| As shown here KBArticle, MsrcSeverity, Support URL, Category, and Description are the new fields. | 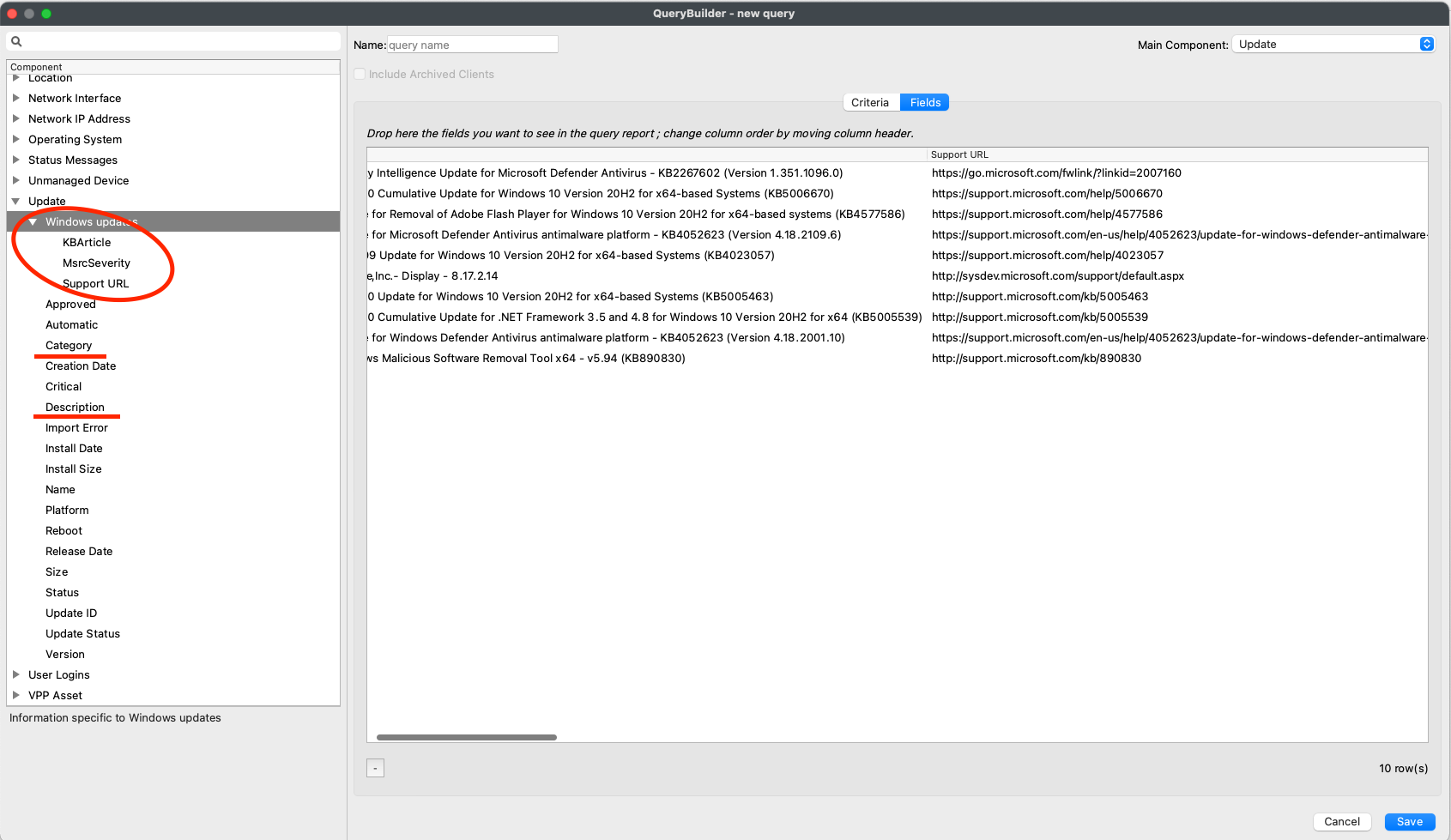 |
| This is an example of Support URL, KBArticle, and MsrcSeverity used in a report. | 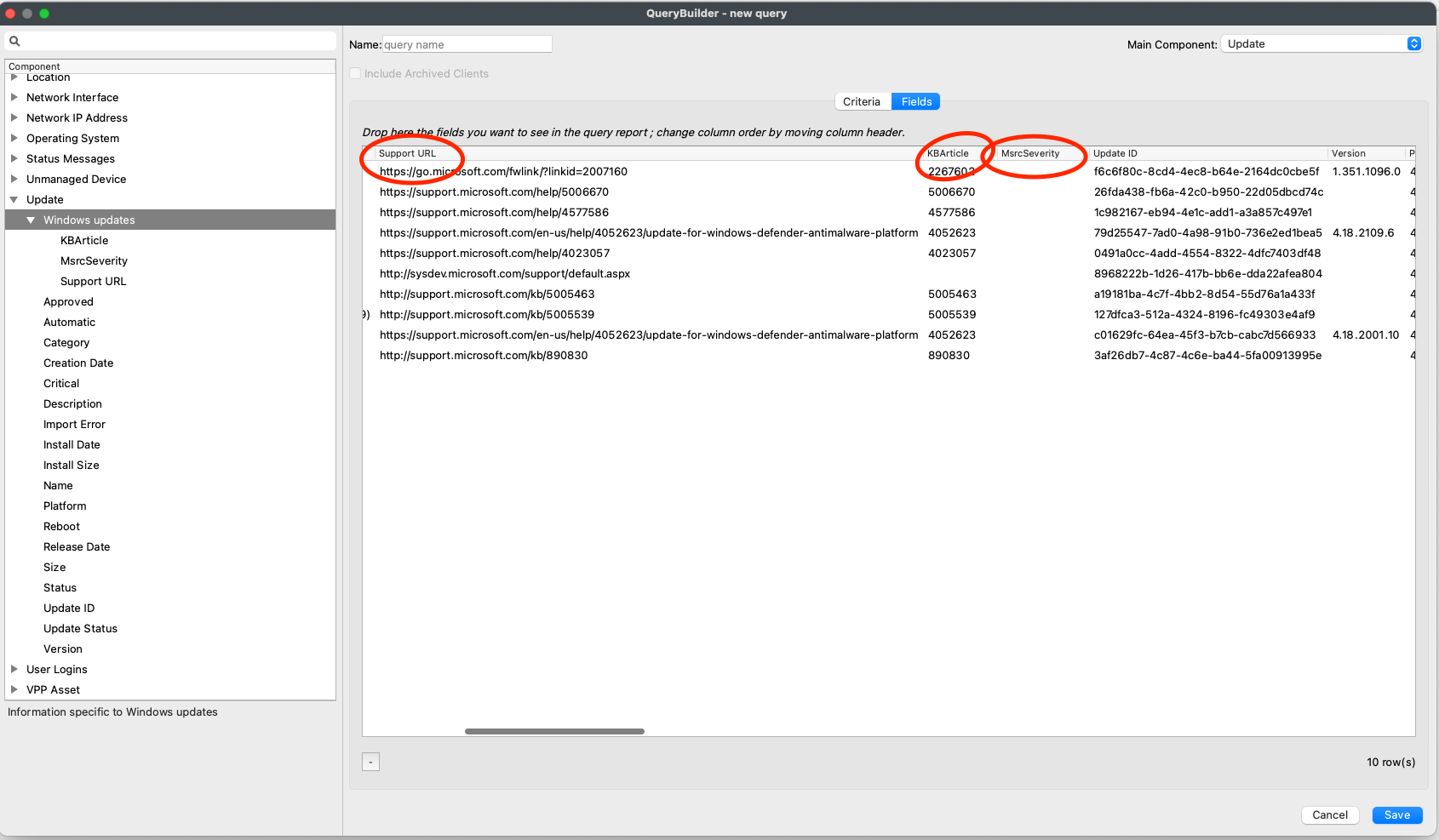 |
| These examples show Category and then Description. | 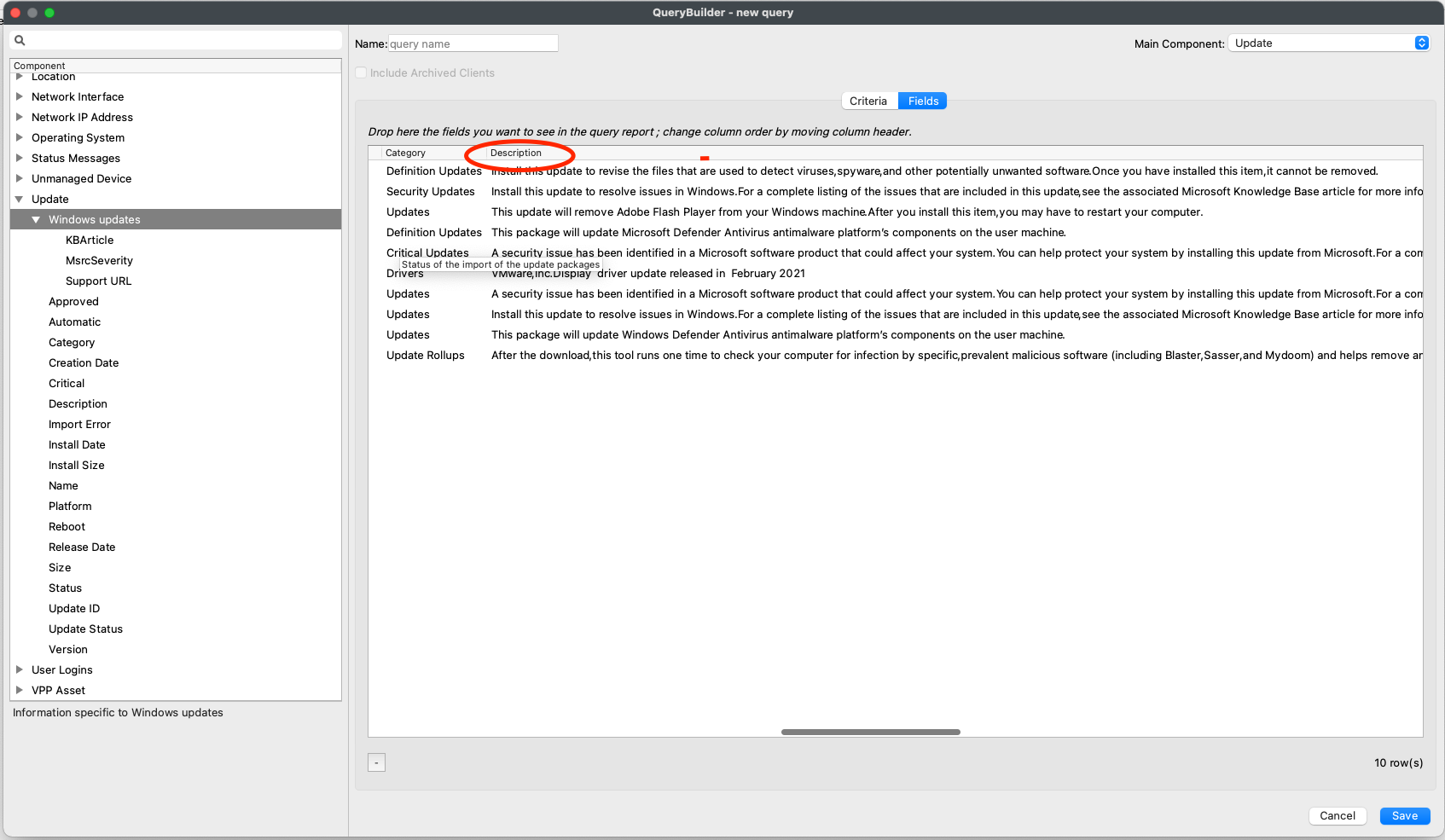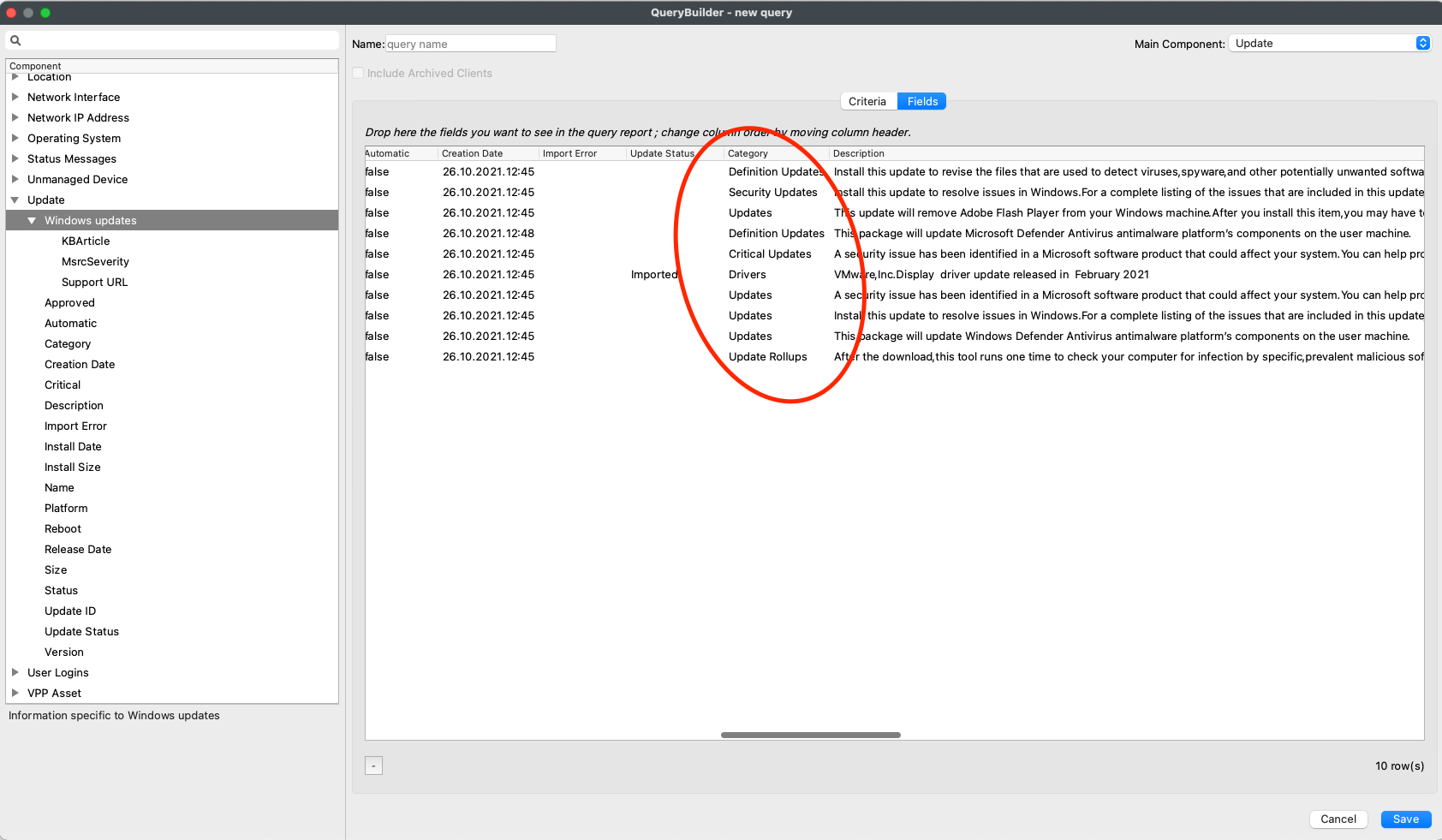 |
You'll notice in the images and script that I shortened the name of the MSU file. That's just to make it easier to read. If you keep the long name it downloads with then just be sure to copy the entire name if you do keep it long. Notice the " marks around the filename as well in case you have spaces in the path.
**Install.bat** ```vbscript REM For all script types, returning an exit code of 0 (success) means the REM script execution completed successfully. REM Add the contents of your script below: %windir%\System32\wusa.exe /quiet /norestart "c:\programdata\FileWave\Installers\windows10.0-kb5012599.msu" exit 0 ``` You may notice that this update has /norestart, but most security updates need a restart. You could go to Properties for the Fileset and have FileWave control the reboot as shown below. 