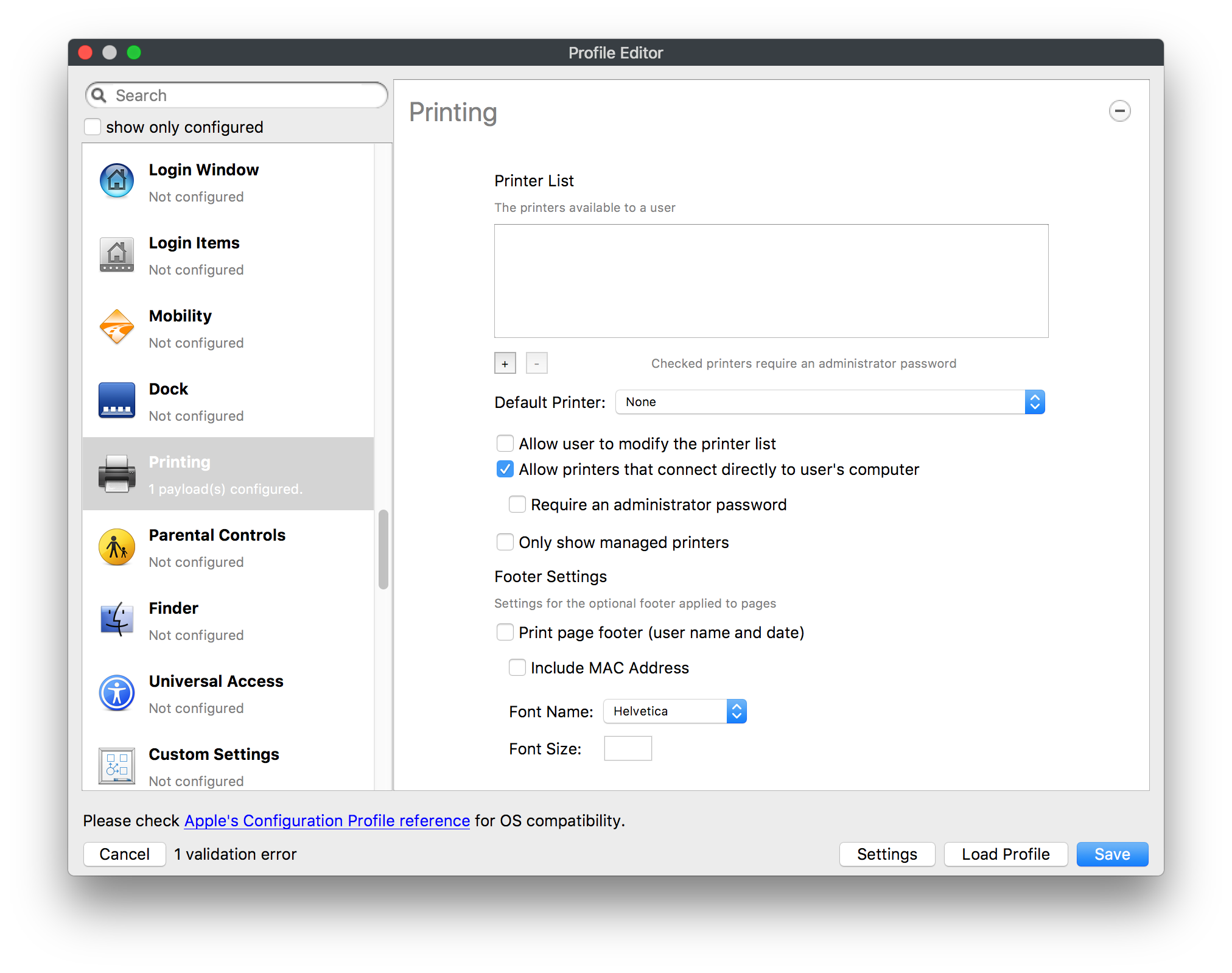](https://kb.filewave.com/uploads/images/gallery/2023-07/DQcFRWo5loaRbWek-image.png) Printing payloads allow the assignment of network printers to managed computers, as well as the ability to force all print jobs to contain the identity of the managed computer. ### Parental Controls [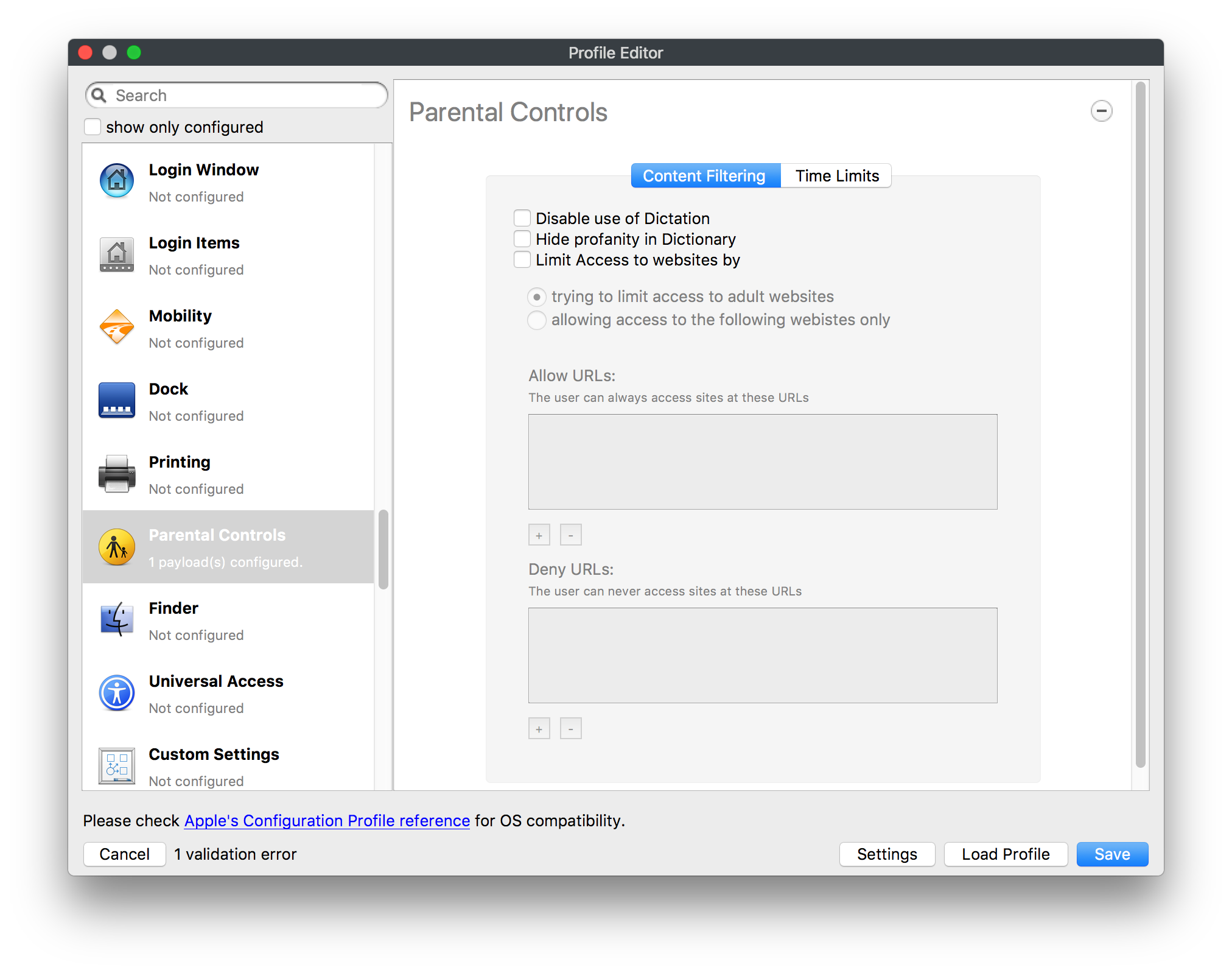](https://kb.filewave.com/uploads/images/gallery/2023-07/LhqSX7Ihq3QxLFsI-image.png) [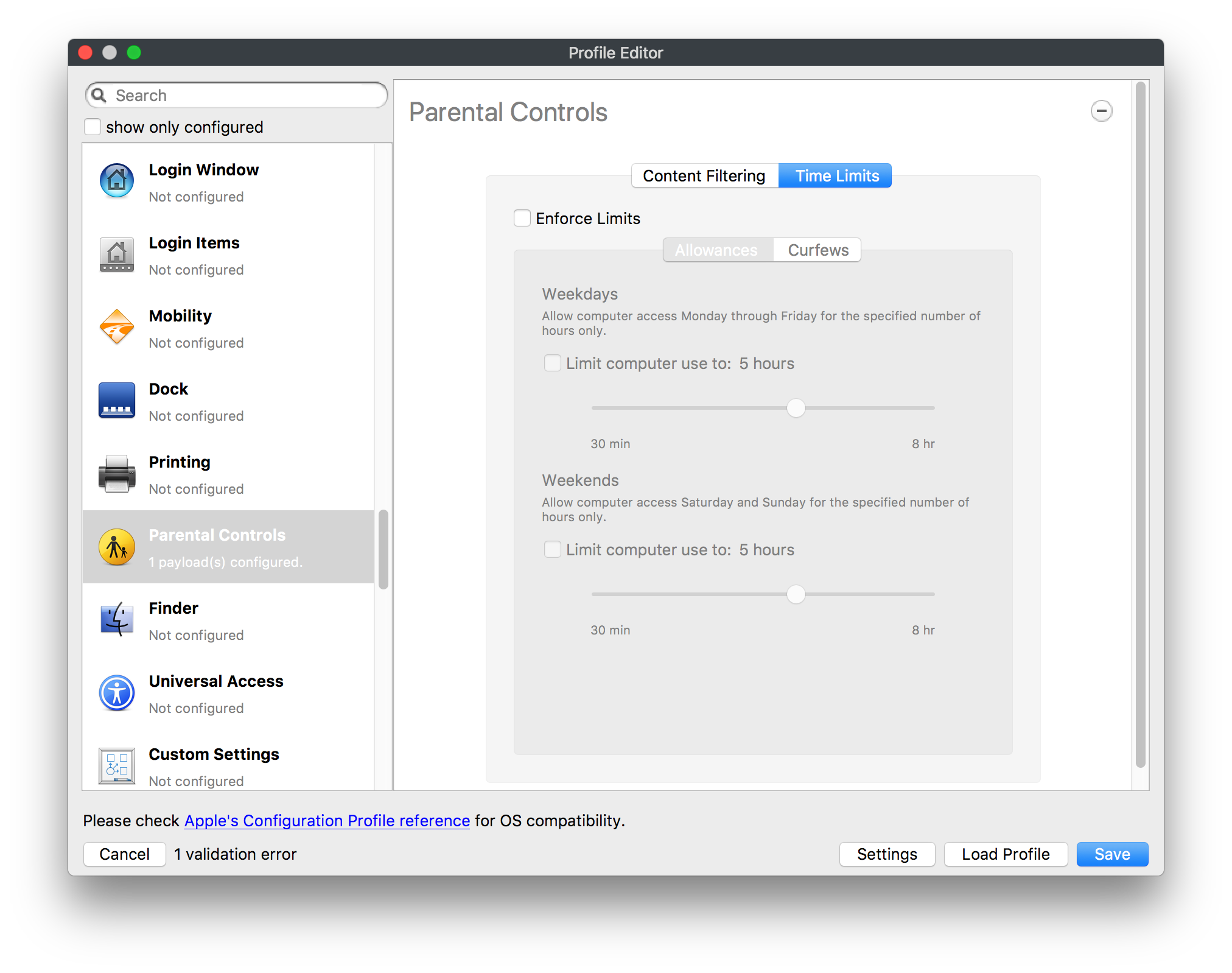](https://kb.filewave.com/uploads/images/gallery/2023-07/GbV9uUpS7HqgpktY-image.png) [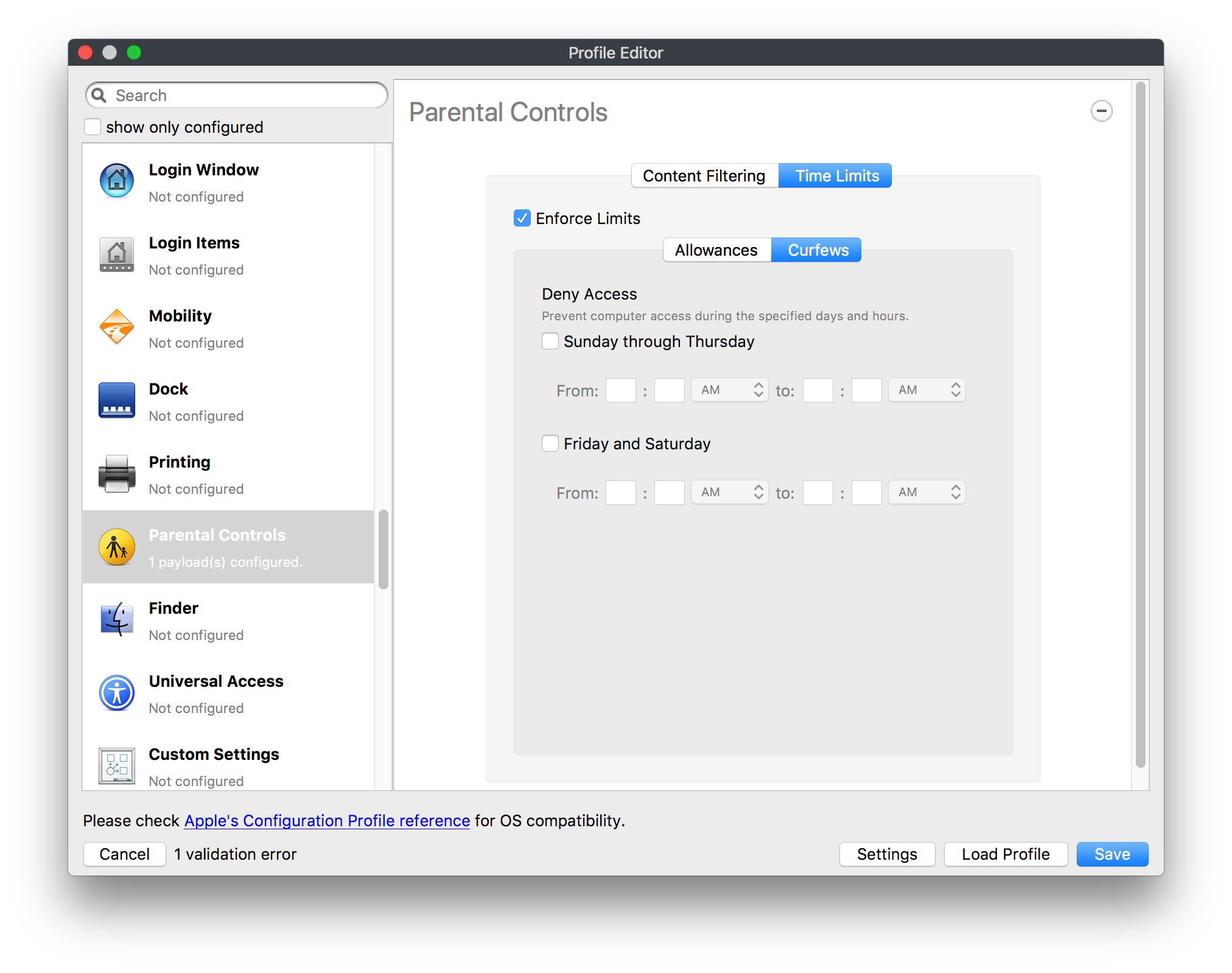](https://kb.filewave.com/uploads/images/gallery/2023-07/VnbBsWcuR7dvgIT8-image.png) Parental Controls were designed to support 1:1's where policies required content filters for managed computers when they were away from the managed network, as well as being able to set curfews and usage time limits for younger users. The payload is also very useful in open labs where the ability to deny non-administrator access to systems past a certain time of day is recommended. ### Finder [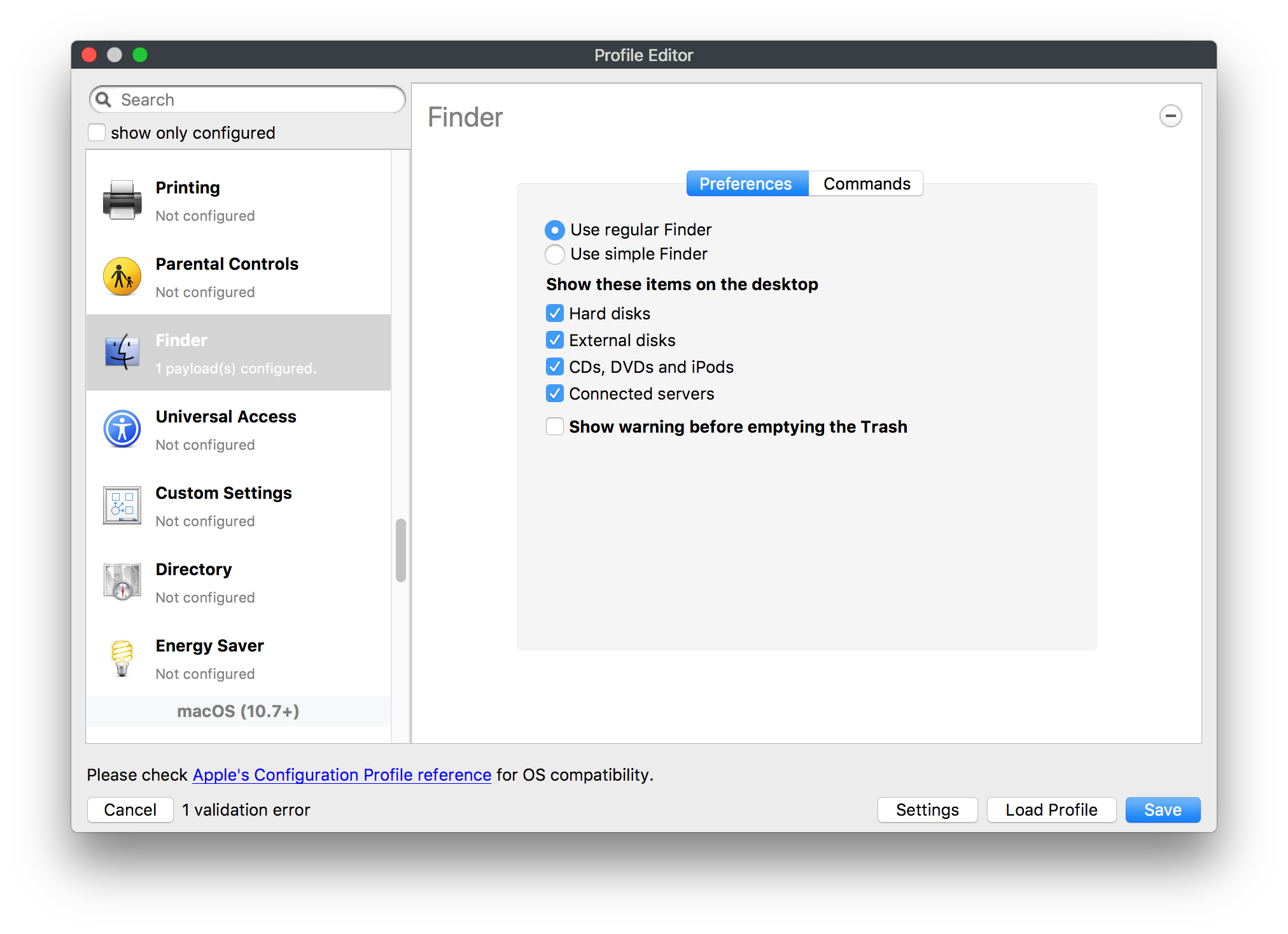](https://kb.filewave.com/uploads/images/gallery/2023-07/4B71BMoHfZn00BZV-image.png) [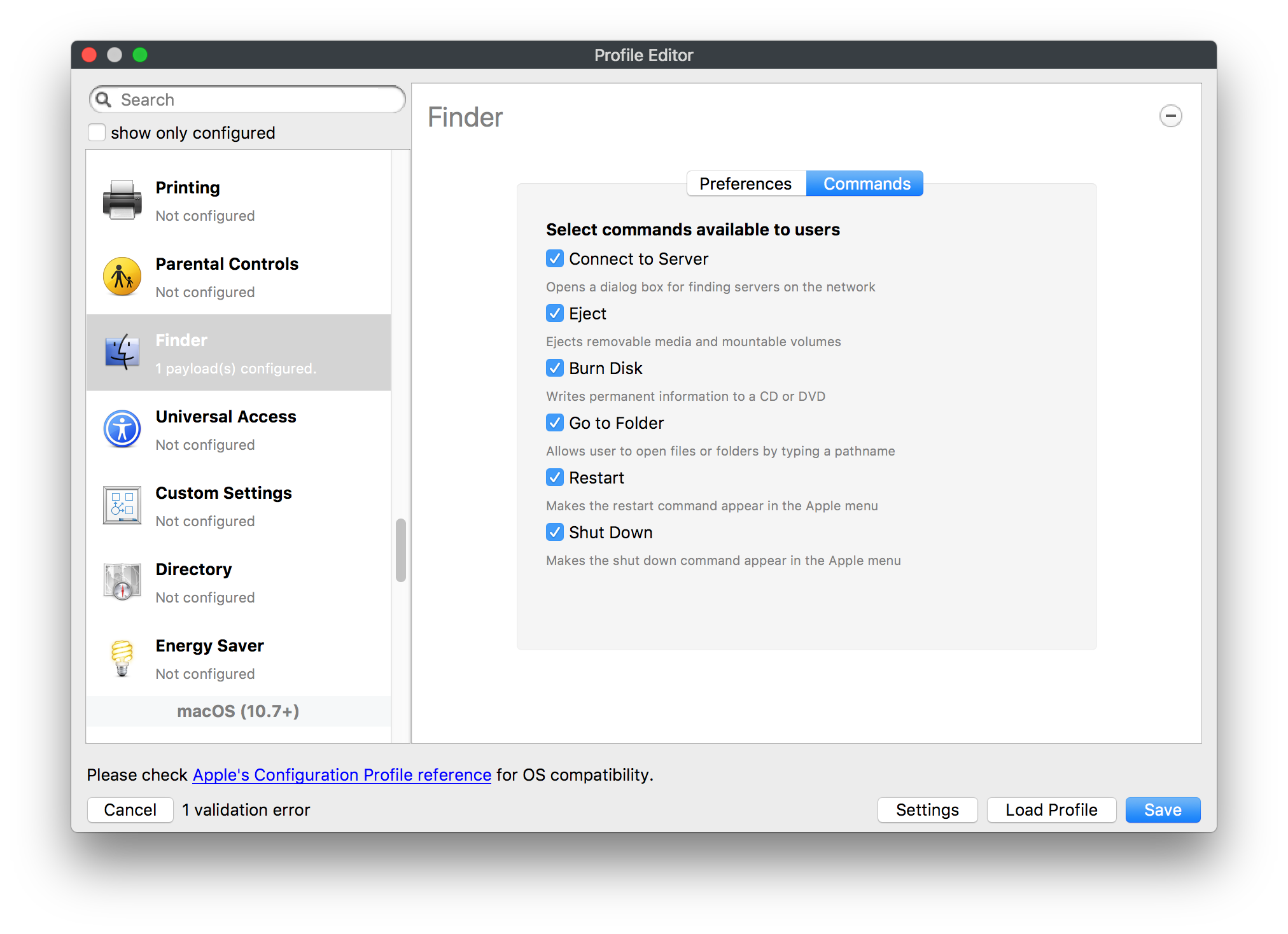](https://kb.filewave.com/uploads/images/gallery/2023-07/GY8SmBARAJkZhpmd-image.png) The Finder payload is designed to allow for limited access to external devices as well as hiding commands such as Shutdown or Go to Folder on common use / shared use systems. ### Universal Access [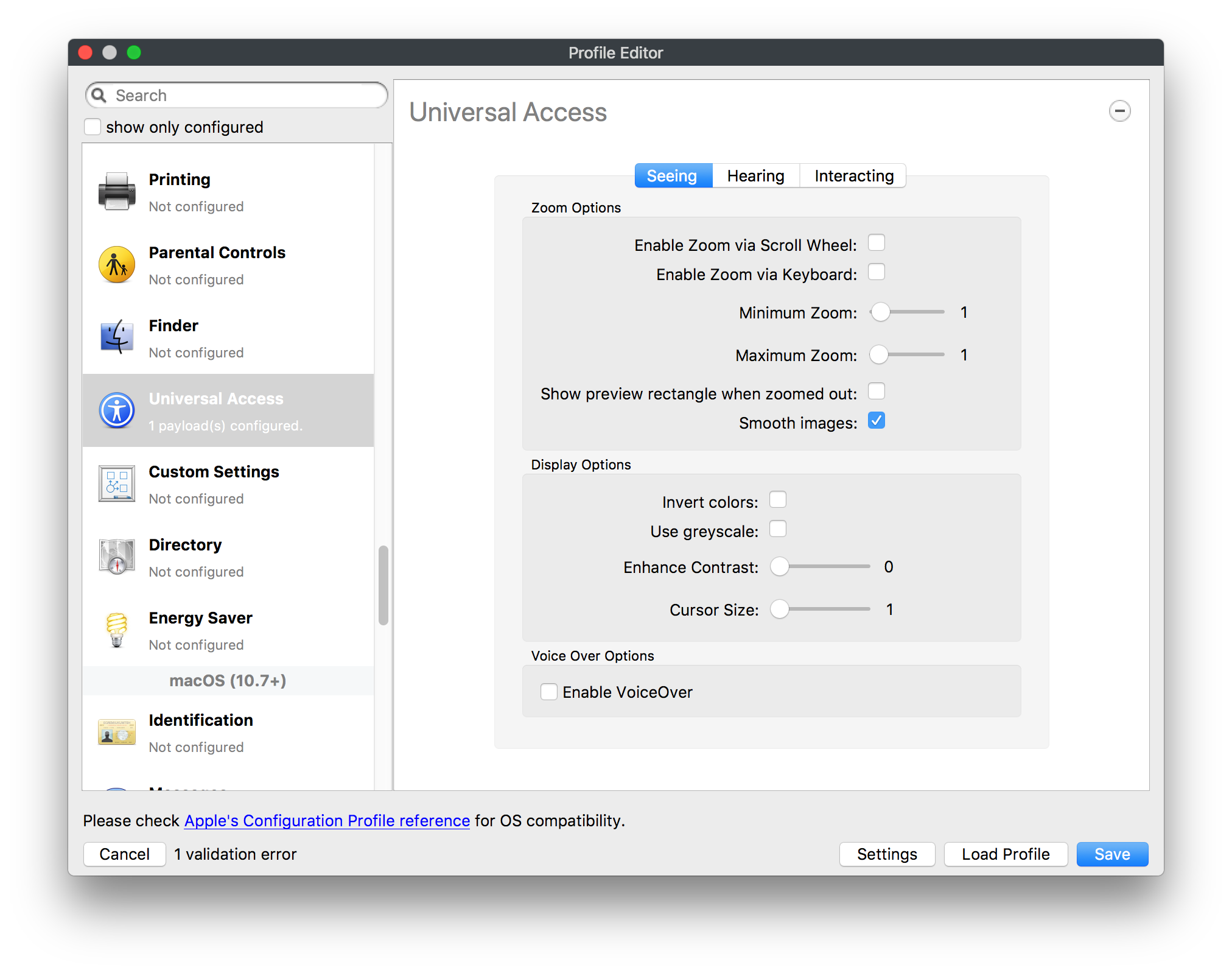](https://kb.filewave.com/uploads/images/gallery/2023-07/S2IQ7IfqiGcvaSmU-image.png) [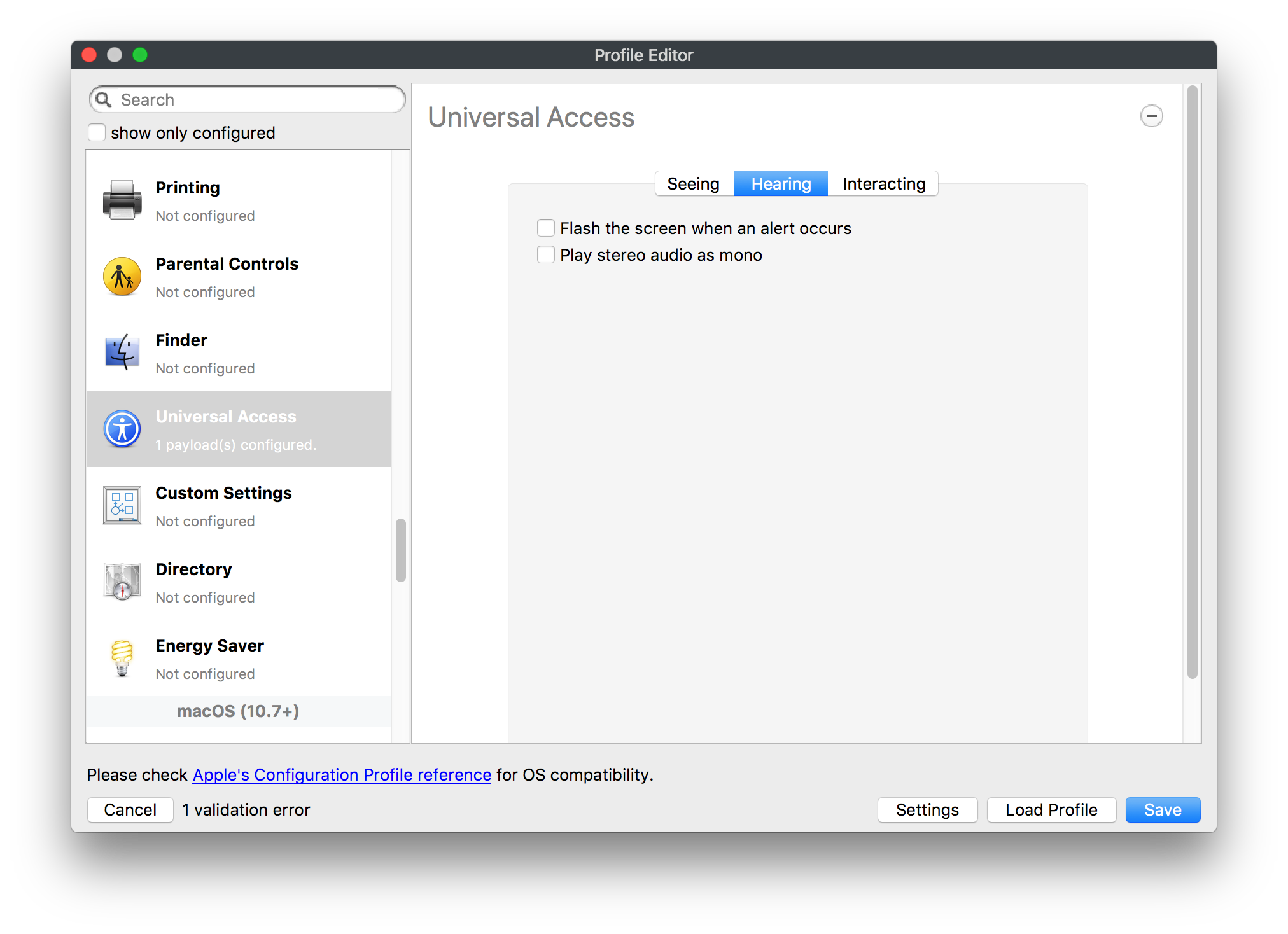](https://kb.filewave.com/uploads/images/gallery/2023-07/7xrbPSc50ef2UPcq-image.png) [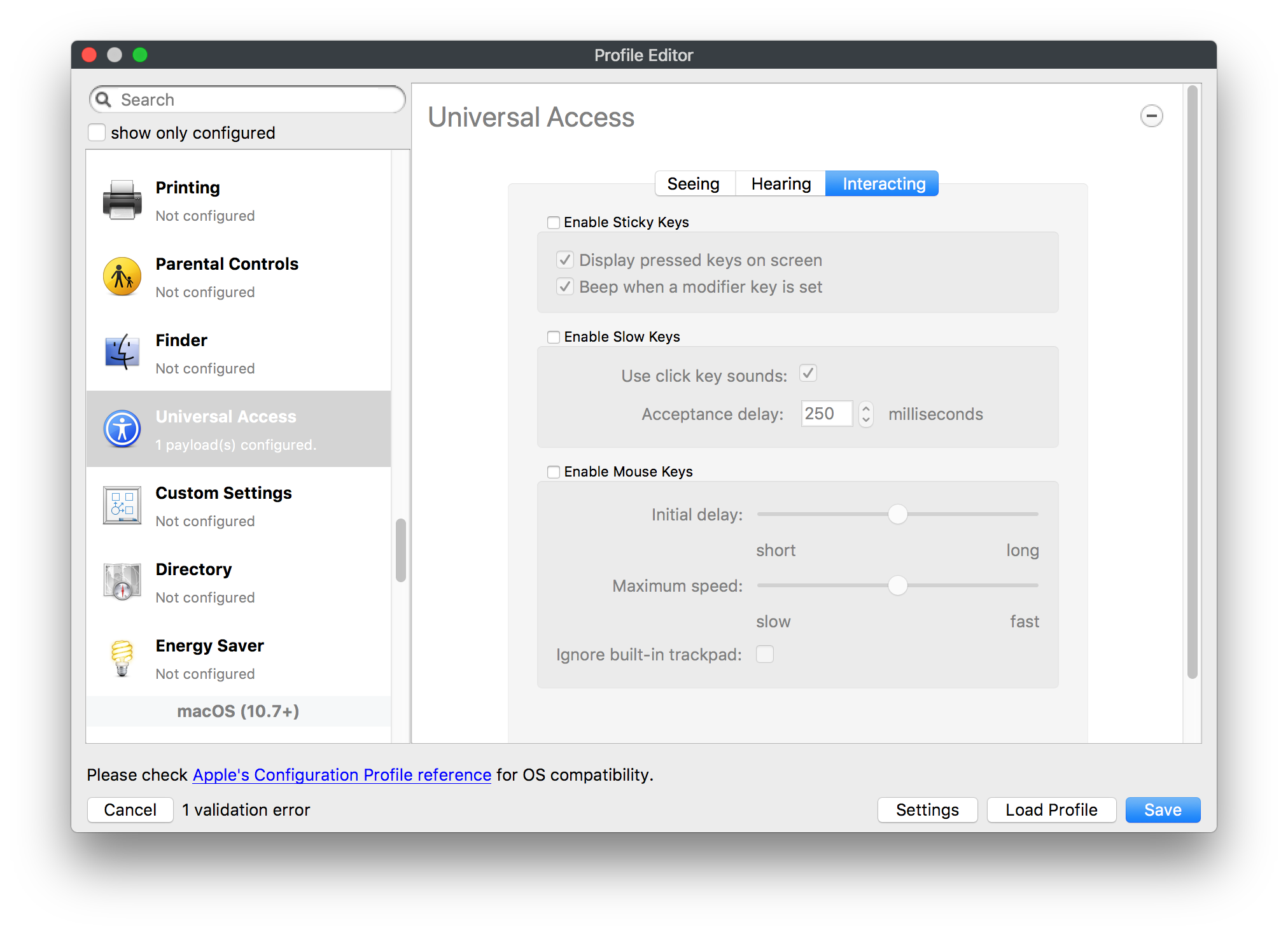](https://kb.filewave.com/uploads/images/gallery/2023-07/uRyLKDBSEABvbAlD-image.png) Universal Access payload settings are not just for special needs; but also contain settings for open labs and users who need additional services, such as zoom. Examples are having screens flash at alerts versus beeping in an open lab, or configuring a Group of users' computers