VMware Carbon Black Cloud sensor recipe (macOS)
Description
VMware Carbon Black is a powerful endpoint protection solution that plays a critical role in an organization's cybersecurity strategy. Deploying Carbon Black via the installer package through the admin console is a strategic approach that ensures consistent, efficient, and effective endpoint security. By mastering this deployment process, organizations can enhance their cybersecurity posture, mitigate threats proactively, and protect their digital assets in an increasingly dangerous digital landscape.
Ingredients
-
FileWave Central
-
VMwave Carbon Black Cloud installer and doc
- VMware CBC license code
- VMware CBC uninstaller code
- System Extension mobile configuration
- Network Extension Web Content Filter mobile configuration
- TCC Privacy Policy mobile configuration
| macOS Kext Approval |
 |
| macOS TCC Profile |
 |
| macOS System Ext |
 |
| VMware CBC Fileset |
 |
Directions
Please note this recipe includes Carbon Black Cloud sensor (CB Defense) 3.7.4.53. This version is supported on MacOS 11.0 and newer.
CreatingDownloading and extracting the VMwareMDM Carbonprofiles Blackand Cloud Filesetinstallers
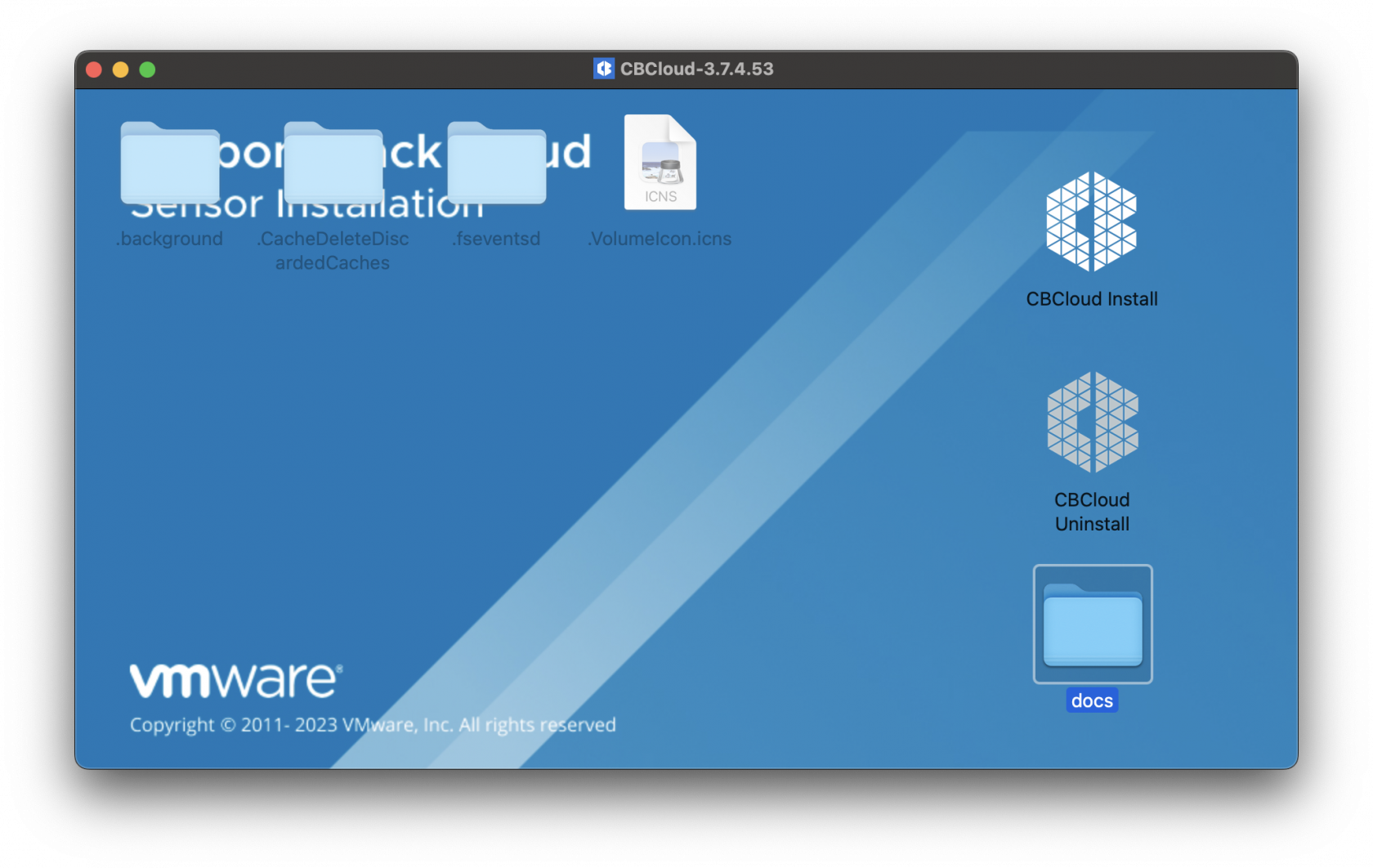
You will first want to grab and download your VMware installations and profiles. The .dmg will need to be mounted first and then extract the necessary components from this file.
Once the .dmg has been mounted you will see the contents listed. Below is the CBCloud Install.pkg and doc folder containing the required MDM profiles.
