VMware Carbon Black Cloud sensor recipe (macOS)
Description
VMware Carbon Black is a powerful endpoint protection solution that plays a critical role in an organization's cybersecurity strategy. Deploying Carbon Black via the installer package through the admin console is a strategic approach that ensures consistent, efficient, and effective endpoint security. By mastering this deployment process, organizations can enhance their cybersecurity posture, mitigate threats proactively, and protect their digital assets in an increasingly dangerous digital landscape.
This guide will help you create a Fileset and deploy the application along with the required profiles.
Ingredients
-
FileWave Central
-
VMware Carbon Black Cloud dmg
- VMware CBC license code
- VMware CBC uninstaller code
- System Extension mobile configuration
- Network Extension Web Content Filter mobile configuration
- TCC Privacy Policy mobile configuration
Downloads
VMware CBCloud Profiles.zip
VMware Carbon Black Cloud.fileset.zip
Directions
Please note this recipe includes Carbon Black Cloud sensor (CB Defense) version 3.7.4.53. This version is supported on MacOS 11.0 and newer.
Downloading and extracting the MDM profiles and installers
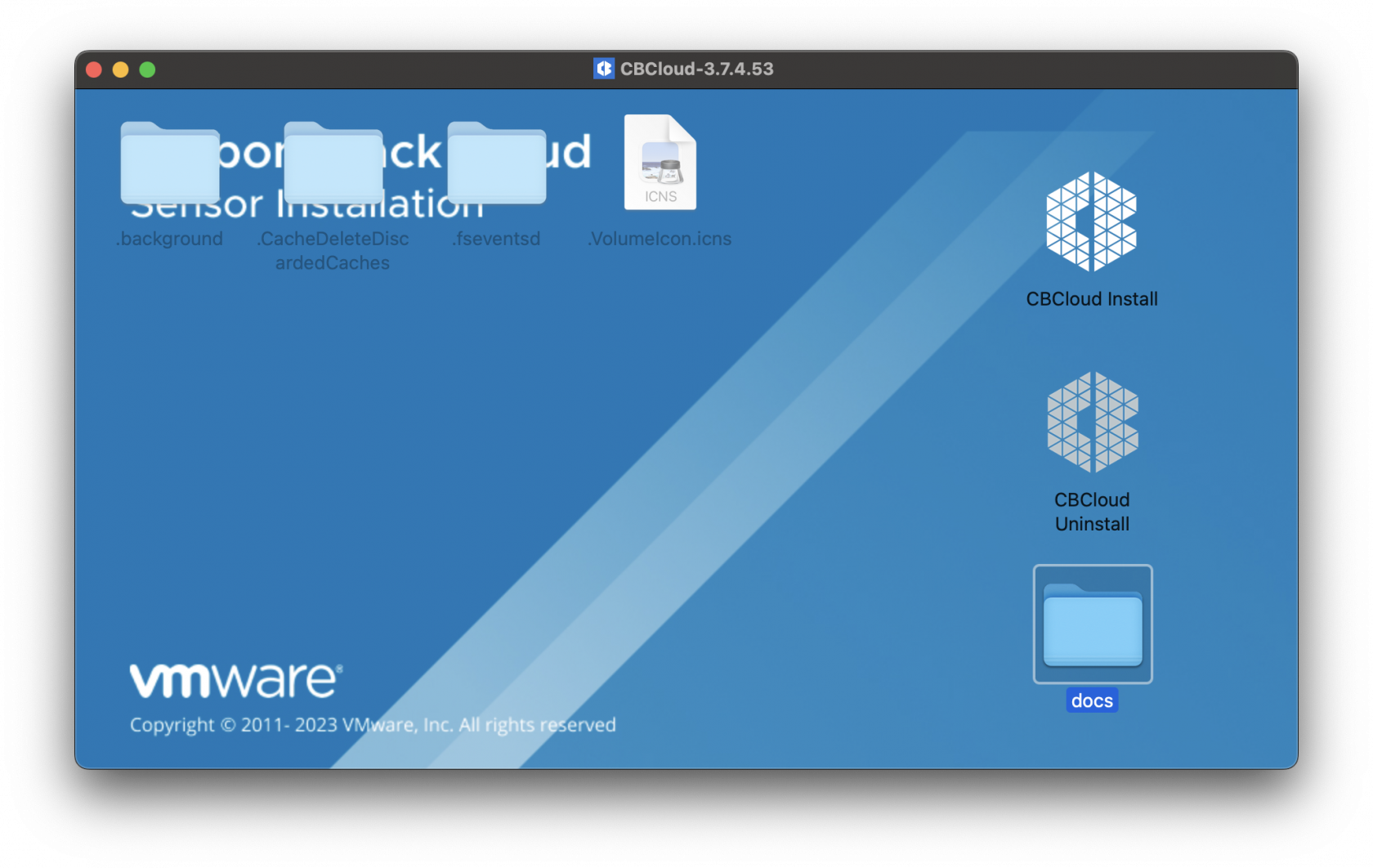
You will first want to grab and download your VMware installations and profiles. The .dmg will need to be mounted first and then extract the necessary components from this file.
Once the .dmg has been mounted you will see the contents listed. Below is the CBCloud Install.pkg and doc folder containing the required MDM profiles.
The required MDM profiles and unattended script for the Fileset deployed are found in the docs folder within the mounted .dmg.
Extract the MDM profiles. These MDM profiles will be uploaded into FileWave Central. Below are the configurations for the three MDM profiles:
MDM Profiles Configurations
If you do not have the VMware Carbon Black Cloud .dmg, you may create the Profiles with the following.
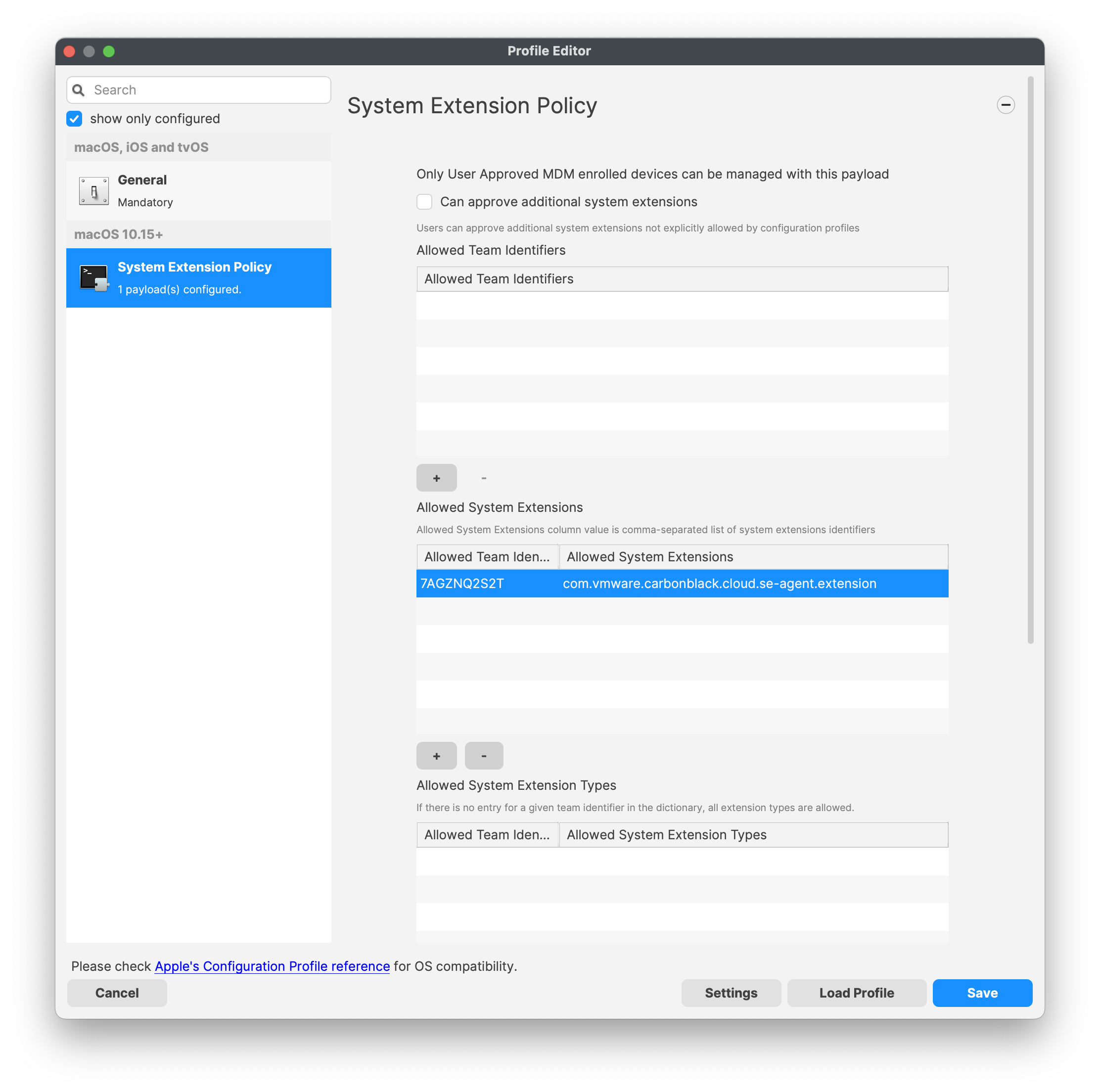
VMware CCB macOS version 3.8+ introduces Approving the System Extension
Approve System Extension
For the Allowed System Extension, please enter in the following:
System Extension Policy
Specify the Apple Team ID and System Extension bundle Identifier in your Allowed System Extension configuration profile:
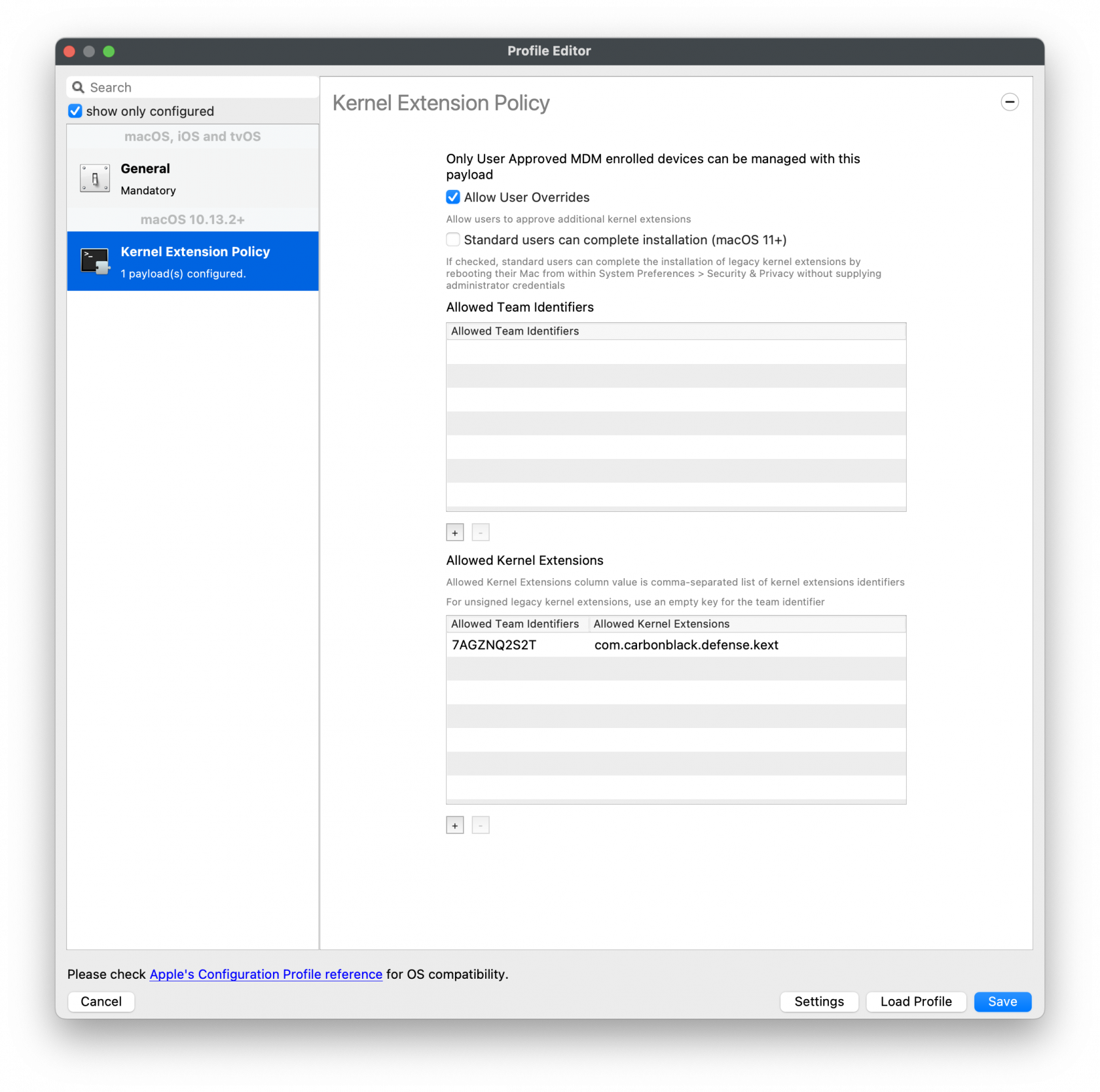
Kernel Extension Policy
For the Kernel Approval profile, please enter in the TeamID and BundleID:
Apple Team ID: 7AGZNQ2S2T
KEXT Bundle ID: com.carbonblack.defense.kext
Kernel Extension Policy: The recommended way to deliver this configuration is through
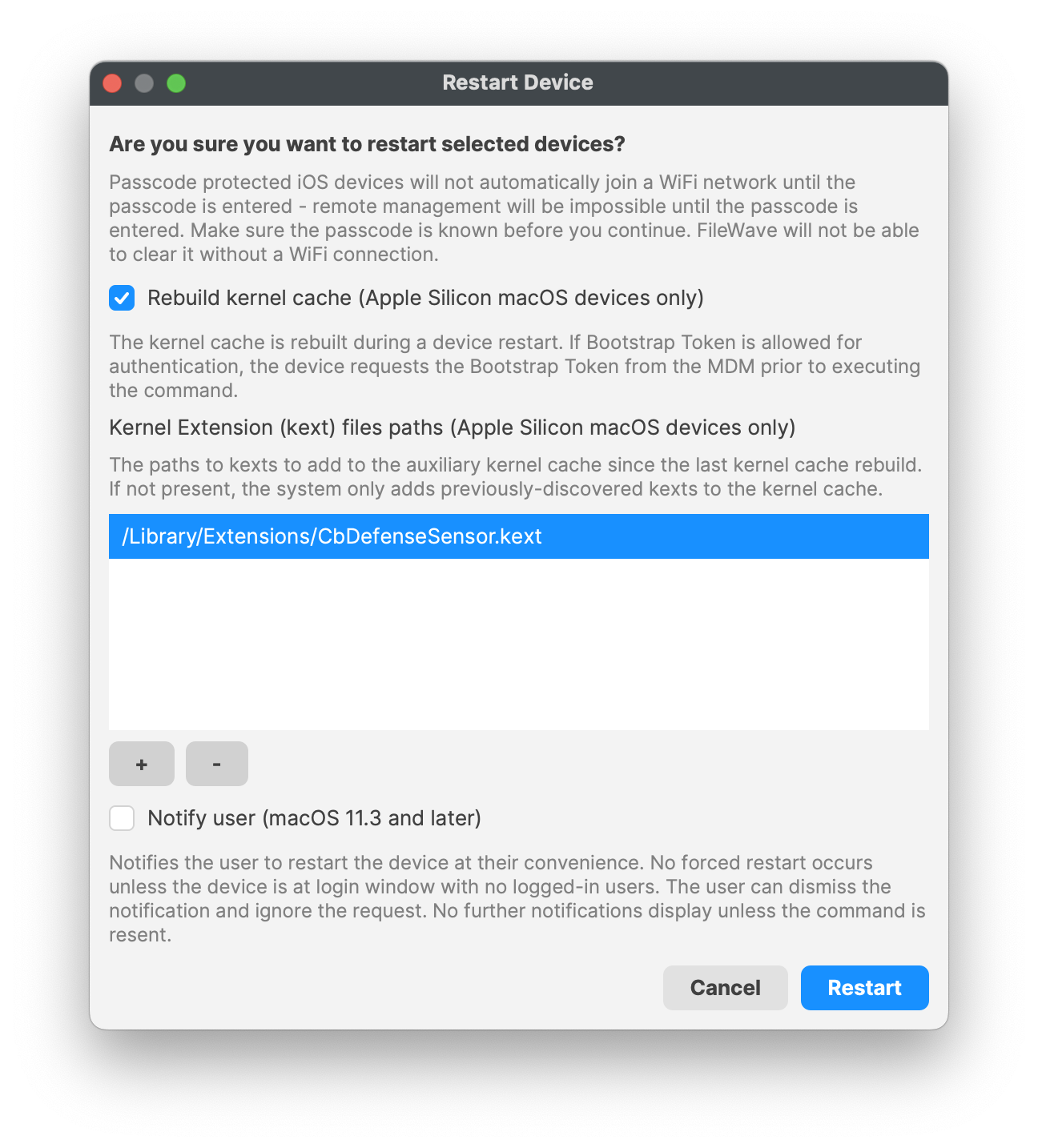
the provided MDM-KEXT-reboot-command.xml. FileWave has the Rebuild Kernel Cache command by highlighting the MDM client, right-clicking Restart (Supported MDM devices), checking the box for Rebuild Kernel Cache, and entering in the Kernel file path:
/Library/Extensions/CbDefenceSensor.kext
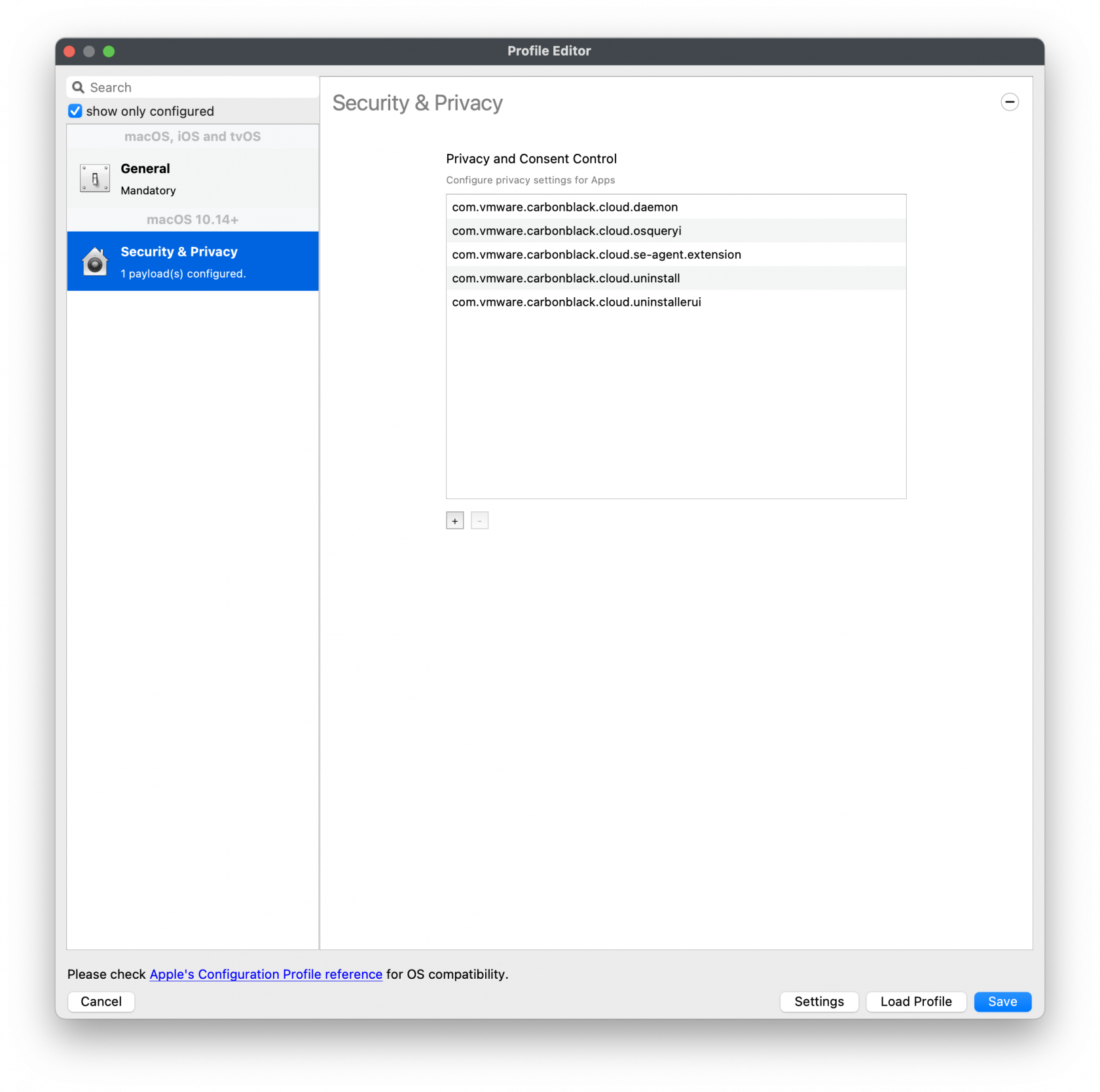
Privacy and Consent Control (TCC) Policy
The following will need to be entered for each of the BundleIDs along with Code Requirements and Services to set.
TCC metadata
The fields should be completed exactly as follows. Please copy and paste for accuracy.