to support zoom with the trackpad. ### Custom Settings [](https://kb.filewave.com/uploads/images/gallery/2023-07/mA9Tb8nyr7pGKBRH-image.png) Custom Settings payloads allow you to greatly expand your ability to provide templates and special settings for managed computers. You configure the preferences for any application that supports property lists (.plist files), upload that configured .plist file, edit out the unneeded portions, and your managed systems will see that payload as a managed set of configuration settings to follow for that application. ### Directory [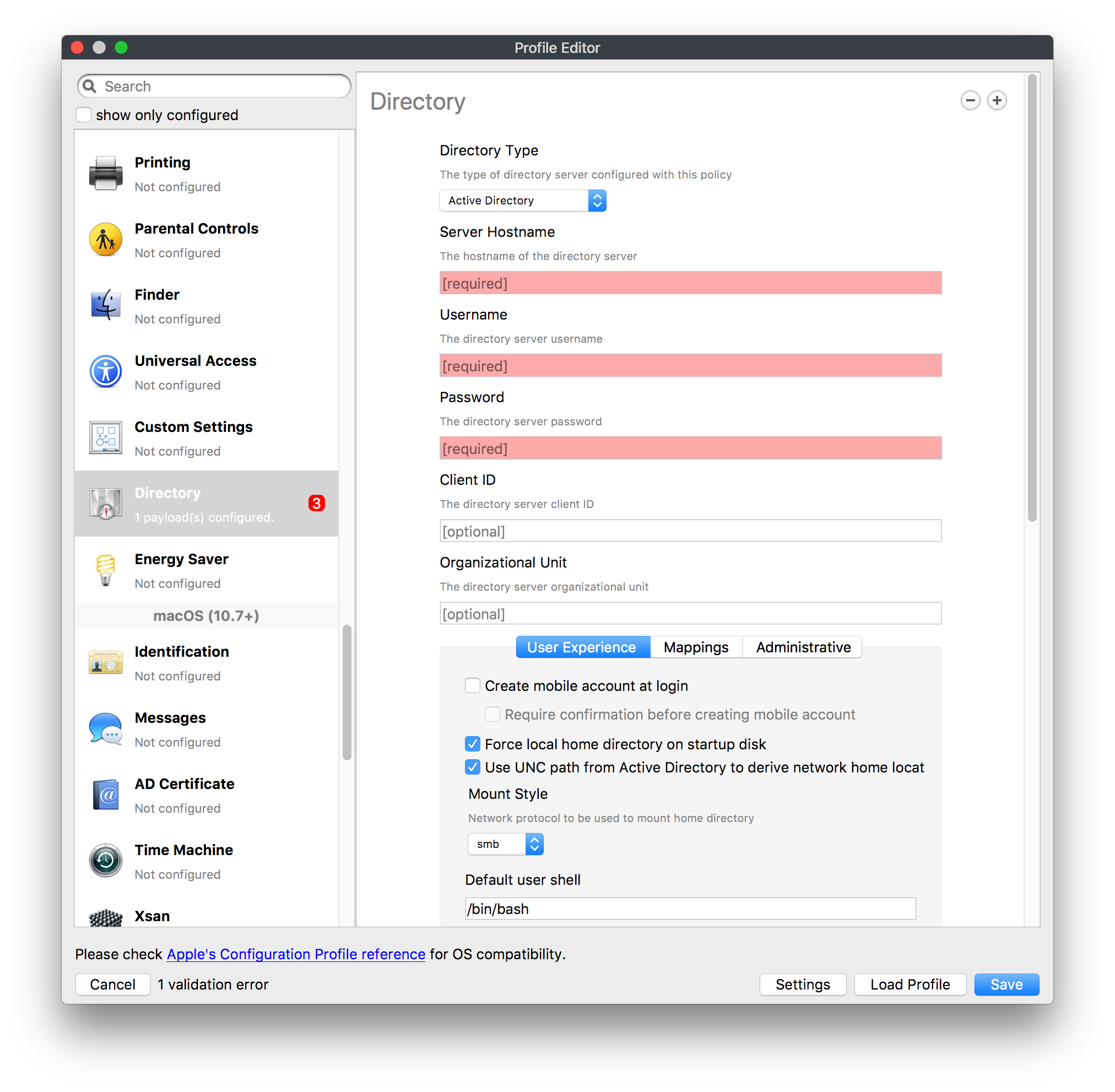](https://kb.filewave.com/uploads/images/gallery/2023-07/0LWKbwEB5WHoypKS-image.png) [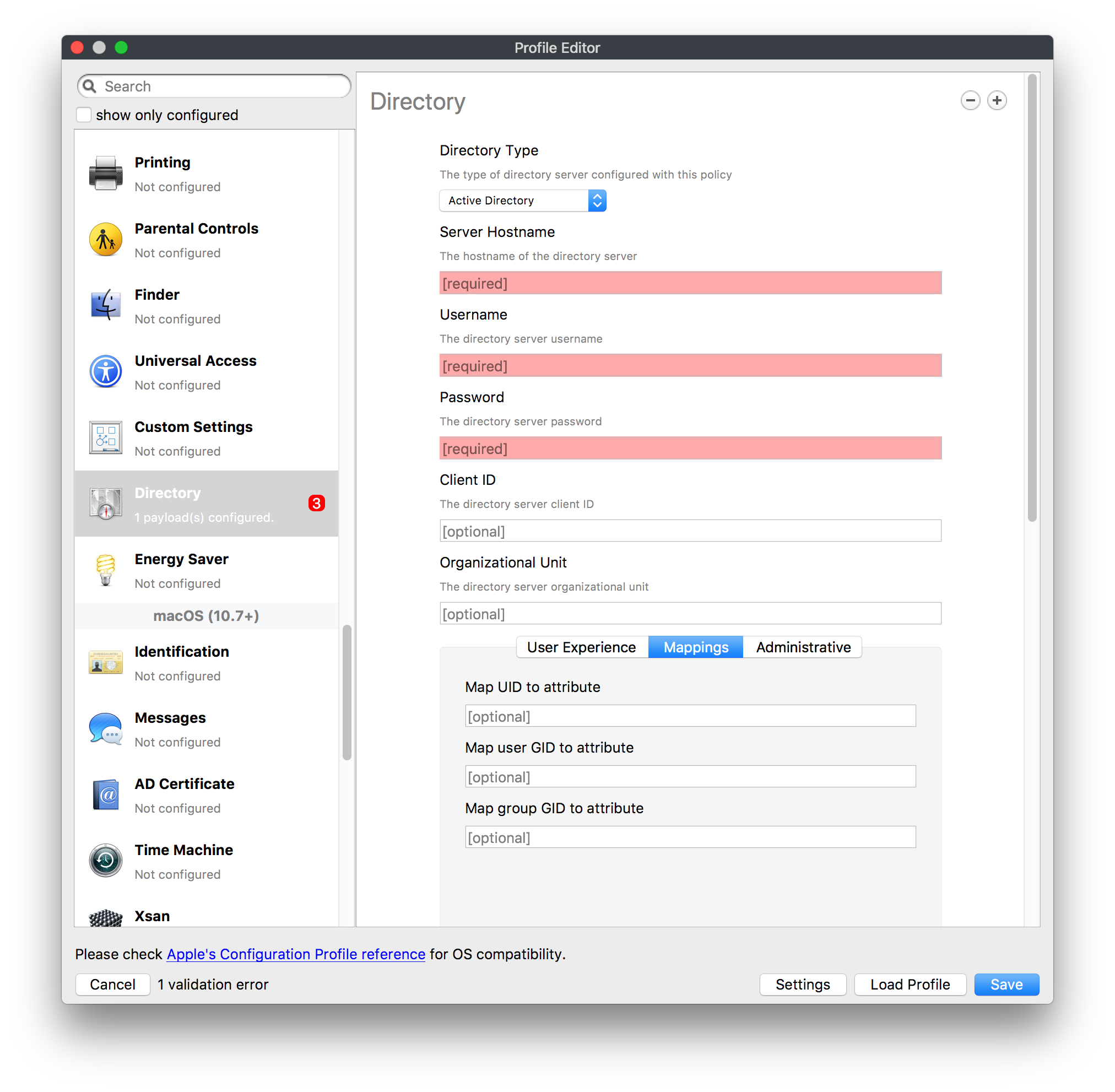](https://kb.filewave.com/uploads/images/gallery/2023-07/qWIOA4I81WmAK4oY-image.png) [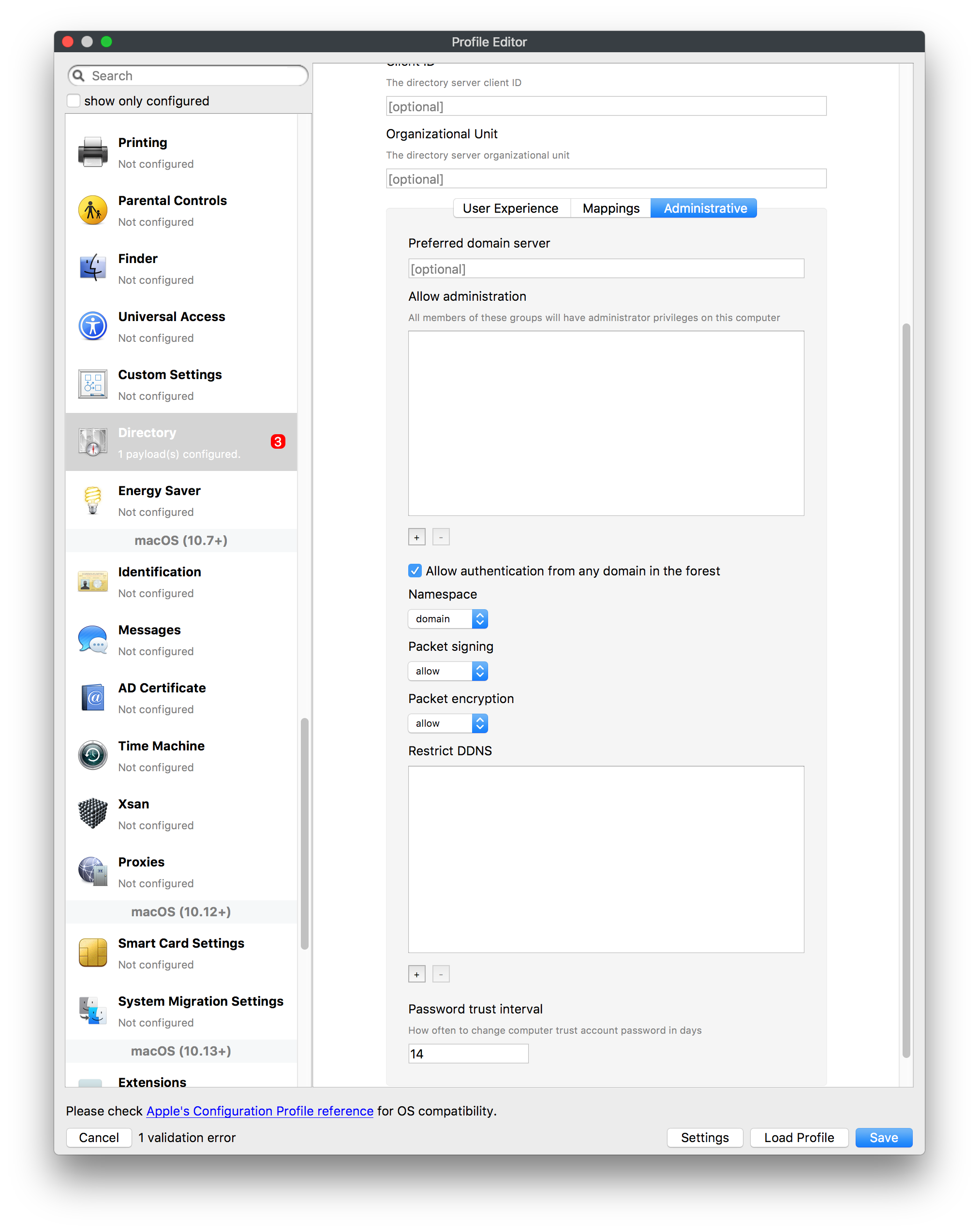](https://kb.filewave.com/uploads/images/gallery/2023-07/AcDVLTErbcrkmLTr-image.png) The Directory payload allows you to configure **binding** to LDAP directories for your macOS systems. You can set up anonymous or authenticated bindings. ### Energy Saver [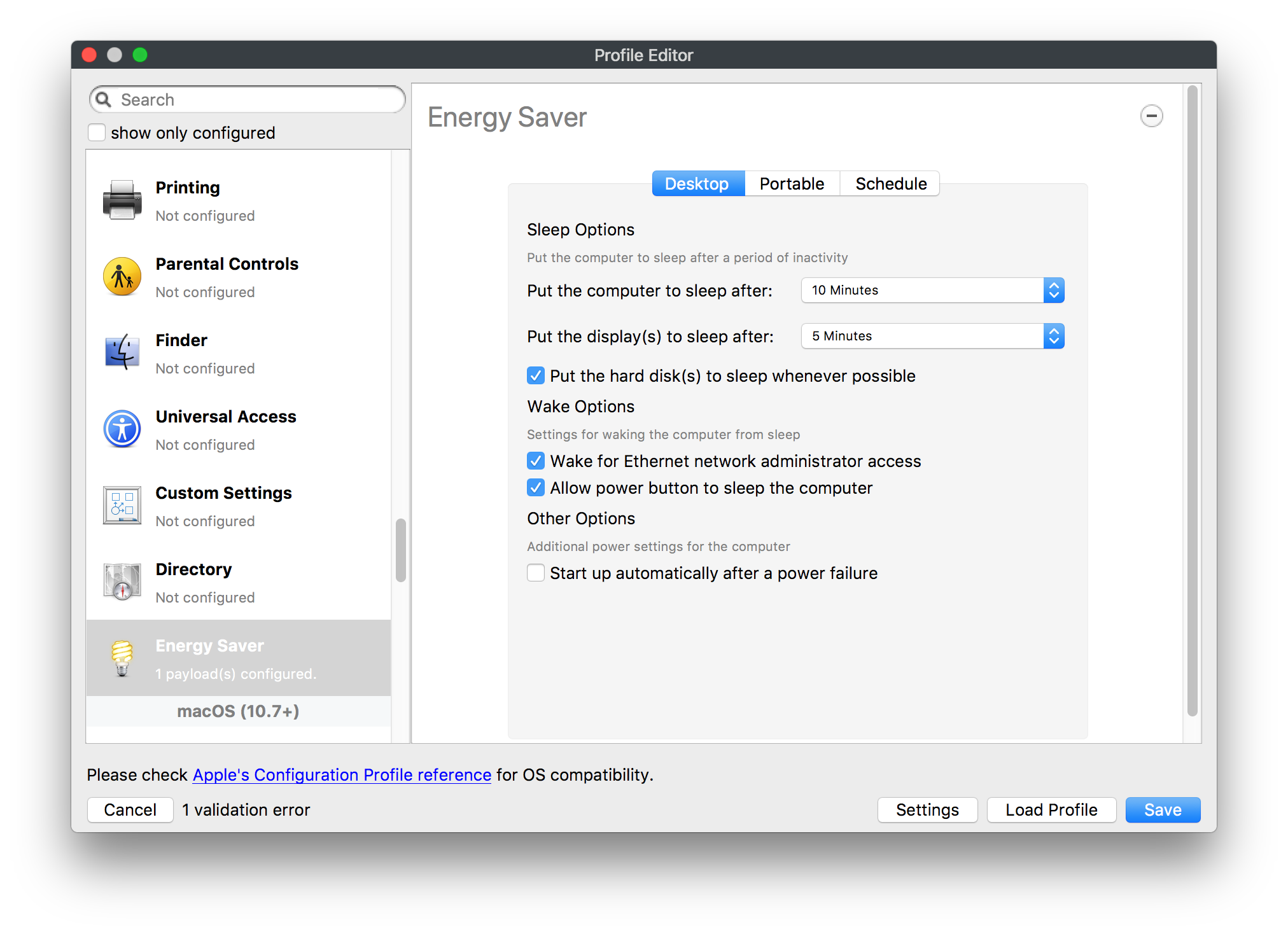](https://kb.filewave.com/uploads/images/gallery/2023-07/H0HoEXl2ciGpBlcz-image.png) [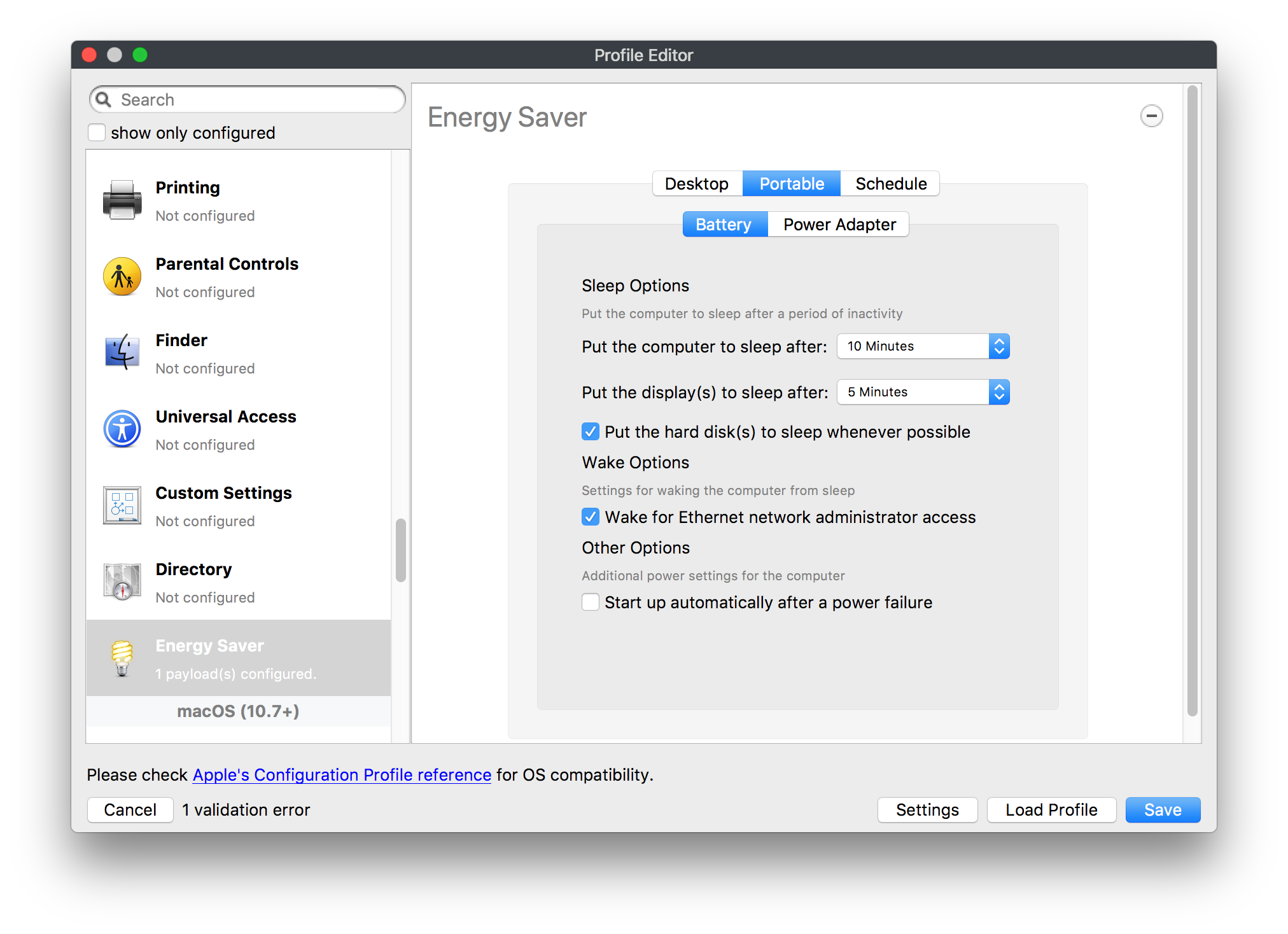](https://kb.filewave.com/uploads/images/gallery/2023-07/JzQGzGHQr9ipnruj-image.png) [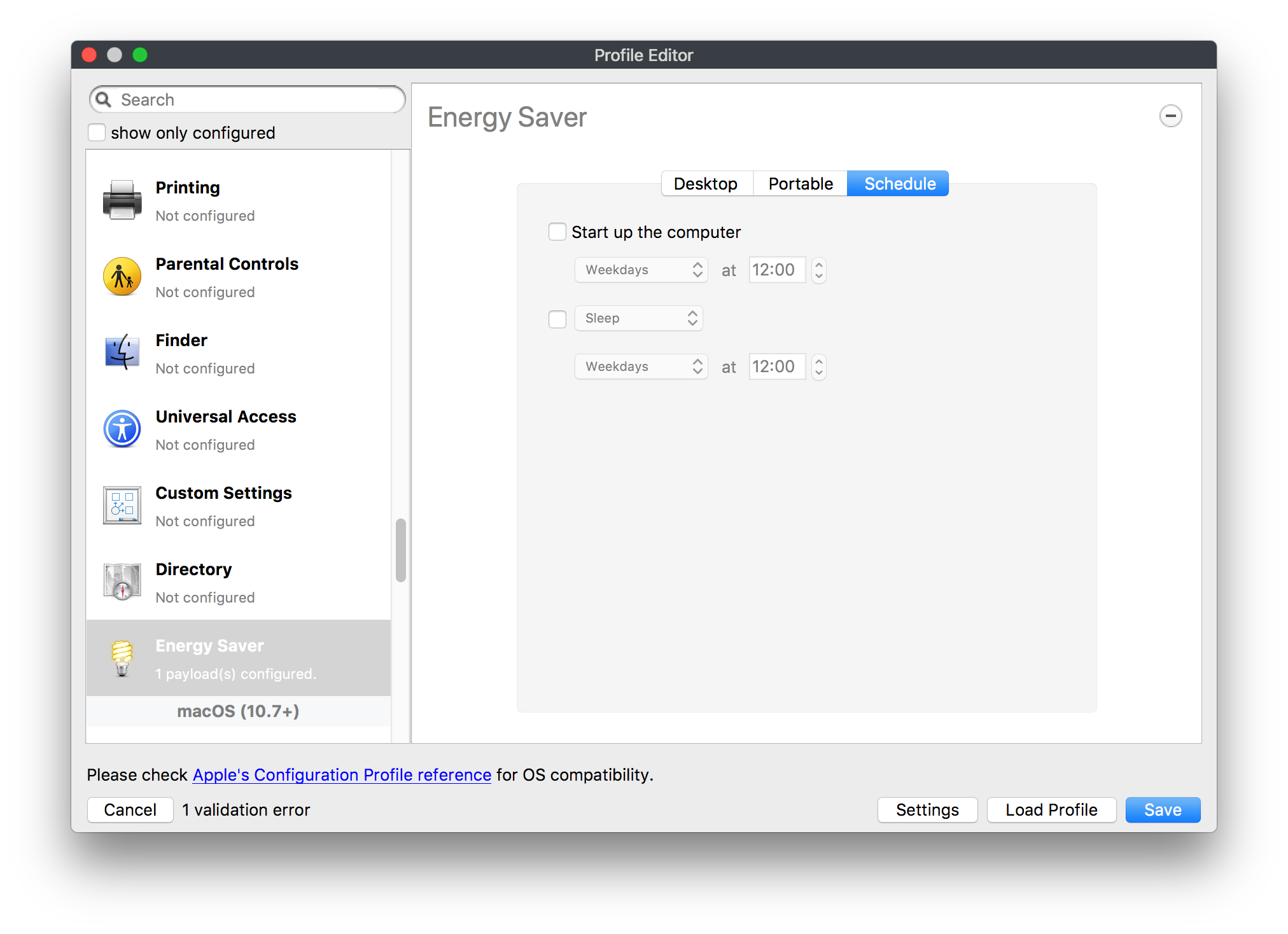](https://kb.filewave.com/uploads/images/gallery/2023-07/ytZWpZ1bJhWWRZCZ-image.png) Energy Saver payload settings allow you to preconfigure managed computers with the settings to optimize battery life in portables, as well as force desktop systems in a lab to sleep or wake when needed for online maintenance. ## macOS (10.7+) settings These settings are OS X running v10.7 (Lion) or higher only. ### Identification [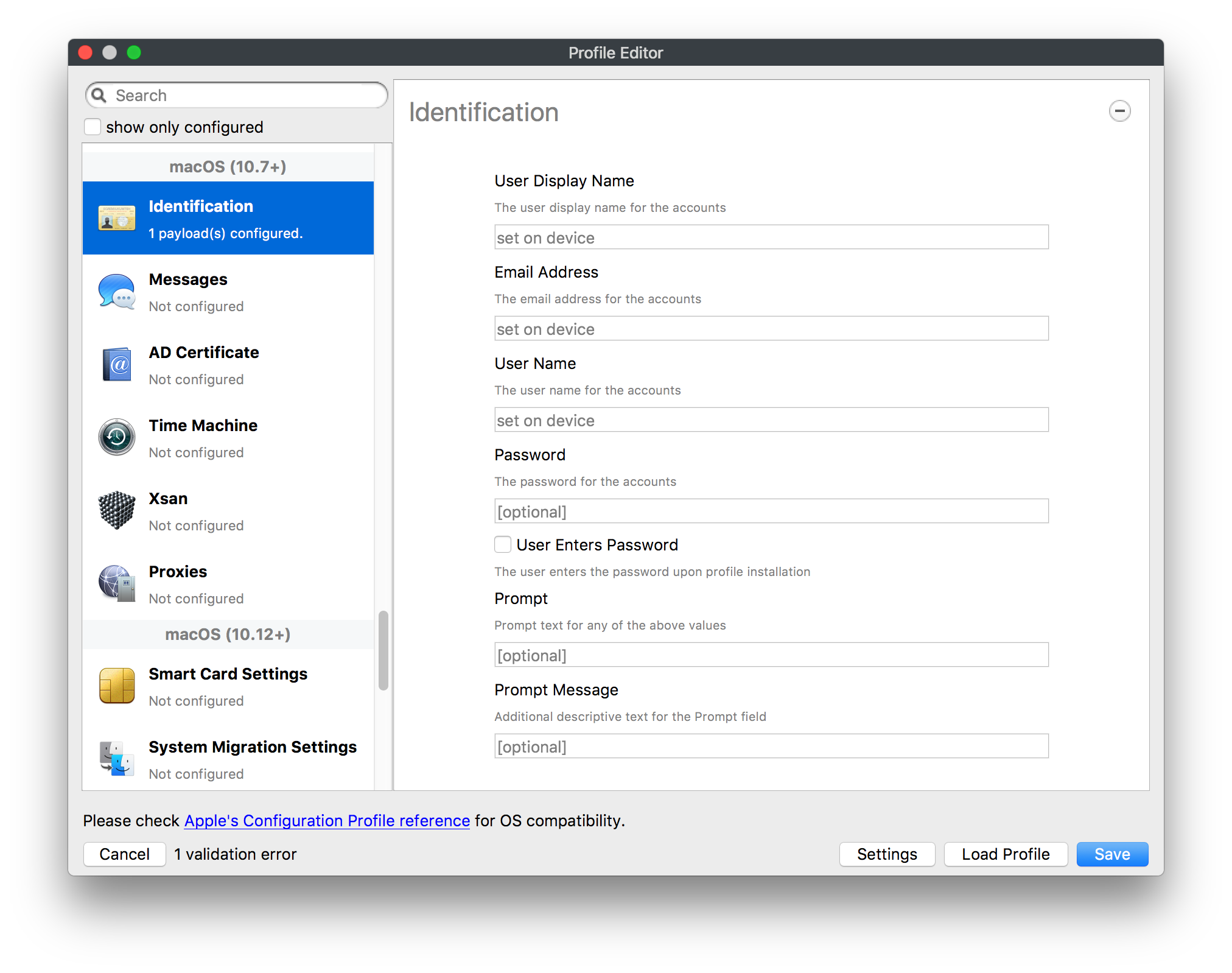](https://kb.filewave.com/uploads/images/gallery/2023-07/rZ3NKIm34V7EV0fH-image.png) The Identification payload, using parameterized profile settings, can allow you to preconfigure user identity information for multiple users in OS X. You can define just a user's name, or nothing at all other than a prompt text that tells