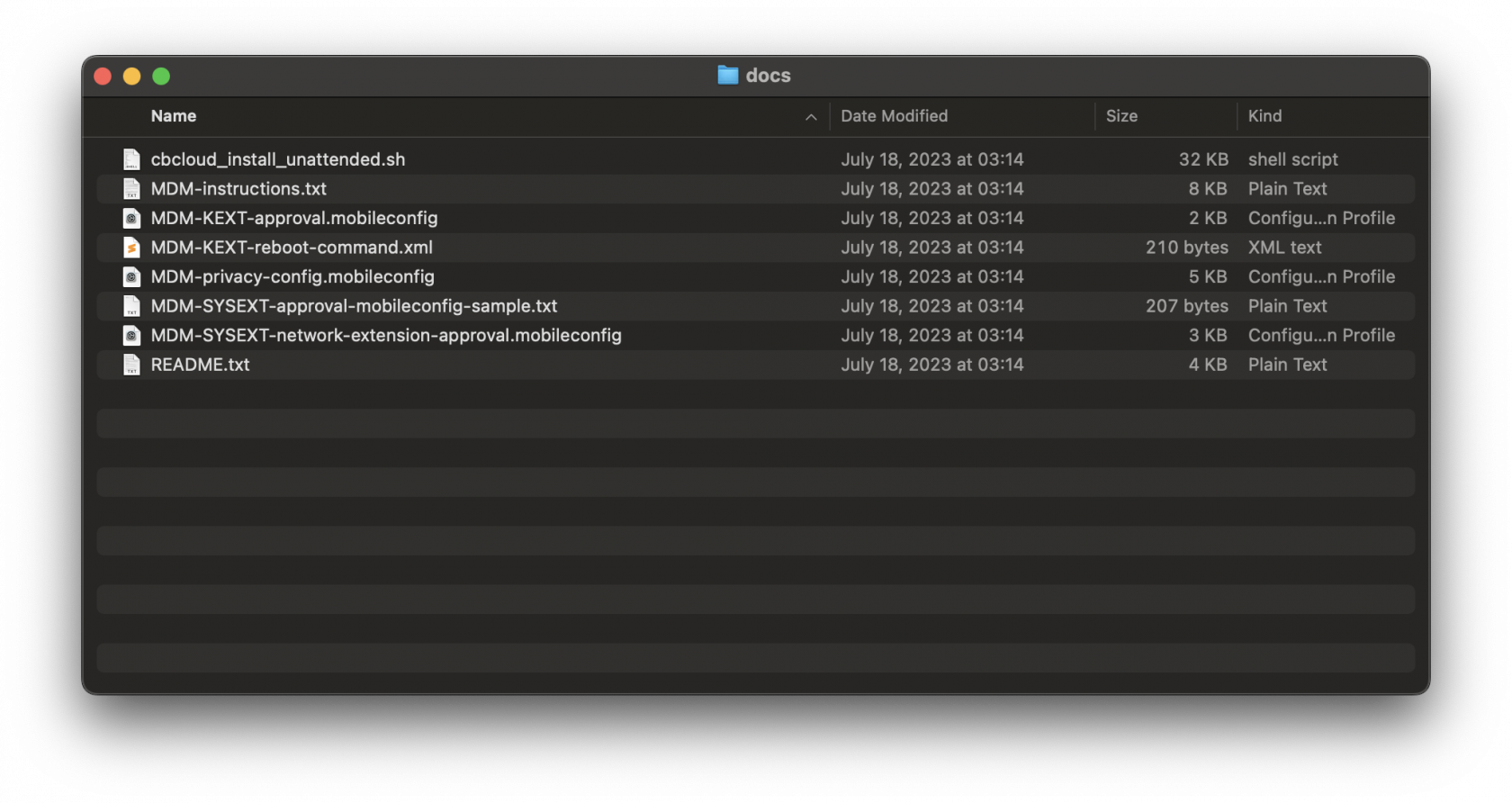
Listed MDM profiles and unattended script for Fileset deployed are found in the docs folder within the mounted .dmg.
Extract the three MDM profiles. These MDM profiles will be uploaded into FileWave Central. Below are the configuration for the three MDM profiles:
MDM Profiles Configurations
If you do not have the VMware Carbon Black Cloud .dmg, you may create the Profiles with the following.
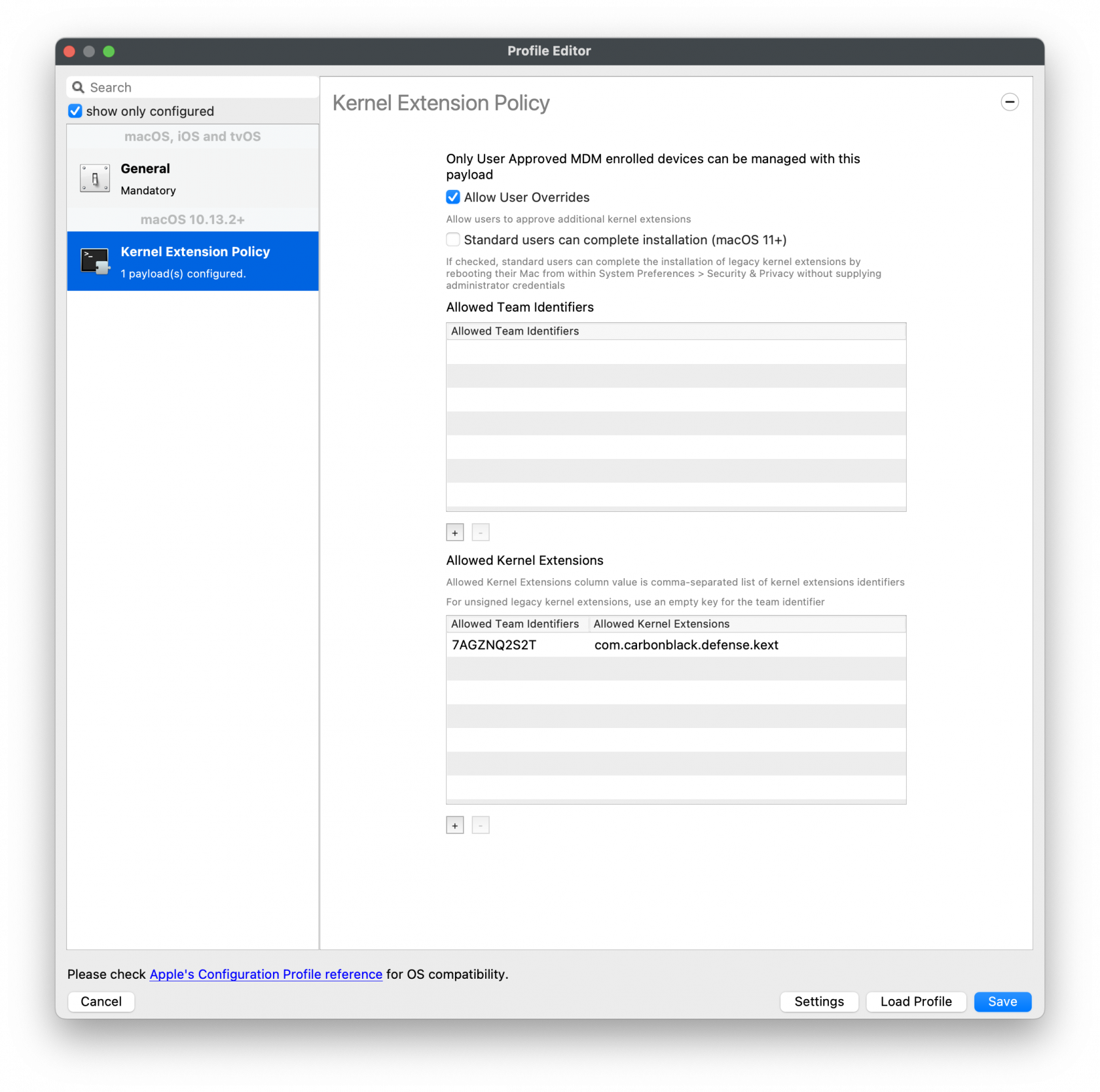
Kernel Extension Policy
For the Kernel Approval profile, please enter in the TeamID and BundleID:
Apple Team ID: 7AGZNQ2S2T
KEXT Bundle ID: com.carbonblack.defense.kext
Kernel Extension Policy: The recommended way to deliver this configuration is through
