IdP Setup: Okta
What
Starting with FileWave Version 14.2.0, we can use Okta for authentication from FileWave. We must create a new application in the Okta Portal and give FileWave access to it.
When/Why
This configuration is required if you want to use Okta for authentication during device enrollment or during login to the FileWave Web and Native administrator consoles.
How
Okta Admin UI
The UI may look different depending on if you are using a Trial Okta organization or the regular, non-Trial version of the Okta.
Part 1: Login to the Okta Admin Portal
Okta Admin Portal
Begin by logging in to the Okta Admin Portal with an administrator's account. (https://example-admin.okta.com/admin)
Part 2: Create an Okta Application in the Okta Admin Portal
Create an Okta Application Integration in Okta Admin Portal
Now we are going to create an Okta application for FileWave to talk to and assign some rights to it.
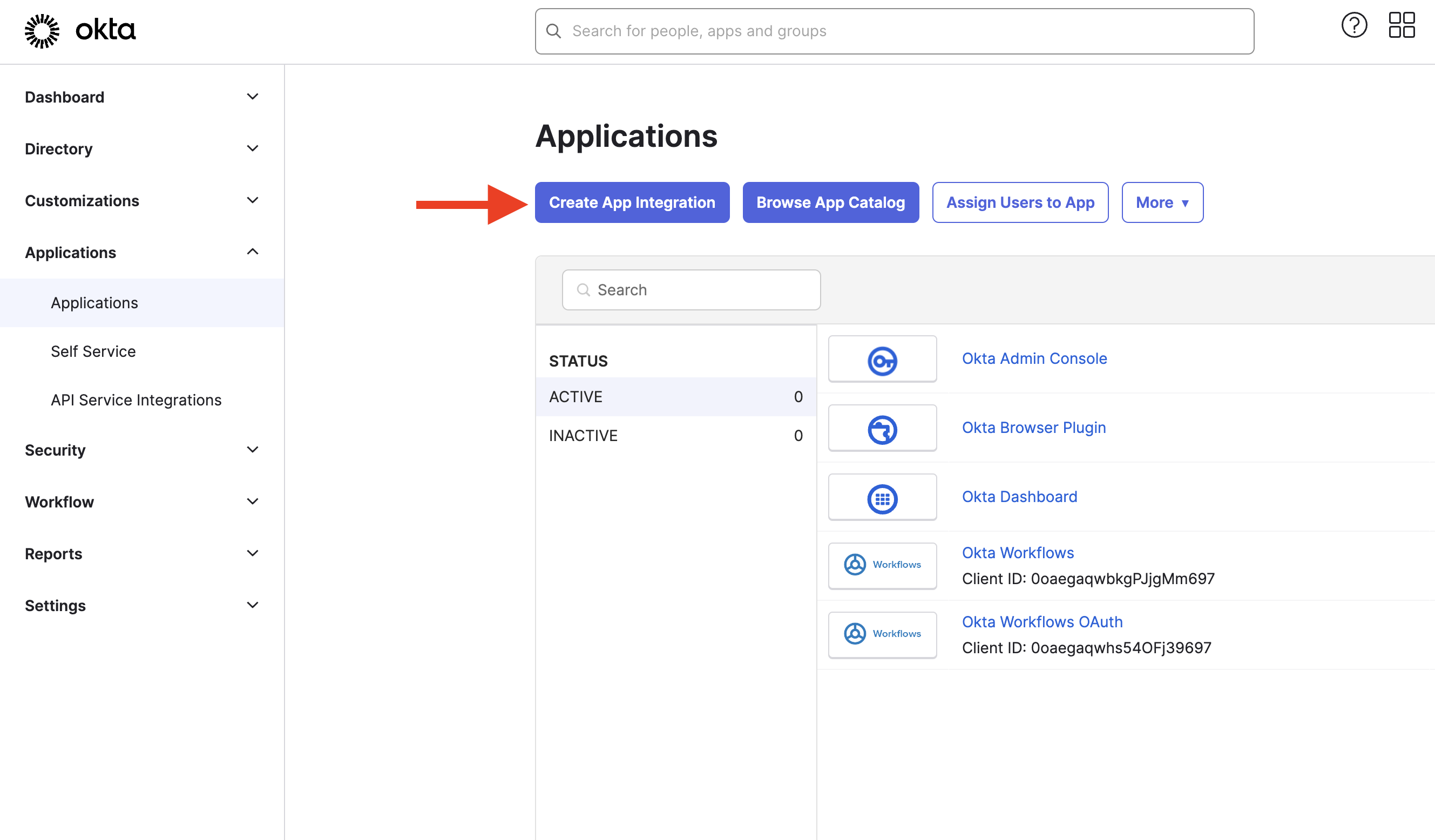
- First, open the Okta Admin > Menu > Applications >
ApplicationsApplications menu and clickthetheAddCreateApplicationApp Integration button.
button.