the user what to do the first time they log in. This information would then be saved for use in any service that can take advantage of Apple's Identity framework. ### Messages [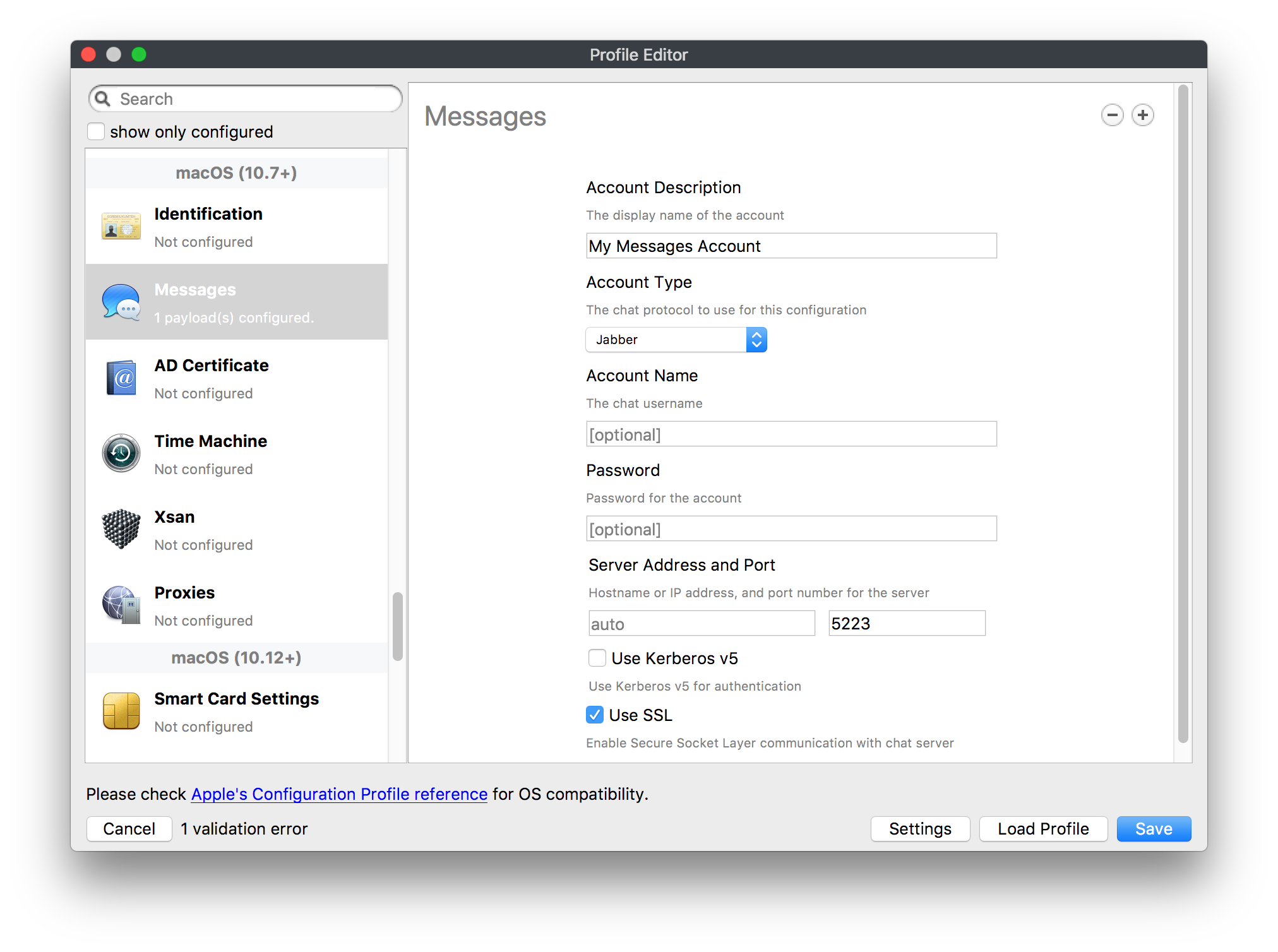](https://kb.filewave.com/uploads/images/gallery/2023-07/zYDAmCgzBHErk2rP-image.png) Messages allows you to preload the settings for user access to Jabber or AIM chat services. It can use parameterized profile settings for this payload. ### AD Certificate [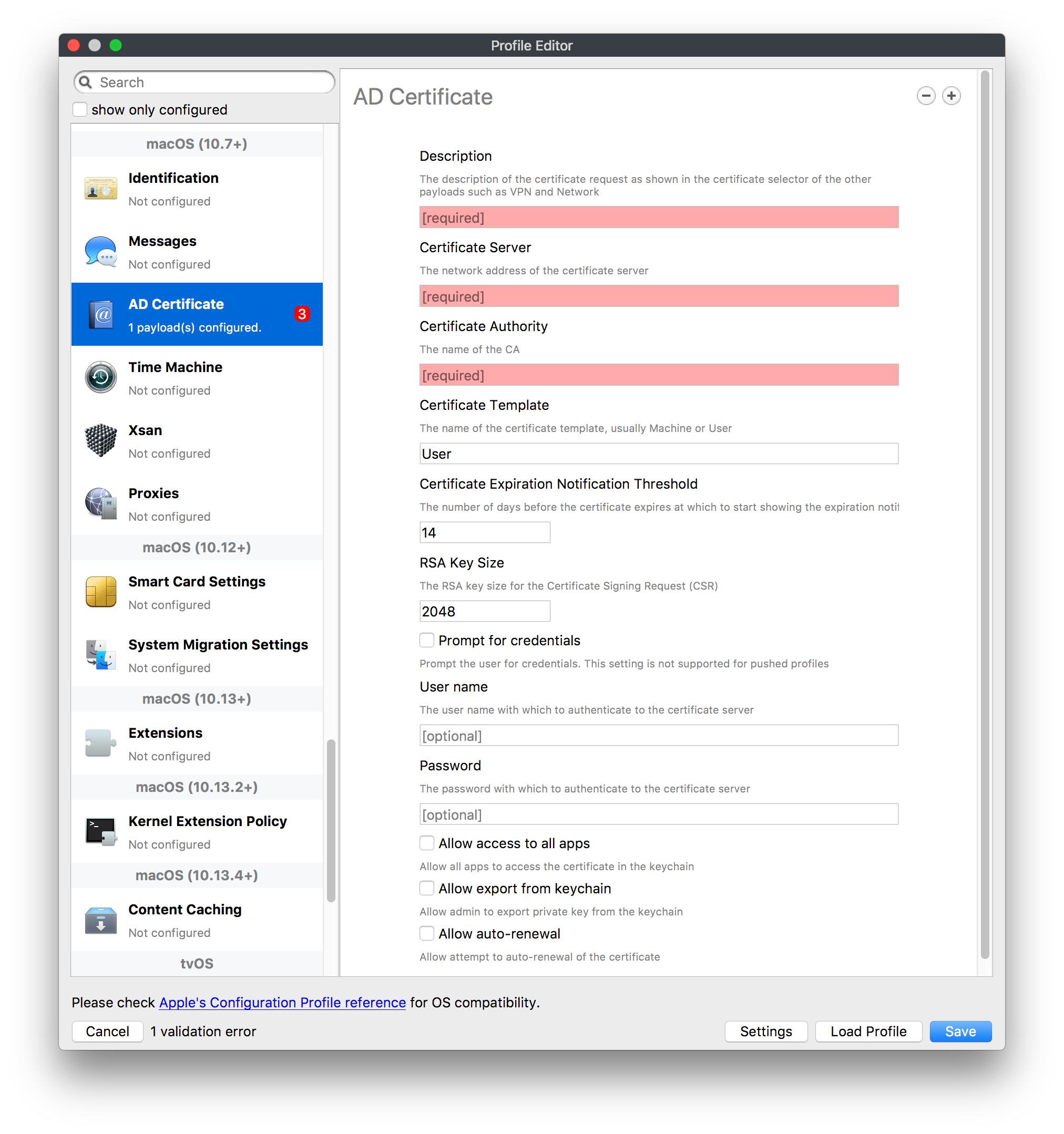](https://kb.filewave.com/uploads/images/gallery/2023-07/KI6qqhDx3Gz1qT7G-image.png) Configuring the AD Certificate payload lets you set up other payloads, such as VPN or Network, more easily. This payload provides the authentication data that will validate access to other services dependent on Active Directory certificates. ### Time Machine [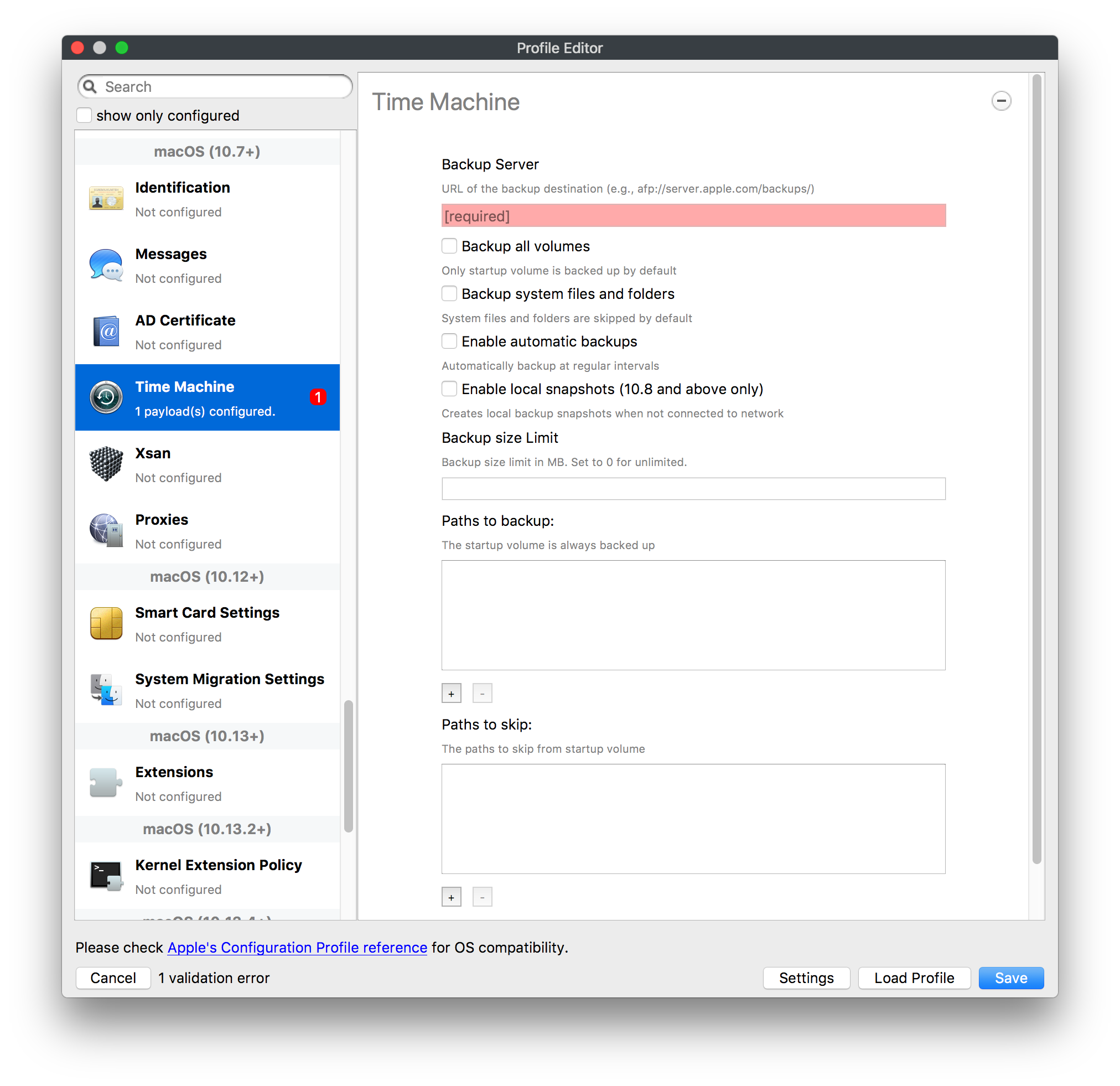](https://kb.filewave.com/uploads/images/gallery/2023-07/fYhewwavVsKvdoas-image.png) For environments using Time Machine servers or Time Capsules, this payload lets you set up the access information for backup of managed devices. ### Xsan [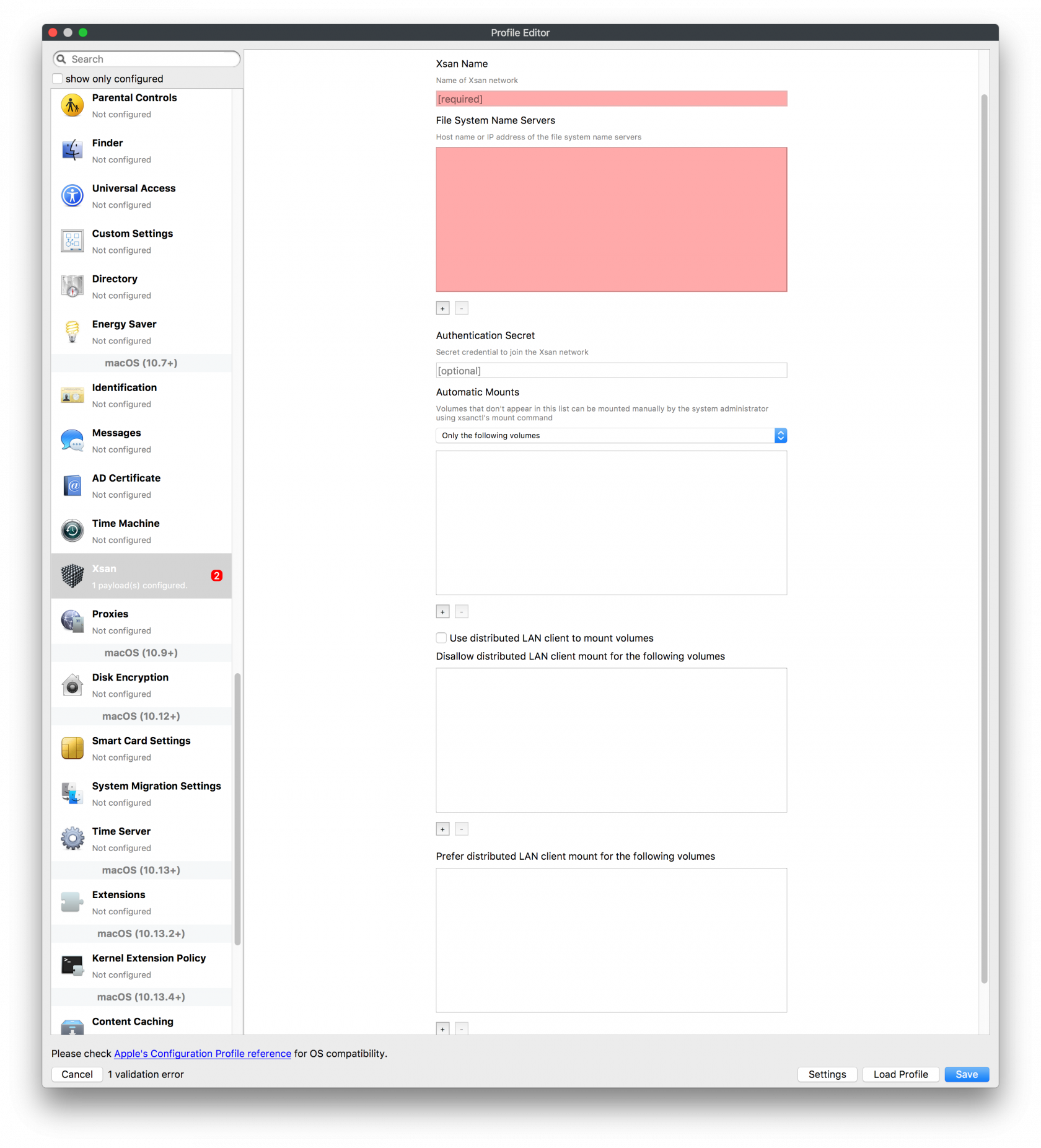](https://kb.filewave.com/uploads/images/gallery/2023-07/zgD6jqLPGa6Tmxcy-image.png) This section is used to configure Xsan; specifically the name of the Xsan network, the name of the FS Name Server, and the authentication secret, if one is used. ### Proxies [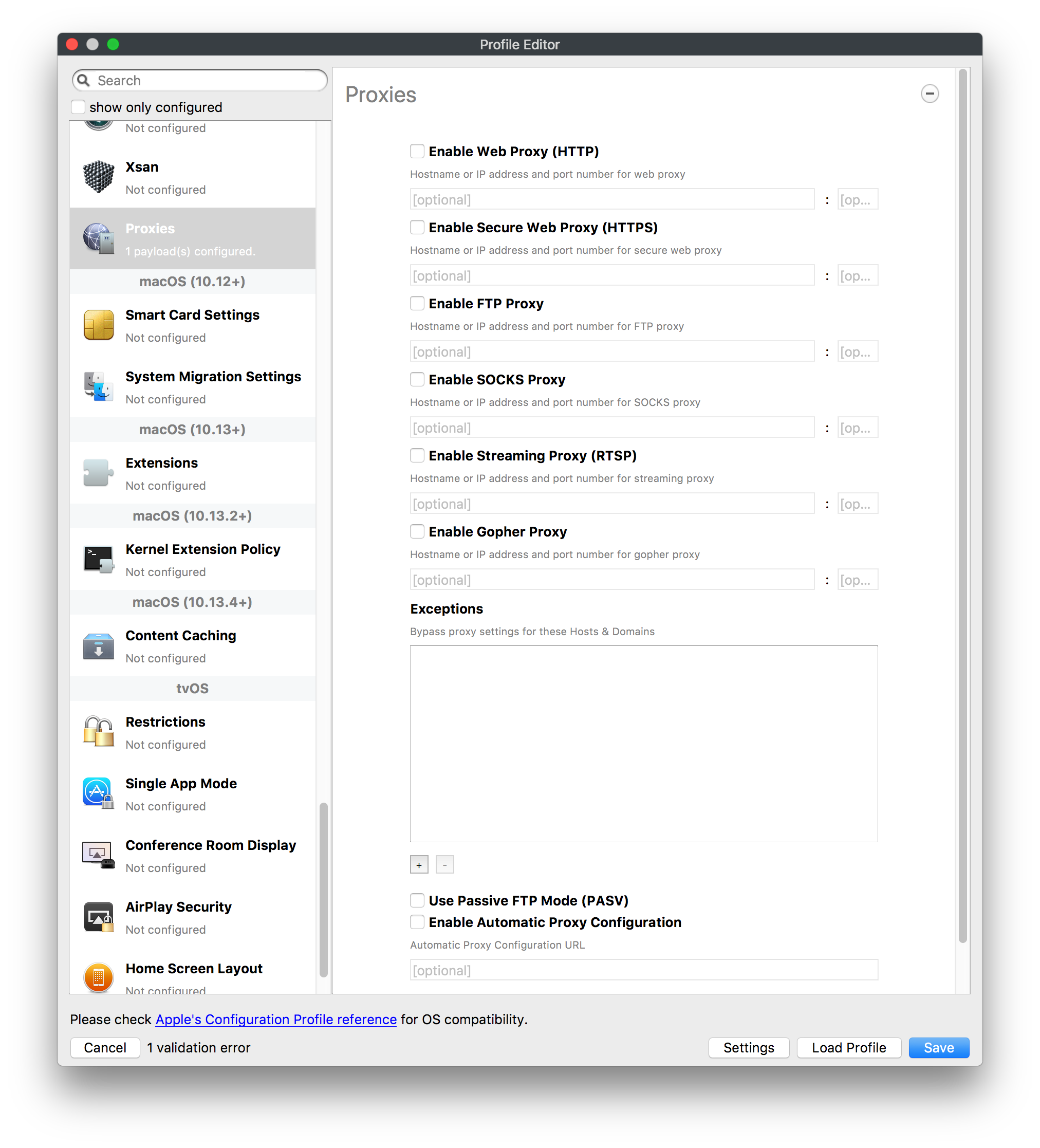](https://kb.filewave.com/uploads/images/gallery/2023-07/VdW9Cc1nZ2GW01MW-image.png) This payload type is used to configure proxy settings, including exception for specified hosts and domains. ## macOS (10.9+) ### Disk Encryption [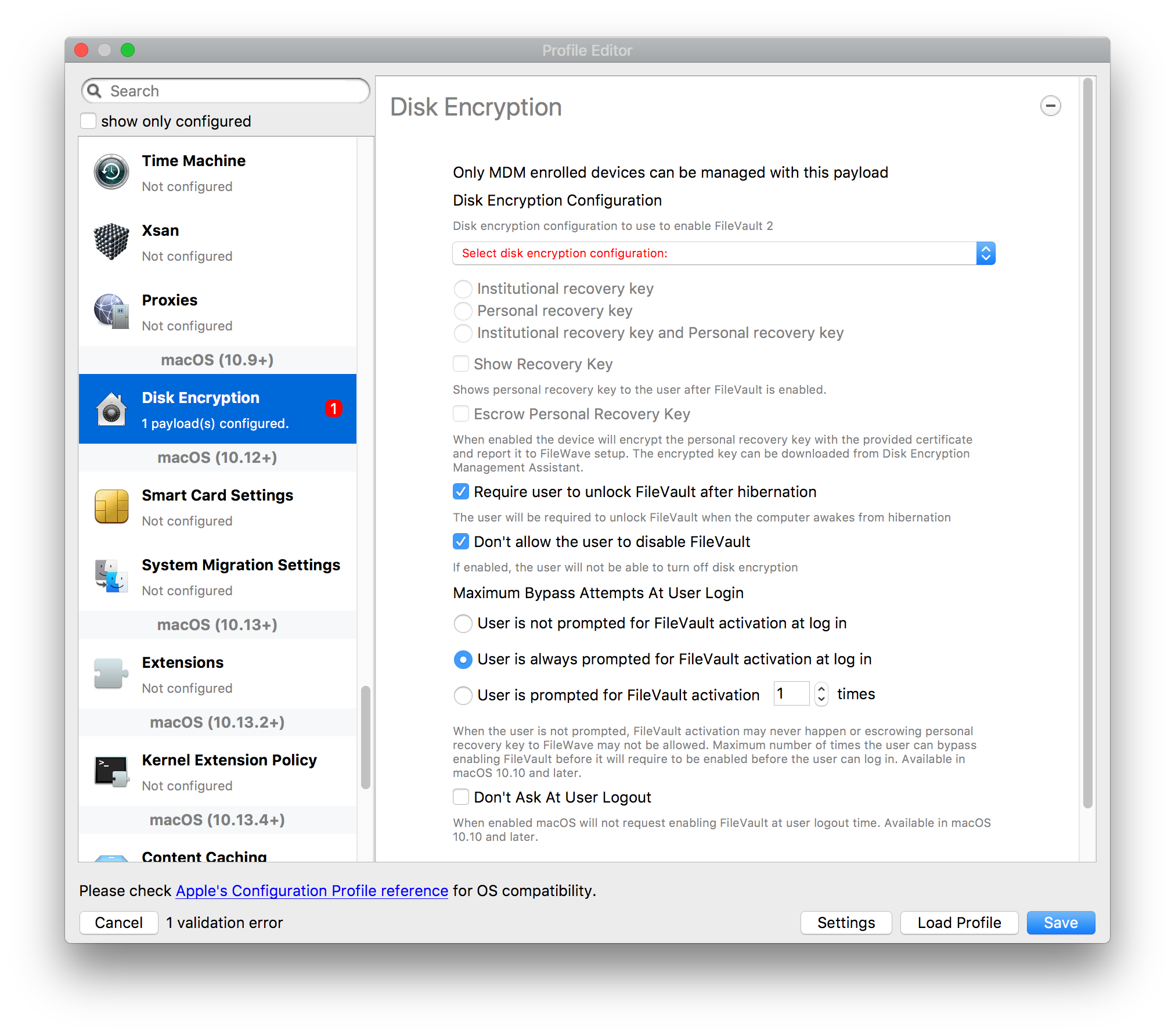](https://kb.filewave.com/uploads/images/gallery/2023-07/L6uUSj947WAXbITf-image.png) Use this section to define settings for Disk Encryption (FileVault 2). [You can find more information about FileVault 2 on FileWave's Knowledge Base](https://kb.filewave.com/wiki/spaces/KB/pages/4327598/FileVault+2) ## macOS (10.12+) ### Smart Card Settings [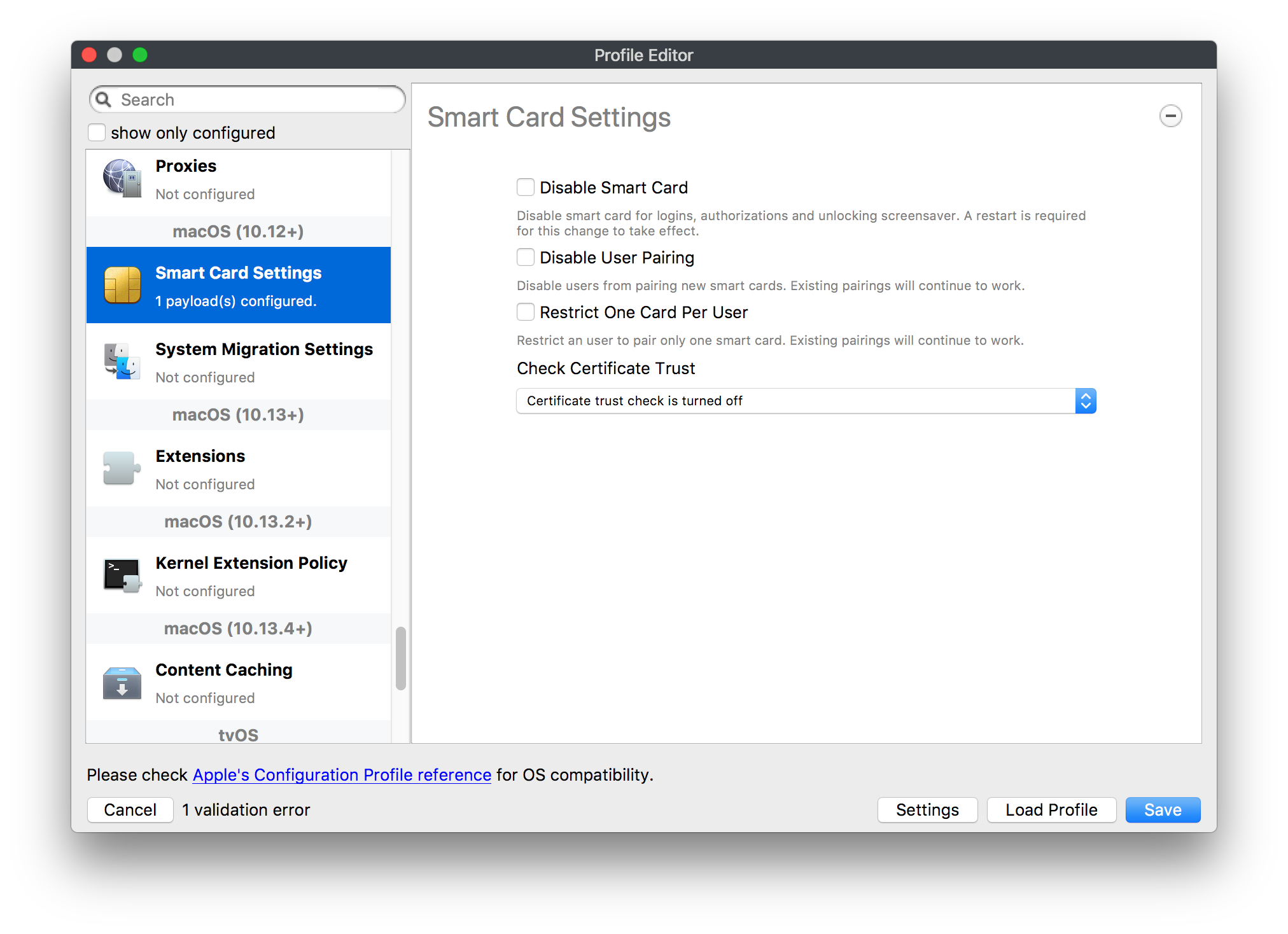](https://kb.filewave.com/uploads/images/gallery/2023-07/5B8fMsM6Xfm1Zako-image.png) Use