the provided MDM-KEXT-reboot-command.xml. This XML file should be uploaded as a Custom Command and sent to endpoints after KEXT install. Note that this will reboot the target machine without warning, and that this distribution method is a temporary workflow until MDM providers update their reboot protocols to support RebuildKernelCache.
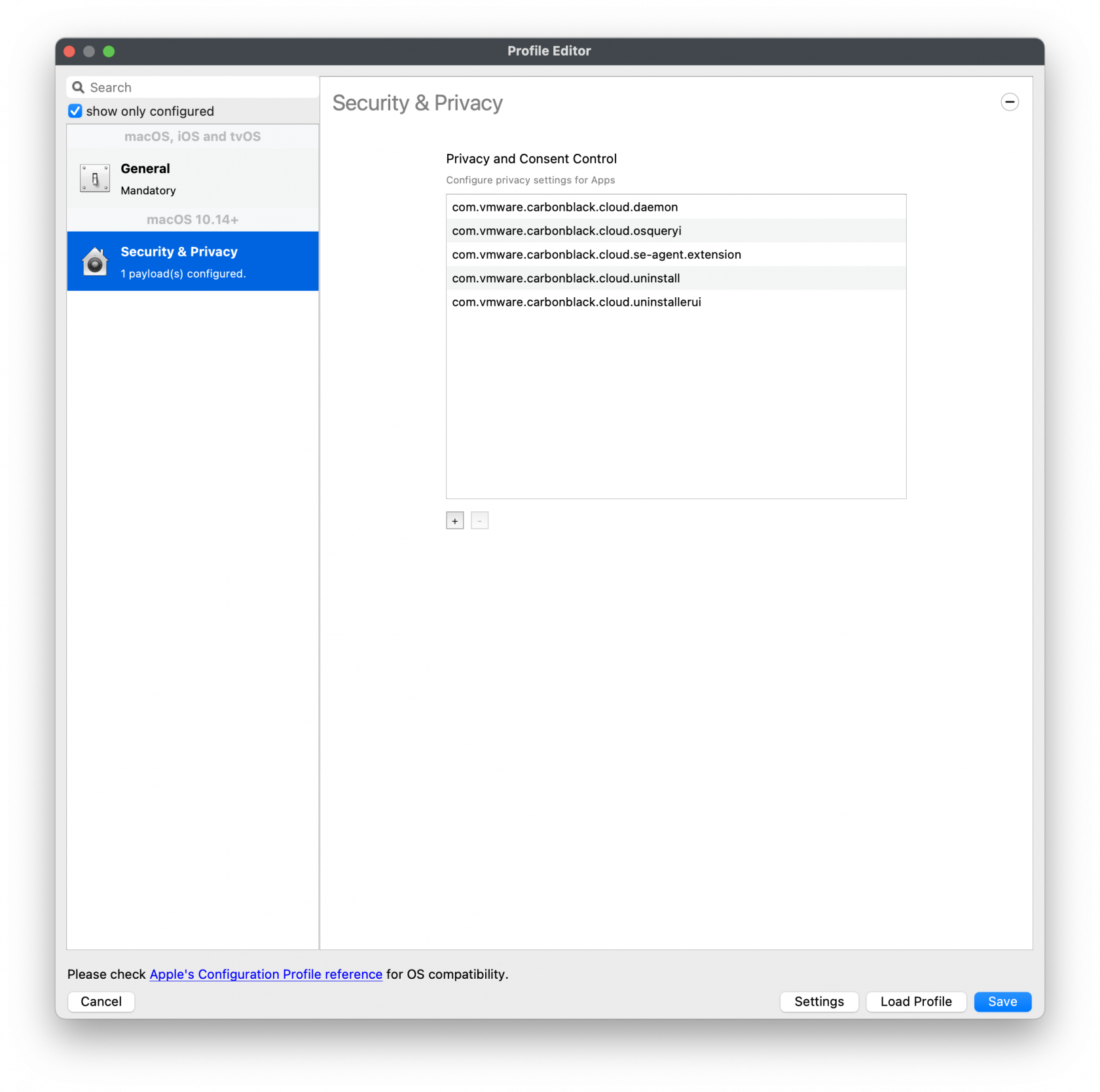
Privacy and Consent Control (TCC) Policy
The following will need to be entered for each of the BundleIDs along with Code Requirements and Services to set.
TCC metadata
The fields should be completed exactly as follows. Please copy and paste for accuracy.
1]
Identifier: com.vmware.carbonblack.cloud.daemon
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
2]
Identifier: com.vmware.carbonblack.cloud.se-agent.extension