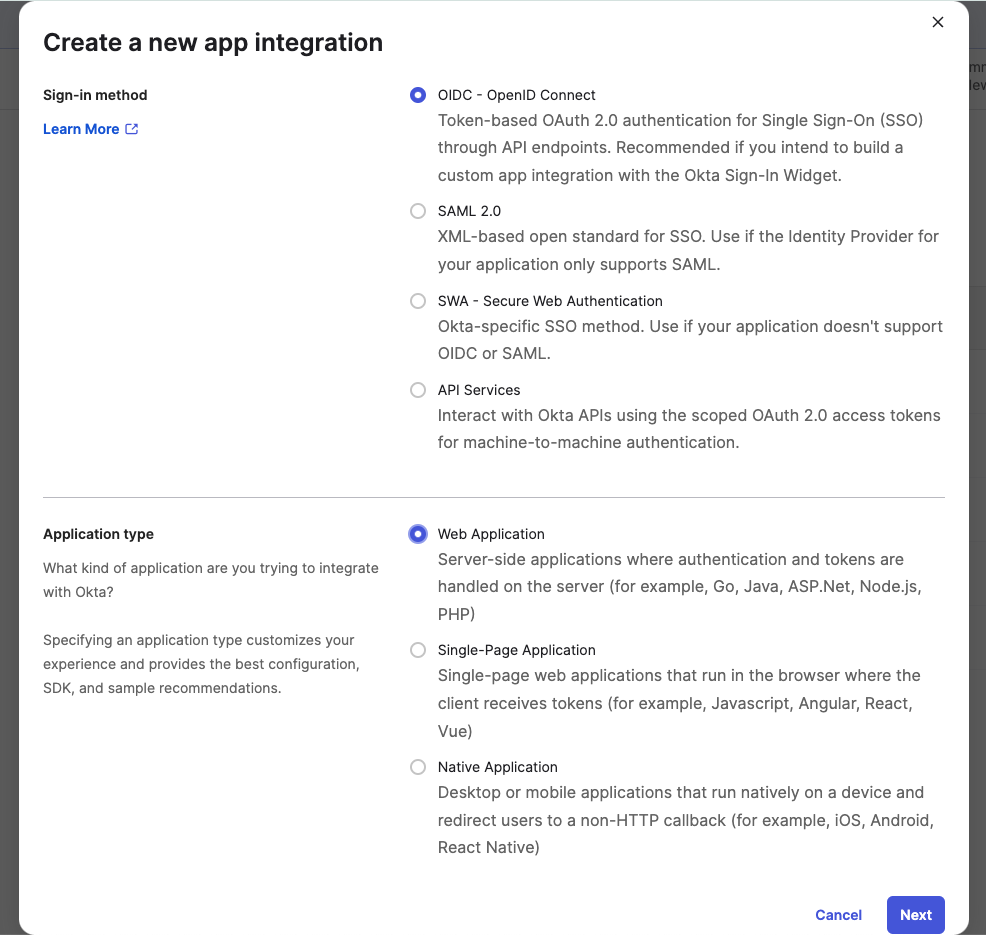
- Next,
clickselecttheCreateOIDCNew-AppOpenID Connect forbuttonthetoSign-inopen theCreate a New Application Integrationmethoddialog.. - Next, configure your Application on
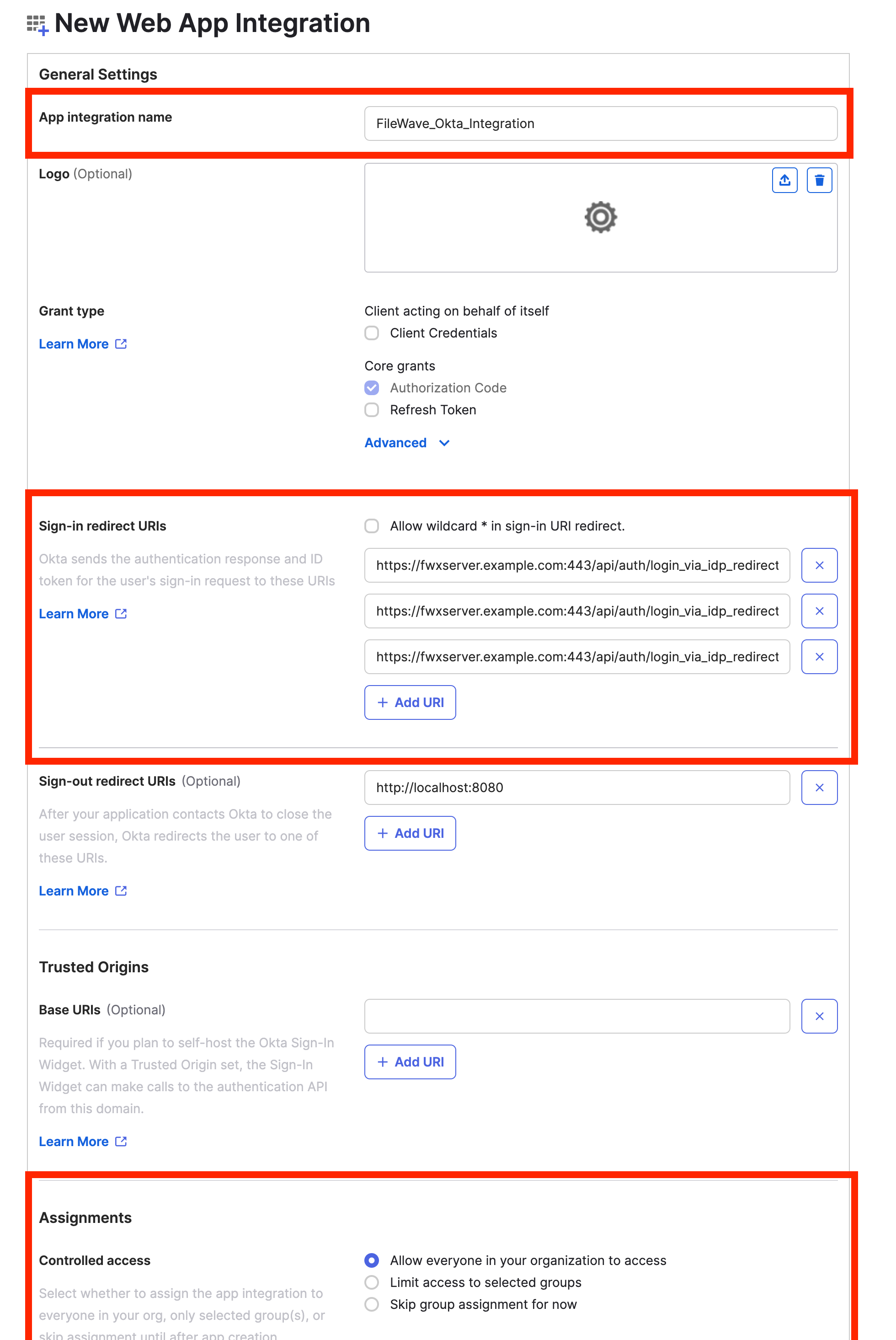
thetheCreateNewOpenID ConnectWeb AppIntegrationIntegrationpage.page you've been redirected to.- Input a meaningful name in
thetheApplicationApp integration name field. - Click
thethe Add URI button forthetheLoginSign-in redirect URIs setting.Paste and inputInput alltheof your FileWaveServerServer's redirect URIs inthetheLoginSign-in redirect URIs setting.If you do not know your redirect URIs then just put some placeholder URI for now and it can be edited later.
Login Redirect URIs for FileWave are displayed in the FileWave Web Admin Settings.
Login Redirect URIs are unique to your server, but will look something like the following:
https://fwxserver.example.com:443/api/auth/login_via_idp_redirect
https://fwxserver.example.com:443/api/auth/login_via_idp_redirect_for_native
https://fwxserver.example.com:443/api/auth/login_via_idp_redirect_for_device
- Under Assignments, choose whether you want to limit access to specific groups or integrate all users in the organization.
- Input a meaningful name in
- Click
thethe Save button to create the Okta App integration.