the section to configure smart card security settings for macOS ### System Migration Settings [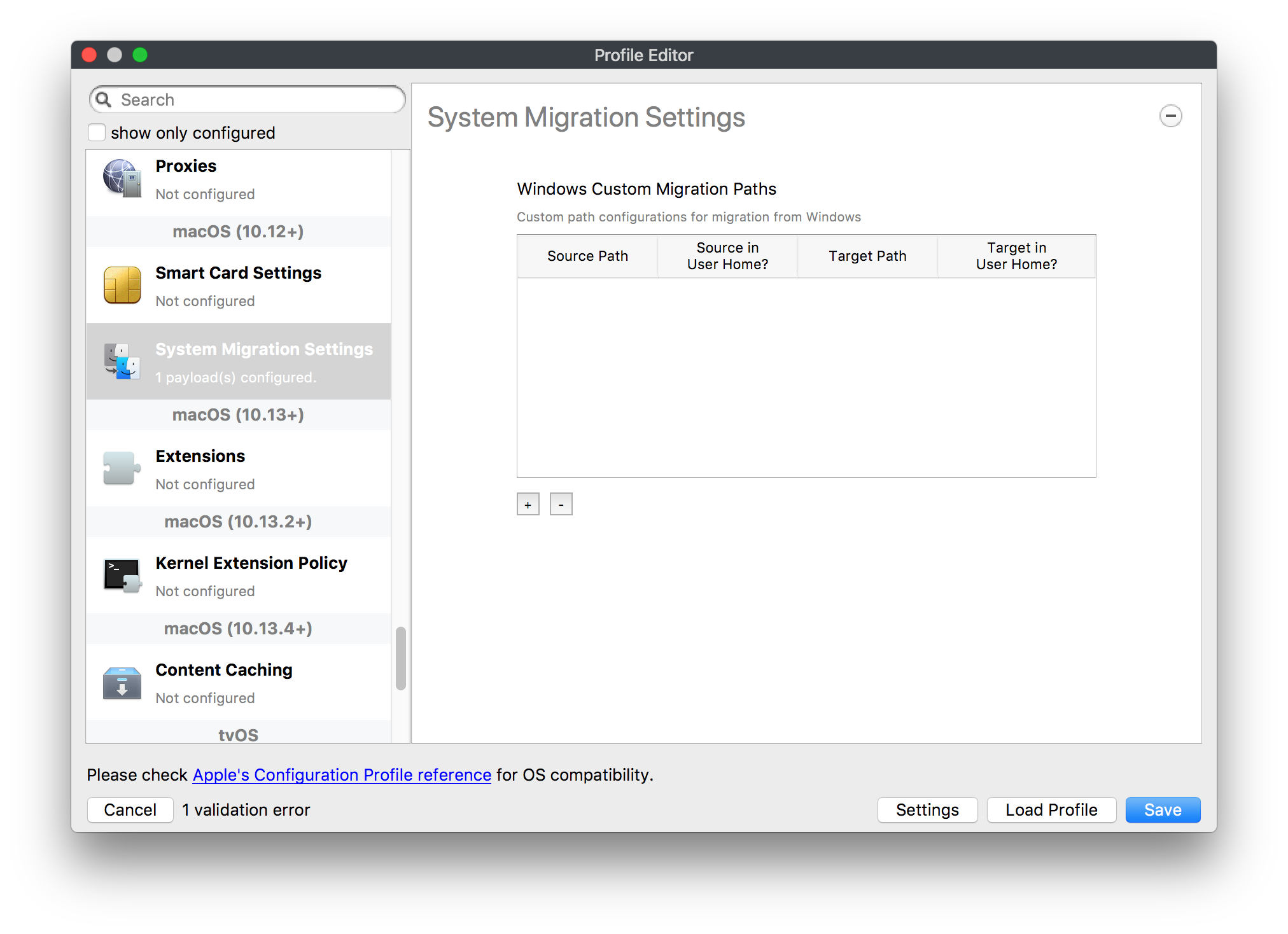](https://kb.filewave.com/uploads/images/gallery/2023-07/6NGqiEFQ7728VZFJ-image.png) Use this section to configure system migration settings ### Time Server [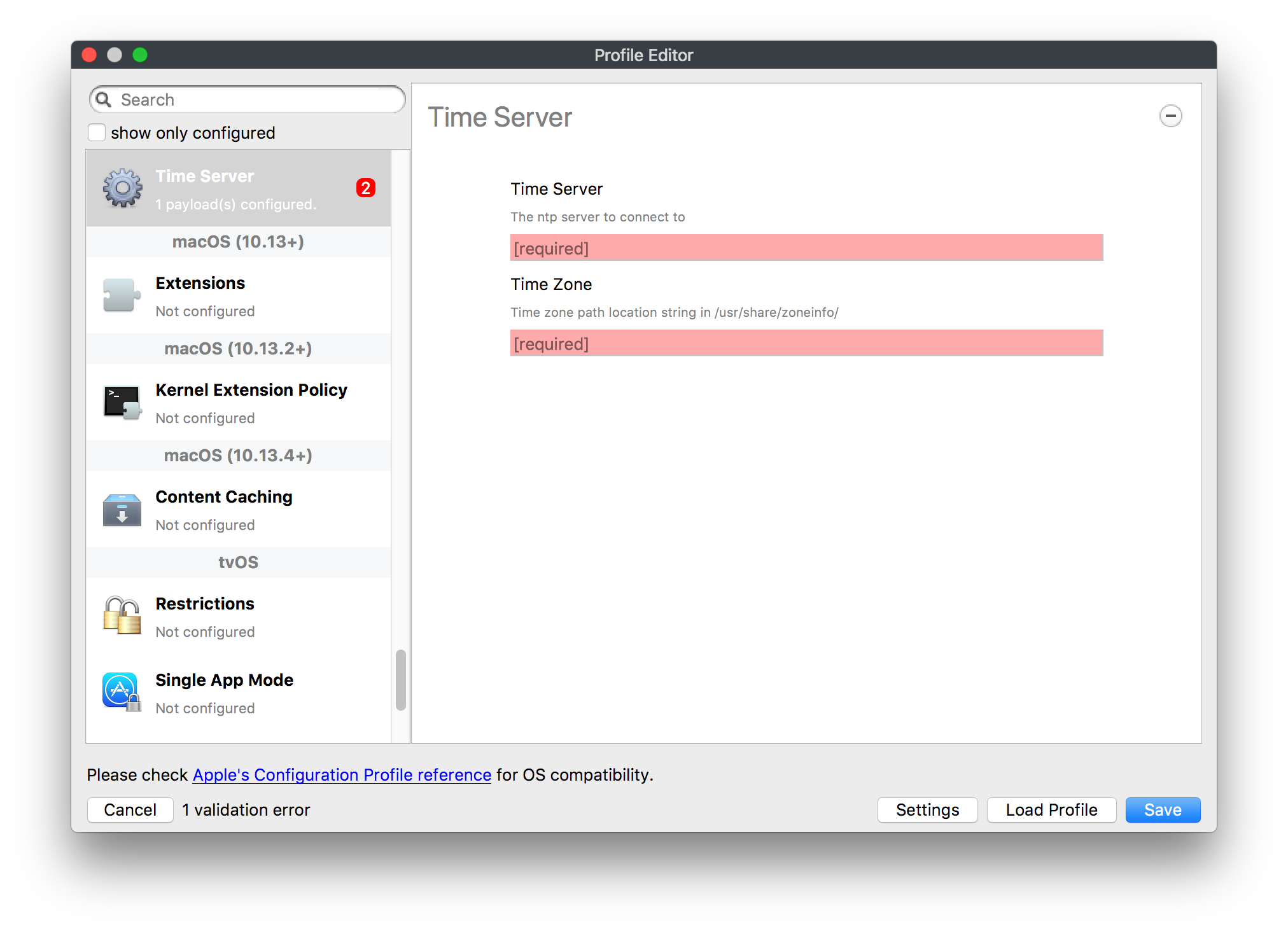](https://kb.filewave.com/uploads/images/gallery/2023-07/SbMoOzucDtyHw8Td-image.png) use this section to configure time server settings ## macOS (10.13+) ### Extensions [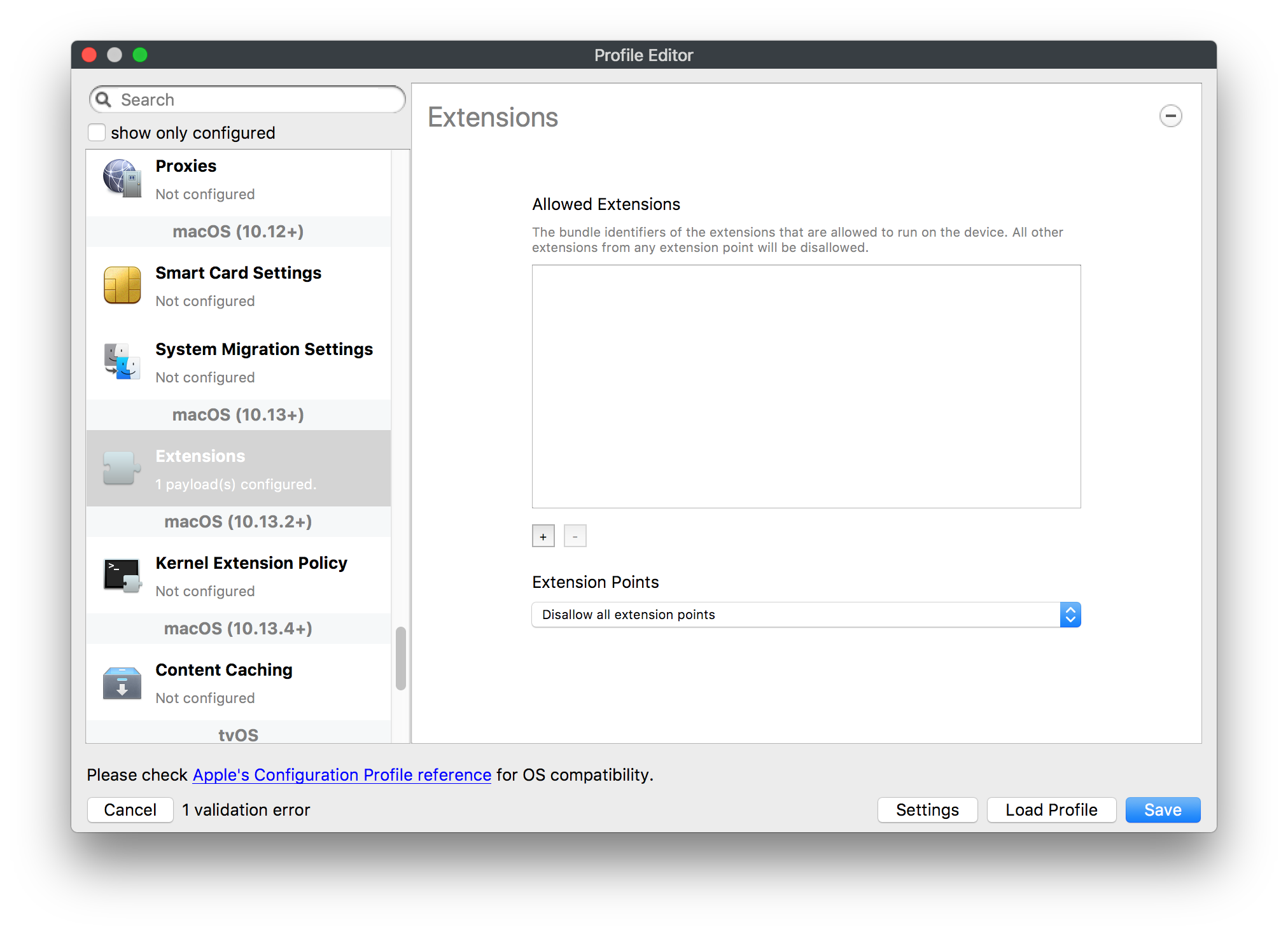](https://kb.filewave.com/uploads/images/gallery/2023-07/roQsQB1rGEhKapP2-image.png) Use this section to configure allowed extensions on macOS ## macOS (10.13.2+) ### Kernel Extension Policy [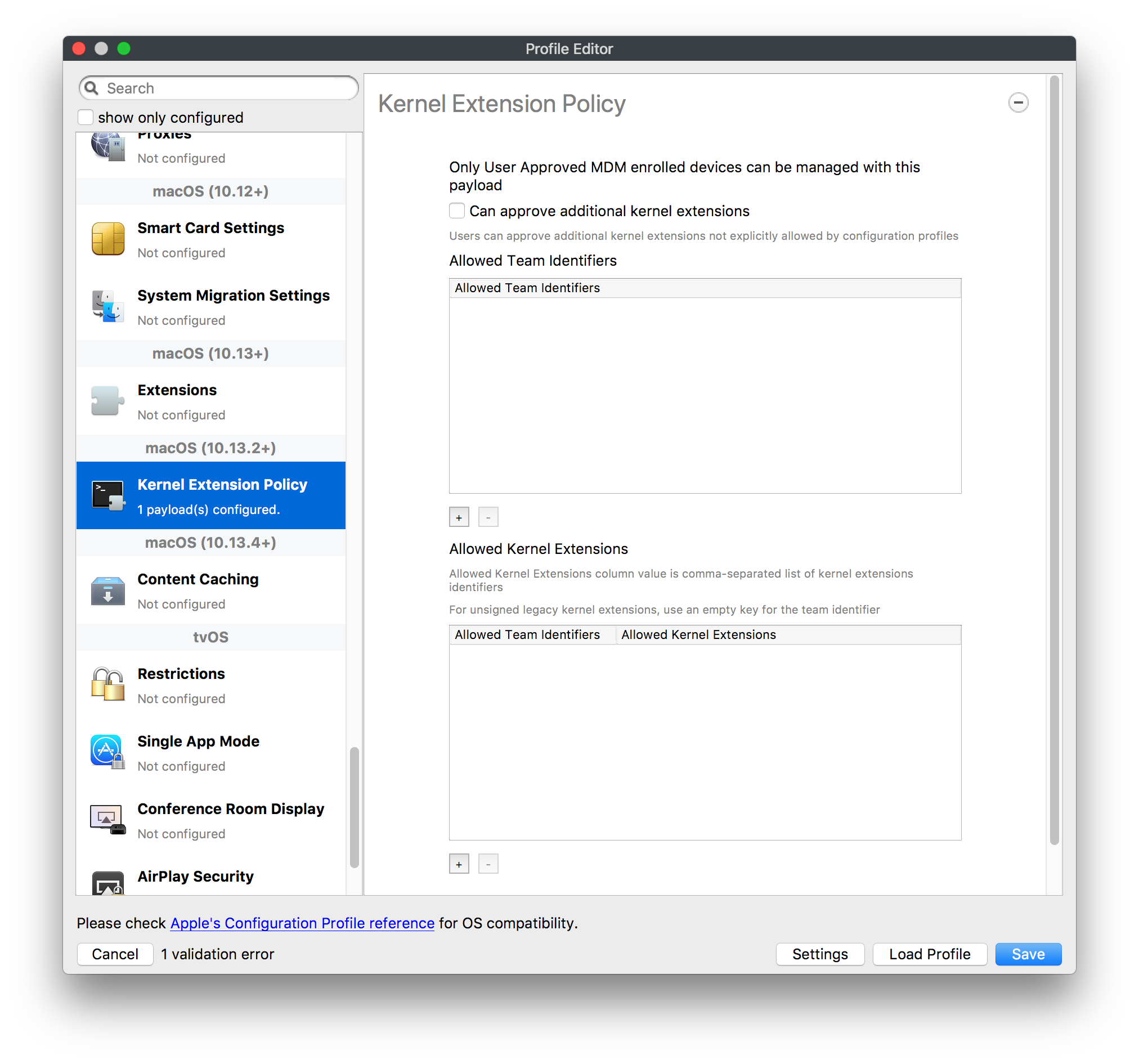](https://kb.filewave.com/uploads/images/gallery/2023-07/oEg7tMnWYJB7q8or-image.png) Use this section to configure kernel extensions on macOS ## macOS (10.13.3+) ### Content Caching [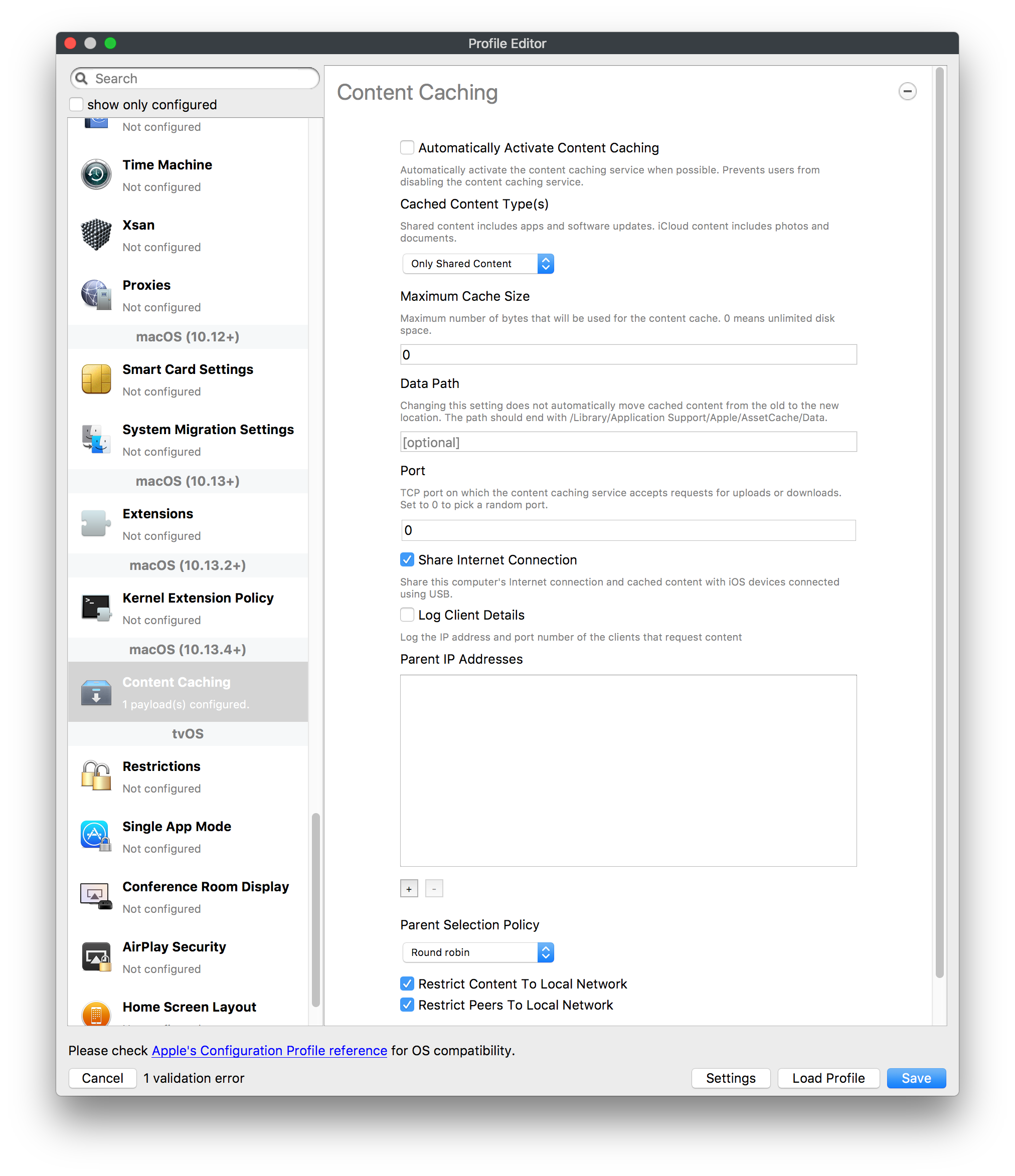](https://kb.filewave.com/uploads/images/gallery/2023-07/Gm8z6AnQRwwOZgoD-image.png) Use this section to configure content caching settings on macOS ## tvOS ### Restrictions [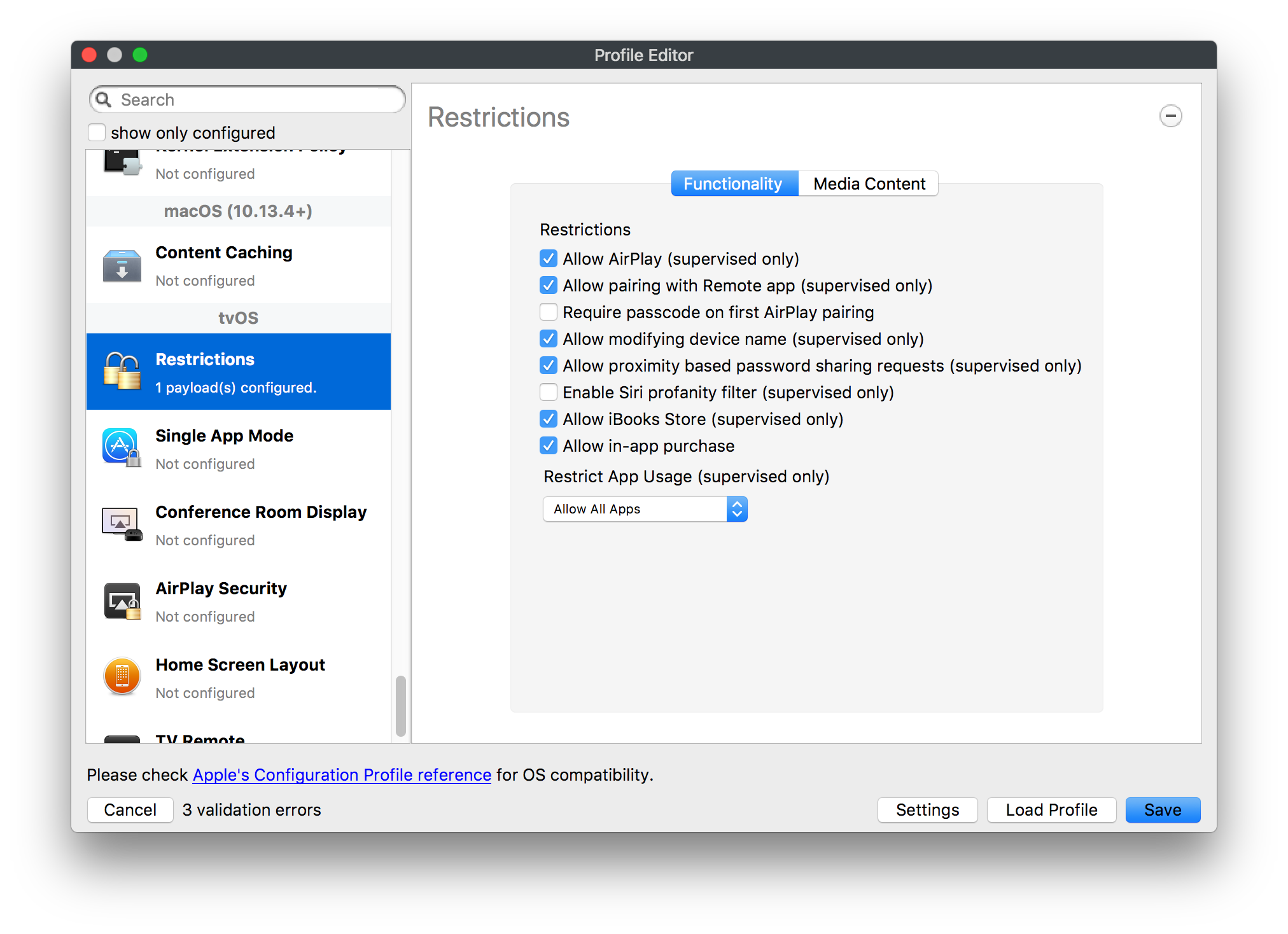](https://kb.filewave.com/uploads/images/gallery/2023-07/V2CNMAN9UXNzkNOs-image.png) [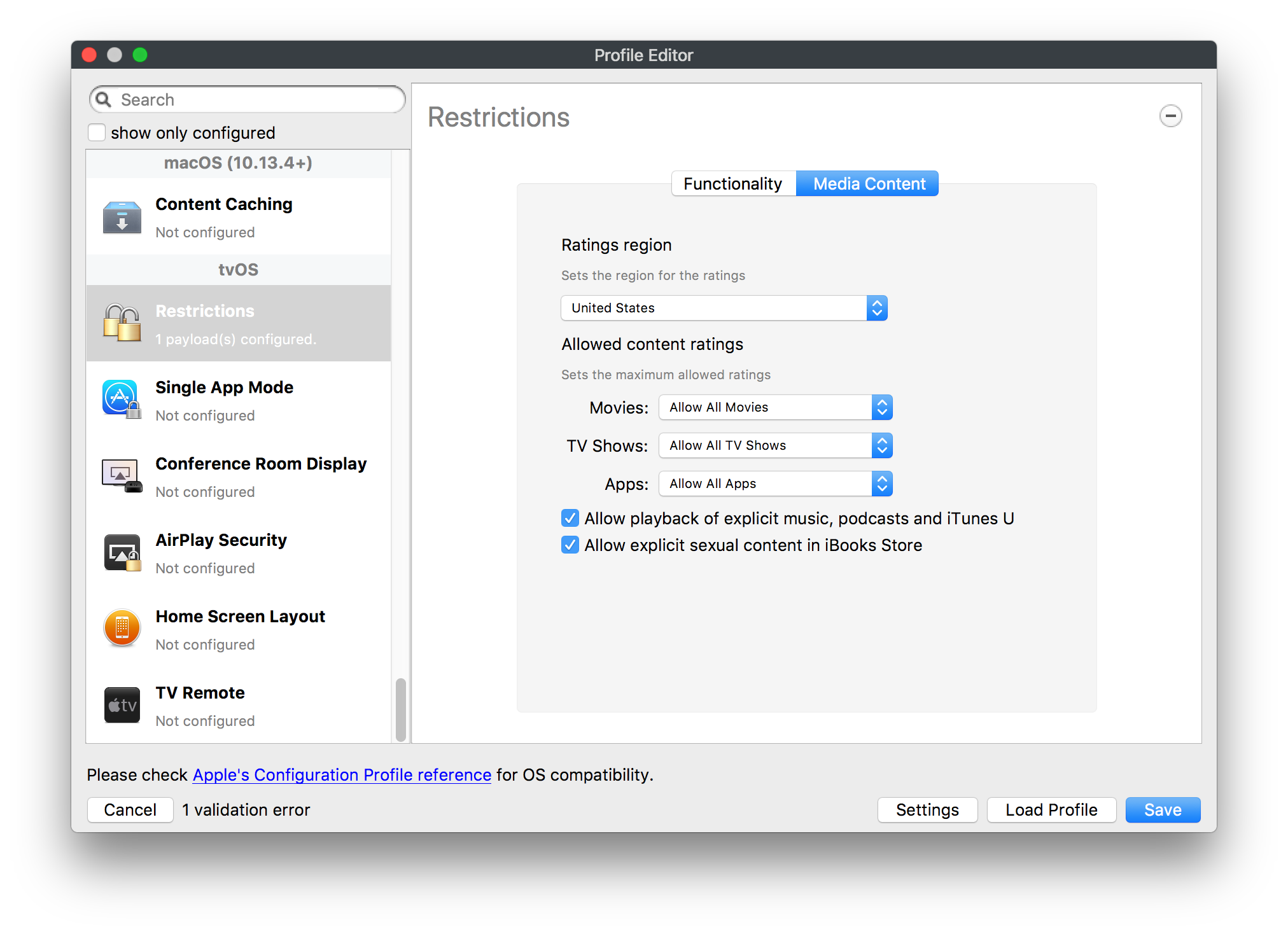](https://kb.filewave.com/uploads/images/gallery/2023-07/hPy0kATtslt6IZO4-image.png) Restrictions allows you to push three different restrictions to your Apple TV. Disable Airplay (supervised only)Require passcode on first AirPlay pairingDisable control using Remote app (supervised only) ### Single App Mode [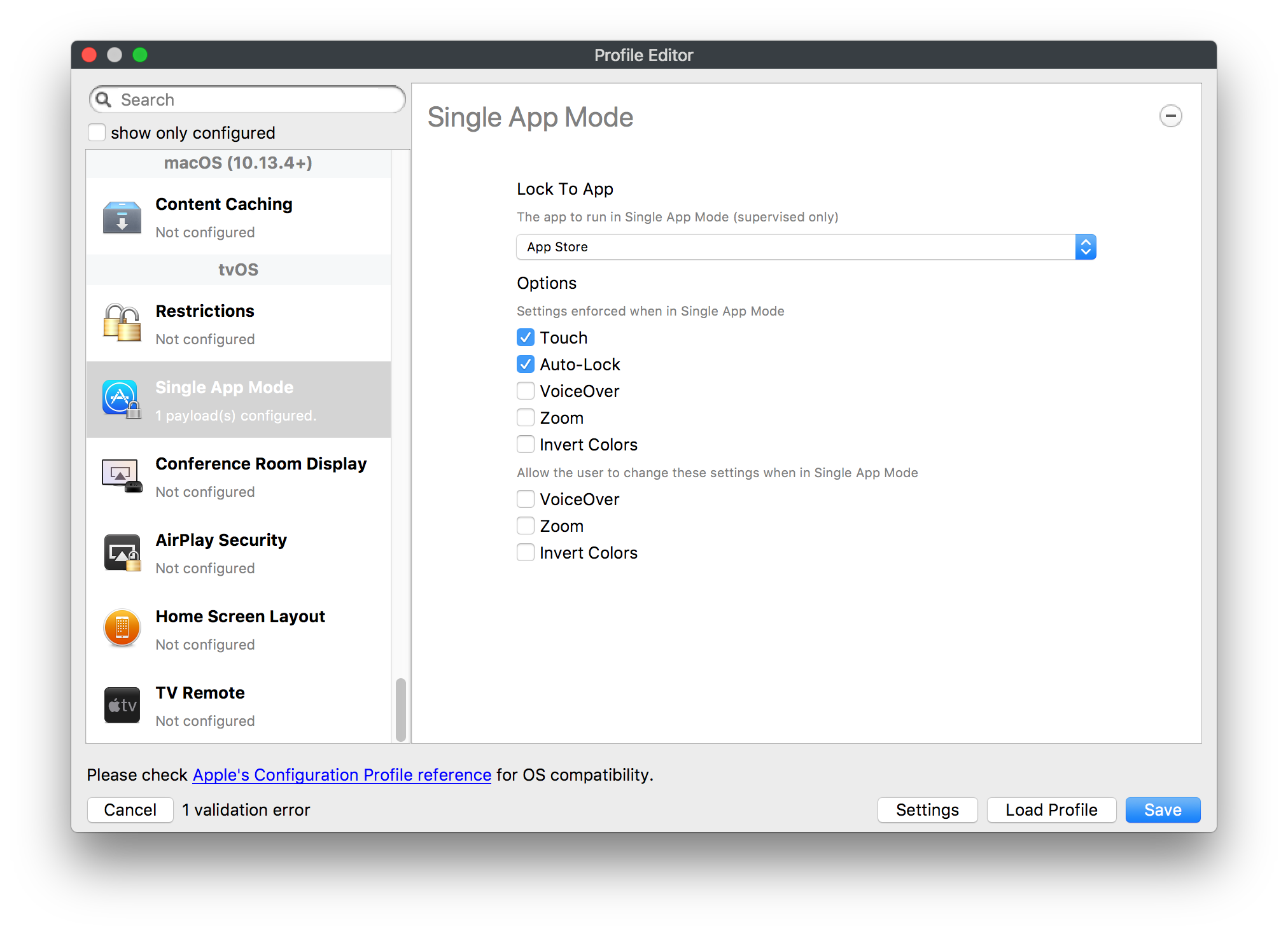](https://kb.filewave.com/uploads/images/gallery/2023-07/1thRIXaqT6nhCO0c-image.png) Use this section to specify the app to which the device should be locked to. These settings will only affect supervised devices. ### Conference Room Display (supervised only) [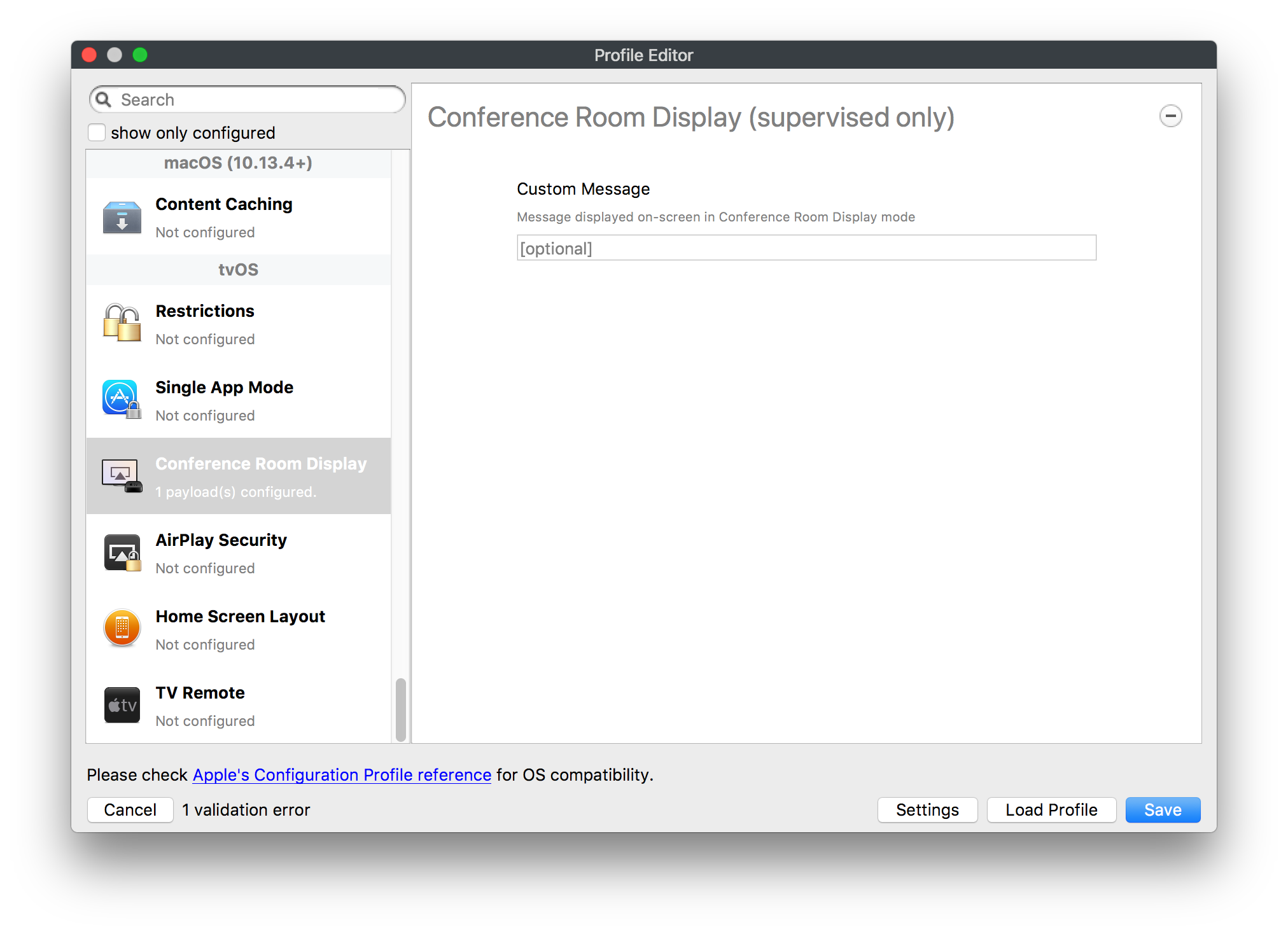](https://kb.filewave.com/uploads/images/gallery/2023-07/ibQcdNaqw0meN5F5-image.png) Use this section to put a supervised Apple TV into Conference room Display mode. ### AirPlay