Default TCP and UDP Port Usage
FileWave software uses the below-listed TCP/IP ports. These are default settings and may be configured to listen on different ports if required. Consider FileWave Server should not have IPv6 enabled for the best experience.
Port Testing
Please consider downloading the FileWave Port Testing macOS/Windows utility to confirm communication of Google Cloud Messaging, Apple Push Notifications and connectivity between device network(s) and Server/Boosters.
The following may be run from the server to confirm Apple, Microsoft, and FileWave services:
Server Command Line
sudo /usr/local/filewave/python/bin/python /usr/local/filewave/django/manage.pyc check_connectionsTeamViewer Ports
TeamViewer has an additional set of ports to consider:
https://community.teamviewer.com/English/kb/articles/4139-ports-used-by-teamviewer
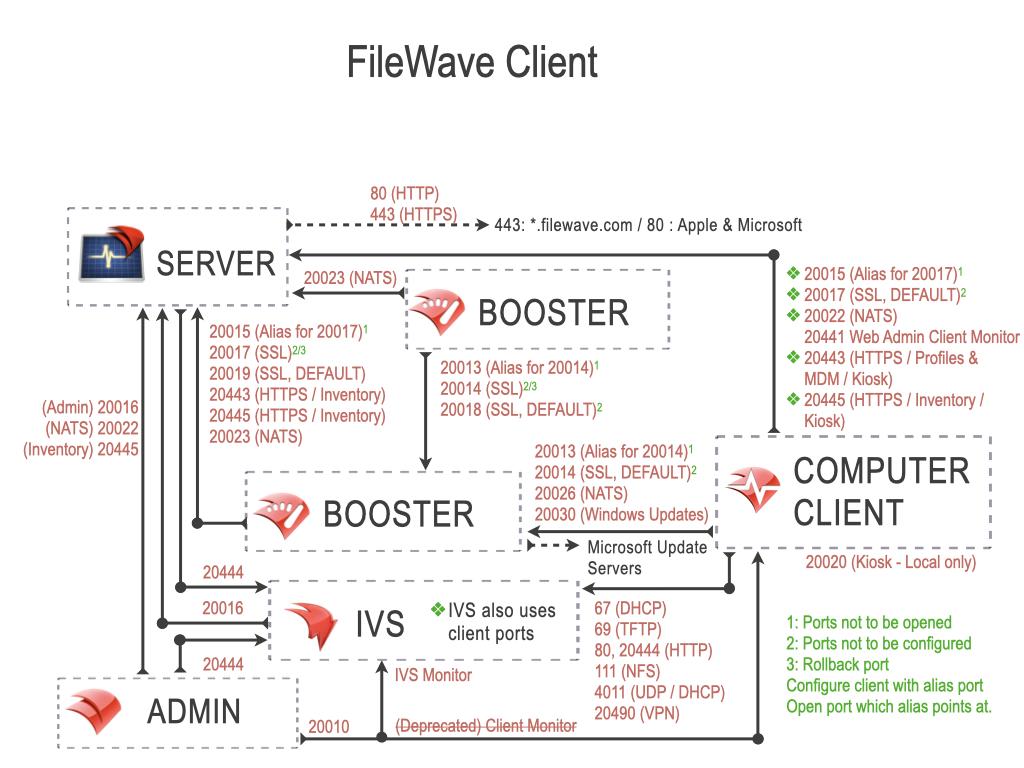
FileWave Server Ports
MDM default port is now 20445 as shown throughout this KB. On older versions of FileWave, this was 20443. To confirm the defined port, check the Port setting in FileWave Central > Preferences > Mobile > MDM Server > Port
The ports in this table are listed from the FileWave Server’s perspective, so the “Server In/Out” column indicates the direction of traffic relative to the Server.
