Part 3: Setting up the Portal App
What
The configuration of your Windows MDM integration will all be driven by an application you yourself create in the Microsoft Entra Portal.
When/Why
This application is the linchpin that ties your devices (in AutoPilot), through your user accounts (the group associated with the app), into redirection to your FileWave MDM server. Detailed setup steps follow.
How
Add the Entra ID account in FileWave
-
Open your FileWave AnyWhere (Web Admin) page and navigate to sources.
-
Click the Microsoft tab.
-
Click on New account, and you should see the following form:
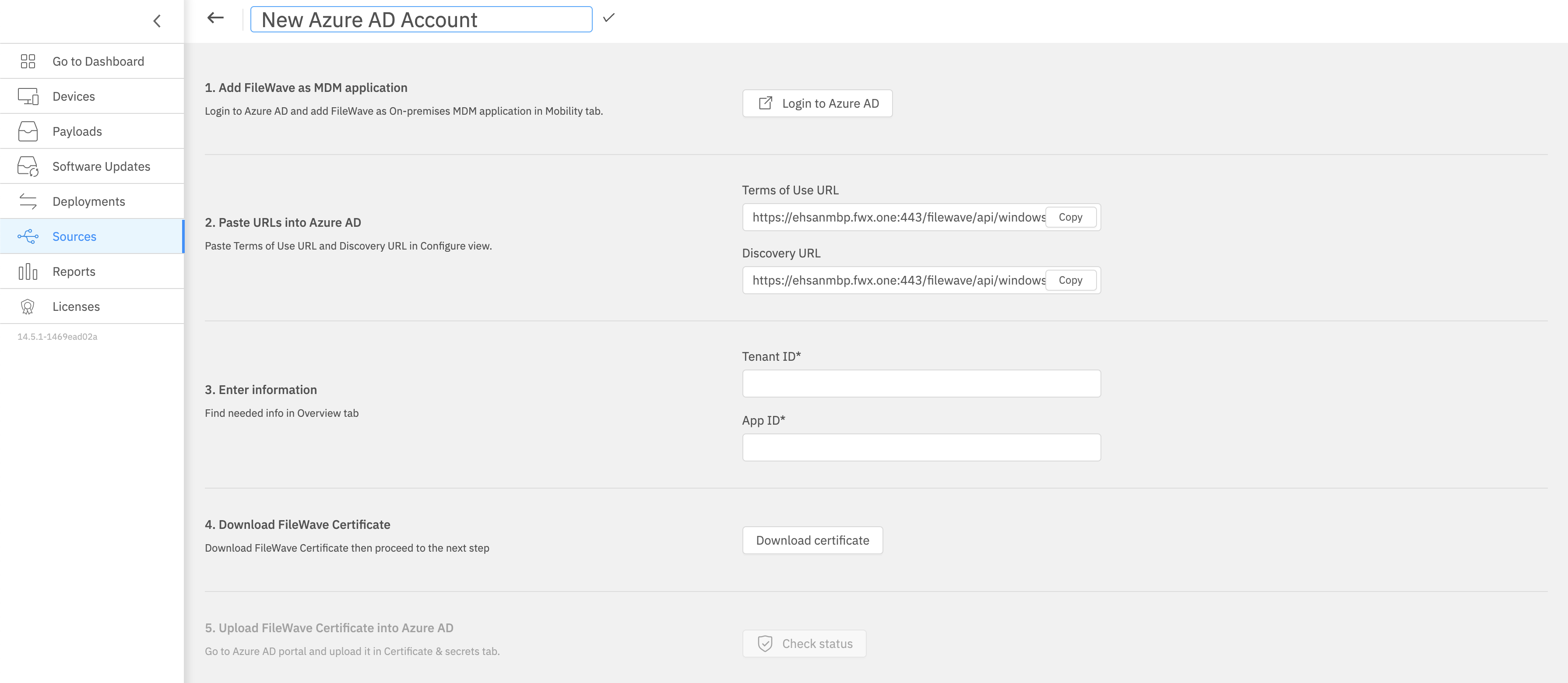
Keep this form open for completion in later steps.