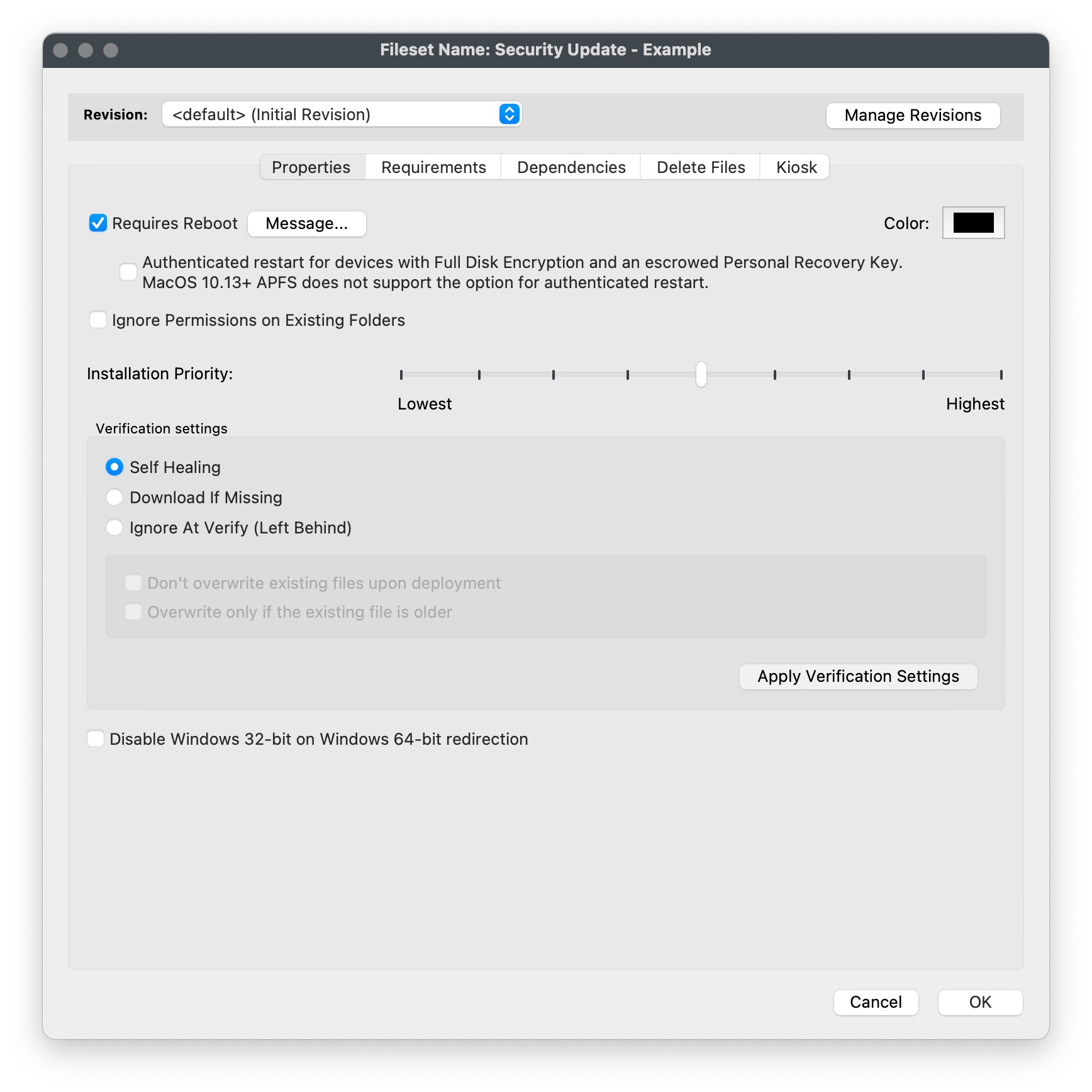It's important to note that wusa.exe is smart enough to not install an update that a device already has or an update that does not really apply to a device. You shouldn't have to worry about if someone already patched their machine. If you want to be a bit fancier you could make a Requirements script that would check if an update is installed and then exit if it is there.
Once an update is installed you would need the inventory to update for a client to see that the update is installed in the Software Updates section of the admin console. You can either wait for the verification to normally happen (once every 24 hours, or on restart) or send an explicit Verify command. That should be all you need to do. Repeat this process for any MSU file that you need to deploy via FileWave. ## Related Content - [Windows Software Update Reporting](https://kb.filewave.com/books/software-updates-windows/page/windows-software-update-reporting "Windows Software Update Reporting") - [Fileset Creation and Deployment](https://kb.filewave.com/books/evaluation-guide/page/fileset-creation-and-deployment "Fileset Creation and Deployment") ## Digging Deeper More