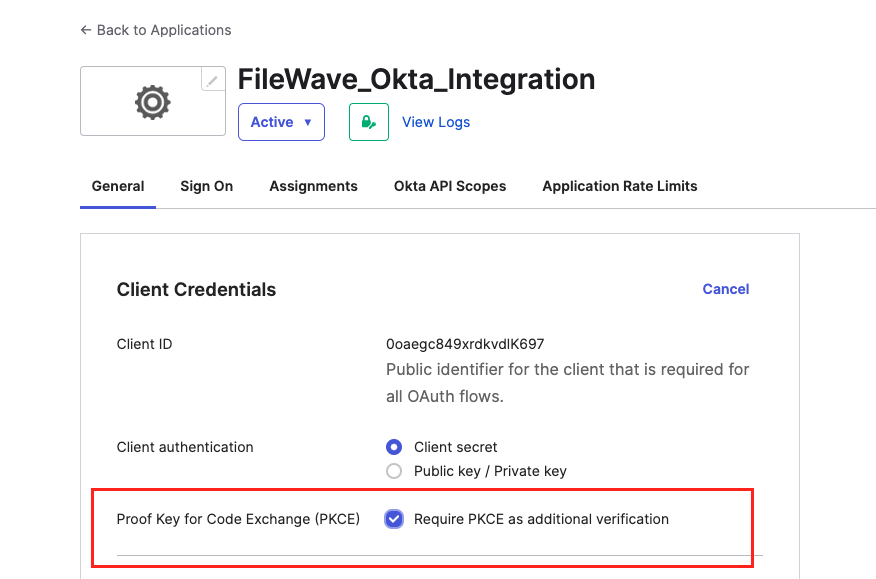
5. After Saving, you'll be Redirected to the application General Settings page. Next to Client Credentials, select Edit and check the box next to Proof Key for Code Exchange (PKCE) and Save.
Part 3: Configure the Okta App in FileWave
Assign Okta Users and/or Groups to the Okta App Integration
Now we are going to configure the Okta App to connect with FileWave.
First, open theOkta Admin > Menu > Applications > Applicationsmenu and select theOkta Appthat was created.On