1]
Identifier: com.vmware.carbonblack.cloud.daemon
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.daemon" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
2]
Identifier: com.vmware.carbonblack.cloud.se-agent.extension
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
3]
Identifier: com.vmware.carbonblack.cloud.osqueryi
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.osqueryi" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
4]
Identifier: com.vmware.carbonblack.cloud.uninstall
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.uninstall" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
5]
Identifier: com.vmware.carbonblack.cloud.uninstallerui
Identifier Type should be set to: Bundle ID
Code Requirement: identifier "com.vmware.carbonblack.cloud.uninstallerui" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
App or Service should be set to: SystemPolicyAllFiles
Access should be set to: Allow
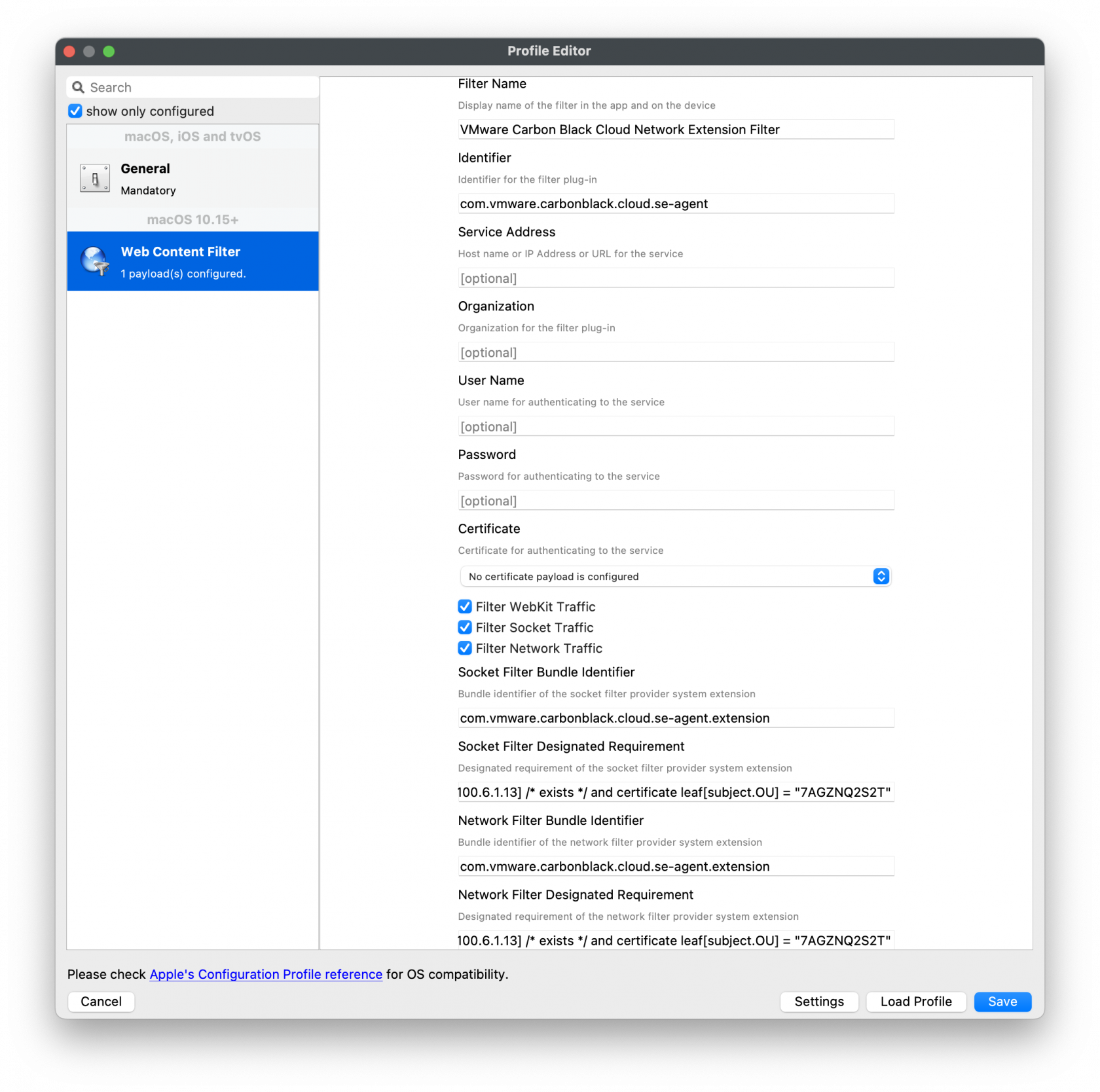
Web Content Filter Policy
The following will need to be entered to create the web content filter manually.
Web Content Filter Policy
The fields should be completed exactly as follows. Please copy and paste for accuracy.
In the General payload:
Payload Scope should be set to: System
In the Web Content Filter payload:
Filter Type: Plug-In
Plug-In Bundle ID: com.vmware.carbonblack.cloud.se-agent
Check Enable Socket Filtering
Filter Data Provider System Extension Bundle ID (macOS): com.vmware.carbonblack.cloud.se-agent.extension
Filter Data Provider Designated Requirement (macOS): identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Check Enable Packet Filtering (macOS)
Filter Packet Provider System Extension Bundle ID (macOS): com.vmware.carbonblack.cloud.se-agent.extension
Filter Packet Provider Designated Requirement (macOS): identifier "com.vmware.carbonblack.cloud.se-agent.extension" and anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] /* exists */ and certificate leaf[field.1.2.840.113635.100.6.1.13] /* exists */ and certificate leaf[subject.OU] = "7AGZNQ2S2T"
Creating the VMware Carbon Black Cloud Fileset
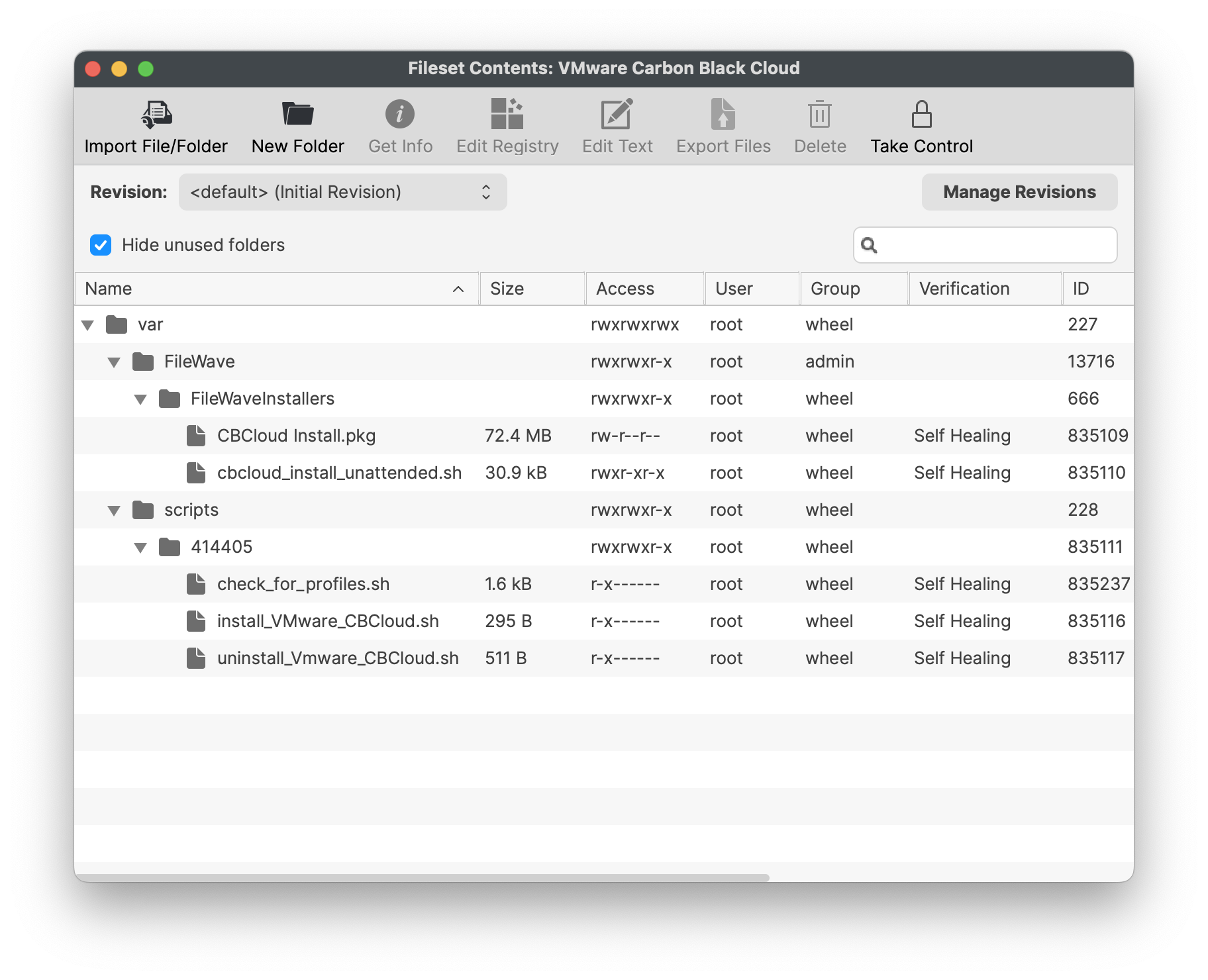
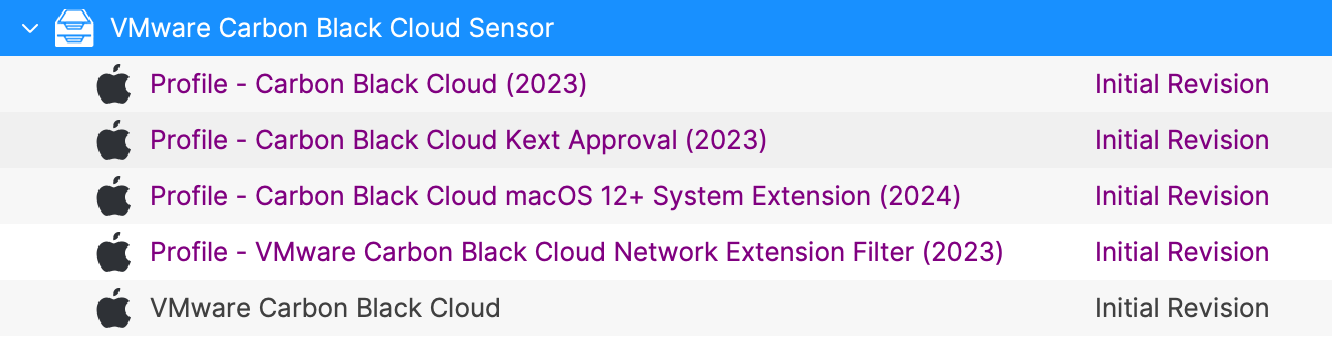
You may download and upload the VMware Carbon Black Cloud Fileset into your FileWave Admin. You should see four items listed in the Fileset Contents:
- CBCloud Install.pkg
- check_for_profiles.sh script
- cbcloud_install_unattended.sh script
- install_VMware_CBCloud.sh script
- uninstall_VMware_CBCloud.sh script
Verification Settings: VMware CBCloud client will get updates from the CBCloud server. If your organization allows, be sure to change the verification settings from 'Self-Healing' to 'Ignore at Verify' for the Fileset.