Security [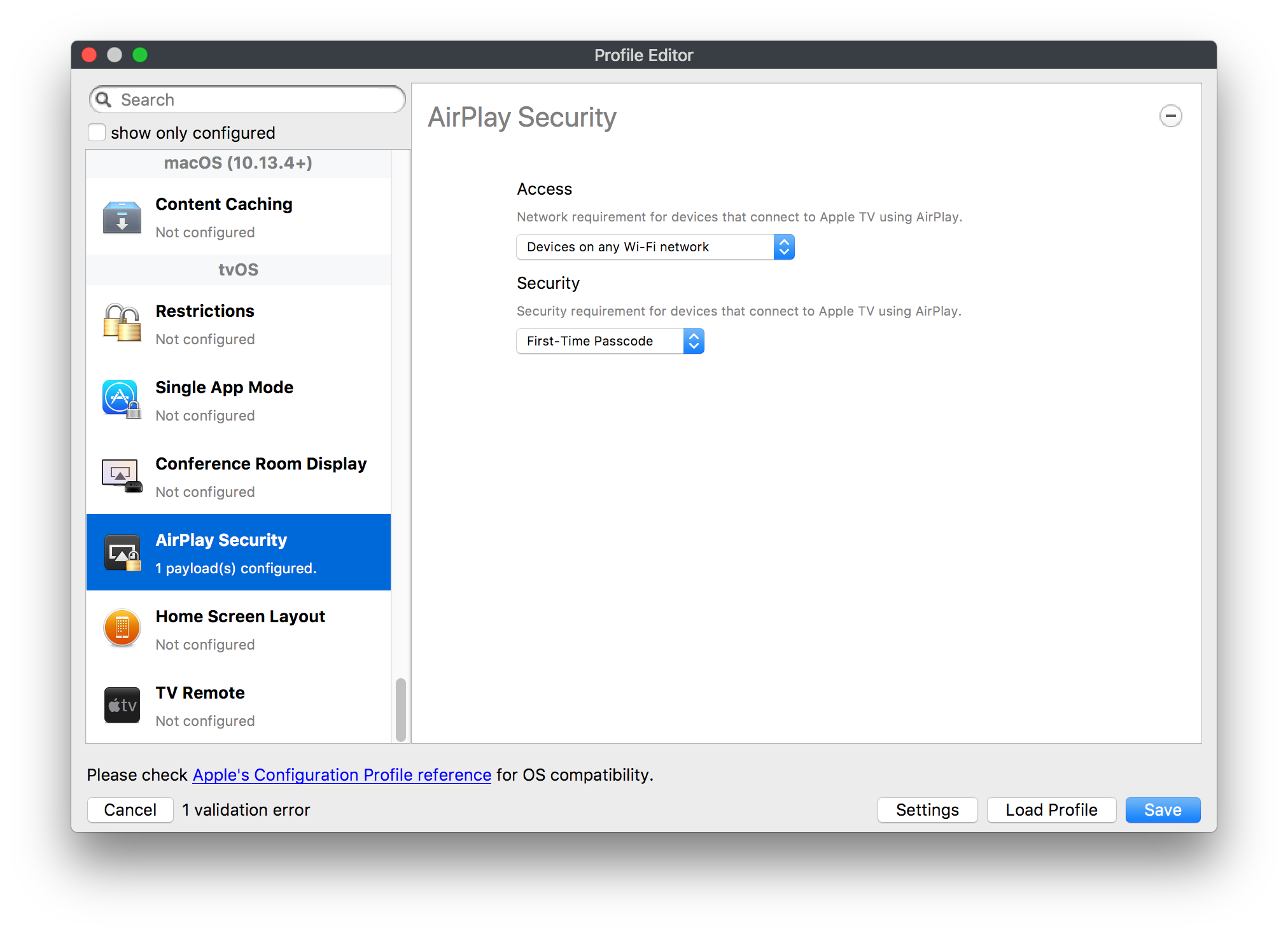](https://kb.filewave.com/uploads/images/gallery/2023-07/5y8I6rTUWPw7Ewr0-image.png) Use this section to configure settings for AirPlay security ### Home Screen Layout (supervised only) [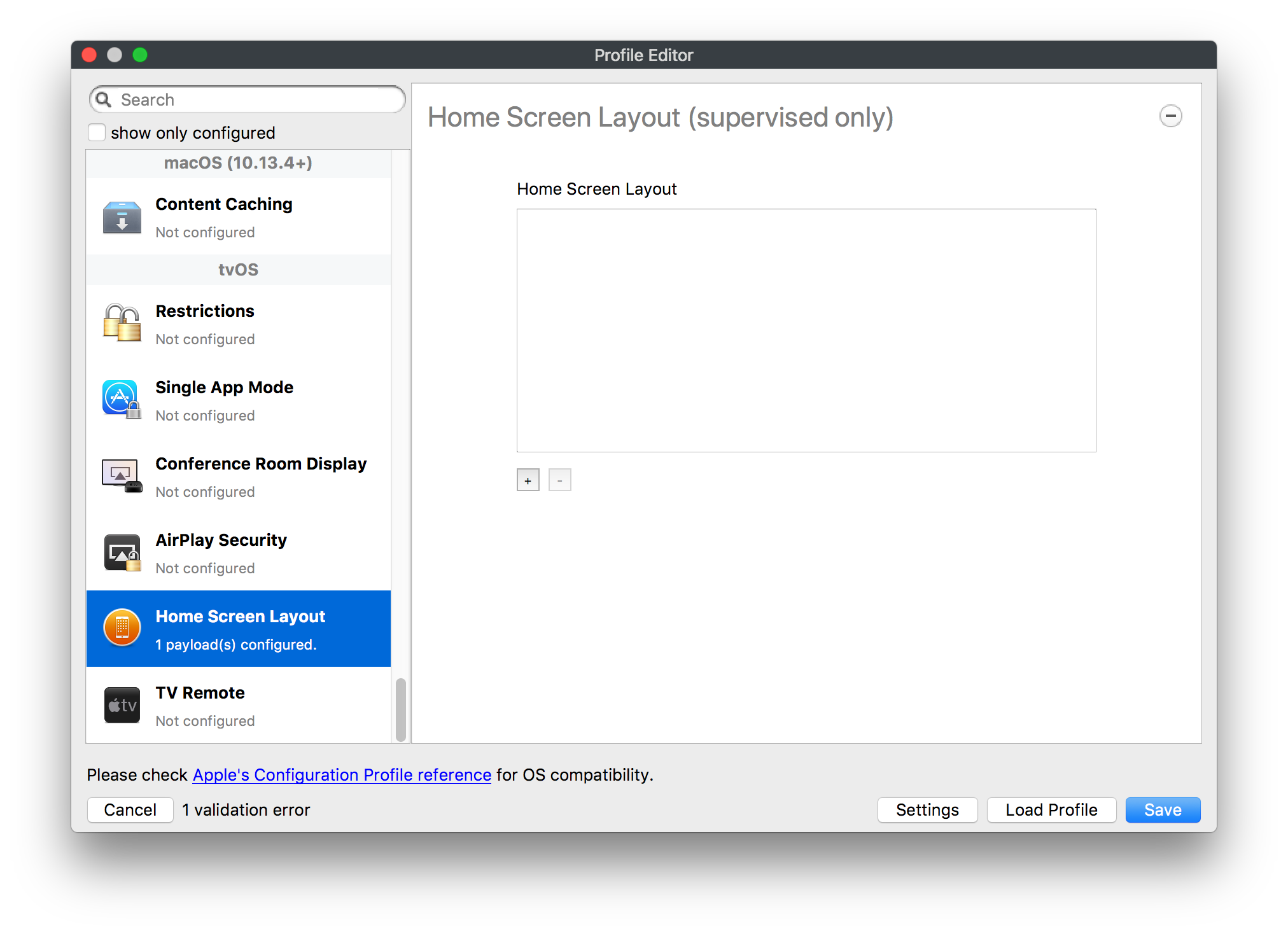](https://kb.filewave.com/uploads/images/gallery/2023-07/O2rPq6IJempd1AKU-image.png) Use this section to configure tvOS home screen layout. These setttings will only affect supervised devices. ### TV Remote (supervised only) [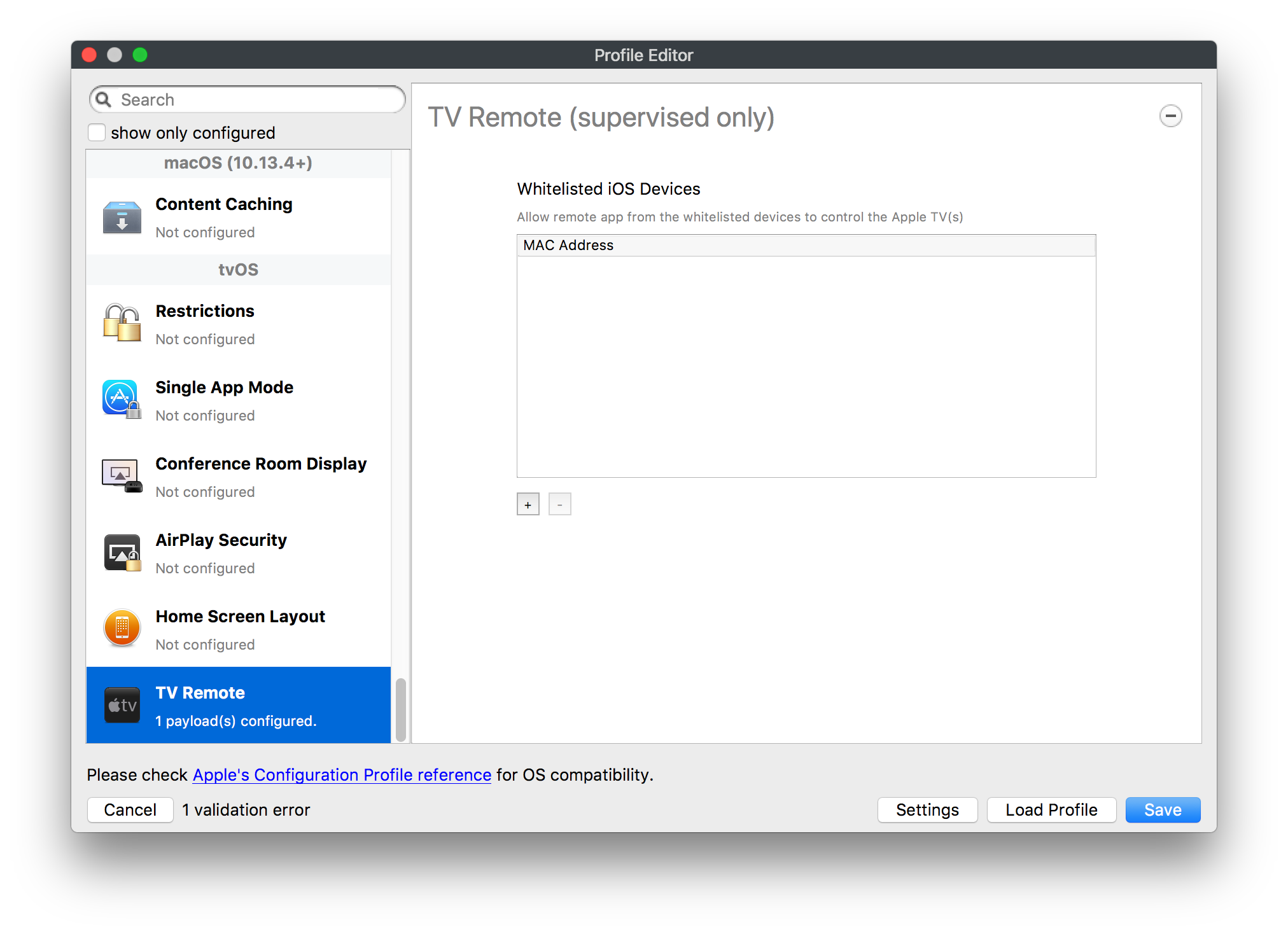](https://kb.filewave.com/uploads/images/gallery/2023-07/hNgcEDg5nxEnUXzy-image.png) Use this section to configure the list of iOS devices that can control the Apple TV(s). These settings will only affect supervised devices. # Profiles in macOS 11 Big Sur and beyond must be installed via MDM Prior to Big Sur, profiles could be installed on macOS devices in multiple ways, including: - Opening a profile locally in System Preferences - Command line tools - Via MDM to devices that are MDM enrolled FileWave had the ability to use either of the latter two options, defaulting to MDM if the device were MDM enrolled at the time of receiving the association. As of Big Sur, Apple made a fundamental change, denying the ability to add profiles using command line tools; they may still be removed though. **This leaves MDM as the only manageable option in Big Sur onwards**. FileWave was required to remember the method of profile installation: via FileWave Client app or via MDM. Each of these methods uses a different channel to instal the profile; to change channel requires removing the profile and re-installing it. Note though, that updating profiles alone could still be achieved and will use the same method of delivery without consequence where allowed. Example: - Associate a Dock profile to a non-MDM enrolled device and Update Model - Profile will instal using the FileWave Client App - Subsequently MDM enrol the device - Update the dock profile and Update Model - The update of the profile will continue to be handled using the FileWave Client App - Newly associated profiles would though be handled by MDM. - Remove the association of the Dock