theOkta App > Assignmentstab, click theAssignbutton to assign the App to specified Okta Users and/or Groups.
Configure an Okta App in the FileWave Web Admin Console
In order for FileWave to communicate with Okta for authentication the the Okta App will need to be configured with FileWave.
- Begin by logging into the FileWave Web Admin and open
thetheSettingsSettings button ('⚙'/gear icon in the header). - Open
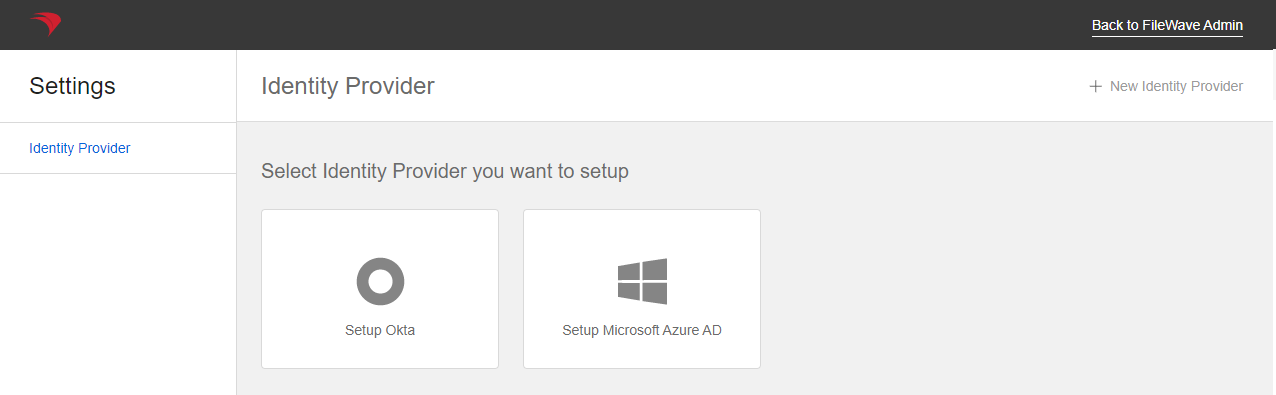
thethe IdentityProviderProvider menu inthethe FileWave Web Admin Settings - On