VMware CBCloud install script
You will need to modify and add your company code to the install_VMware_CBCloud.sh script.
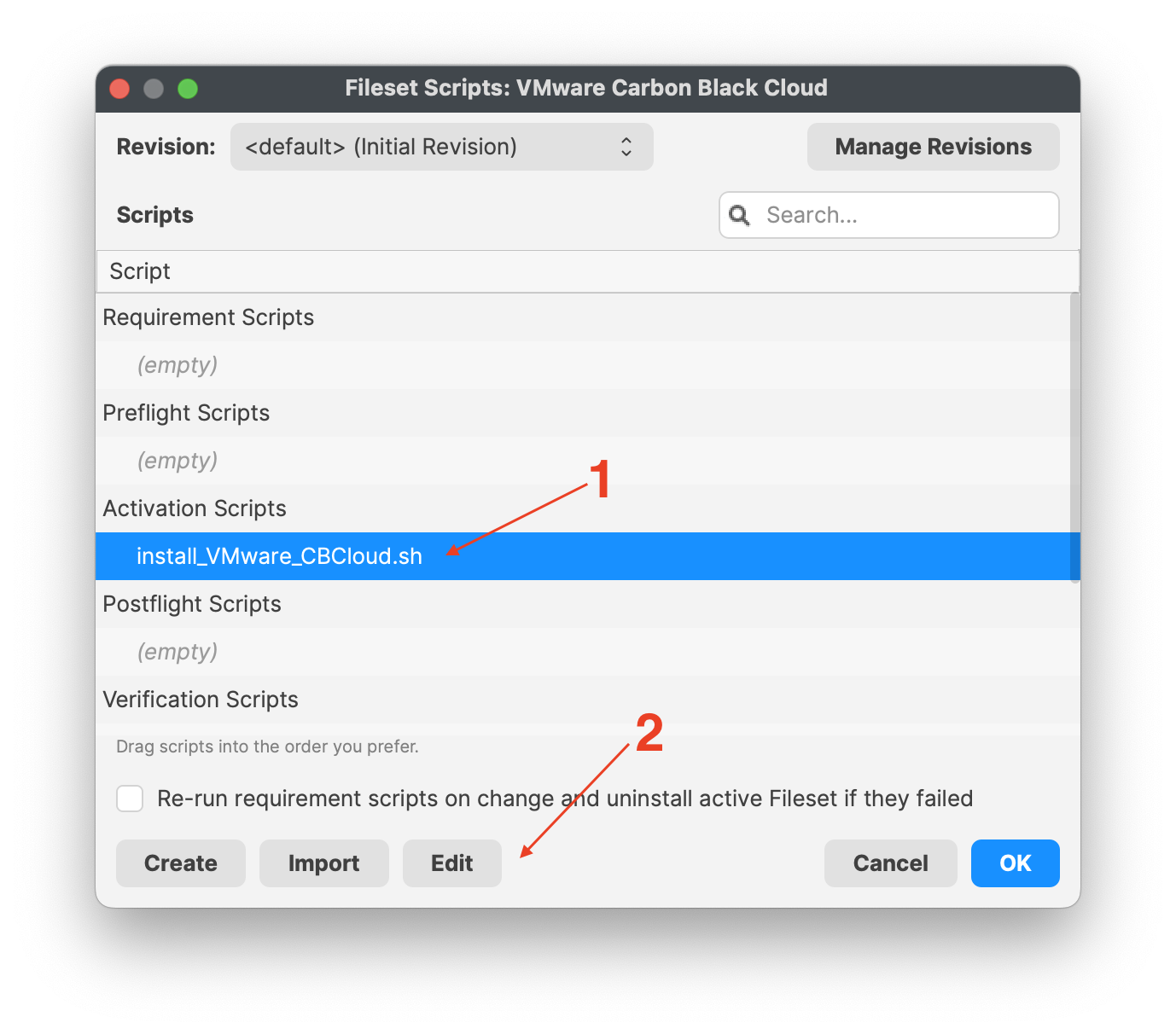
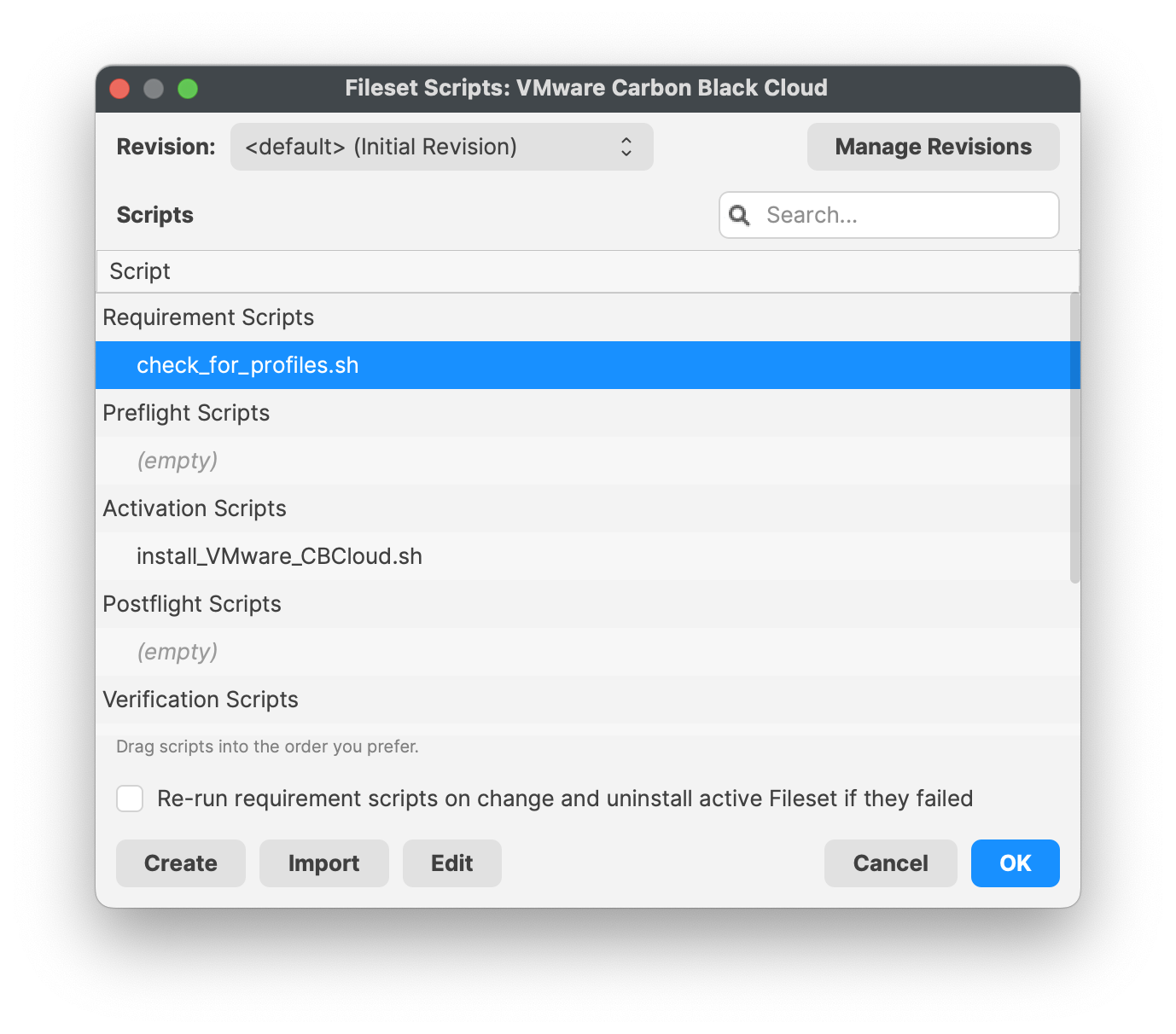
- Highlight the Fileset and click on Scripts (FW Central menu)
- Highlight Activation Scripts, install_VMware_CBCloud.sh