| Server Ports | Service | Protocol | Server In/Out | Description |
| 80 | HTTP | TCP | Outgoing |
FileWave Software Updates (apple.com & microsoft.com) *** |
| 443 | HTTPS | TCP | Outgoing | * FileWave License Server (fwks.filewave.com & logstash.filewave.com)
* FileWave Software Updates (apple.com) *** * FileWave/TeamViewer Session Server (rcs.filewave.com) * FileWave/TeamViewer Push Notification Server (fwpn.filewave.com) * FileWave Kiosk ( *.filewave.cloud ) * FileWave AutoPkg integration (le7bqzikha.execute-api.us-east-1.amazonaws.com) |
| 443 | HTTPS | TCP | Incoming |
* API endpoints - Anywhere API (v2 API) * Device to Server (Enrollment URL) - Google/Azure/Okta |
| 20016 | SSL | TCP | Incoming | FileWave Central to Server |
| 20017 | SSL | TCP | Incoming |
FileWave Client to Server: Secure Set port 20015, not 20017, in Client Configuration |
| 20019 | SSL | TCP | Incoming | Booster to Server: Priority Traffic |
| 20022 | SSL | TCP | Incoming | FileWave Central to Server: NATS
FileWave Client to Server: NATS IVS to Server: NATS |
| 20023 | SSL | TCP | Incoming |
FileWave Booster to Server: NATS |
| 20124 | SSL | TCP | Incoming | FileWave Server JSON Websockets (JWT) Websocket connections for NATS SERVER used between FW Anywhere and Central to FW Server. |
| 20441 | Proprietary | TCP | Incoming | DO NOT OPEN FileWave Client to Server: Remote Client Monitor (Removed in FileWave 16.1+) Server no longer listens on this port. |
| 20443 | HTTPS | TCP | Incoming |
* FileWave Client to Server: Inventory * Apple Devices to Server: Inventory, Profiles, DDM, MDM * Android Devices to Server: Companion App * Chromebook to Server: Inventory * Booster to Server: Inventory/Discovery * App Portal to Server * FileWave Central and FileWave Anywhere to Dashboard |
| 20445 | HTTPS | TCP | Incoming |
NATS includes: Remote Control Publishing, Remote Control Routing, device renaming, revoking device certificates, push notifications
*** Also used by FileWave Central to vendor Software Update Servers.
Configuring port 20015 also automatically configures SSL port; 20017 [port entered +2]. 20015 is now deprecated and 20017 will be used where 20015 is set. Open port 20017 alone for Client communication.
FileWave Central Ports
The ports in this table are listed from FileWave Central's perspective, so the “In/Out” column indicates the direction of traffic relative to the macOS or Windows running Central there.
| Server Ports | Service | Protocol | In/Out | Description |
| 443 | HTTPS | TCP | Outgoing | * FileWave License Server (fwks.filewave.com & logstash.filewave.com)
* FileWave/TeamViewer Session Server (rcs.filewave.com) * FileWave/TeamViewer Push Notification Server (fwpn.filewave.com) * FileWave AutoPkg integration (le7bqzikha.execute-api.us-east-1.amazonaws.com) |
| 20016 | SSL | TCP | Outgoing | FileWave Central to Server |
| 20022 | SSL | TCP | Outgoing | FileWave Central to Server: NATS |
| 20443 | HTTPS | TCP | Outgoing |
* FileWave Central and FileWave Anywhere to Dashboard on Server |
| 20445 | HTTPS | TCP | Outgoing |
FileWave Kiosk Ports
The ports in this table are listed from the Kiosk on the Client's perspective, so the “In/Out” column indicates the direction of traffic relative to the macOS or Windows Kiosk running there.
| Kiosk Ports | Service | Protocol | In/Out | Description |
| 443 | HTTPS | TCP | Out | Devices to *.filewave.cloud (To download the Kiosk App) |
| 20443 | HTTPS | TCP | Out | Devices to FileWave Server |
| 20445 | HTTPS | TCP | Out | Devices to FileWave Server |
FileWave Client Ports
The ports in this table are listed from the FileWave Client's perspective, so the “In/Out” column indicates the direction of traffic relative to the macOS or Windows Client.
