This article will give you as much detail as possible to help you get started, but this is incredibly easy software to deploy and configure and we'll show you how below.
Xcreds replaces the loginwindow and allows the connection with a directory providers that supports OIDC. Not all directory providers, however, support Apple's Platform SSO. At the time of writing, only Entra and Okta support Apple's Platform SSO.
## Ingredients - FW Admin - Example Fileset - [PKG - XCreds.fileset.zip](https://kb.filewave.com/attachments/474) - Configuration files - [Configuration + License](#bkmrk-software---download-) ## Directions XCreds has two components: - XCreds app -- runs in user space - XCreds Login Window -- security agent which runs when the user is logging in to macOS Example Login Window: [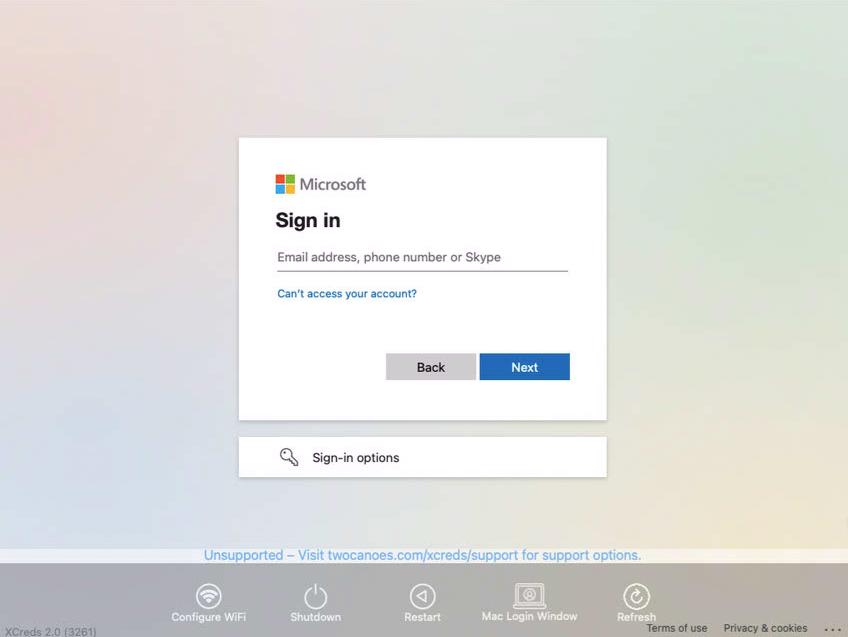](https://kb.filewave.com/uploads/images/gallery/2023-07/MJPAjQvRJE8CqM8w-image.png) Both the security agent and the app share keychain items in the user’s keychain to keep track of the current local password and the tokens from the cloud provider. Both items prompt the user with a web view to authenticate to their cloud provider, verify login was successful and then update both the local password and user keychain passwords as needed. ### Features| - Login Window log in to OIDC provider - Support for Azure, Google Cloud, Okta and any OIDC provider - Initial account provisioning - WiFi Login Window configuration - Restart and shutdown from Login Window - Profile manifest available for easy configuration - Local password update with IdP password - Prompt for IdP password when changed - Login Keychain password updating - Customizable preferences - Easy deployment - Uses OpenID Connect | - Attractive and pleasing menu icon - Easy configuration with profile / MDM - [Profile Manifest](https://github.com/ProfileCreator/ProfileManifests) for [Profile Creator](https://github.com/ProfileCreator/ProfileCreator) Support - Two-Factor and Multi-Factor support - New username and password window - Able to create a user as an admin using group member preference - Kerberos ticket - Switch to login window at screensaver - Reset keychain - Most preferences are now able to be overridden - Added shake to the password field |
| IdP | Microsoft Entra (Azure) | Okta | |
| Vendor Specific Instructions | [Microsoft Setup](https://twocanoes.com/knowledge-base/xcreds-setup-with-azure-oidc/) | [Okta Setup](https://twocanoes.com/knowledge-base/xcreds-setup-with-okta/) | [Google Setup](https://twocanoes.com/knowledge-base/xcreds-setup-with-google-oidc/) |
| Example Plist | [Microsoft Plist](https://twocanoes-app-resources.s3.amazonaws.com/xcreds/xcreds_example_azure.mobileconfig) | [Okta Plist](https://twocanoes-app-resources.s3.amazonaws.com/xcreds/okta/XCredsOktaTest.mobileconfig) | [Google Setup](https://twocanoes-app-resources.s3.amazonaws.com/xcreds/xcreds_example_google.mobileconfig) |
If the second option is actioned, the provided uninstaller will not be included, but could be added, based upon the details shown below in the uninstaller section.