- Click on Edit to open the script
- Enter your company code, i.e. #######
- Click OK to save
- Click OK to save your changes
|
|
|
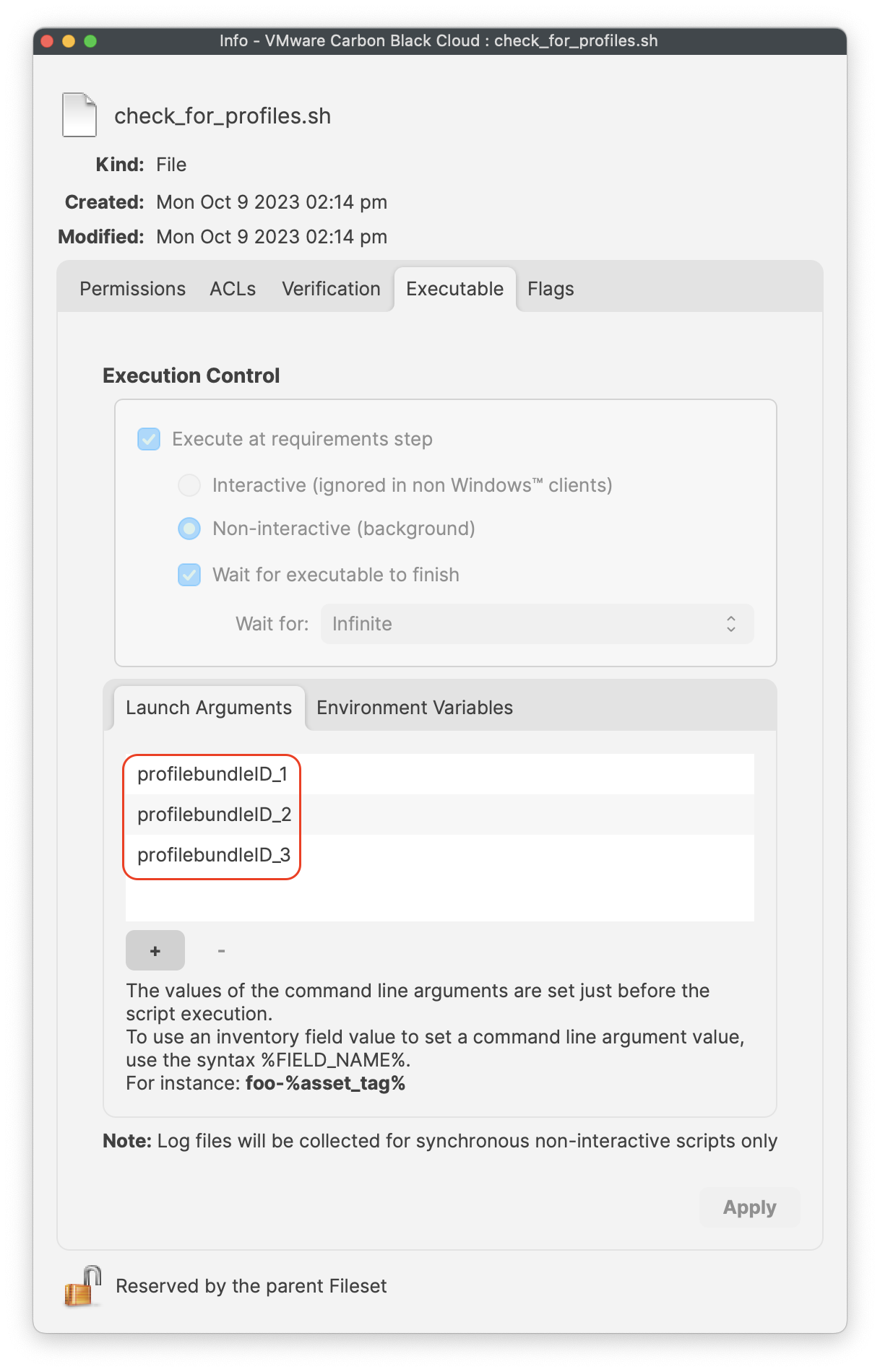
Check for Profiles requirement script
You will need to modify and add your profile bundle IDs to the requirement script.