Configuring Microsoft Entra ID
Creating an MDM application
To enable MDM enrollment, first, you need to configure your Microsoft Entra ID to recognize your FileWave server as your MDM.
-
Go to your Microsoft Entra ID portal: https://entra.microsoft.com
-
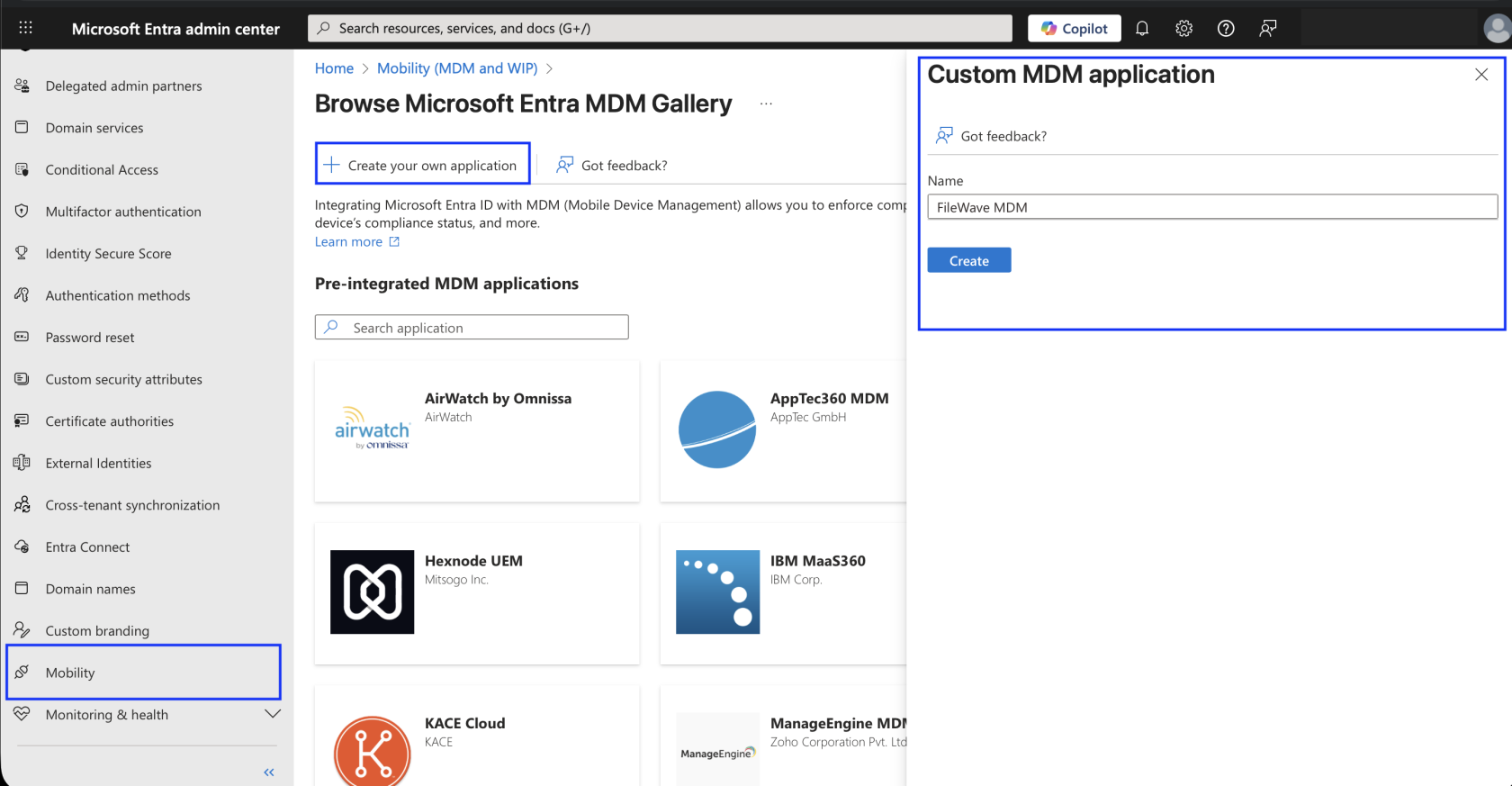
From Home, navigate to Entra ID → Mobility and then click Add application.