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
3)
Identifier: com.vmware.carbonblack.cloud.osqueryi
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.osqueryi" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
4)
Identifier: com.vmware.carbonblack.cloud.uninstall
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.uninstall" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
5)
Identifier: com.vmware.carbonblack.cloud.uninstallerui
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.uninstallerui" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
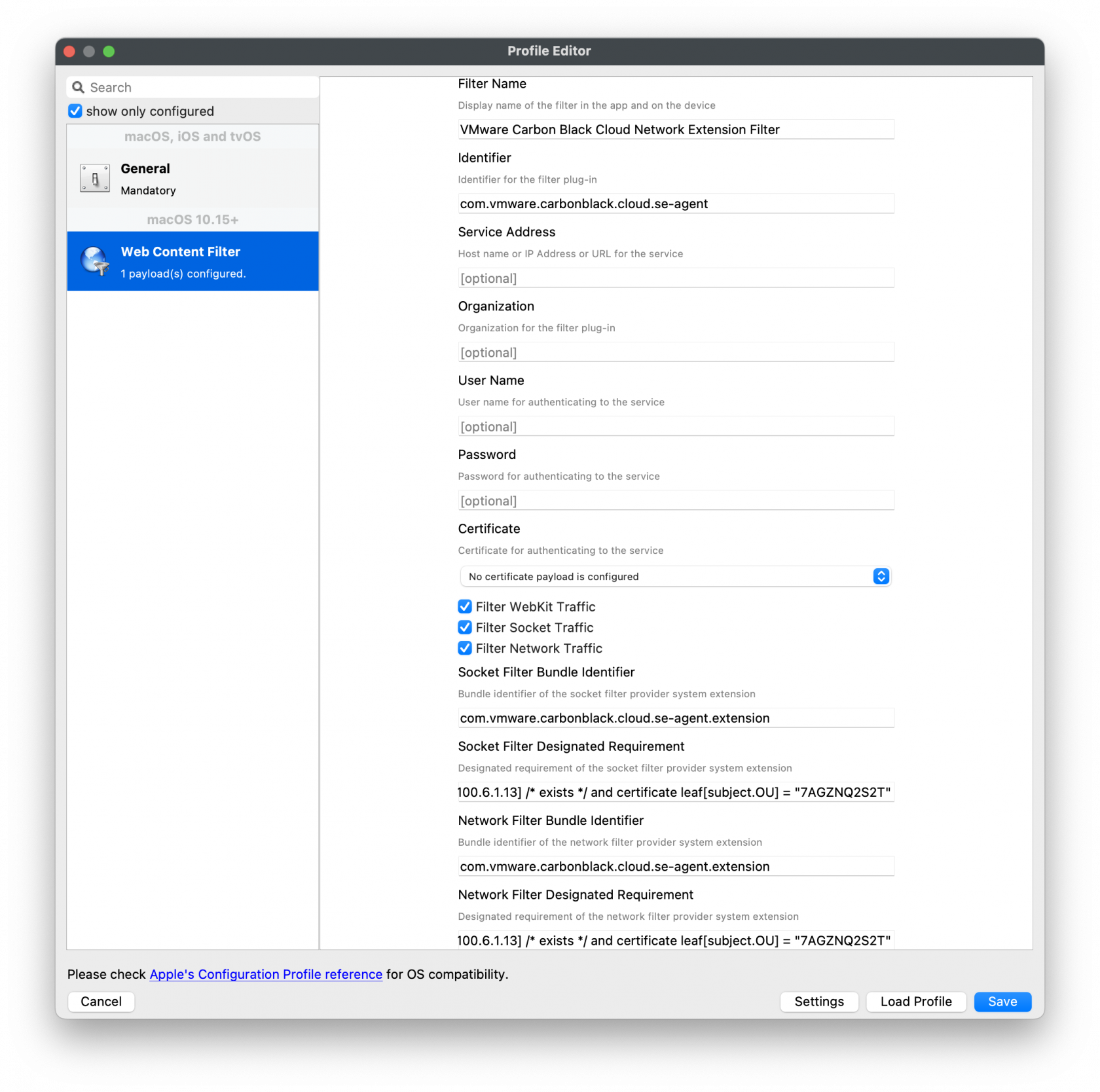
Web Content Filter Policy
The following will need to be entered to create the web content filter manually.
Web Content Filter Policy
The fields should be completed exactly as follows. Please copy and paste for accuracy.
In the General payload:
Payload Scope should be set to: System
In the Web Content Filter payload:
Filter Type should be set to: Plug-In
Plug-In Bundle ID: com.vmware.carbonblack.cloud.se-agent
Check Enable Socket Filtering
Filter Data Provider System Extension Bundle ID (macOS): com.vmware.carbonblack.cloud.se-agent.extension
Filter Data Provider Designated Requirement (macOS): identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Check Enable Packet Filtering (macOS)
Filter Packet Provider System Extension Bundle ID (macOS): com.vmware.carbonblack.cloud.se-agent.extension
Filter Packet Provider Designated Requirement (macOS): identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"