- Highlight the Fileset and on Scripts (FW Central menu)
- Highlight Requirement Scripts, check_for_profiles.sh
- Right-click and select properties
- Select and click on the Launch Arguments tab
- Enter in your three profile bundle IDs
- Click 'Apply' to save your changes
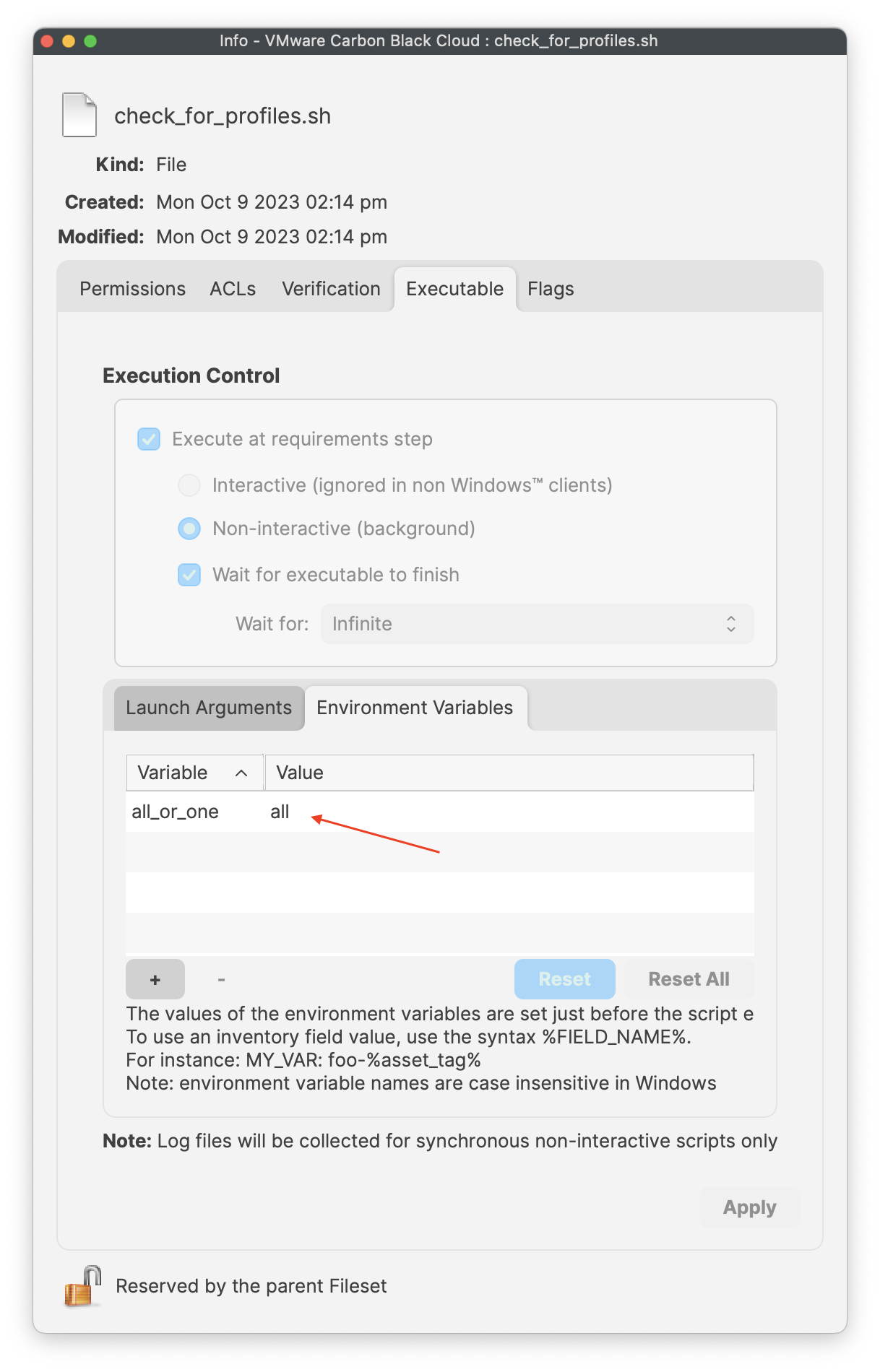
- Select and click on the Environment Variables tab
- Confirm the all_or_one variables string is set to 'all'
- Click 'Apply' to save your changes, if not saved
- Close the script properties window
- Click OK to save your changes to the requirement script
|
|
 |
 |
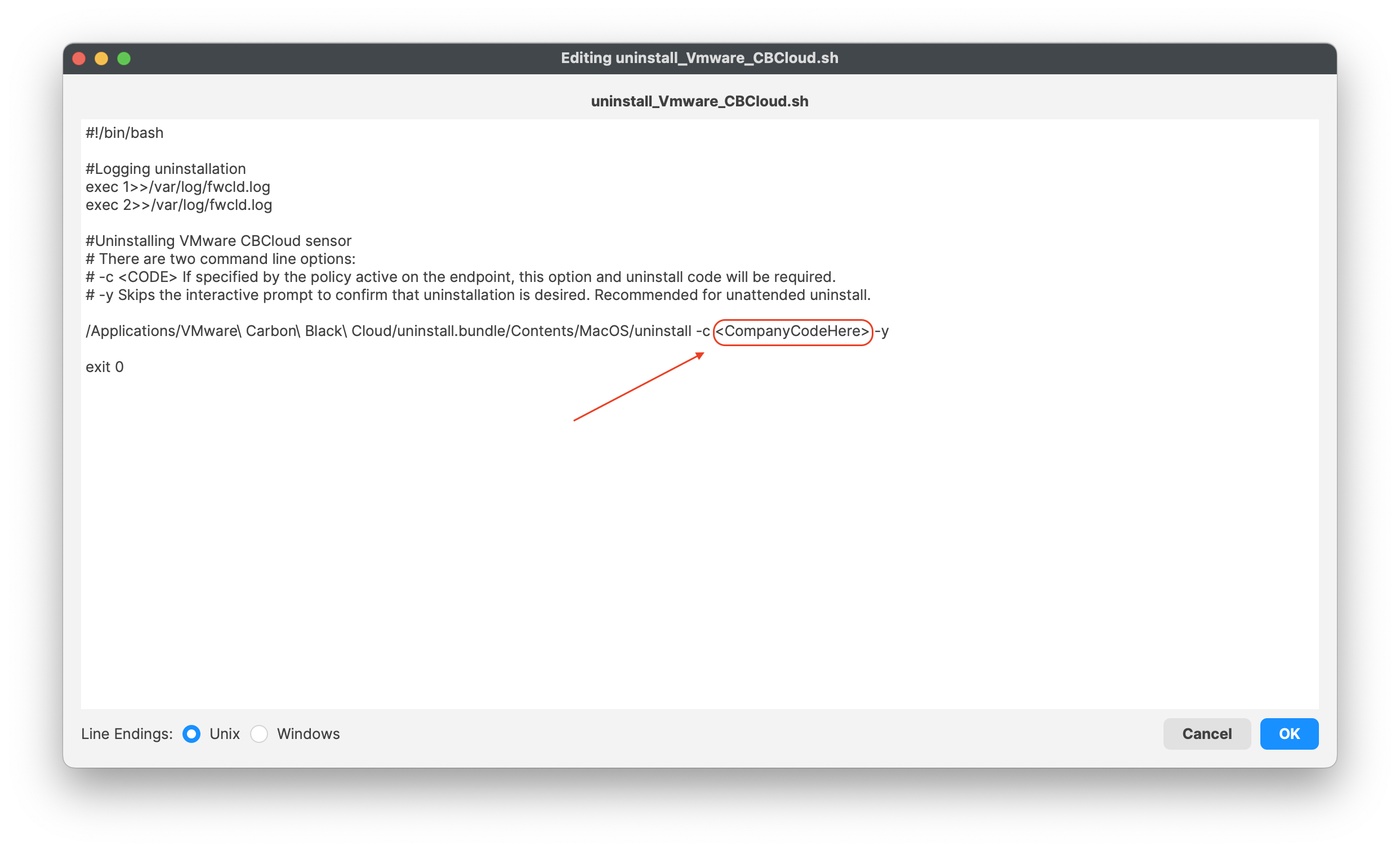
Vmware uninstall script
This is optional and not required!