-
Select Create your own application, give it a name and a log, and click Create.
Configuring your MDM application
-
You will now be prompted to configure MDM user scope:
-
MDM user scope: This is where you indicate which users can enroll their devices using this MDM application. You can either choose:
-
All: Force all users to use this MDM application. (Preferred)
-
Some: You can select user groups that are allowed to use this MDM application to enroll their devices. If you do use this, then you will need to make sure that you make a Group to restrict this, and add all of the users who will have their devices managed by MDM in that same group.
-
-
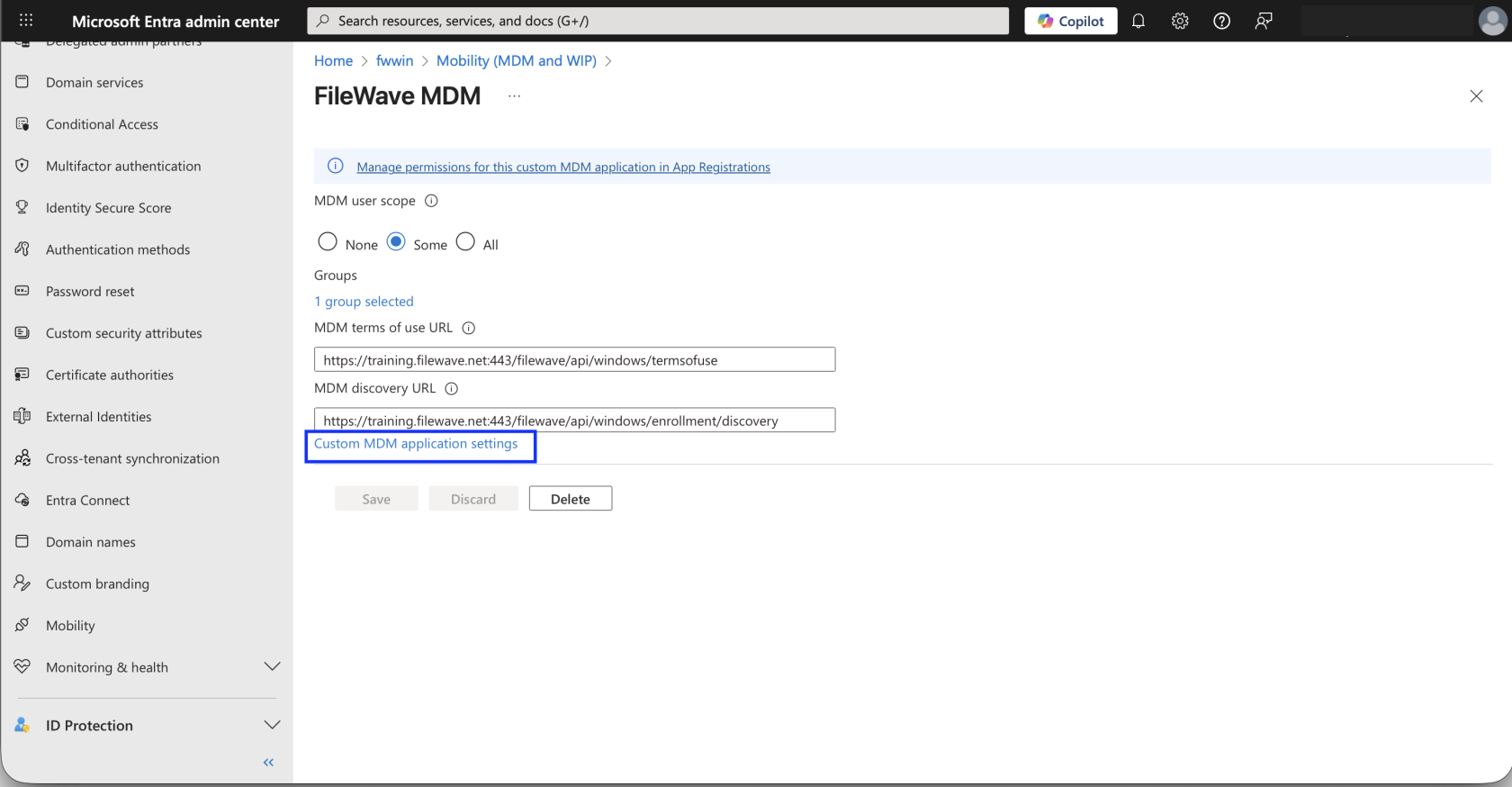
MDM terms of use URL:
Copy the value from the form you opened up in FileWave AnyWhere (Web Admin) earlier.
-
MDM discovery URL:
Copy the value from the form you opened up in FileWave AnyWhere (Web Admin) earlier.
-
It is very important that if you have another solution in place, like InTune, you make sure that you do not have both InTune and FileWave enabled