| Client Ports | Service | Protocol | In/Out | Description |
| 443 | HTTPS | TCP | Out | FileWave Software Updates (apple.com & microsoft.com) *** |
| 443 | HTTPS | TCP | Out |
For Hosted Customers Only. If blocked then a Booster can be used so that the configured Booster can reach these and a Client would not need to: Cloudflare host for Filesets in the Cloud - c7b0813948fe034d9fe3ca8c90faddab.r2.cloudflarestorage.com
Cloudflare IP addresses as listed on https://www.cloudflare.com/ips-v4 - 173.245.48.0/20 |
*** Also used by FileWave Central to vendor Software Update Servers.
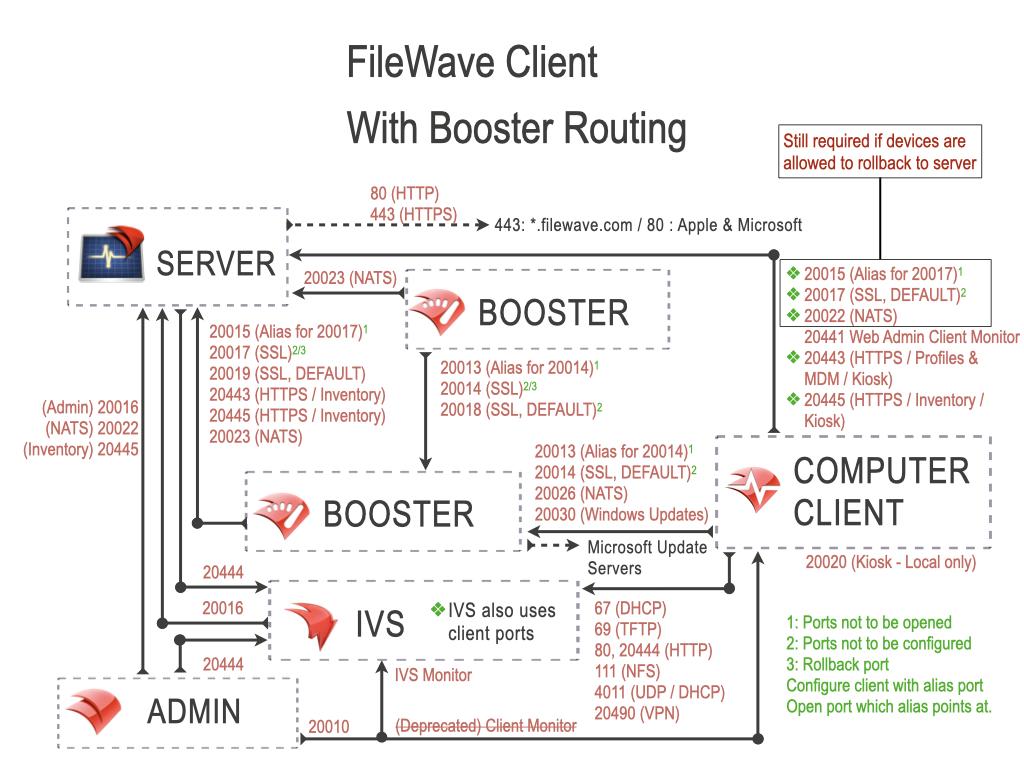
FileWave Booster Ports
The ports in this table are listed from the Booster's perspective, so the “In/Out” column indicates the direction of traffic relative to the Booster.
| Booster Ports | Service | Protocol | In/Out | Description |
| 443 | HTTPS | TCP | Out | FileWave Software Updates (microsoft.com) *** |
| 20014 | SSL | TCP | Incoming |
FileWave Client to Booster: Secure (Booster Priority fallback) Set port 20013, not 20014, in Booster Configuration |
| 20018 | SSL | TCP | Incoming | Booster to Booster: Priority Traffic |
| 20026 | SSL | TCP | Incoming | FileWave Client to Booster connections using NATS Server |
| 20030 | SSL | TCP | Incoming | FileWave Client to Booster for Windows OS updates |
| 443 | HTTPS | TCP | Out |
For Hosted Customers Only: Cloudflare host for Filesets in the Cloud - c7b0813948fe034d9fe3ca8c90faddab.r2.cloudflarestorage.com
Cloudflare IP addresses as listed on https://www.cloudflare.com/ips-v4 - 173.245.48.0/20 |
NATS includes: Remote Control Publishing, Remote Control Routing, device renaming, revoking device certificates, push notifications
*** Also used by FileWave Central to vendor Software Update Servers.
Configuring port 20013 also automatically configures SSL ports; 20014 [port entered +1] and 20018 [port entered + 5]. 20013 is now deprecated and 20014 will be used where 20013 is set. Open port 20014 alone for Client to Booster communication. Open ports 20014 and 20018 for Booster to Booster communication.
