Firmware Password (macOS 10.14 Mojave+)
Description
Apple have seen to make some changes regarding this over time, through versions of macOS. The following is a method that should work with macOS 10.10+ machines. This recipe allows for creating, changing or deleting the Firmware password.
This script in this recipe is setting the Firmware password of macOS devices. If set incorrectly, you could become locked out of the device. FileWave offers this script as is, use of this script is at the user's understanding and risk and FileWave holds no responsibility for devices that become locked and un-usable. If concerned, please refrain from using this script.
macOS Catalina
This script has been tested successfully on macOS Catalina (10.15.x)
Ingredients
- FileWave
- macOS 10.11+
- Supplied Fileset - Set Firmware Password V1.1.fileset.zip
macOS versions
This method uses the binary 'firmwarepasswd'. This was known to exist in all versions of macOS 10.10 and above. It is possible that this was introduced in later versions of 10.9. However, FileWave 13+ supports macOS 10.11+
Directions
- Download the above Fileset recipe and import into FileWave
- Duplicate the Fileset and append the name appropriately: New, Change or Delete
- Change the Launch Arguments to match the renamed duplicated Fileset based upon the below table
- Edit the script if required for reboot options or set Fileset Properties Reboot
- Associate, test and then deploy
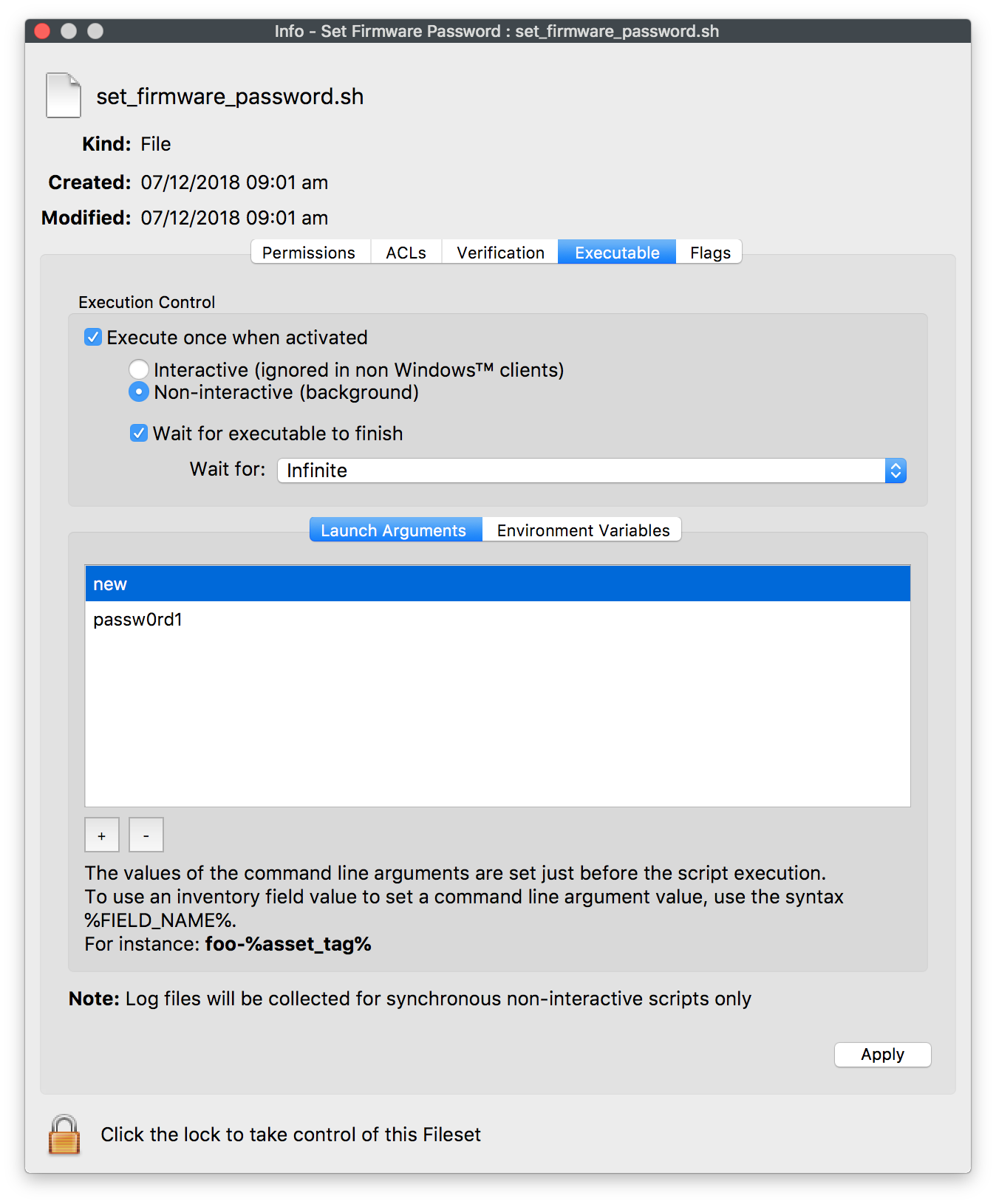
Launch Arguments
To set the Launch Arguments
- Open the Fileset
- Select the script within the Fileset
- Choose Get Info
- Select Executable tab
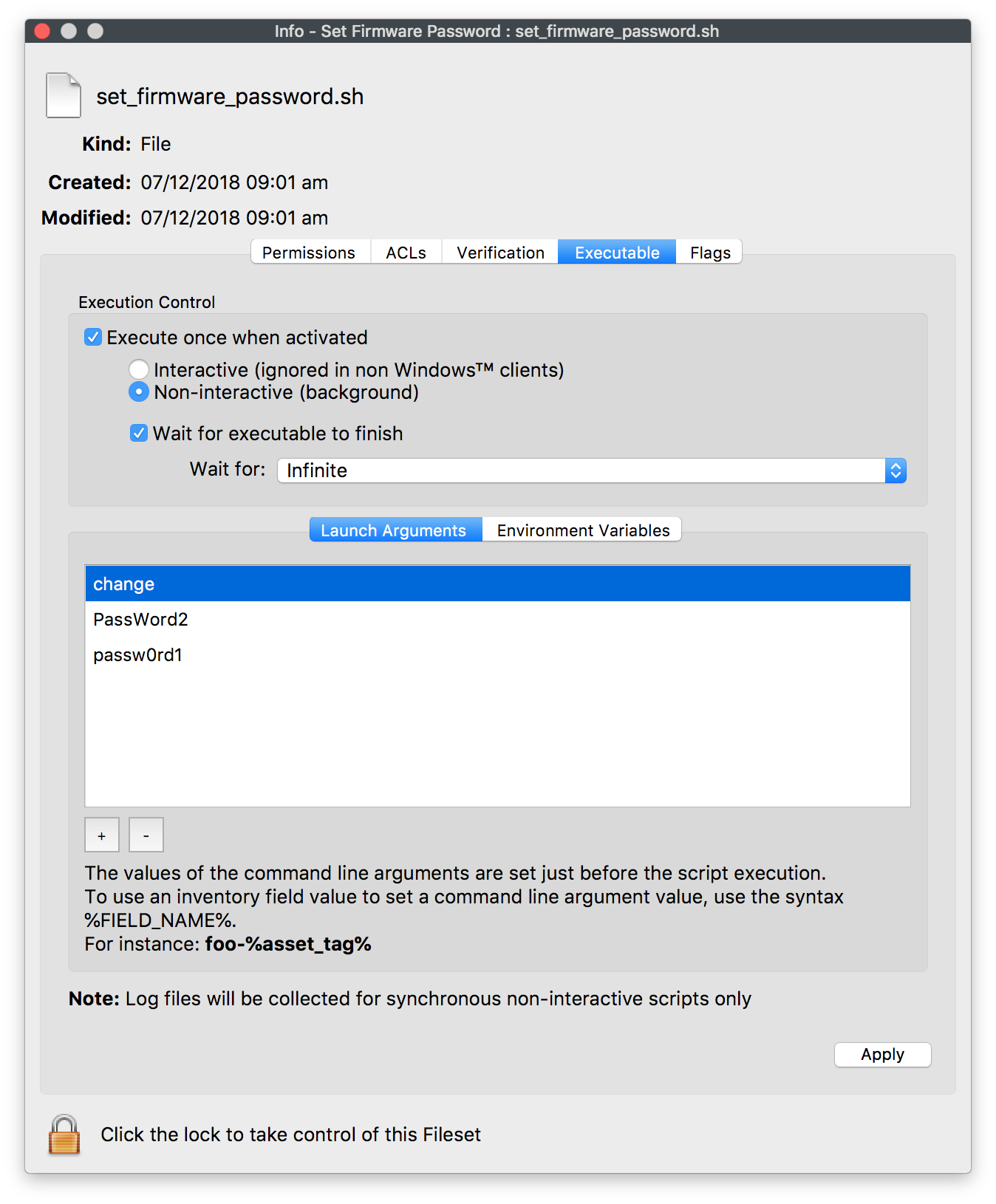
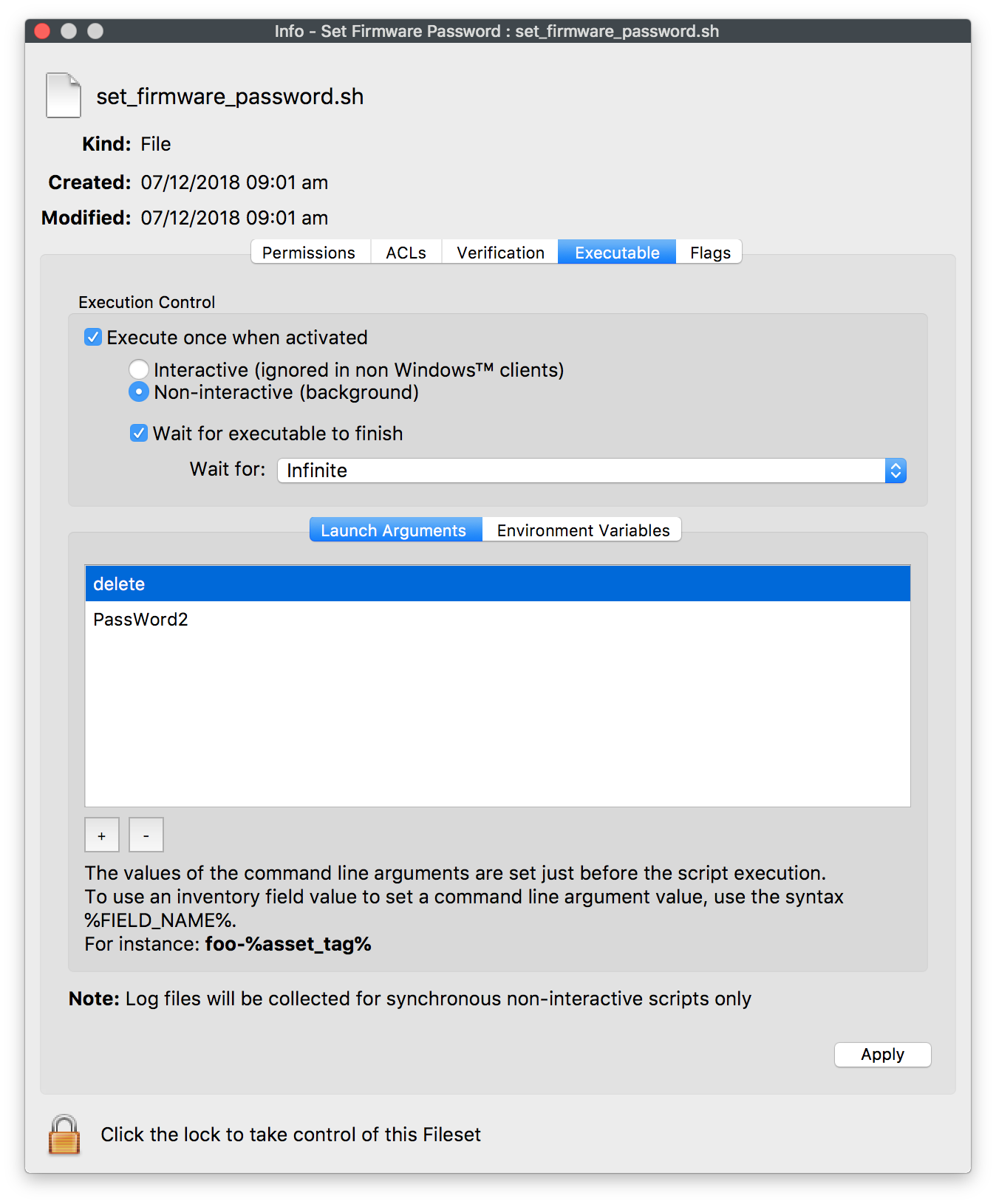
There are 3 options for this fileset: New, Change or Delete. The Launch Arguments should be set as required based upon these options as seen in the table below:
|
Launch Argument |
New |
Change |
Delete |
|
1 |
new |
change |
delete |
|
2 |
new password |
new password |
old password |
|
3 |
old password |
Examples
Reboot Options
By default, the script will not reboot once completed. However, a reboot is required after setting. This could be achieved by setting the Fileset Properties. Alternatively, an option is built into the script to allow for this. Please edit the script appropriately:
reboot_flag=false
# Default - do not reboot at script end; consider using Fileset properties for reboot.
# Firmware password change requires reboot. Tests for alternate boot drive selected
# Alternative options: error, set or ignore
# Use ignore to set default to reboot
# Uncomment command as desired
# error: Script will abort and no firmware password will be set if set boot drive does not match current booted drive
# reboot_device error
# set: Script will set the firmware password without a reboot attempt if set boot drive does not match current booted drive
# reboot_device set
# ignore: Script will continue regardless, setting firmware password and rebooting
# reboot_device ignoreIf choosing an option that does not reboot, the device will need a reboot before the firmware password setting is complete.
Options 'error' and 'set' will check to see if currently set boot drive matches currently booted drive. If true, both options will continue to set the firmware password. If false, 'error' will exit an error without any change, whilst 'set' will set the password but will not reboot.
All options: 'set', 'error' and 'ignore', will ensure (on success) that the current set boot drive matches the currently booted drive before rebooting.
Examples:
For the script to reboot, un-hash the following line:
# ignore: Script will continue regardless, setting firmware password and rebooting
reboot_device ignoreTo allow the password to be changed, but only reboot if set boot drive matches currently booted drive, un-hash the following line:
# set: Script will set the firmware password without a reboot attempt
reboot_device setOnly un-hash one line from these options.
Firmware Password Unlock Seed
The unlock seed is a unique recovery key that can be used by Apple to unlock a device in the event of the password being forgotten. Please see the following KB for an example Custom Field that may be used to report this key:
EUD Security Guidance: macOS 10.13+
No comments to display
No comments to display