for the same users. You may get an error about not having permission to enroll devices. You can test this by disabling the Intune MDM (or another vendor) in Microsoft Entra by setting it to None, waiting 5 minutes, and then you will be able to enroll using FileWave.
Think about which MDM solution you want to use for your different users in your environment. A single device can only really be in a single MDM. You can enroll in Intune for MDM and install the FileWave agent, for instance, but then you could only push Windows Profiles from Intune. Everything else would work just fine in FileWave for those devices.
Integrating FileWave and Microsoft Entra
After configuring your MDM application, on the same page, click on the small link that reads: Create MDM application settings.
You should see the following page:
From here there are only few steps left!
-
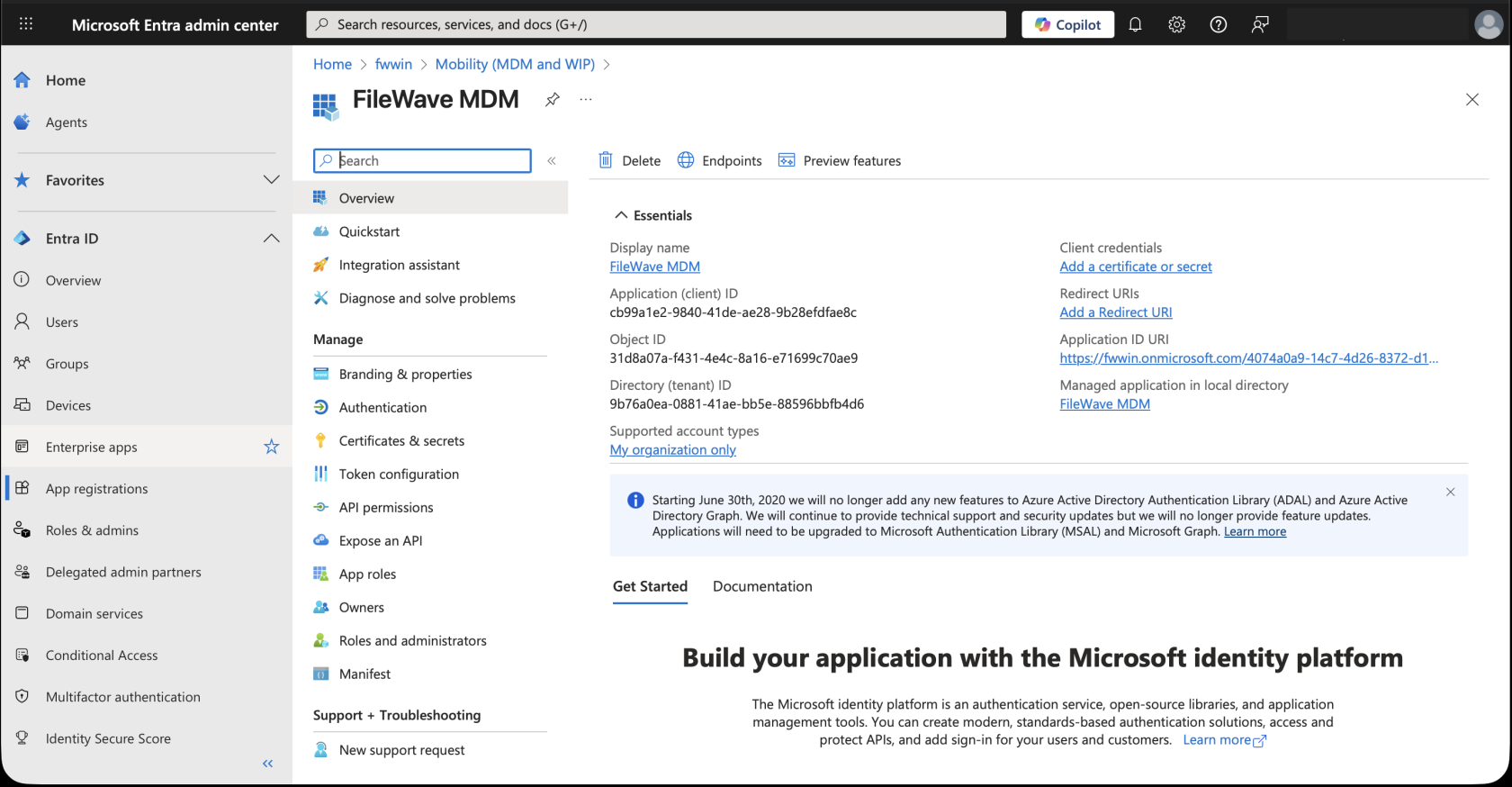
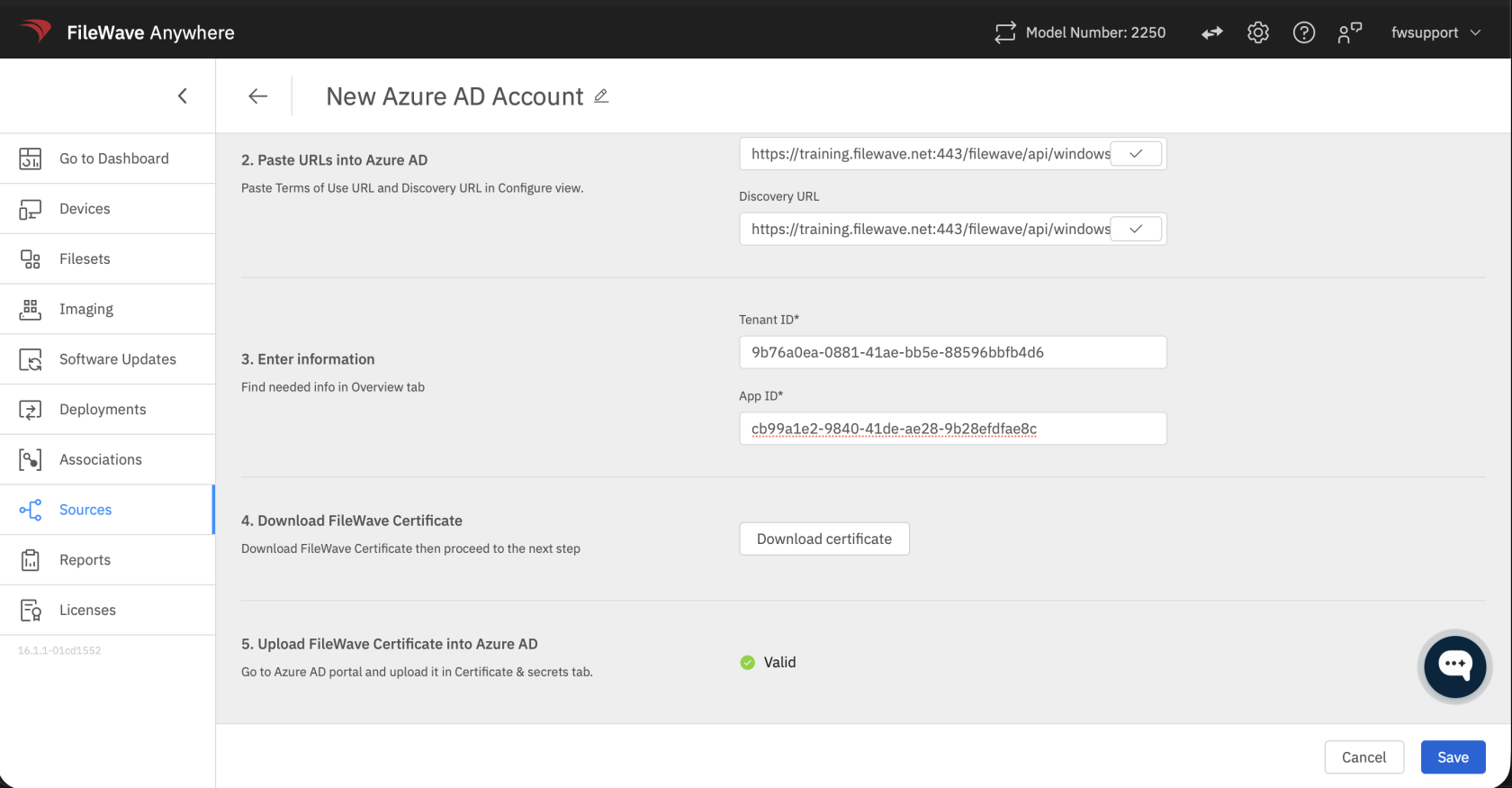
Copy the Application (client) ID and Directory (tenant) ID from this page and paste it in the Microsoft Entra