Booster should be able to connect with Microsoft OS Updates URL, if using FileWave to manage Windows Software Updates.
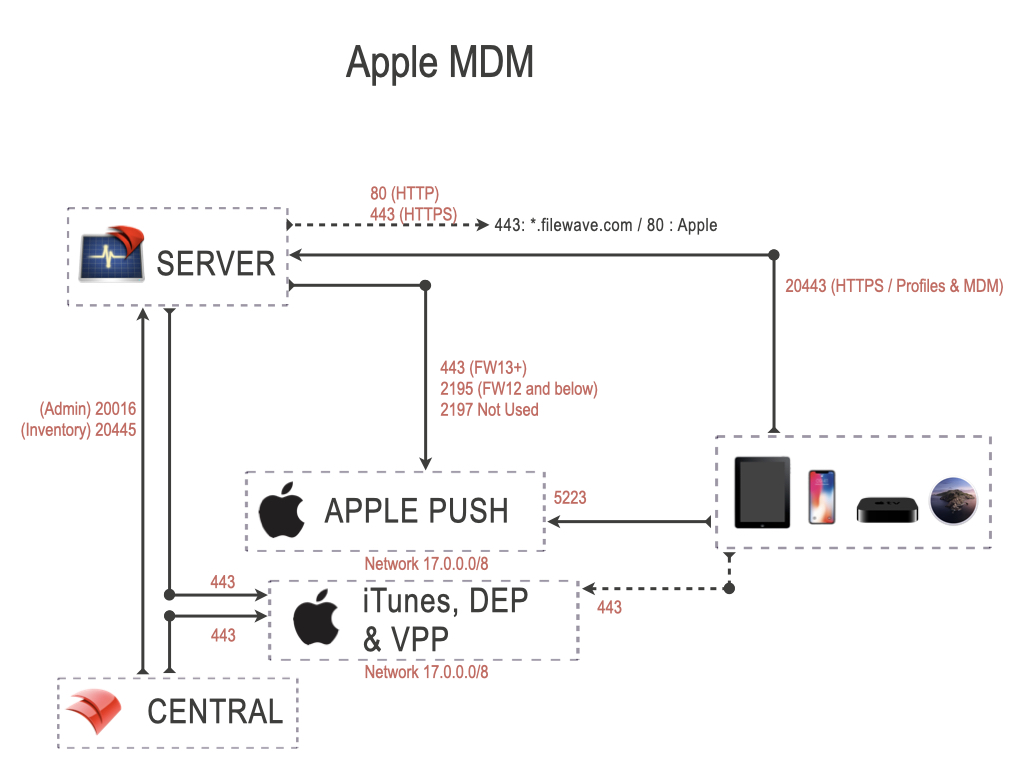
Apple MDM Ports
The ports in this table are listed from the FileWave Server’s perspective, so the “Server In/Out” column indicates the direction of traffic relative to the Server and these ports are specifically those needed to manage Apple devices. Apple devices will also need to reach the Apple servers on 17.0.0.0/8.