information on wusa.exe is here: [https://support.microsoft.com/en-us/topic/description-of-the-windows-update-standalone-installer-in-windows-799ba3df-ec7e-b05e-ee13-1cdae8f23b19](https://support.microsoft.com/en-us/topic/description-of-the-windows-update-standalone-installer-in-windows-799ba3df-ec7e-b05e-ee13-1cdae8f23b19) When you are testing it may be difficult to repeat your testing once an update installs, but wusa has an /uninstall switch as well that can save you time. Below is an example that would remove a patch. Another alternative is to use a Virtual Machine for testing and use snapshots to be able to install and then roll back to before the update was installed. ```vbscript wusa /uninstall /kb: KB5000802 /quiet /promptrestart ``` For troubleshooting to view the Windows Update Standalone Installer event log on a client device, follow these steps: 1. Click Start, type event viewer in the **Start Search** box, and then click **Event Viewer** in the Programs list. 2. In Event Viewer, expand **Windows Logs**, and then click **Setup**. 3. Setup events appear in the middle pane. 4. In the **Actions** pane, click **Filter Current Log**. 5. In the **Event sources** list, click to select the **WUSA** check box, and then click **OK**. # Automated Windows OS Updates Policy ## What There may be Windows OS updates that you want to simply apply without needing to create a Fileset or manage in FileWave. This new option will allow you to set it and forget it. FileWave 16.2.0 introduces a new concept to simplify Windows OS patching. ## When/Why If you have a very lightly managed environment or have certain updates that you always want to have applied then this option may be for you. ## How When you create a new Fileset in FileWave 16.2.0 or higher you can pick General -> Policy to create a FileWave Policy. In the below image you can see the options for the Windows Software Updates component of FileWave Policy. This type of Fileset can also be used for [customizing the Kiosk appearance](https://kb.filewave.com/books/kiosk/page/setting-the-primary-colour-name-and-logo-in-kioskapp-portal-160 "Setting the Primary Colour, Name and Logo in Kiosk/App Portal (16.0+)"), [Geofencing for Android](https://kb.filewave.com/books/android/page/geofencing "Geofencing"), and [Blocker Scripts](https://kb.filewave.com/link/506#bkmrk-policy). You will give the Policy a name on the General section and then go