**Admin Only:** In this scenario, admins would update each device to ensure that students are unable to change this permission. This is labor-intensive but locked down. **Admin or Students:** In this scenario, teachers instruct students on how to enable this permission. Please note that in this configuration, students will then be able to remove this permission. Such matters should be handled by instructing students in your district’s Acceptable Use Policy. This scales more easily, but it requires coordination. **Please note:** Screen recording policy follows Apple's privacy policy. Any user can agree to allow screen recording for the application, disable screen recording services, and revoke FileWave's right to view the screen, as per [Apple Inc. policy.](https://www.apple.com/legal/privacy/en-ww/)
Ensure this profile is deployed before proceeding with the PKG installation. Securly Classroom macOS Fileset has a placeholder for the PKG installer and a requirement script to check TCC Profile is installed before the PKG installation. [Securly Classroom macOS.fileset.zip](https://kb.filewave.com/attachments/448) ##### Requirement Script: Where software is already installed and services are active, Privacy Settings Profiles installed subsequently require the service of that software to be restarted. This Fileset example includes a Requirement Script that checks for profile installation before activating Securly, preventing the need to restart the service. The 'check\_profile.sh' script is designed to recognise one of the two provided Profiles and, once installed, allow activation of the Fileset. If Profiles with a different Profile ID