thethe IdentityProviderProvider menu, clickthethe Setup Okta buttonoror New Identity Provider button in the topright.right if one has already been configured.
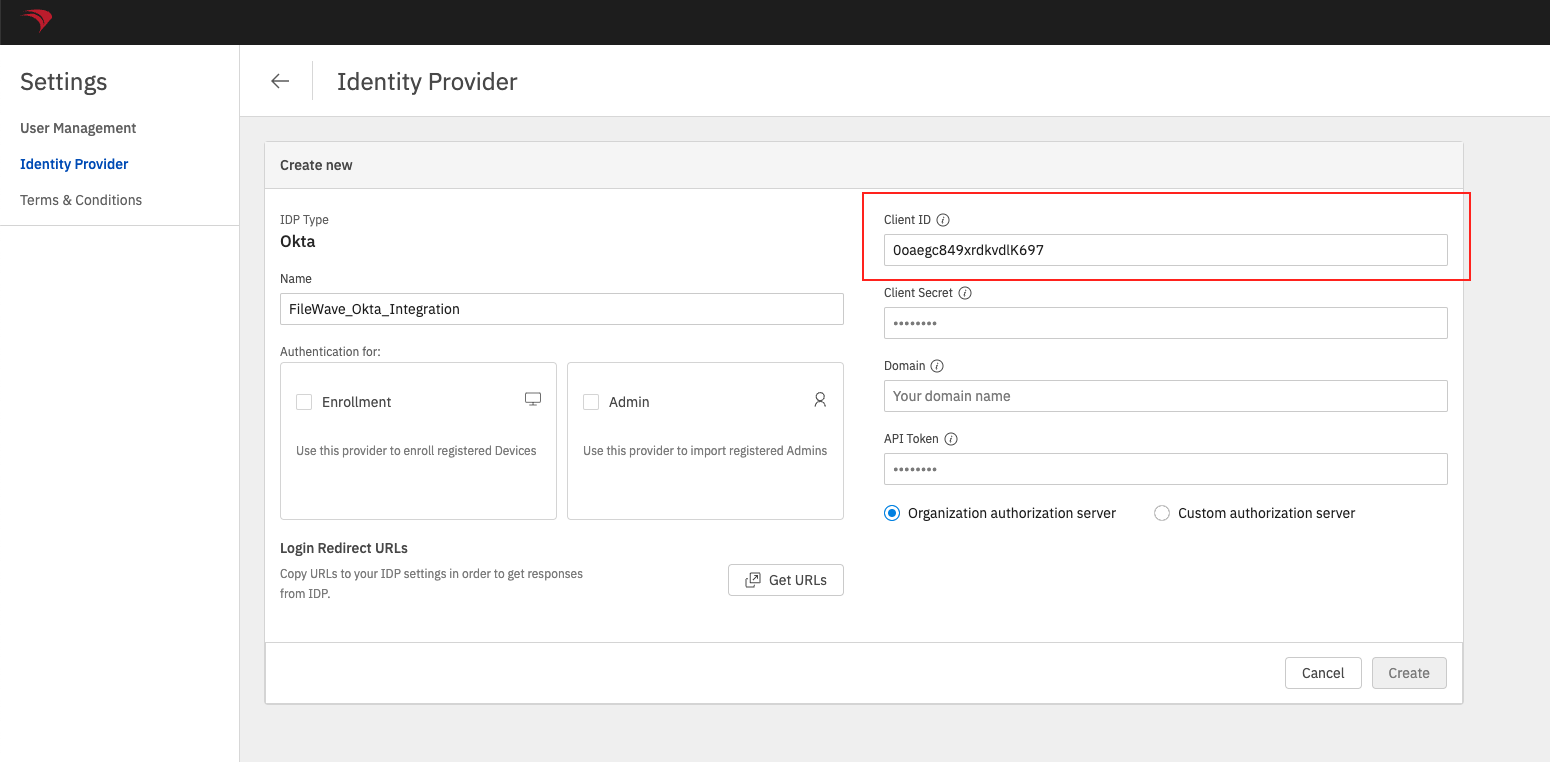
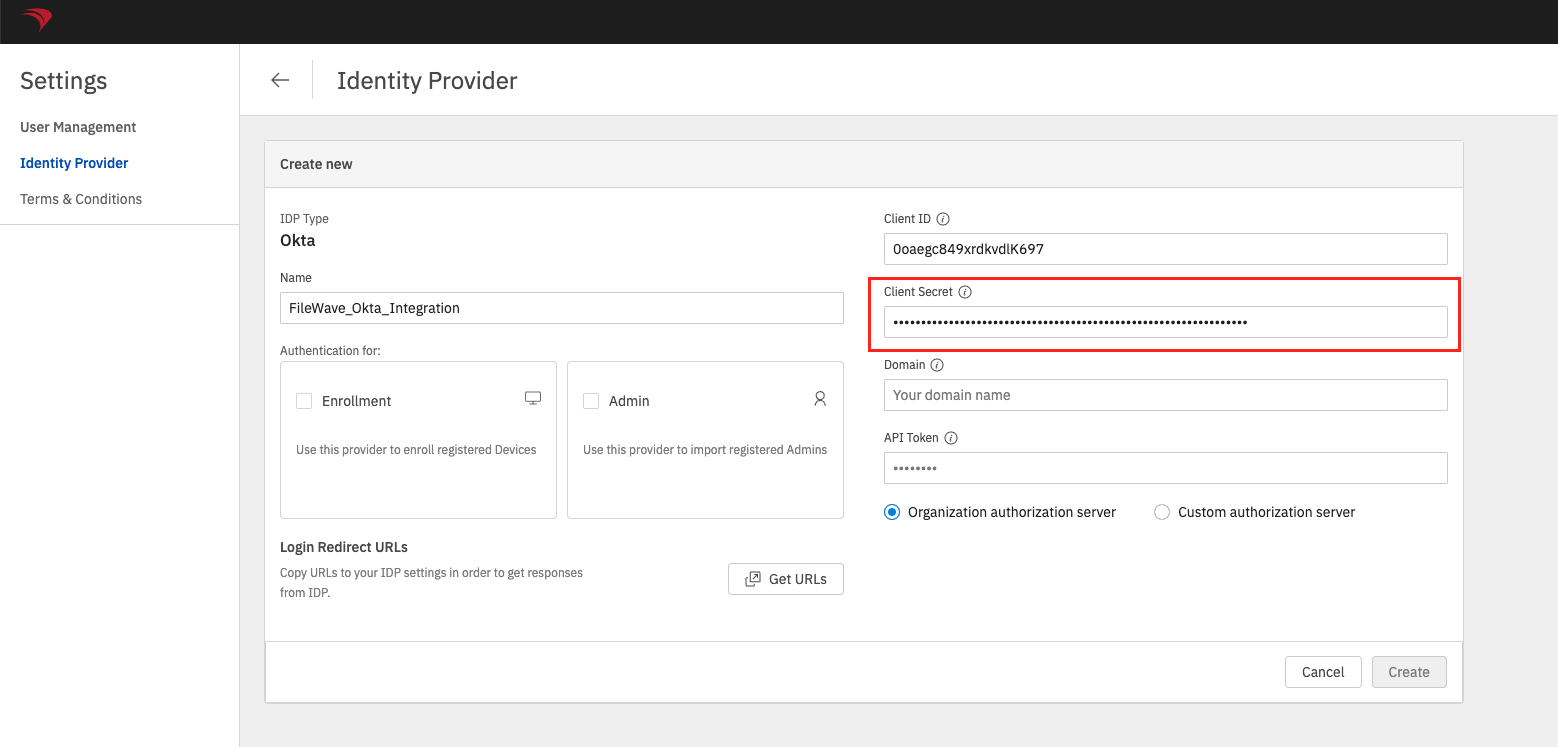
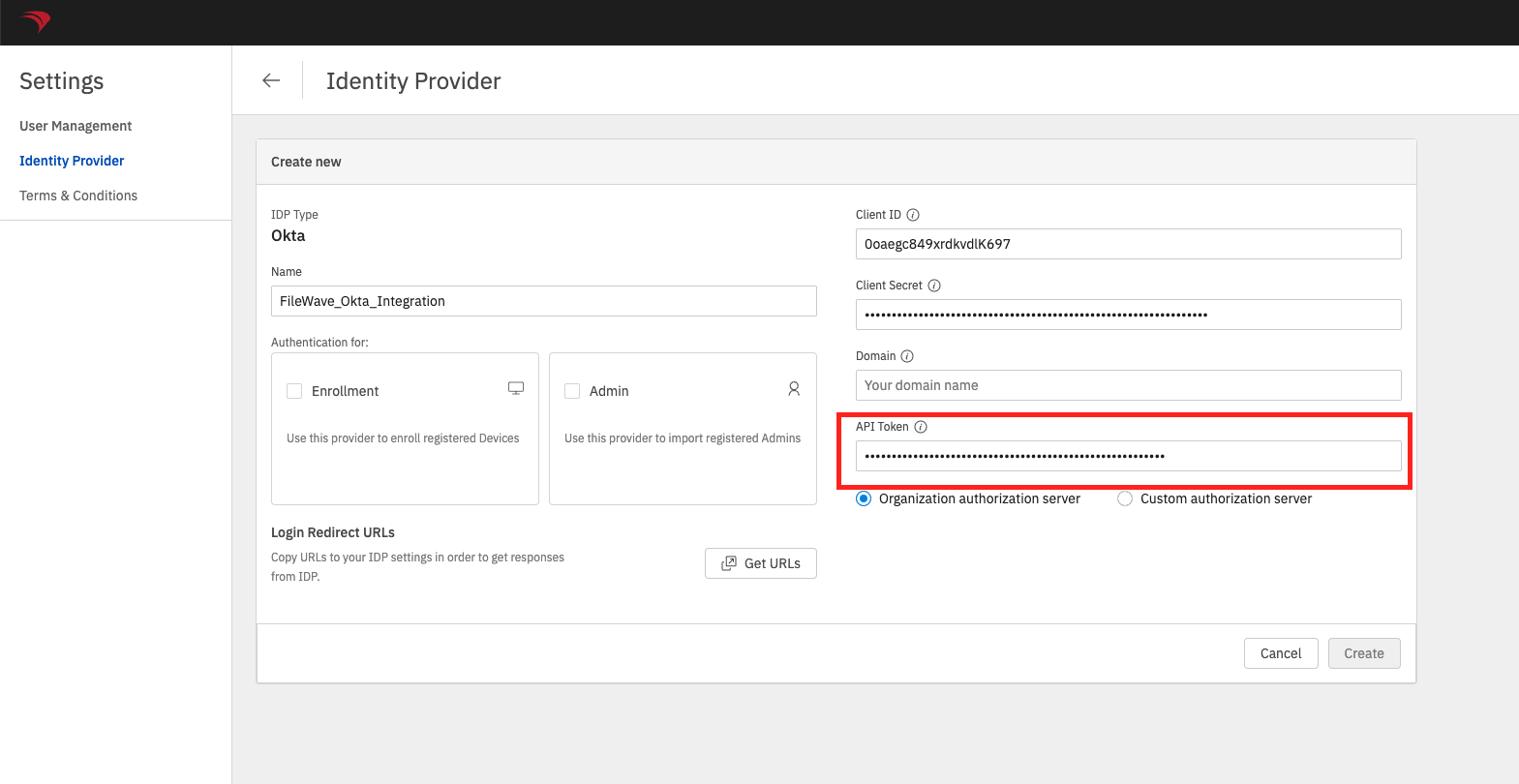
SelectOktain theIDP Typedropdown.- Input a meaningful name in
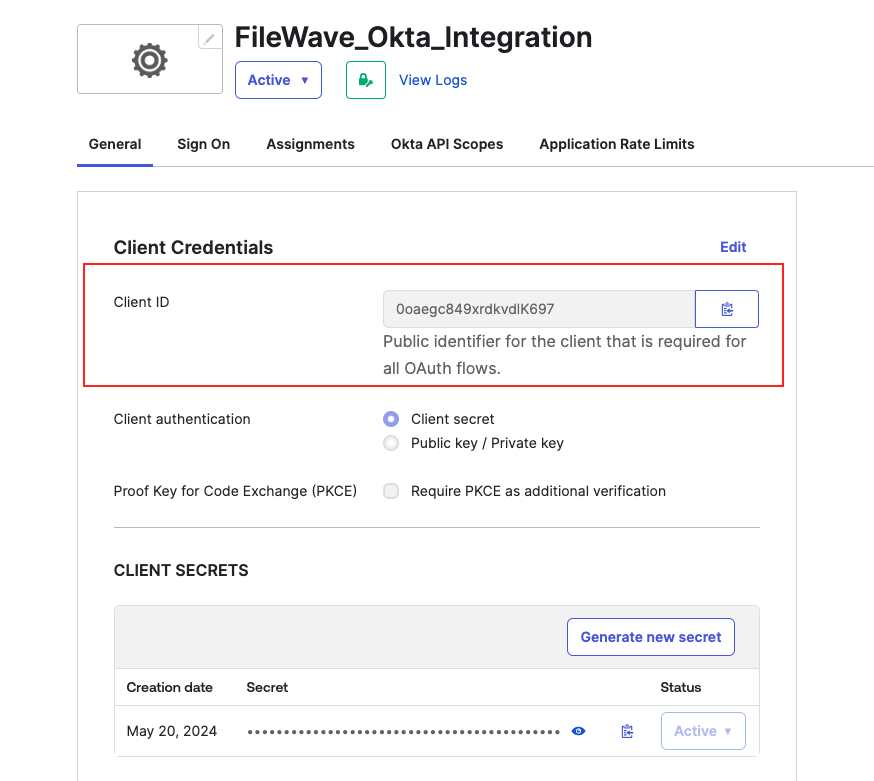
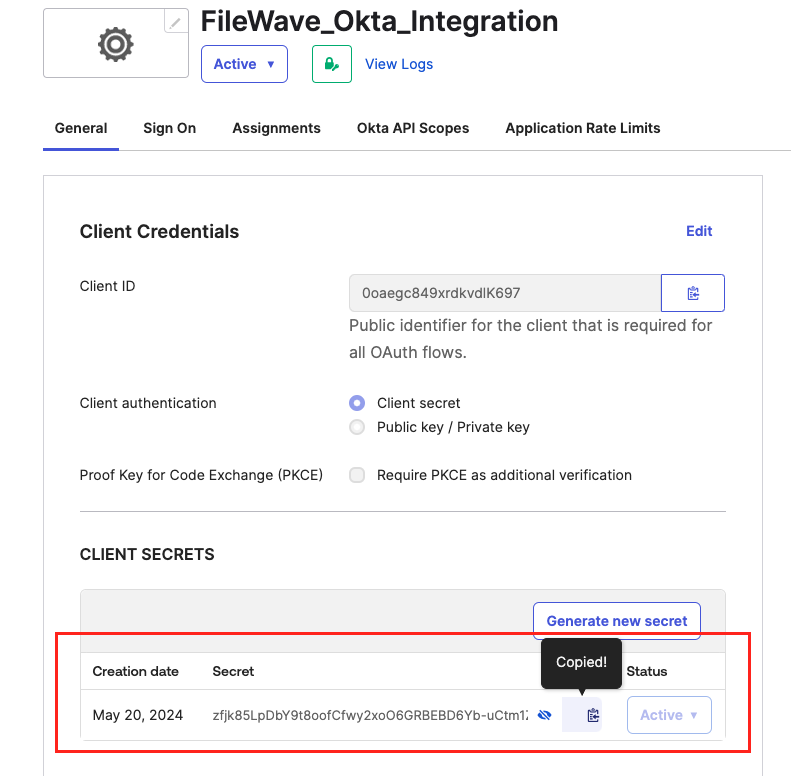
thethe Name field. InputCopytheOktatheClient IDvalue in theClient IDfield.