to the Windows Software Updates section and set the rules. Anything that matches will apply. - **Update Name** - Here you may want to use "Contains" as the rule if you are looking for a certain name but you can leave this blank if you are just setting the type of update with the switches. Note that the text is localized so if in your language it would be a different word then use what you usually see in Windows Updates. - **Critical** - Any update marked by Microsoft as Critical. If enabled then they will be considered. - **Reboot** - Any update marked as requiring a reboot. If you do not want reboot updates to be pushed automatically then do not enable this, but know that many Microsoft updates require a reboot. - **Category** - Enabled Categories will be considered. When setting this up consider the example below. For any update where "Cumulative" is in the name, the update MUST be Critical, the update may or may not reboot, and the update is ONLY an update of the two categories; Critical updates OR Security updates. [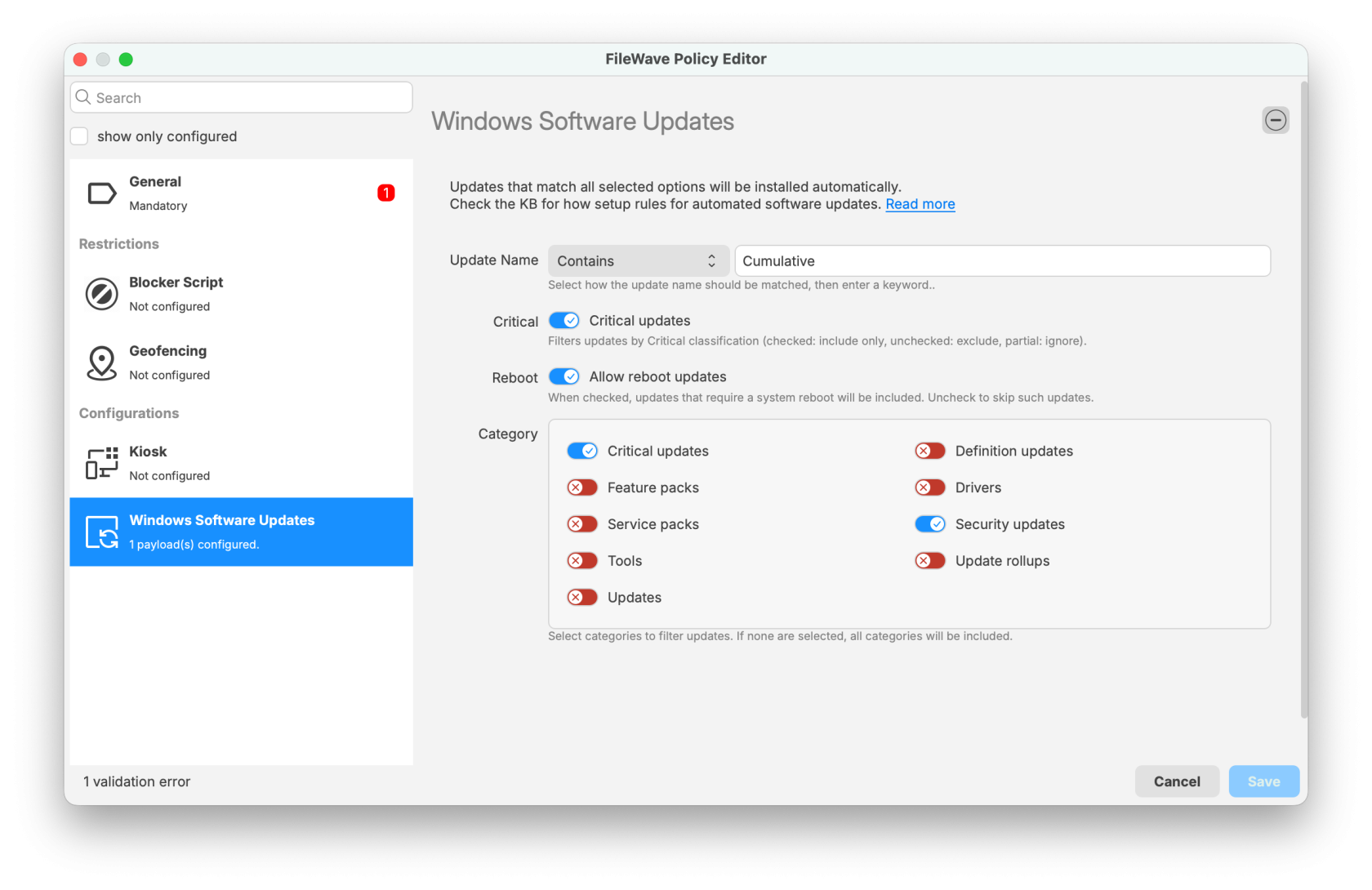](https://kb.filewave.com/uploads/images/gallery/2025-09/ildyZfsQenAUK0wA-filewave-admin-2025-09-23-09-21-11.png) You can also deploy