Account form in FileWave AnyWhere (Web Admin) (which you kept open from earlier)
-
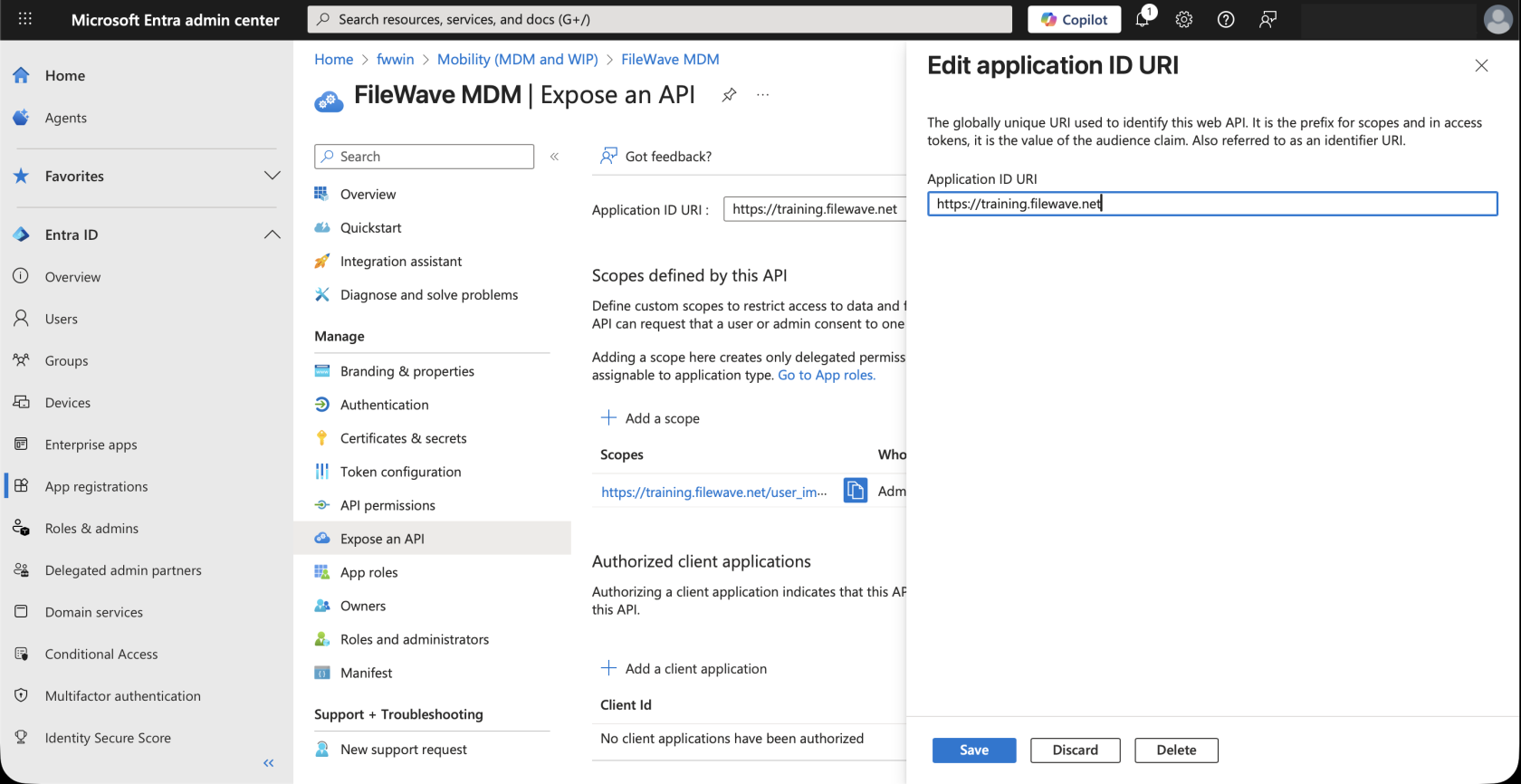
The Application ID URI value in your MDM app (in Microsoft Entra ID) must match your FileWave server URL, to fix that, go to Expose an API on the left side, and edit the URL there. The URL should be like https://example.filewave.net, replacing that with your server's DNS name.
-
Go back to the Microsoft Entra account form in your FileWave AnyWhere (Web Admin), and download the FileWave certificate.