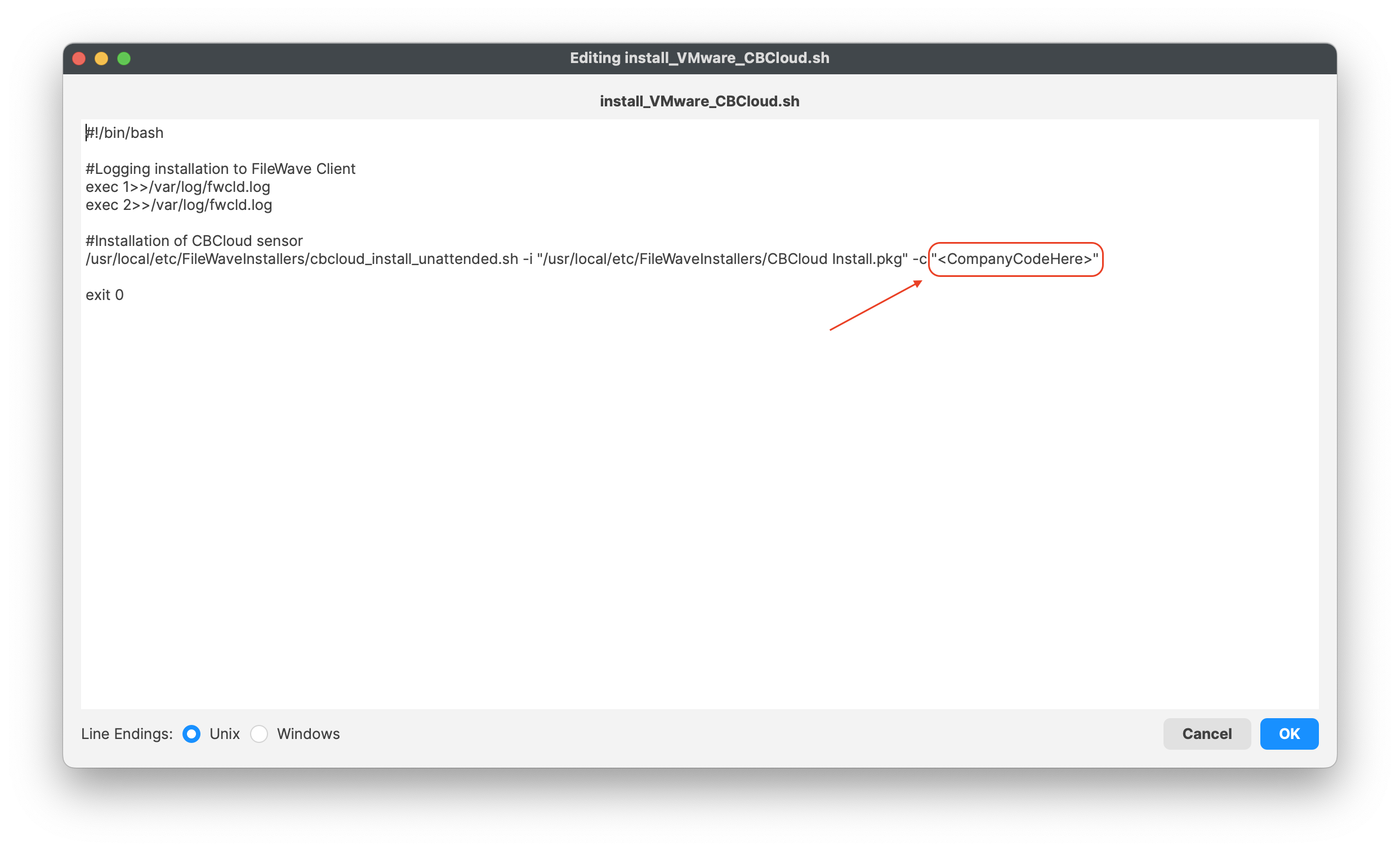
If you have a company code to allow uninstallation of the VMware Carbon sensor, you may enter your code into the script under:
- Line 12 <CompanyCodeHere>; replace with your code and remove the <>
uninstall_Vmware_CBCloud.sh
#!/bin/bash
#Logging uninstallation
exec 1>>/var/log/fwcld.log
exec 2>>/var/log/fwcld.log
#Uninstalling VMware CBCloud sensor
# There are two command line options:
# -c <CODE> If specified by the policy active on the endpoint, this option and uninstall code will be required.
# -y Skips the interactive prompt to confirm that uninstallation is desired. Recommended for unattended uninstall.
/Applications/VMware\ Carbon\ Black\ Cloud/uninstall.bundle/Contents/MacOS/uninstall -c <CompanyCodeHere> -y
exit 0
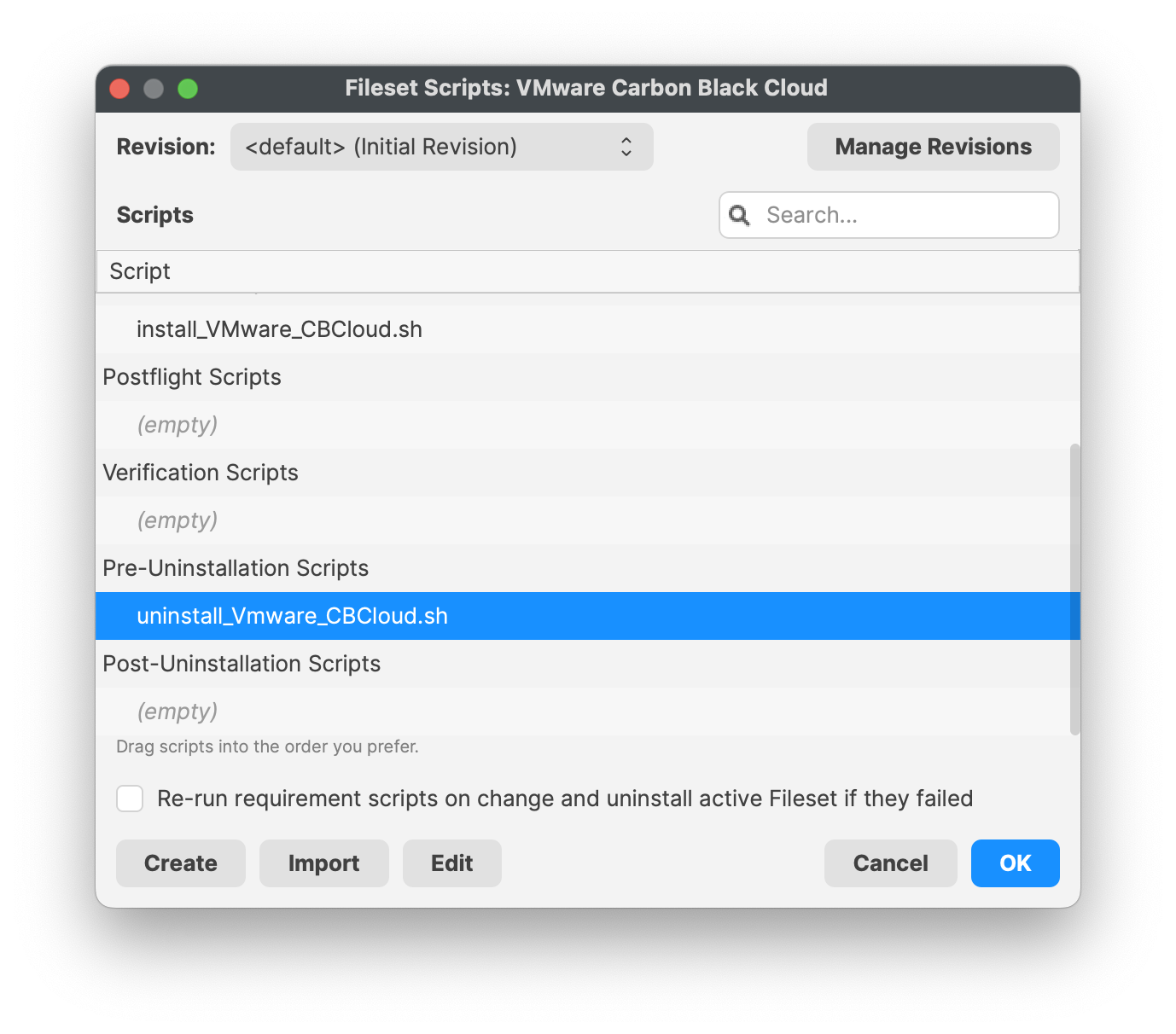
To make the changes in the Fileset:
- Highlight the Fileset and click on Scripts (FW Central menu)
- Highlight Pre-Uninstallation Scripts, uninstall_VMware_CBCloud.sh
- Click on Edit to open the script
- Enter in your company code, i.e. #######
- Click OK to save
- Click OK to save your changes
 |
|
Fileset Group
Once the Fileset and Profiles have been created, the best practice is to create a Fileset group. Organizing and keeping multiple profiles and Filesets within the same group for the same application and its configurations is great management and organization.
Profiles should be installed first. The VMware Carbon Black Cloud Fileset has a requirement script to ensure profiles are installed, before commencing with download and activation of the Fileset.
Remember to always test Fileset to a few devices before mass deployment.
Mac Version 3.8.x is out now and has new deployment methods deprecating the KEXT needs and replacing it with the system extension.
In reply to #1
Thanks, I'll update with the appropriate deployment methods.
No comments to display
No comments to display