updates with finer control by following the guidance in [Best Practice Guide: Software Update Deployment (16.0+)](https://kb.filewave.com/books/top-tips/page/best-practice-guide-software-update-deployment-160 "Best Practice Guide: Software Update Deployment (16.0+)") ## Related Content - [Description of the standard terminology that is used to describe Microsoft software updates](https://learn.microsoft.com/en-us/troubleshoot/windows-client/installing-updates-features-roles/standard-terminology-software-updates) - [Windows Patching Automations for Fileset creation](https://kb.filewave.com/books/filewave-central-anywhere/page/os-software-updates-automation-rules "Windows Patching Automations for Fileset creation") # Understanding and Utilizing the Windows Update Build Revision (UBR) Number ## What The Update Build Revision (UBR) number is a unique identifier for individual updates in Windows 10 and Windows 11 operating systems. It allows IT administrators to track, monitor, and ensure that their devices are up-to-date with the latest security patches, bug fixes, and feature improvements. The UBR number is not reported by FileWave by default; however, you can use Custom Fields in FileWave to collect and report on this information. ## When/Why Keeping devices updated is crucial for maintaining security, stability, and optimal performance. By monitoring UBR numbers, IT administrators can: 1. Identify devices that are not up-to-date with the latest updates. 2. Plan and execute update deployments effectively. 3. Verify the success of update installations. 4. Maintain compliance with internal and external policies or regulations. This is particularly relevant for Education organizations, corporations, and state and local government agencies that rely on FileWave for their Unified Endpoint Management needs. ## How Using the below PowerShell code you can get the UBR from the Registry: ```powershell $ubr_version =(Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").UBR echo "$ubr_version" exit 0 ``` Using the below PowerShell code you can see how you can get both the OS version together with the UBR if that is desired: ```powershell $os_version = (Get-WmiObject -Class win32_OperatingSystem).Version $sub_build_version = (Get-ItemProperty "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion").UBR echo "$os_version.$sub_build_version" exit 0 ``` To implement this very easily simply: 1. Download the below Custom Field file: [Windows UBR.customfields.zip](https://kb.filewave.com/attachments/119) 2. Extract the zip archive 3. In FileWave Central go to Assistants → Custom Fields → Edit Custom Fields 4. Click Import and pick the file you extracted 5. Now make sure for one or both fields that you make sure to check the box to assign it to all devices so that they can report in their values. Then you can use the Custom Fields in any Query/Report/Smart Group ## Related Content - [Custom Fields](https://kb.filewave.com/books/custom-fields/page/custom-fields "Custom Fields") - [https://www.vcloudinfo.com/2020/12/how-to-decode-windows-version-numbers.html](https://www.vcloudinfo.com/2020/12/how-to-decode-windows-version-numbers.html) - [https://superuser.com/questions/1287950/how-to-find-the-build-ubr-kernel-version-of-windows-10-using-command-line-c](https://superuser.com/questions/1287950/how-to-find-the-build-ubr-kernel-version-of-windows-10-using-command-line-c) - [https://stackoverflow.com/questions/47859658/find-the-extended-ver-information-for-remote-windows-computer](https://stackoverflow.com/questions/47859658/find-the-extended-ver-information-for-remote-windows-computer)