| Apple MDM Ports | Service | Protocol | Server In/Out | Description |
| 443 | HTTPS | TCP | Outgoing |
FileWave Server to Apple's servers (17.0.0.0/8) FileWave Admin to iTunes, DEP & VPP (17.0.0.0/8) Device to iTunes, DEP & VPP (17.0.0.0/8) |
| 443 | HTTPS | TCP | Incoming |
VPP v2 Notifications from Apple |
| 5223 | APNS | TCP | Outgoing | FileWave Server to Apple's servers (17.0.0.0/8) |
| 20443 | HTTPS | TCP | Incoming | Device to Server: Profiles & MDM |
| 20445 | HTTPS | TCP | Incoming | FileWave Central to Server |
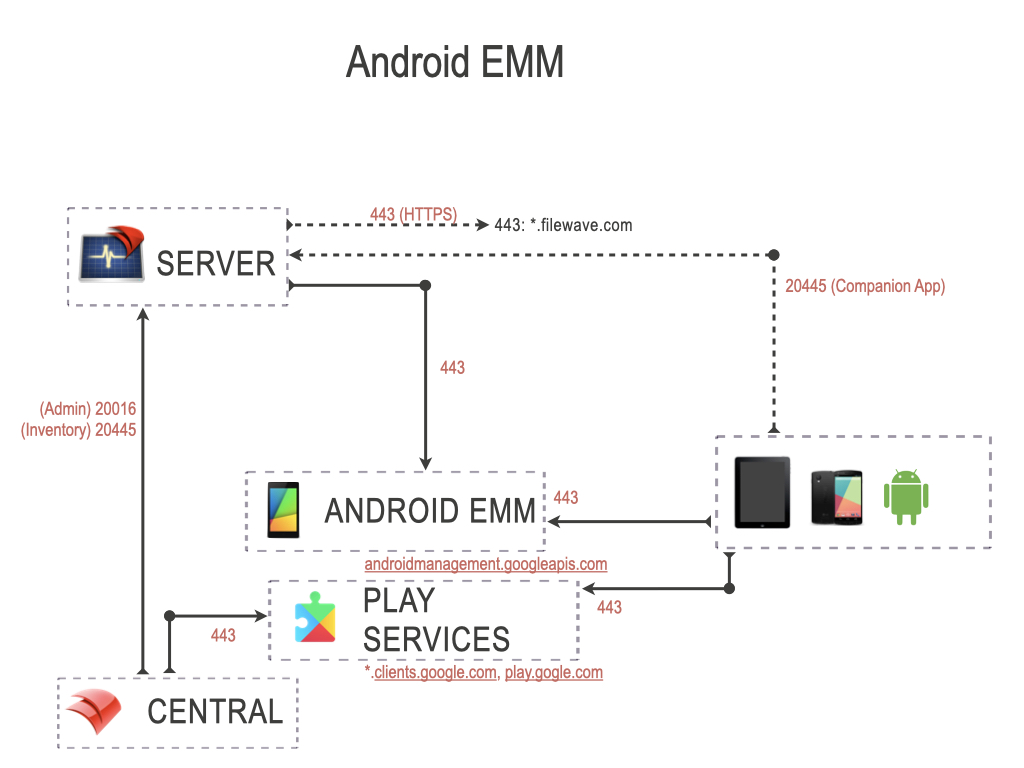
Android EMM Ports
The ports in this table are listed from the FileWave Server’s perspective, so the “Server In/Out” column indicates the direction of traffic relative to the Server and these ports are specifically those needed to manage Android devices. Android devices will also need to reach the Google's servers.