Okta Client ID value
|
|
|
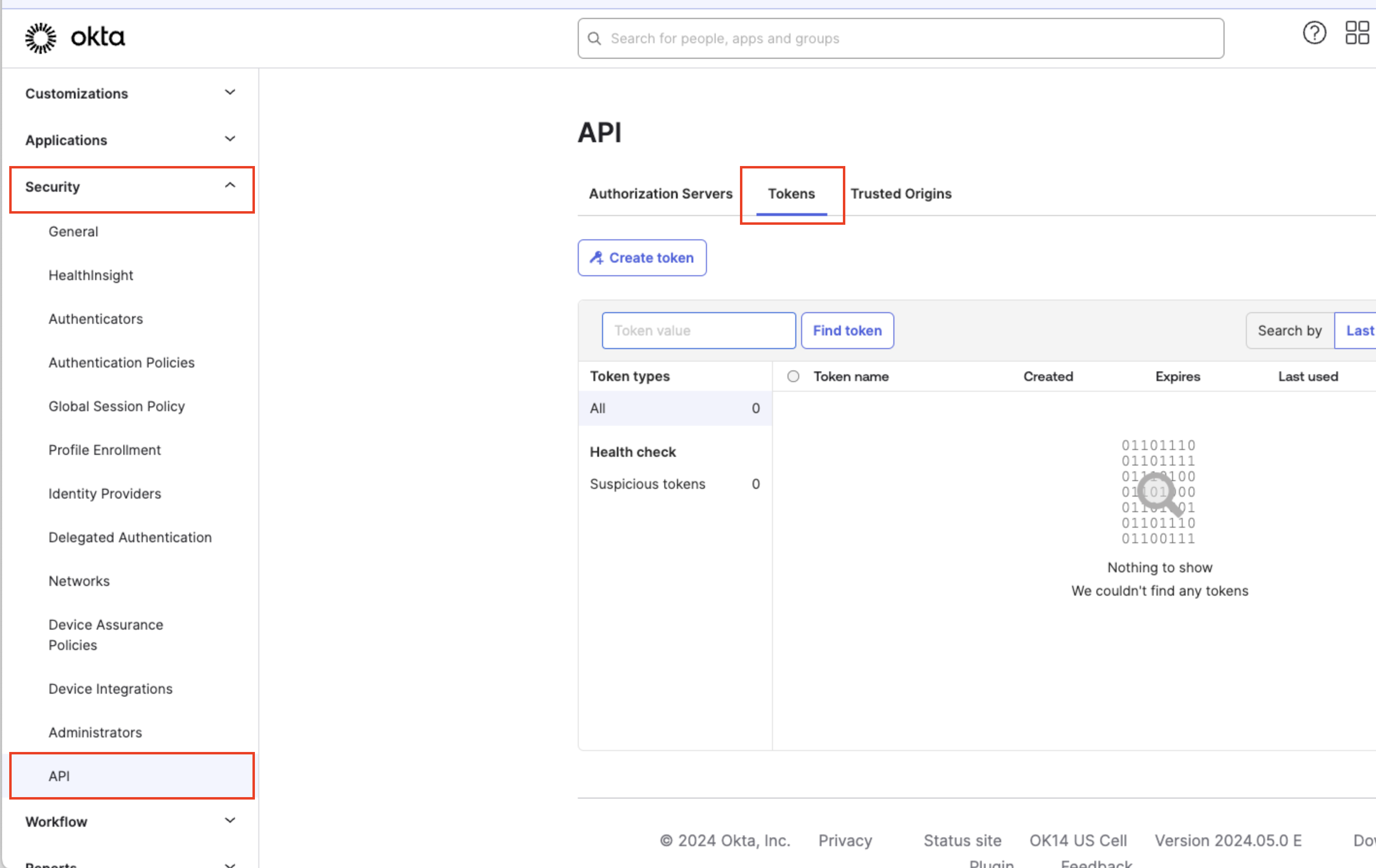
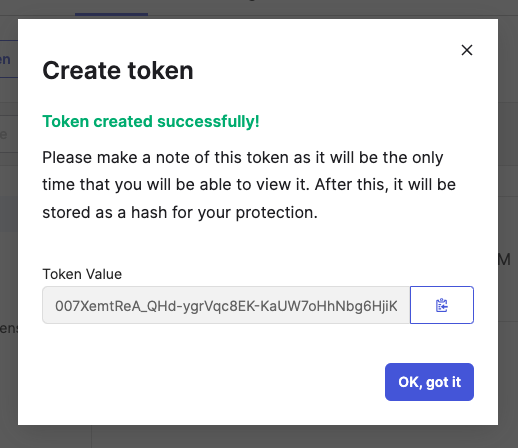
Input theOkta API Tokenvalue in theAPI Token
field.
|
- Open
- the Okta Admin > Menu > Applications > Okta App > General tab and copy the Domain value to a secure location.