are used instead of those supplied, the script settings will require alteration. - Double-click the Fileset - Select the 'check\_profile.sh' (located in a numbered subfolder in /var/scripts/) - Choose Get Info > Executable view The Launch Arguments display the Payload ID of the TCC profile. Add in the correct Fileset Profile UDID.| Fileset Contents | Check Profile script | Enter the TCC Profile UDID |
| [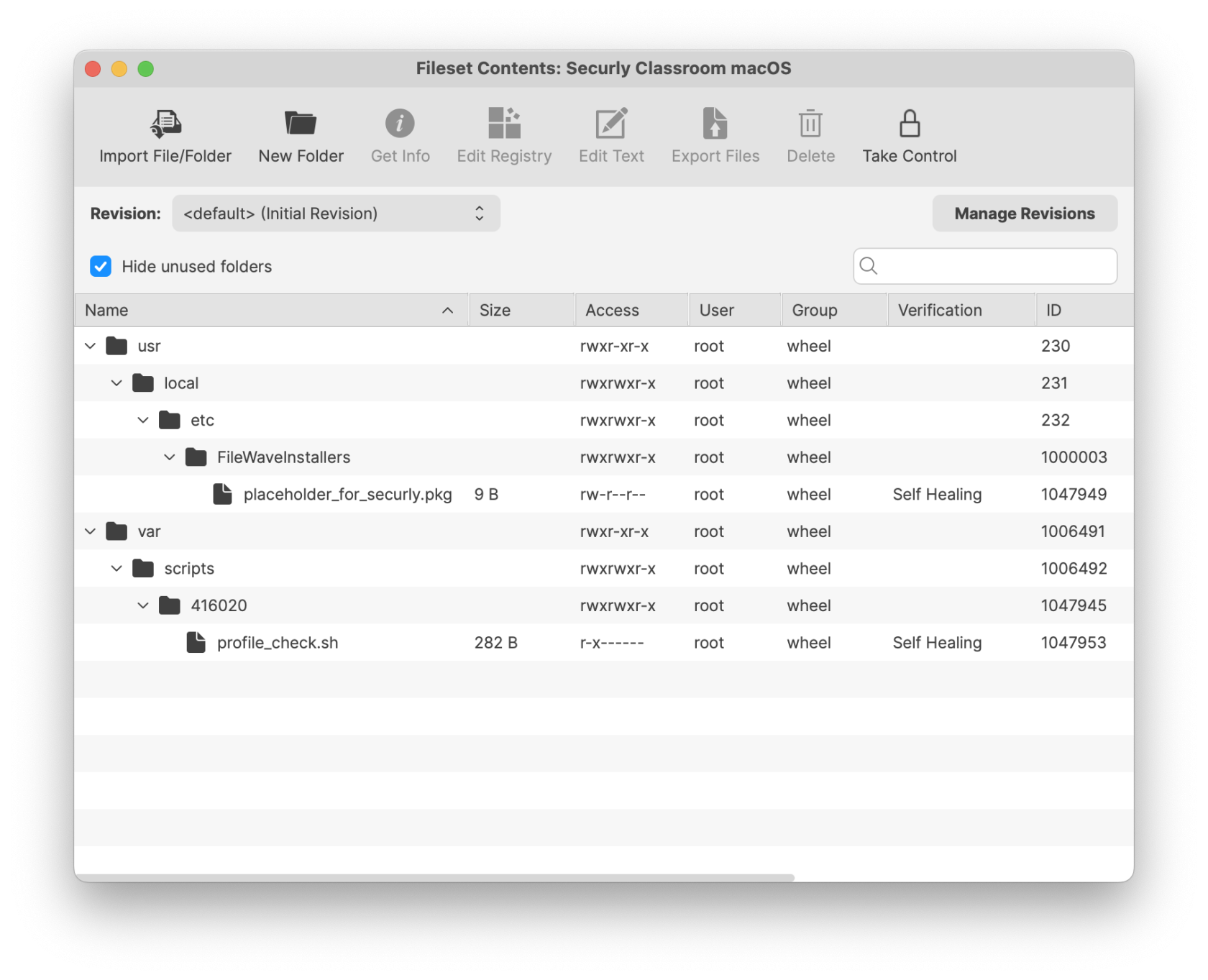](https://kb.filewave.com/uploads/images/gallery/2025-04/QXDVfIQklwWnVG13-securlyclassroommacos.png) | [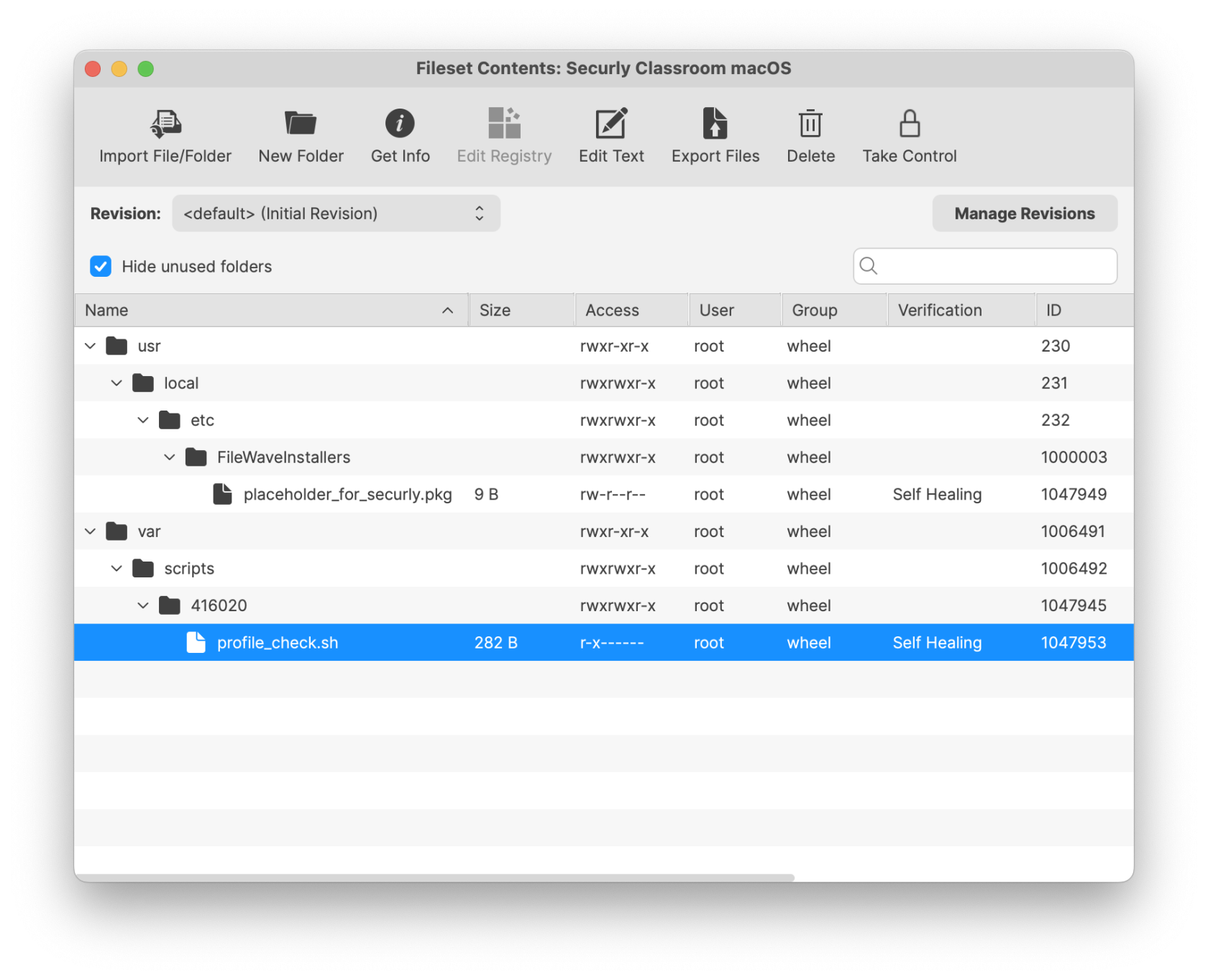](https://kb.filewave.com/uploads/images/gallery/2025-04/eGfMRTIHfGQ2oWkt-requirementtccprofile.png) | [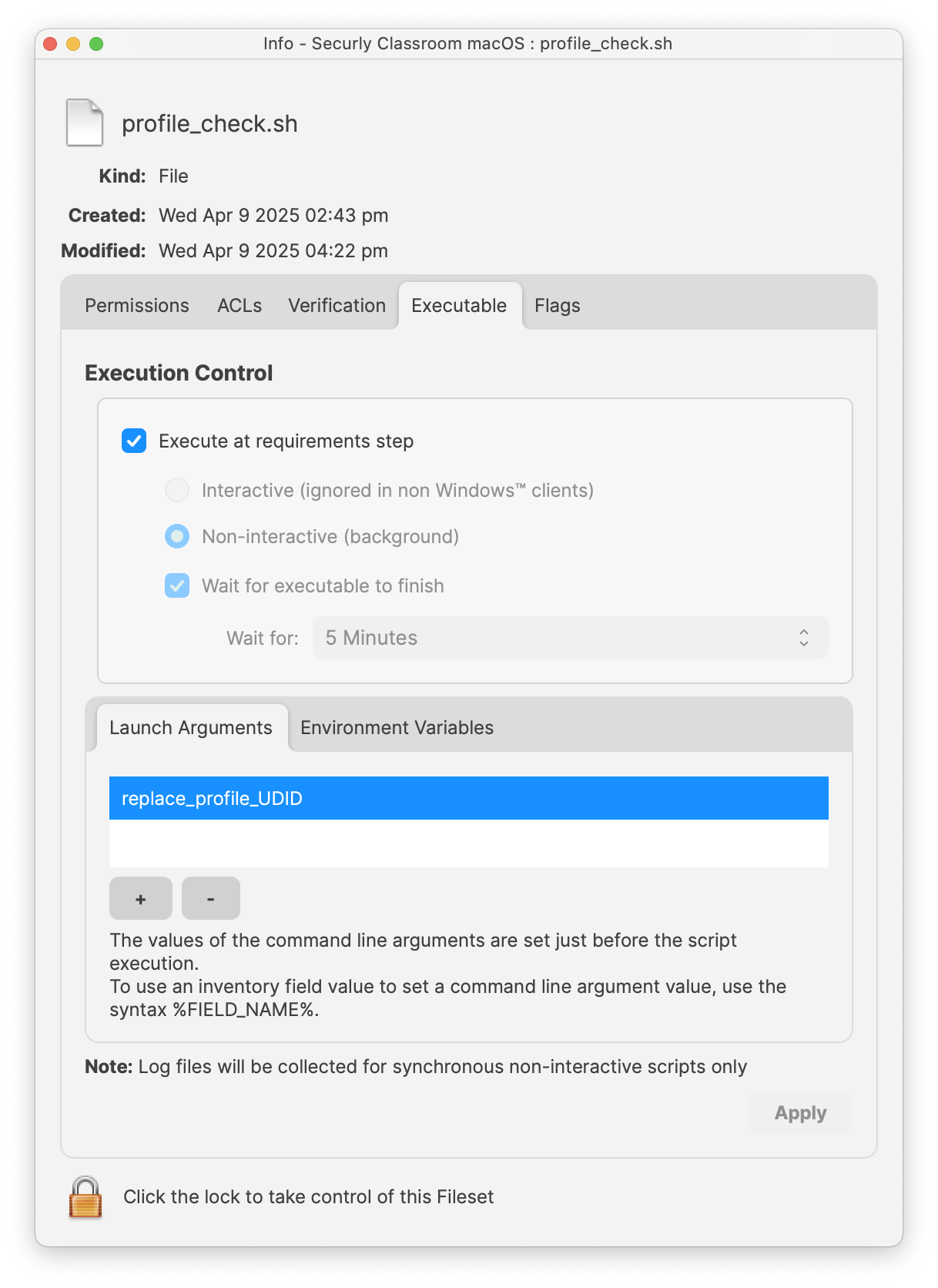](https://kb.filewave.com/uploads/images/gallery/2025-04/UO7GWatZDRtn6mjE-replaceudid.png) |