| Android EMM Ports | Service | Protocol | Server In/Out | Description |
| 443 | HTTPS | TCP | Outgoing |
Server to EMM commands (androidmanagement.googleapis.com) Device to Activation servers (*.clients.google.com) Device to Play Store (play.google.com) EMM commands (androidmanagement.googleapis.com) FileWave Central to Play Store (play.google.com) |
| 20016 | SSL | TCP | Incoming | FileWave Central to Server |
| 20445 | HTTPS | TCP | Incoming | FileWave Central to Server: Inventory
Companion App to Server: Location Tracking |
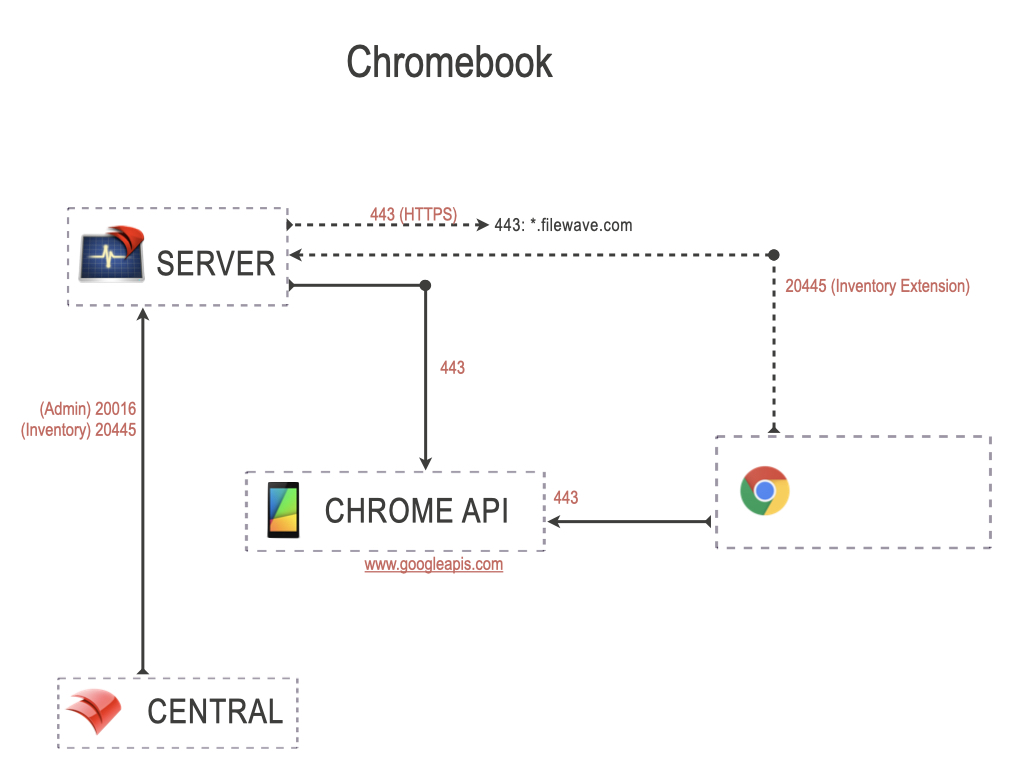
Chromebook Ports
The ports in this table are listed from the FileWave Server’s perspective, so the “Server In/Out” column indicates the direction of traffic relative to the Server and these ports are specifically those needed to manage Google Chromebook devices. Chromebook devices will also need to reach the Google's servers.
| Chromebook Ports | Service | Protocol | Server In/Out | Description |
| 443 | HTTPS | TCP | Outgoing |
Server to Chrome API Chromebook to Chrome API (www.googleapis.com) |
| 20016 | SSL | TCP | Incoming | FileWave Central to Server |
| 20445 | HTTPS | TCP | Incoming |
FileWave Central to Server Chromebook Inventory Extension to Server |
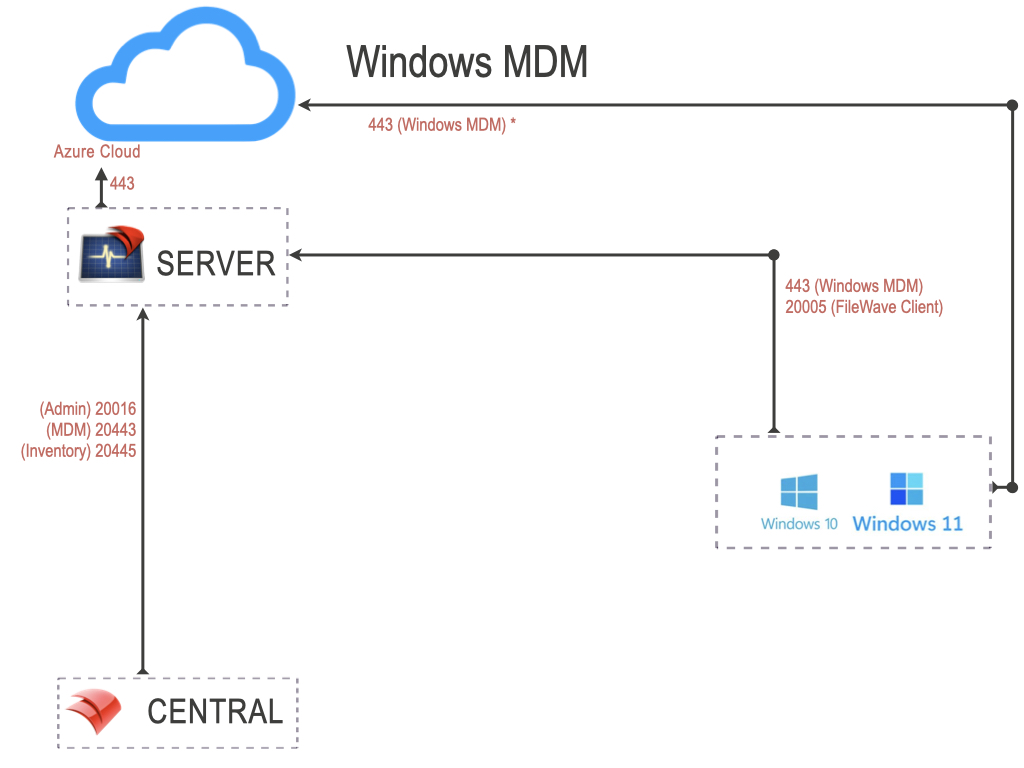
Windows MDM Ports
The ports in this table are listed from the FileWave Server’s perspective, so the “Server In/Out” column indicates the direction of traffic relative to the Server and these ports are specifically those needed to manage Windows MDM devices. Windows devices will also need to reach the Microsoft's servers.
| Windows MDM Ports | Service | Protocol | Server In/Out | Description |
| 443 | HTTPS | TCP | Incoming | Device to Server (Enrollment URL) |
| 443 | HTTPS | TCP | Outgoing |
Server to Windows MDM (*.azure.com) Device to Windows MDM (*.azure.com) |