(*This is an older screenshot, the current trial Okta account that I am using at the time of this KB's creation doesn't have a domain)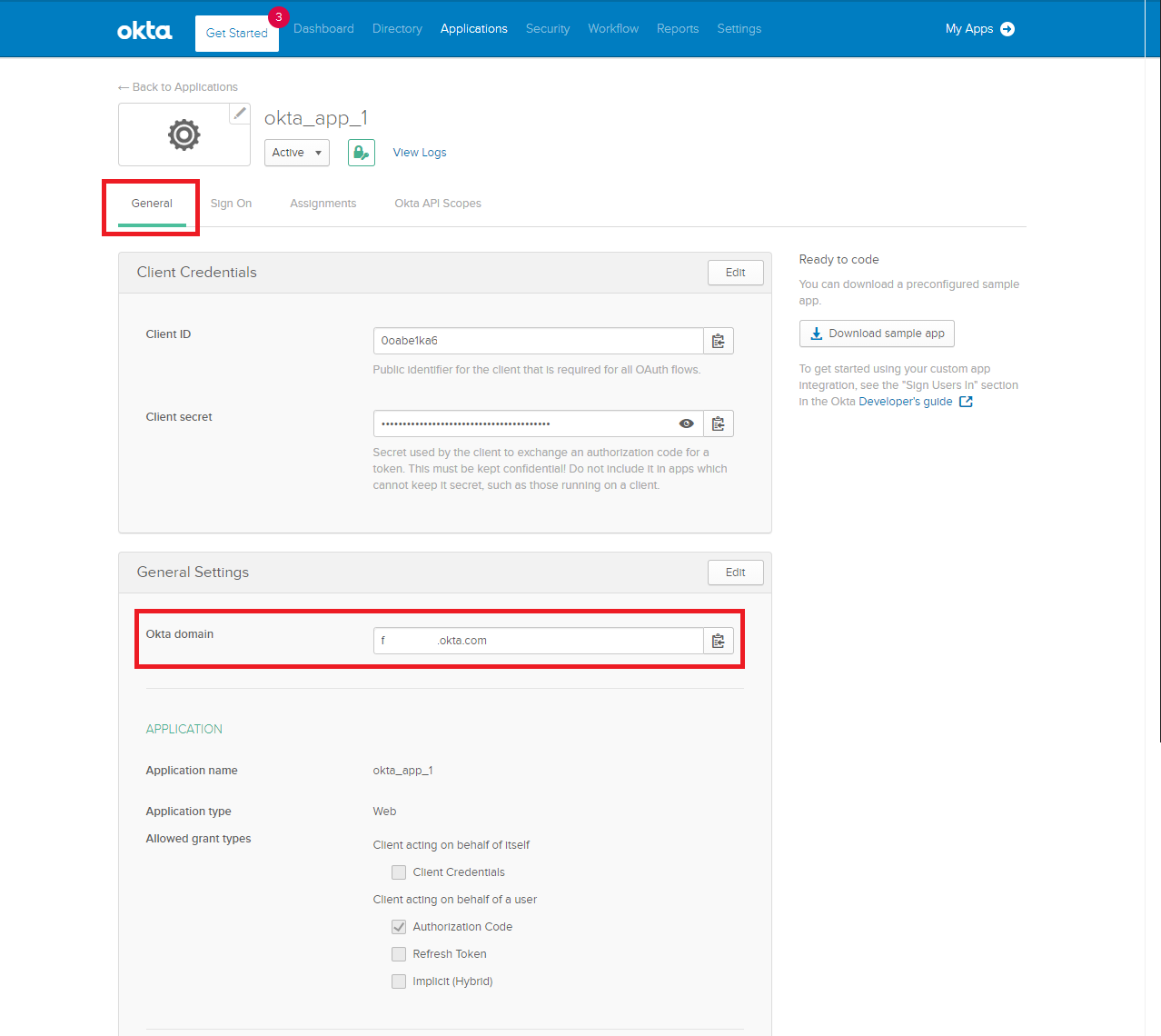
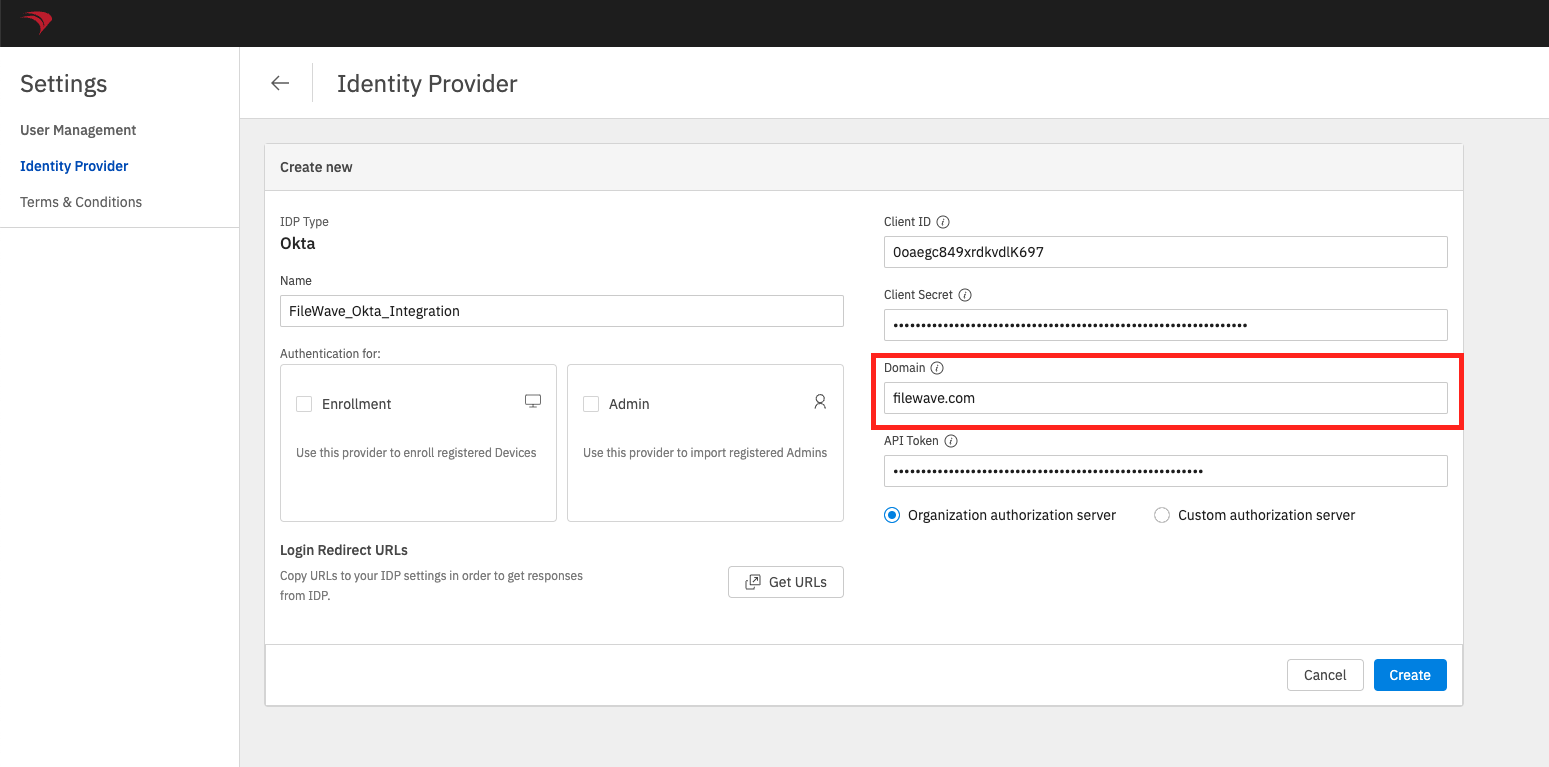
- Input
thethe OktaDomainDomain inthetheDomainDomain field. The value in FileWave should not be saved with the "https://" portion.
Okta Domain
|
|
Select theOrganization authorization serverradio button unless you have setup a custom authorization server.Check theEnrollmentcheckbox if you want to use thisOkta Appauthentication for FileWave Device enrollment.
|
Check theAdmincheckbox if you want to use thisOkta Appfor FileWave Native and Web Admin console authentication.
|
Click theCreate / Savebutton in the Identity Provider card.
Login Redirect URLs
In order for Okta authentication to redirect back to FileWave the Login Redirect URLs will need to be configured in the Okta App.