##### IdP Configuration Follow the related IdP twocanoes documentation to configure the IdP App. Details from this App will be required in the next step. ##### Profile Creation Download ProfileCreator App and the twocanoes manifest from the Profile Creator page: - [ProfileCreator App Releases Page](https://github.com/ProfileCreator/ProfileCreator/releases) - [twocanoes Profile Manifest](https://github.com/ProfileCreator/ProfileManifests/blob/master/Manifests/ManagedPreferencesApplications/com.twocanoes.xcreds.plist) On the computer running Profile Creator, add the manifest to the following user location: ``` ~/Library/Application\ Support/ProfilePayloads/Manifests/ManagedPreferencesApplications/com.twocanoes.xcreds.plist ``` Run Profile Creator and add any items required from the chosen IdP settings, for example: Client ID, DiscoveryURL, etc. and save. [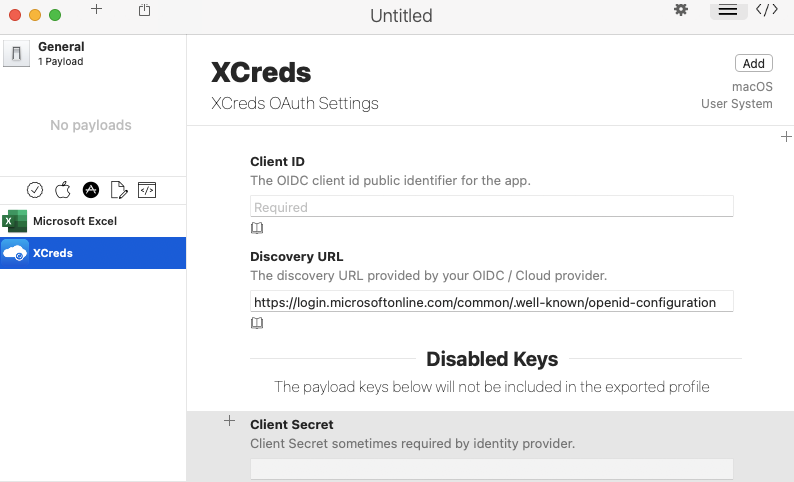](https://kb.filewave.com/uploads/images/gallery/2023-07/wy8603IOWVVXmmYr-image.png)For Microsoft DiscoveryURL, edit the plist, replacing 'common' with the Directory (Tenant) ID if available. For example: discoveryURL = https://login.microsoftonline.com/5c3864d2-38e9-5555-8888-621b9d17fd46/.well-known/openid-configuration
This Profile may now be used to create a Profile Fileset. Do so, by dragging this mobileconfig file to the same XCreds Fileset Group where the XCreds PKG Fileset resides. For example: [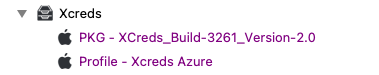](https://kb.filewave.com/uploads/images/gallery/2023-07/uzlukxsVdfSGg5PF-image.png)The contents of the XCreds payload are beyond the scope of the FileWave interface. Once imported to FileWave, the Payload may not be edited directly within FileWave. Any attempt to view the Payload will fail to show the XCreds portion of the Payload; ensure to Cancel and not save if opened. For the same reason, it is not possible to duplicate this Fileset either. Any editing should be handled within Profile Creator and the Payload re-uploaded to FileWave.
##### Testing The Fileset Group may now be associated with one or more test devices, as seen fit. Use the above details for the licence file during testing. Once tested and all is good, the scope of association may be increased and once purchased, the licence details should be pushed as another Profile. This may also be added to the same XCreds Fileset Group