NOTE: The FileWave client will also be installed and all previously listed FileWave client ports are required.
FileWave IVS Ports
| IVS Ports | Service | Protocol | From | To | Notes | Open port on... |
| 67 | DHCP | UDP | Client | IVS | ‡‡ | IVS |
| 69 | TFTP | UDP | Client | IVS | ‡‡ | IVS |
| 80 | HTTP | TCP |
Client |
IVS | IVS | |
| 111 | NFS | TCP/UDP | Client | IVS | ‡ | IVS |
| 4011 | DHCP | UDP | Client | IVS | UEFI PXE‡‡ | IVS |
| 2049 | NFS | TCP/UDP | Client | IVS | Client to IVS‡ when Secure Imaging is disabled. | IVS |
| 5201 | iperf3 | TCP | Client | IVS | For Performance testing | IVS |
| 20016 | SSL | TCP | IVS | Server | Server | |
| 20017 | SSL | TCP | IVS | Server | Server | |
| 20022 | SSL | TCP | IVS | Server | NATS | Server |
| 20443 | HTTPS | TCP | IVS | Server | Inventory | Server |
| 20444 |
HTTPS |
TCP |
Server | IVS |
Non Hosted Only |
IVS |
| Client | IVS |
|
||||
| IVS |
IVS Django |
|||||
| 20490 | VPN | TCP/UDP | Client | IVS | Client to IVS‡ when Secure Imaging is enabled. | IVS |
| 20445 | HTTPS | TCP | IVS | Server | Inventory | Server |
‡ TCP/IP & UDP
‡‡ UDP only
No comments to display
When ports are added/removed, will the port tester applications be updated as well (in terms of what ports are auto-populated)?
In reply to #1
Thank Sean. The challenge can be when a port is removed or added in version 2.0 we still support 1.0 so there's sometimes a lag, and there were a lot of port changes in the 14.7 - 15.0 releases. That one port though that we are removing now I think stayed too long. In the future it might be nicer if the tool asked what version of FW server it was testing against and then loaded the appropriate list but I also hope we don't go through such a big change in port numbers again.
thanks for literally highlighting 20015!
No comments to display