profile, Update Model - Once removed, re-associate the Dock profile and Update Model - Since the device is now MDM enrolled, the profile will be delivered using MDM, as will any updates to this profileNote that not every type of change that a profile makes can be cleanly undone simply by removing the profile. One example would be if you add a printer via profile and then remove the profile the printer will remain. Always test adding and take a look at what happens when removing a setting.
### Impact Consequences can therefore occur when devices are upgraded to macOS Big Sur or higher.If devices rely upon profiles, for example providing network connectivity, and the profile is removed to be re-installed, the network will be lost and the new profile will never become installed until the device is back online. As such, FileWave will not attempt to change the channel of delivery of these profiles, but careful consideration should be contemplated when manually attempting to use this process. Other examples could include profiles containing certificates, VPN, etc.
#### Devices not MDM enrolled Where devices are not MDM enrolled: - Any associated profile would have been installed using the FileWave Client App prior to Big Sur - After upgrading to Big Sur, profiles would remain installed - Once on Big Sur any attempt to make changes to the profile will result in a failure to deliver the update - Once on Big Sur any new profile associations will also fail - Disassociation of a profile will remove the profile #### Device MDM enrolled after profile installation When not MDM enrolled, the above would still be of consideration. However after MDM enrolled: - Any new association will instal via MDM - Removing an association, allowing the device to remove the profile and then re-associating the profile will then instal the profile using MDM This is the same impact even if not upgraded to Big Sur ### Resolution Management of profiles on Big Sur relies upon devices being MDM enrolled. If not they may not be installed or updated. As such devices must be MDM enrolled Where profiles were installed not using MDM, the only way for these profiles to become managed is by removing the