Start by opening theFileWave Web Admin > Settings > Identity Providermenu.Create or Edit a configured Okta Identity Provider card.Click theGet URLsbutton to display the dialog showing theLogin Redirect URLs.

Next, login to theOkta Admin Portaland open theOkta Admin > Menu > Applications > ApplicationsmenuSelect theOkta Appthat was created that needs theLogin Redirect URIsmodified.Open theGeneraltab for theOkta Appand click theEditbutton in the "General Settings" section.Copy theLogin Redirect URLsfrom theFileWave Web Admin > Settings > Identity Provider > Okta Appand paste all theLogin Redirect URIsin their own rows.Click theSavebutton in the "General Settings" for theOkta App.
Part 4: Configuring and Authenticating with Okta Users
Configure an Okta Identity Provider for Authentication
An An Okta App will need to be be configured in the FileWave Identity Provider settings for use with FileWave Device enrollment and/or FileWave Admin authentication.
- Begin by logging into the FileWave Web
AdminAdmin and openthetheSettingsSettings button (gear icon in the header). - Click
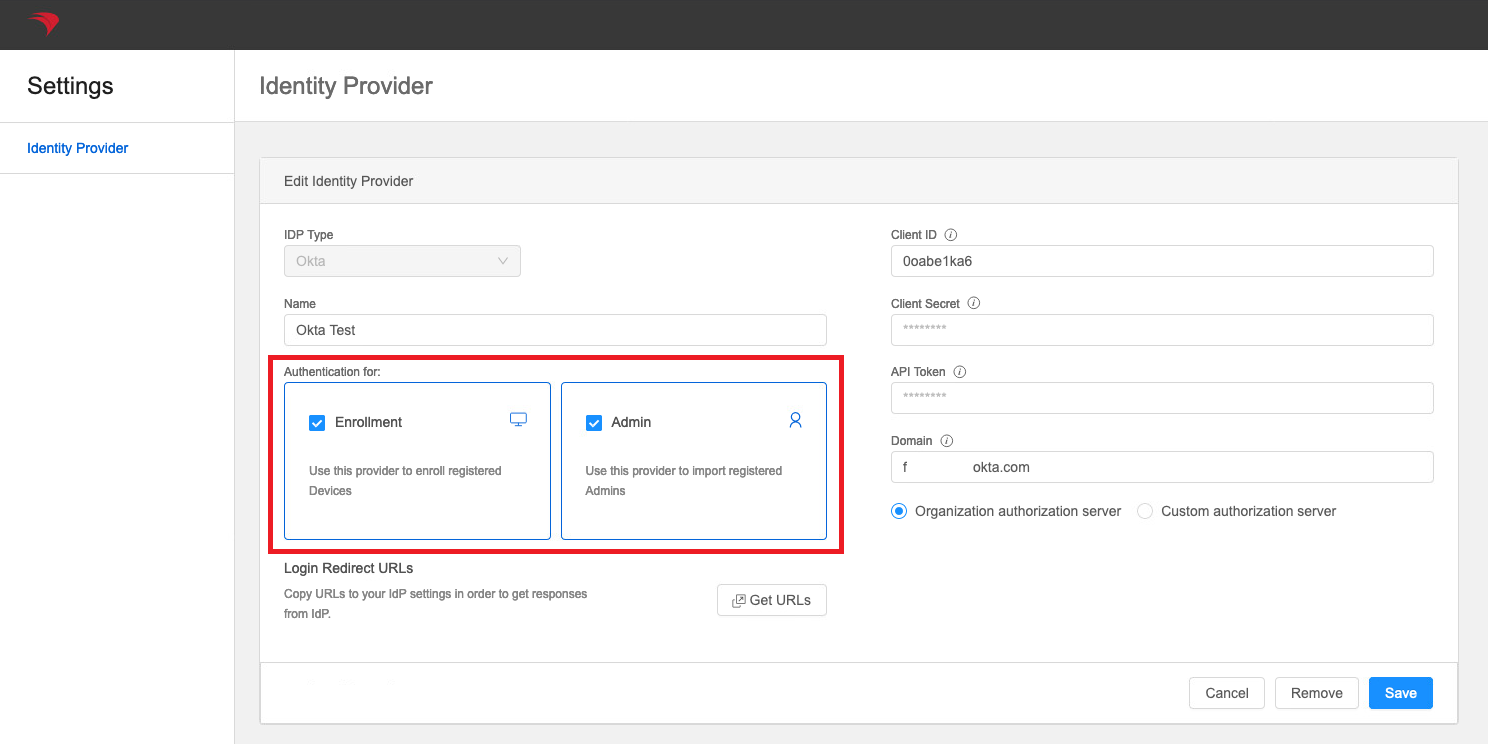
thetheEditEdit button onthethe Okta App card that will be used for authentication. - Check
thethe Enrollment checkbox if you want to usethisthis Okta App authentication for FileWave Device enrollment.
|
- Check
thetheAdminAdmin checkbox if you want to usethisthis Okta App for FileWave Native and Web Admin console authentication.
|
ℹ️ Only one Identity Provider App instance (Okta, Azure AD, etc.) can be configured with
ℹ️ Only one Identity Provider can be configured for FileWave Device Enrollment authentication. |
5. Click the
SaveSave button onthethe OktaAppApp to confirm any authentication changes.

Configure FileWave Admin IdP Groups
- FileWave Admin IDP Groups will need to be created in order to use
thethe OktaAppApp for authentication with the FileWave Native or Web Admin console. - See:
Authenticate with Okta during FileWave Device Enrollment
- Once
thetheEnrollmentEnrollment checkbox is set for an IDP configuration thenthethe OktaAppApp can be used for authentication during FileWave Device enrollment. - See:
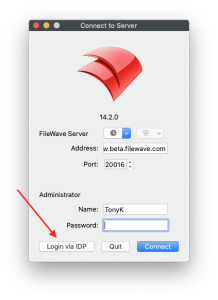
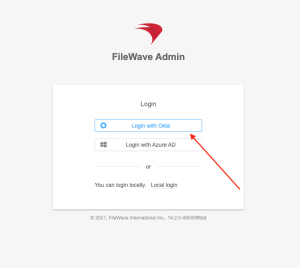
Login with Okta for FileWave Native or Web Admin Console
- Once FileWave Admin IDP Groups are created for
anan Okta App the Login withOktaOktaoptionoption can be used with the FileWave Native or Web Admin console for authentication. - See:


Related Content
- IdP Setup: Azure AD
- Adding IdP Groups for FileWave Authentication
- Adding IdP Groups for FileWave Authentication
- Admin Login in Using an IdP Provider