-
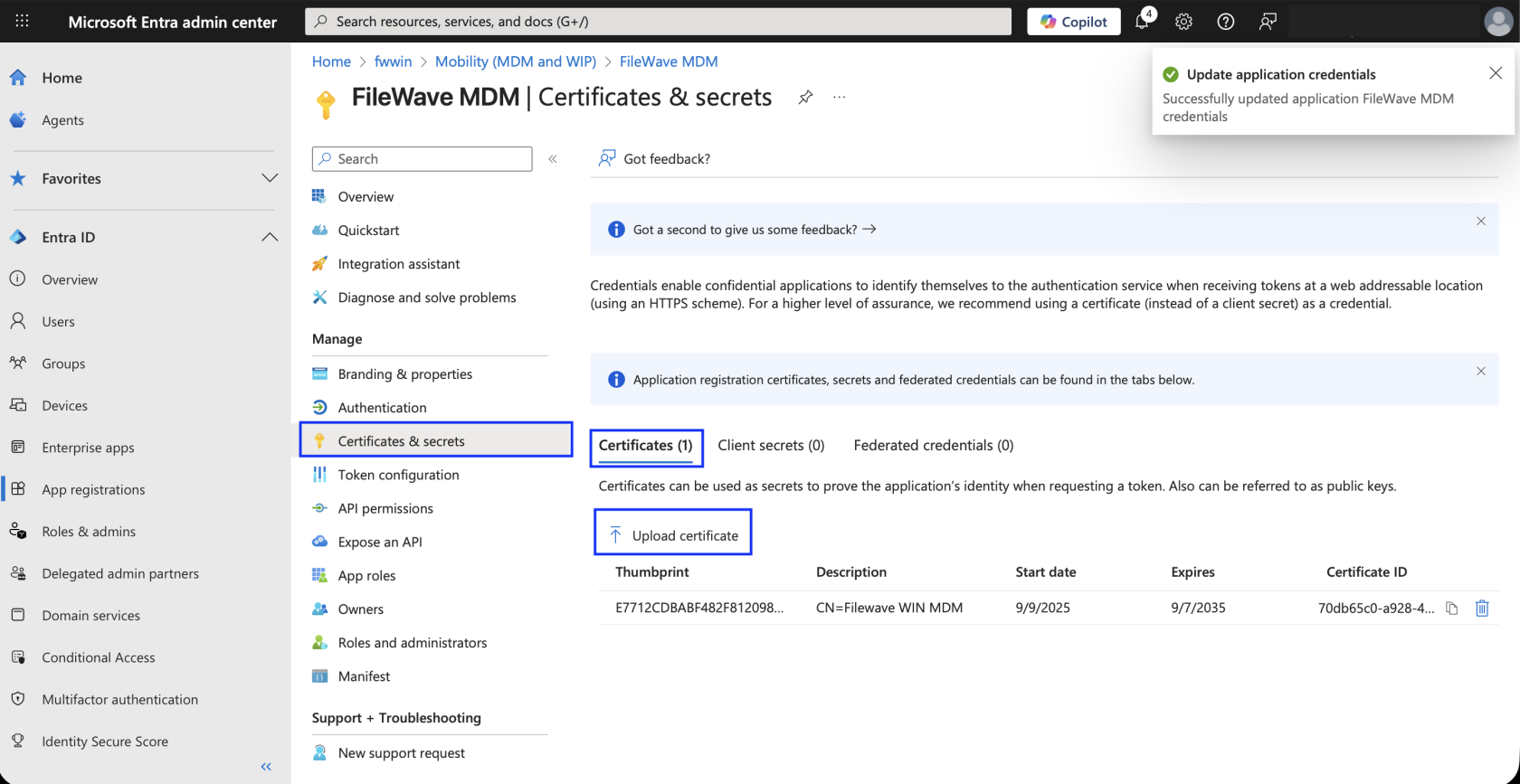
Once you have the certificate, go back to the Microsoft Entra ID portal, navigate to Certificates & secrets > Certificates and upload your certificate to your Microsoft Entra MDM application there.
-
Once the Certificate is uploaded, wait couple of seconds, then go back to FileWave AnyWhere (Web Admin), in the already open Microsoft Entra account form and click on Check Status button.
-
As soon as you see the green light, go ahead and save your Microsoft Entra account.
You are now ready to enroll a device in to Windows MDM.
Application tenant or consent messages
You may see a message similar to below:
- AADSTS500011 – The resource principal named [URI] was not found in the tenant named [guid]. This can happen if the application has not been installed by the administrator of the tenant or consented to by any user in the tenant. You might have sent your authentication request to the wrong tenant.
If you’re trying to log in from an application that doesn’t support user consent flow or you’re unable to use it otherwise, you can use the same special login URL crafting trick that I proposed in my article for resolving consent-related issues when getting error AADSTS650001, and create a URL like this:
If the application requires admin consent, you may replace "consent" with "admin_consent".
No comments to display
No comments to display