association, allowing the device to remove the profile and then creating a new association. As highlighted above, take great care in the choice of profile removal if you have network reliance on installed profiles. This will require some manual method of transition where this is the case. ### Additional Information If the Client Info of a Device does not have a 'Command History' tab, it should imply that the device is not MDM enrolled. In this instance, only the FileWave Client App may instal Filesets of any type. Note Apple's VPP also requires MDM. # Restrictions Profile & Control Center ## What Apple provides separate Restrictions profiles for iOS, macOS and tvOS. macOS Ventura has somewhat altered System Preferences and is now System Settings, aligning it with iOS. This has implications. ## When/Why To date, the Restrictions Payload provided the ability to control the System Preference Panes viewable on macOS. This was either a list of those denied or those allowed. - EnabledThis recipe was tested on 10.13.2 with Safari 11.0.2
## Ingredients - FW Admin ## Directions 1. Create a New Desktop Fileset and select the **Profile** option 2. Name the profile in the **General** payload and fill out the **Custom Settings** payload with the following information where the value can be whatever site you wish: Preference Domain : com.apple.safari Key: HomePage Type: String Value: [https://www.filewave.com ](https://ww.filewave.com/) 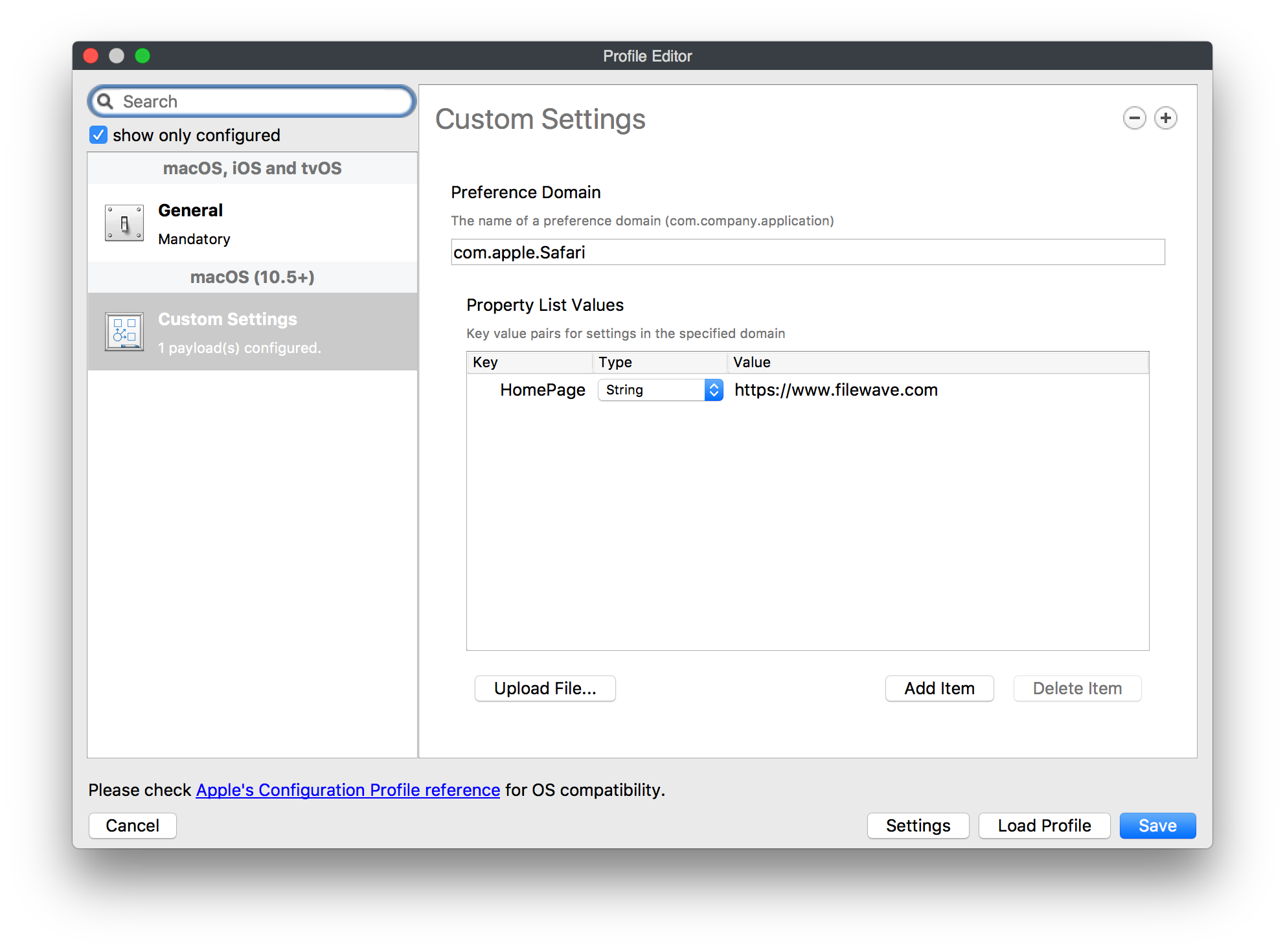 3. Close the **Profile Editor** 4. Double click on the newly created profile → select the settings tab → uncheck the box for "Users" under installation and check the box for "System" under installation. 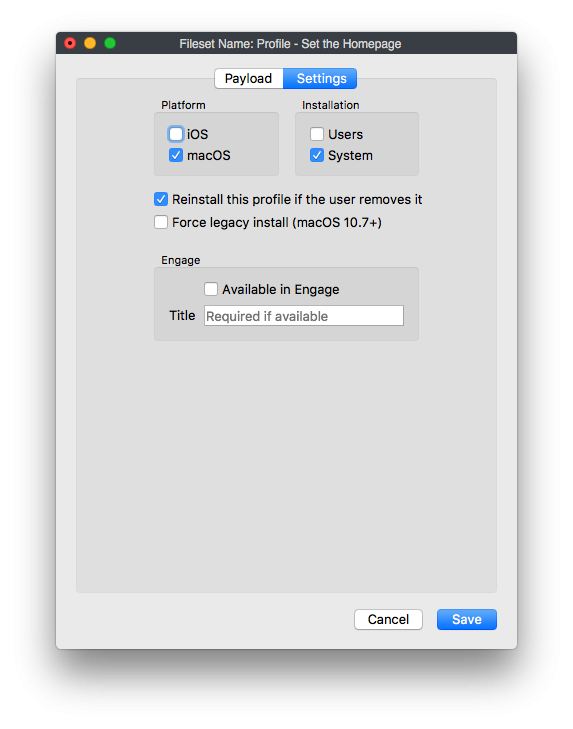 5. Then deploy the profile out to your selected macOS devices. ### Notes Some additional options that may require consideration:"*This payload defines a layout of apps, folders, and web clips for the Home screen. **On iOS, this layout is locked and can't be modified by the user**.*"
"*If a home screen layout puts more than four items in the iPhone or iPod touch dock the location of the fifth and succeeding items may be undefined but they will not be omitted*."
## Step-by-step guide 1. In the Admin console, create new Mobile Fileset> Profile 2. Configure the "General" payload to give the profile a name 3. Configure the "Command Policy" payload and select the relevant option in the section "Wallpaper" combo box. 4. Click "Save" at the bottom left to save your profile. [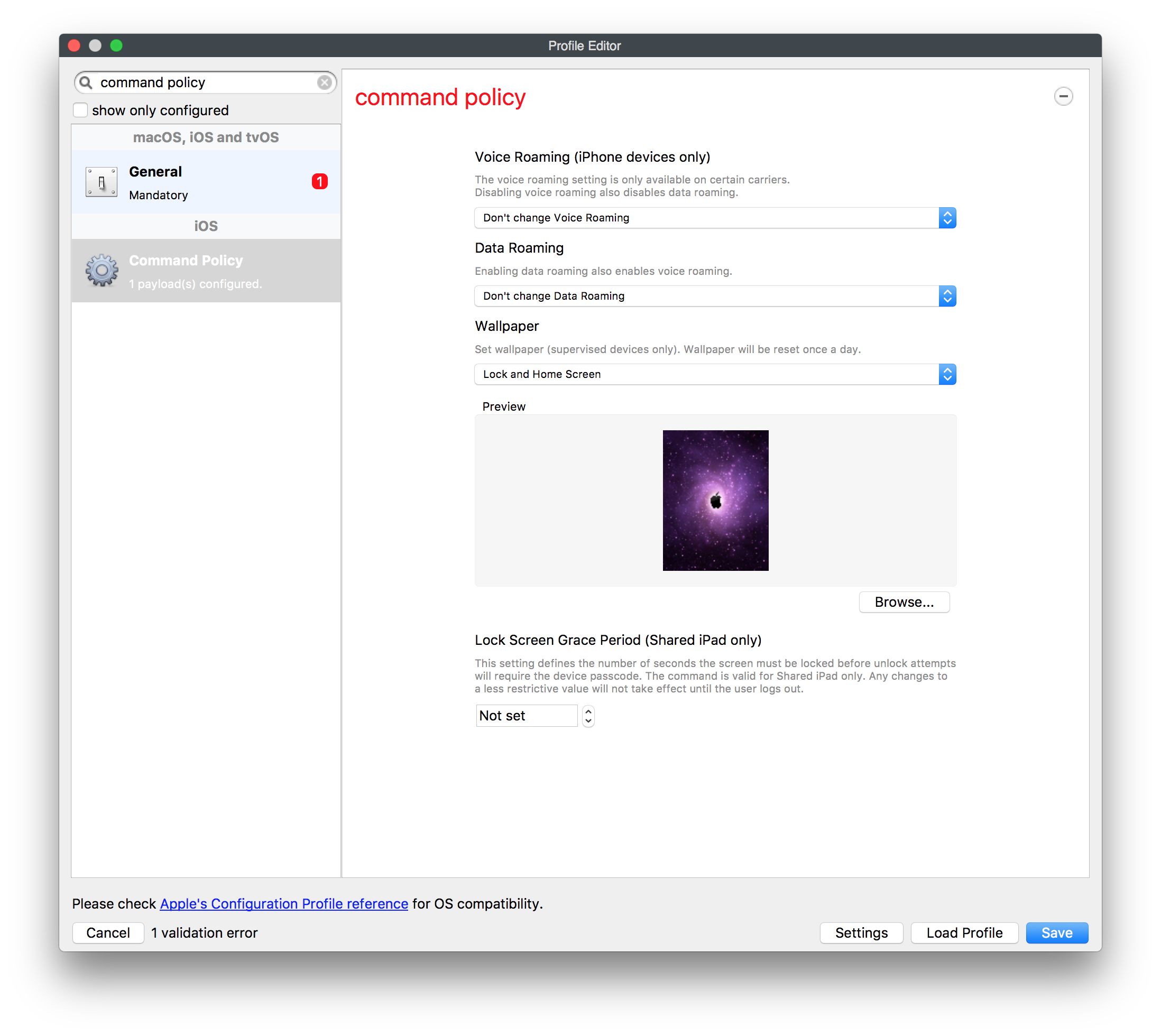](https://kb.filewave.com/uploads/images/gallery/2023-07/by3HkM8MzXdM5iP6-image.png) Deploy the Command Policy payload to a group of test devices, and after successful installation, deploy to your wider population of devices. **Note**: It is best practice when creating your wallpaper to try and create the image file as small as possible to expedite the deployment process. Also, when deploying this payload, it will execute as a command on a recurring basis (every day) to ensure that the wallpaper will be re-applied correctly. ## Related articles - [Customizing iOS Device Wallpaper with Dynamic Text](https://kb.filewave.com/books/ios-ipados/page/customizing-ios-device-wallpaper-with-dynamic-text "Customizing iOS Device Wallpaper with Dynamic Text") # Setting Timezones on Apple Devices ## What In FileWave 14.1+ you are able to make command policy profiles for iOS (14+ supervised) and tvOS (14+ supervised) ## When/Why Setting the timezone can help a user with their localization settings. ## How| Native Admin | Web Admin |
| 1. Filesets view 2. New Mobile ( or Desktop) Fileset 3. Profile 4. Command Policy 5. Configure... 6. Find "Time Zone" You can choose between \* **Don't Change timezone** - (Default) Does nothing \* **Use FWAdmin time zone (X)** - Where X should be the timezone of the computer admin is running \* This option is something like a quick-set value that makes it so you don't have to wade through the long list of time zones \* **Select from the list of all time zones** - A second drop down list will show of available timezones [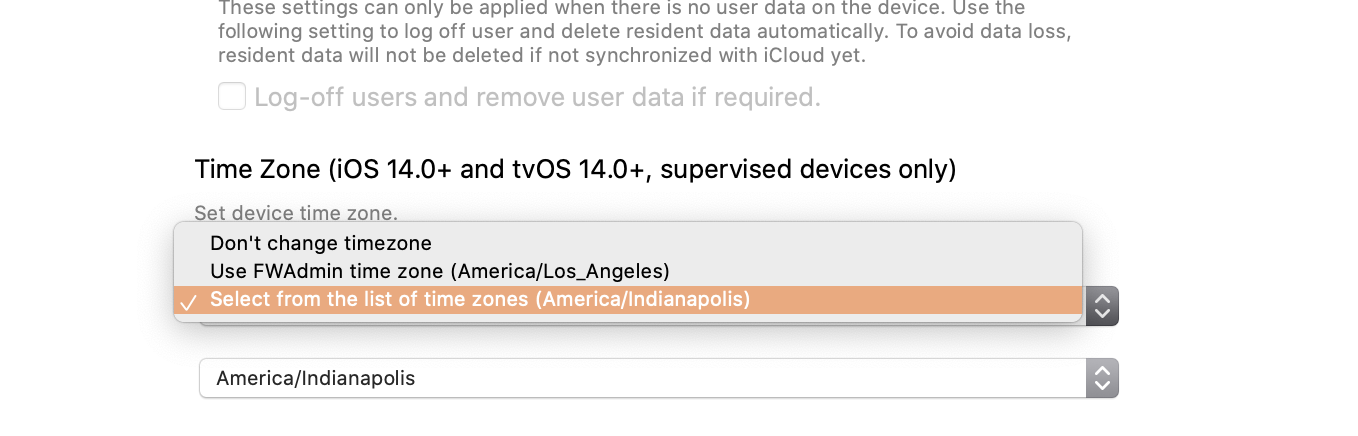](https://kb.filewave.com/uploads/images/gallery/2023-07/IYffN6AsoVk9Rrm8-image.png) | 1. Payloads 2. Plus  3. Command Policy 4. Configure 5. Find "Time Zone" You can choose between \* **Don't Change timezone** - (Default) Does nothing \* **Use FWAdmin time zone (X)** - Where X should be the timezone of the computer admin is running Known issue that the webadmin does not reflect the proper local timezone...under development \* **Select from the list of time zones** - A second drop down list will show of available timezones [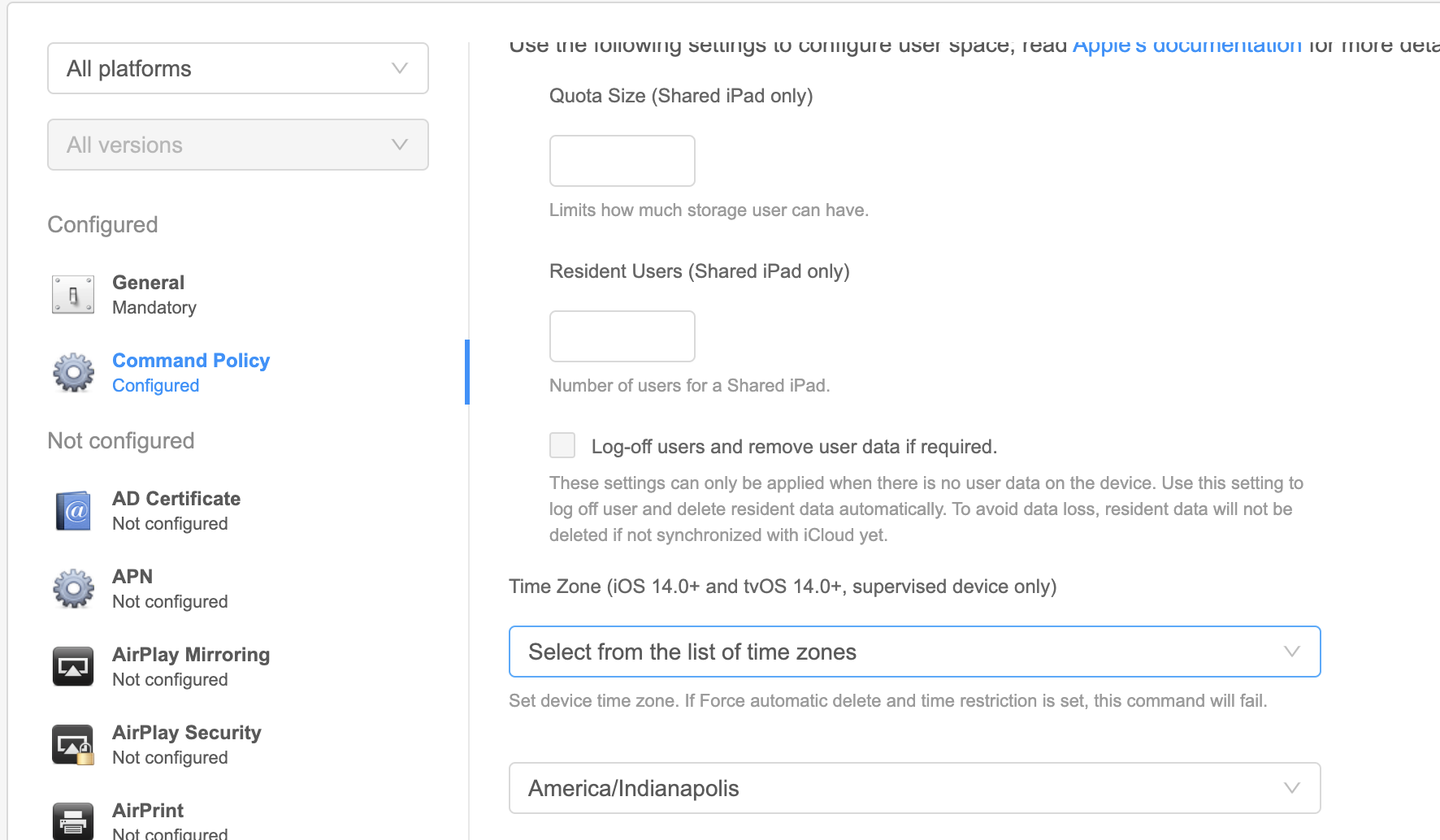](https://kb.filewave.com/uploads/images/gallery/2023-07/FMDJtF9xyw0sdhLU-image.png) |
| %first\_name% %last\_name% %full\_name% %short\_name% %email% %job\_title% %mobile\_phone% %guid% |
For the above user strings to work you must be pointed to an Directory server and have it selected as authentication
You can also map custom fields to LDAP parameters to extend the above list. See [Custom Fields](https://kb.filewave.com/books/custom-fields/page/custom-fields "Custom Fields") for more information.
## Inventory / Device Parameters Starting in FileWave **6.1+** you can reference specific information about the device as well, directly from FileWave Inventory. Those fields are:| %OSVersion% %SerialNumber% %ProductName% %BuildVersion% %WIFIMAC% %ICCID% %IMEI% |
| Common Device Parameters | Type | FileWave Version Introduced |
| %archived% | datetime | 13.0.0 |
| %auth\_username% | string | 13.0.0 |
| %cpu\_count% | int | 13.0.0 |
| %cpu\_type% | string | 13.0.0 |
| %current\_ip\_address% | string | 13.0.0 |
| %last\_enterprise\_app\_validation\_date% | datetime | 13.0.0 |
| %last\_state\_change\_date% | datetime | 13.0.0 |
| %department% | string | 13.0.0 |
| %device\_id% | string | 13.0.0 |
| %device\_name% | string | 13.0.0 |
| %device\_product\_name% | string | 13.0.0 |
| %enroll\_date% | datetime | 13.0.0 |
| %filewave\_client\_name% | string | 13.0.0 |
| %filewave\_id% | string | 13.0.0 |
| %free\_disk\_space% | int | 13.0.0 |
| %is\_system\_integrity\_protection\_enabled% | bool | 13.0.0 |
| %is\_tracking\_enabled% | bool | 13.0.0 |
| %last\_check\_in% | datetime | 13.0.0 |
| %last\_ldap\_username% | string | 13.0.0 |
| %last\_logged\_in\_username% | string | 13.0.0 |
| %location% | string | 13.0.0 |
| %management\_mode% | int | 13.0.0 |
| %monitor\_id% | string | 13.0.0 |
| %ram\_size% | int | 13.0.0 |
| %serial\_number% | string | 13.0.0 |
| %state% | int | 13.0.0 |
| %total\_disk\_space% | int | 13.0.0 |
| %unenrolled% | bool | 13.0.0 |
| %is\_user\_enrollment% | bool | 13.2.0 |
| %is\_activation\_lock\_manageable% | bool | 13.2.0 |
| %remote\_desktop\_enabled% | bool | 13.2.0 |
| %external\_boot\_level% | bool | 13.2.0 |
| Desktop Device Parameters | Type | |
| %device\_manufacturer% | string | 13.0.0 |
| %filewave\_client\_locked% | bool | 13.0.0 |
| %filewave\_client\_version% | string | 13.0.0 |
| %filewave\_model\_number% | int | 13.0.0 |
| %rom\_bios\_version% | string | 13.0.0 |
| iOS Device Parameters | Type | |
| %battery\_level% | float (from 0 to 1) | 13.0.0 |
| %last\_cloud\_backup\_date% | datetime | 13.0.0 |
| %last\_wallpaper\_change\_date% | datetime | 13.0.0 |
| %apple\_device\_id% | string | 13.0.0 |
| %eas\_device\_identifier% | string | 13.0.0 |
| %is\_activation\_lock\_enabled% | bool | 13.0.0 |
| %is\_device\_locator\_service\_enabled% | bool | 13.0.0 |
| %is\_do\_not\_disturb\_in\_effect% | bool | 13.0.0 |
| %is\_cloud\_backup\_enabled% | bool | 13.0.0 |
| %is\_mdm\_lost\_mode\_enabled% | bool | 13.0.0 |
| %is\_supervised% | bool | 13.0.0 |
| %awaiting\_configuration% | bool | 13.0.0 |
| %is\_network\_tethered% | bool | 13.0.0 |
| %itunes\_store\_account\_is\_active% | bool | 13.0.0 |
| %itunes\_store\_account\_hash% | string | 13.0.0 |
| %languages% | string | 13.0.0 |
| %locales% | string | 13.0.0 |
| %maximum\_resident\_users% | int | 13.0.0 |
| %meid% | string | 13.0.0 |
| %model% | string | 13.0.0 |
| %organization\_info% | string | 13.0.0 |
| %product% | string | 13.0.0 |
| %product\_name% | string | 13.0.0 |
You can also map custom fields to script results to extend the above list. See [Custom Fields](https://kb.filewave.com/books/custom-fields/page/custom-fields "Custom Fields") for more information.
| You can also look in the inventory query builder and it will tell you the internal name in the bottom left: 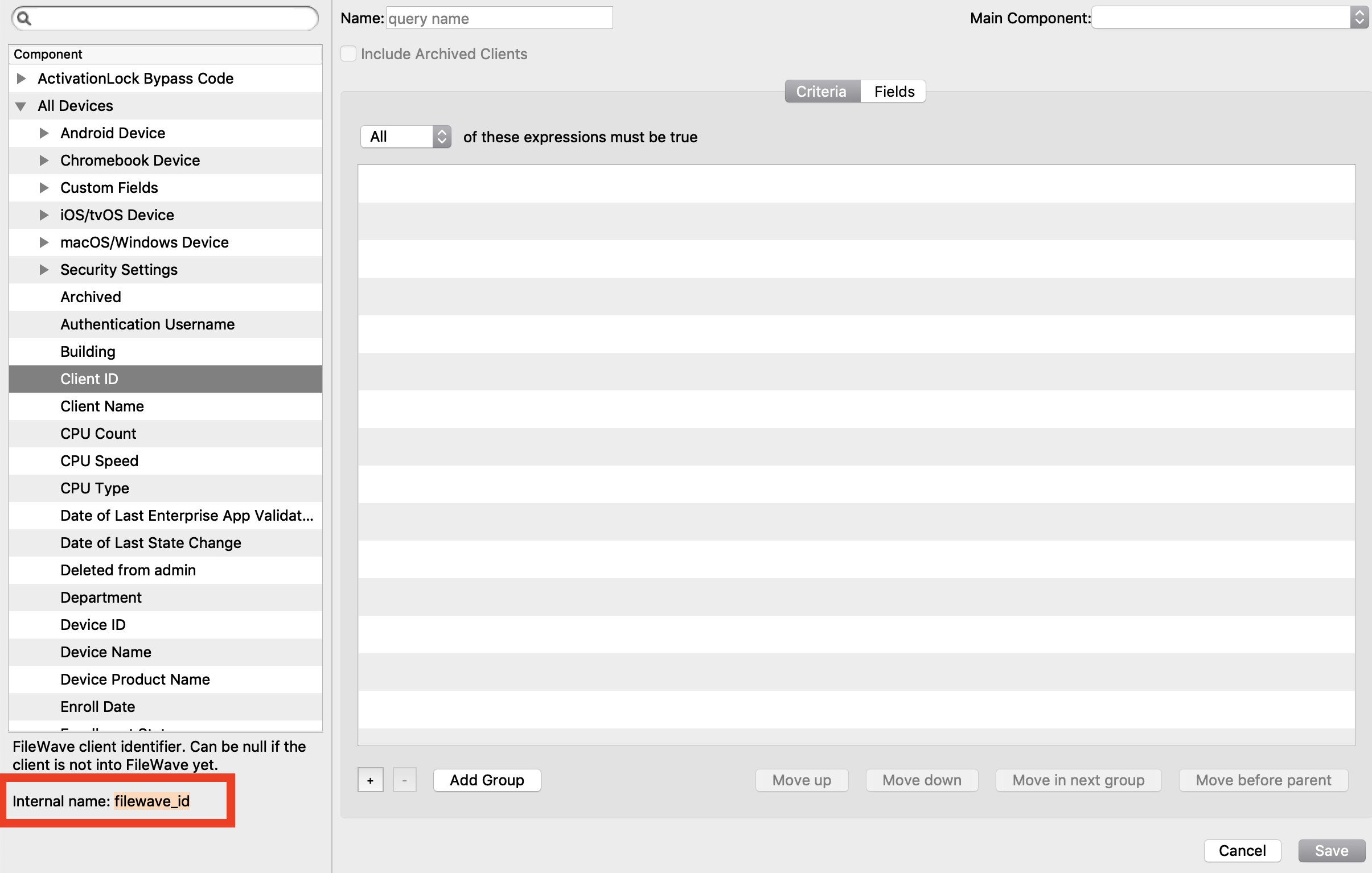 |
| Profile Parameters | LDAP attribute name | Remarks |
| short\_name | uid | |
| first\_name | givenName | |
| last\_name | sn | |
| full\_name | fullName | |
| job\_title | title | |
| mobile\_phone | mobile | |
| guid | GUID | A binary read-only attribute |
| Profile Parameters | LDAP attribute name |
| first\_name | givenName |
| full\_name | fullName |
| guid | apple-generateduid |
| job\_title | title |
| last\_name | sn |
| mobile\_phone | mobile |
| short\_name | uid |
| Profile Parameters | LDAP attribute name |
| first\_name | givenName |
| full\_name | fullName |
| guid | objectGUID |
| job\_title | title |
| last\_name | sn |
| mobile\_phone | mobile |
| short\_name | sAMAccountName |